


• The various kinds of attacks on WSN
• The attack taxonomy for WSN
• Threats to privacy, control, and availability
• Countermeasures to attacks on WSN
Wireless sensor networks have been a promising approach to many diverse applications and are playing a major role in the upcoming age of intelligent networking. However, with the increase in popularity of such networks, there is an ever-increasing demand for better security. In many military applications, for instance, sensor networks are involved in mission-critical tasks, and security therefore is a top priority in such situations. In addition, resource, computing, and environmental constraints on WSN (discussed in Chapter 1) pose new challenges in securing such networks. Security in WSN is especially challenging due to the inherent broadcast nature of wireless communication. Any radio equipment can participate, either passively or actively, in any form of radio communication, by tuning the equipment to the same frequency band as that of the communicating nodes.
The demand for WSN is increasing even faster with the introduction of miniaturization technology. Consequently, there has been mass production of sensor nodes with mediocre hardware, which is usually not tamper-resistant. Hence, nodes can easily be compromised by attackers, leading to a completely new set of attacks. In this chapter, we review the different kinds of attacks that can be carried out on WSN and then briefly look into state-of-the-art security in WSN.
Wireless sensor networks are a subclass of wireless networks in general, so most kinds of attacks that can be directed at wireless networks can be directed at WSN. However, due to the additional challenges as discussed in Chapter 1, WSN breed a whole new set of attacks that can be classified into “mote-class attacks” and “laptop-class attacks” (Karlof and Wagner 2003). In a mote-class attack, the attacker takes control of a few compromised nodes and has capacity no greater than that of these ordinary sensor nodes. Hence, he has to launch attacks without depleting his resources (storage, computation, and bandwidth). Moreover, the attacker is restricted in his coverage due to limited transmission power. In contrast, the laptop-class attacker is resource-abundant (high transmitting power, longer battery life, high-speed processors, and highly receptive omnidirectional antennae). Hence, he has greater coverage and diversity in terms of the attacks that he can launch. Figure 2.1 portrays the attack taxonomy for WSN, while Table 2.1 shows the attack classification through a layered approach.
In general, attacks can be divided into active and passive attacks.
• Passive attack: In this type of attack, the attacker is able to intercept and monitor data between communicating nodes, but does not tamper or modify packets for fear of raising suspicion of malicious activity among the nodes. For example, in traffic analysis, the attacker may not be able to decode encrypted data, but can find useful information by analyzing headers of packets, their sizes, and the frequency of transmission. In WSN, reconnaissance can also be performed to understand information exchange between communicating nodes, particularly at data aggregation points. Furthermore, routing information can be exploited using traffic analysis.
• Active attack: In this type of attack, the attacker actively participates in all forms of communication (control and data) and may modify, delete, reorder, and replay messages or even send spoofed illicit messages to nodes in the network. Some other active attacks include node capturing, tampering with routing information, and resource exhaustion attacks. Peculiar to WSN, the attacker can modify the environment surrounding sensors, which could affect the sensed phenomena.
In WSN, threats to privacy can be further classified into reconnaissance and eavesdropping.
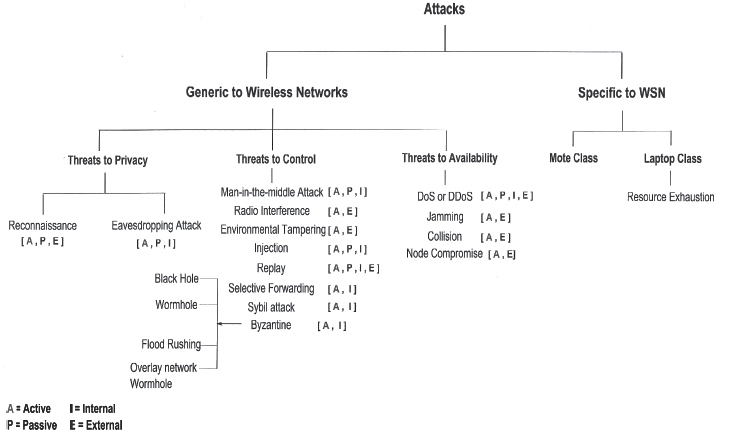

Figure 2.1. Attack Taxonomy for WSN
Table 2.1 Attack Classification Using a Layered Approach
| Layer | Attack vectors |
| Application | Data corruption and repudiation |
| Transport | Session hijacking and SYN flooding |
| IP layer | Byzantine, resource consumption, location disclosure, wormhole and black hole |
| Data link | Traffic analysis |
| Physical | Interference and jamming |
| Multilayer attack | DoS, replay, man-in-the-middle and replay. |
Reconnaissance refers to intelligent gathering or probing to access the vulnerabilities in a network, to launch a full-scale attack later. Reconnaissance attacks can be further classified into active and passive. Passive reconnaissance attacks include the collection of network information through indirect or direct methods, but without probing the targe; active reconnaissance attacks involve the process of gathering traffic with the intention of eliciting responses from the target.
Eavesdropping is the act of listening secretly to a private conversation. However, in the paradigm of WSN, eavesdropping is an operation to learn the “aggregate data” that is being collected by the entire network. Hence, eavesdropping between two specific sensor nodes may not help the attacker in thoroughly understanding the entire network. It can be further classified into active and passive eavesdropping.
• Active eavesdropping: In this case, the adversary actively sends queries to other nodes in an attempt to instigate them to respond to his queries, and in exchange will be able to comprehend the precise task assigned to the nodes in the network. Usually, the attacker launches a “man-in-the-middle attack” (discussed in the next section) to infiltrate into the network and enforce himself on the active path.
• Passive eavesdropping: The attacker inserts himself into the active path, unbeknownst to other nodes in the network. He then passively listens to all traffic sent over the broadcast medium. It may be difficult to detect a passive eavesdropping attack, as the attacker may be operating in stealth mode. (Detection mechanisms are covered in the chapter on intrusion detection systems.)
Man-in-the-middle attack is one of the classical attack vectors that can be executed in a WSN environment (Figure 2.2). In this type of attack, the attacker intrudes into the network and makes an effort to establish an independent connection between a set of nodes and the sink node. The nodes in the network are unaware that the entire flow control is being handled by the attacker. He can be in either a passive or an active state. In a passive state, he simply relays every message among the nodes with the intention of performing an eavesdropping attack. In an active state, he can tamper with the intercepted data in an attempt to break authentication (Authentication is discussed below). The attack can be executed at the physical, data link, network, and application layers (Anand et al. 2005).
With the increase in the number of wireless technologies using the same open spectrum band (2.4 GHz, 5 GHz, or 900 MHz), there is bound to be radio interference. For example, in a dense urban environment, where cordless phones share the same spectrum, there is a sharp degradation of individual node performance due to radio interference. Similar problems can be foretold for sensor networks with the increase in sensor nodes per network. The result of such interference could lead to change in the information bits transmitted over the wireless medium, thereby making the bits unintelligible and ultimately being dropped by the receiver (Xu et al. 2008). Hence, radio interference could lead to a denial-of-service attack. The worst-case scenario in radio interference is jamming.


Figure 2.2. Man-in-the-Middle Attack in WSN
After the attacker has clandestinely intruded into the WSN network, he may impersonate a few of the sensor nodes (or even sink nodes) and may inject malicious data into the network. The malicious data might be false advertisement of neighbor-node information to other nodes, leading to impersonation of sink nodes and aggregation of all data.
A replay attack is a common attack in WSN, whereby an attacker is able to intercept user data and retransmit user data at a later time. This attack is particularly useful in breaking weak authentication schemes, which do not consider the time stamp when authenticating nodes. This attack is also useful during shared-key distribution processes.
In a Byzantine attack, the outside adversary is able to take full control of a subset of authenticated nodes that can be used to attack the network from inside. Such attacks by malicious behavior are known as Byzantine attacks. Some examples of Byzantine attacks are black holes, wormholes, flood rushing, and overlay network wormholes.
• Black hole attacks: In this type of attack (Figure 2.3), the attacker drops packets selectively, or all control and data packets that are routed through him. Therefore, any packet routed through this intermediate malicious node will suffer from partial or total data loss.
• Flood rushing attack: This type of attack (Figure 2.4) is common to wireless networks and exploits the flood duplicate suppression technique. In this attack, the attacker attempts to overthrow the existing routing path by sending a flood of packets through an alternate route, which will result in discarding the legitimate route and adopting the adversarial route. Usual authentication schemes cannot prevent this attack, as the adversaries are authenticated nodes.
• Wormhole attack: In this type of attack, two conniving sensor nodes, or laptops, tunnel control and data packets between each other, with the intention of creating a shortcut in the WSN. Such a low-latency tunnel between the two conniving nodes will likely increase the probability of it being selected as an active path. This type of attack is very closely related to the sinkhole attack, because one of the conniving nodes could falsely advertise to be the sink node and thereby attract more traffic than usual. One of the main differences between a Byzantine wormhole and a traditional wormhole is that in a Byzantine wormhole, the tunnel exists between two compromised nodes, while in a traditional wormhole, two legitimate nodes are tricked into believing that a secure tunnel exists between them.


Figure 2.3. Black Hole Attack
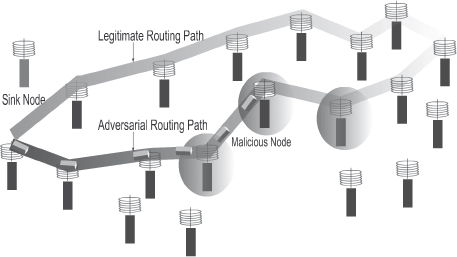

Figure 2.4. Flood Rushing Attack
• Byzantine overlay network wormhole attack: This type of attack is a variant of wormhole attack, and occurs when the wormhole attack is extended to multiple sensor nodes; resulting in an overlay of compromised nodes. It provides a false illusion, to honest nodes, that they are surrounded by legitimate nodes, resulting in frequent reuse of the adversarial path.
The sybil attack was first introduced by Douceur while studying security in peer-to-peer networks (Douceur 2002), and later Karlof and Wagner showed that this type of attack poses a serious threat to routing mechanisms in WSN (Karlof and Wagner 2003). Sybil is an impersonation attack in which a malicious node masquerades as a set of nodes by claiming false identities, or generating new identities in the worst case (Newsome et al. 2004). Such attacks can be easily executed in a WSN environment because the nodes are invariably deployed in an unstructured and distributed environment, and communicate via radio transmission. They are especially detrimental in applications such as data aggregation, voting systems, reputation evaluation, and geographic routing. Using a sybil attack in location-aware routing, it is possible to be in multiple locations at the same time.
In a sinkhole attack, the adversary impersonates a sink node and attracts the whole of traffic to a node or a set of nodes. Similar to a blackhole attack, the attacker takes control of a few compromised nodes and advertises false routing information to its neighbors, thereby luring all traffic to him.
A denial-of-service attack occurs when an attacker floods the victim with bogus or spoofed packets with the intent to lower the response rate of the victim. In the worst-case scenario, it makes the victim totally unresponsive. For instance, in a WSN environment where nodes have limited computational capacity, a DoS attack from a resource-abundant adversary can overwhelm the nodes by flooding packets, which will exhaust communication bandwidth, memory, and processing power. From an attacker’s point of view, this attack is also useful in wireless networks where nodes are required to deliver time-critical data. Jamming (discussed in the next section) the wireless links can also lead to a DoS attack.
An extension of a DoS attack is a distributed DoS attack, where an attacker takes control of a few nodes in the network, leading to a distributed flood attack against the victim.
One of the common techniques to discover neighbors is to send HELLO packets. If a node receives a HELLO packet, it indicates that it is within the range of communication. However, a laptop-class adversary can easily send HELLO packets with sufficient power to convince the sensor nodes that it is in proximity of communication and may be a potential neighbor. The adversary can also impersonate a sink node or a cluster node.
Jamming is one of the most lethal types of attacks in WSN and is a direct way to compromise the entire wireless network. In this type of attack, the attacker jams a spectrum band with a powerful transmitter, and prevents any member of the network in the affected area from transmitting or receiving any packet. Jamming attacks can be divided into constant jamming and sporadic jamming. Sporadic jamming can be very effective at times when a change in one bit of a data frame will force the receiver to drop it. In this kind of attack, it is difficult for the victim to identify whether his band is being jammed intentionally or due to channel interference, and his immediate reaction is usually to increase his transmitting power, thereby depleting resources at a faster rate. Jamming attacks target the physical and MAC layers. Xu et al. discuss four types of jamming attacks (random, reactive, deceptive, and constant) which would result in DoS attacks (Xu et al. 2005). They conclude that detection schemes can be very complex with reference to differentiating malicious attacks from link impairment.
Collision attacks target the MAC layer to create costly exponential back-off. Whenever collision occurs, the nodes should retransmit packets affected by collision, thus leading to multiple retransmissions. The amount of energy expended by the attacker is much less than the energy expended (battery exhaustion) by the sensor nodes. Collision attack can be categorized under resource exhaustion attacks.
Node compromise is one of the most common and detrimental attacks in WSN. As sensors can be deployed in harsh environments such as a battlefield, ocean bed, or the edge of an active volcano, they are easily susceptible to capture by a foreign agent. In case of a battlefield scenario, the enemy could make an effort to dig into nodes with the intention of extracting useful data (extracting private keys in sensor nodes). Furthermore, it could be reprogrammed and launched into a battlefield to operate on behalf of the enemy.
TinyOS Beaconing Protocol uses a breadth-first spanning tree algorithm to broadcast routing updates. The sink node periodically broadcasts updated routing information to its immediate neighboring nodes. These neighboring nodes then rebroadcast this information to their immediate neighbors, and the process continues recursively. During this process, each intermediate node makes a note of its parent node (the parent node is the first node that was able to make contact with its subordinate node and relay the routing information). When all the active nodes are operational, they should send all the sensed data to their parent node. However, this protocol is vulnerable to many attacks. For example, a simple impersonation attack, leading to a sinkhole attack, can totally compromise the entire network (Karlof and Wagner 2003; Sun et al. 2008).
Authentication can be used to prevent such impersonation attacks, but it does not prevent a laptop-class adversary from launching a selective forwarding attack (Figure 2.5), an eavesdropping attack, or a black-hole attack. The attacker creates a wormhole between two conniving laptop-class adversaries. The two laptops are placed near the sink node and the targeted area, respectively. The laptop near the sink node attracts its entire neighbor’s traffic and simply tunnels these authenticated messages to its colluder. The laptop attacker, close to the sink node, plays a passive role in forwarding these messages. Due to his furtive nature, it is difficult for his neighbors to detect whether he is malicious. Once the authenticated messages reach the remote laptop adversary, he could launch a black-hole attack or a selective forwarding attack.
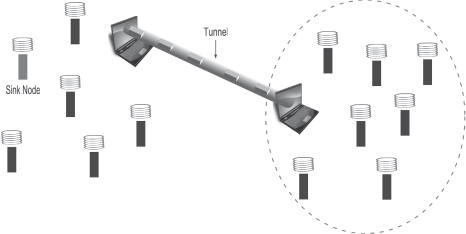

Figure 2.5. Selective Forwarding Attack in TinyOS Beaconing
Let us consider a situation where digital signatures are being used for authentication and, while the routing updates are in progress, the sink node’s private key is leaked. (Methods used to leak the private key are beyond the scope of this book.) As soon as the sink node realizes that its private key is being compromised, it immediately broadcasts a new public key. All the nodes in close proximity to the sink node will update their local copy of the sink node’s public key. The laptop close to the sink node will perform the same operation and convey this information to its colluding laptop. The remote laptop can now easily impersonate the sink node and launch a sinkhole attack. In addition, he can further create routing loops, which is a resource-exhaustion attack.
GEAR (discussed in Chapter 1) proposes a location- and energy-aware, recursive routing algorithm to address the problem of uneven energy consumption in routing in WSN. In GEAR, every node gauges the energy levels of its neighbors along with the distance from the target before making a routing decision. In such situations, a laptop-class attacker can advertise that he has larger energy levels than his neighboring node and attract all traffic to him. Thenceforth, he can execute a sybil, black-hole, or selective forwarding attack.
As attacks on WSN become more sophisticated, the demand for new security solutions is continually increasing. Hence, an array of new security schemes have been designed and implemented in the past decade (Healyet al. 2009; Perrig et al. 2004). Most of these schemes have been designed to provide solutions on a layer-by-layer basis rather than on a per-attack basis; in doing so, they have left a gap between layers that may lead to cross-layer attacks. We will look more closely at cross-layer security later in this book.
In general, any security suite should ensure authentication, integrity, confidentiality, availability, access control, and nonrepudiation. In addition, physical safety is absolutely necessary to avoid tampering or destruction of nodes. Therefore, construction of tamper-resistant sensor nodes is absolutely necessary. However, such tamper-resistant schemes come at a higher manufacturing cost and are restricted to applications that are not only critical but that use fewer nodes.
• Authentication: The main objective of authentication is to prevent impersonation attacks. Hence, authentication can be defined as the process of assuring that the identity of the communicating entity is what it claims to be.
• Integrity: The goal of integrity is to affirm that the data received is not altered by an interceptor during communication (by insertion, deletion, or replay of data) and is exactly as it was sent by the authorized sender. Usually, cryptographic methods such as digital signatures and hash values are used to provide data integrity.
• Confidentiality: The goal of confidentiality is to protect the data from unauthorized disclosure. A common approach to achieving confidentiality is by encrypting user data.
• Availability: The goal of availability is to ensure that the system (network) resources are available and usable by an authorized entity, upon its request. It tries to achieve survivability of the network at all times.
• Access control: The goal of access control is to enforce access rights to all resources in its system. It tries to prevent unauthorized use of system and network resources. Access control is closely related to authentication attributes. It plays a major role in preventing leakage of information during a node-compromise attack. One of the conventional approaches to access control is to use threshold cryptography. This approach hides data by splitting it into a number of shares. To retrieve the final data, each share should be received through an authenticated process.
• Nonrepudiation: Nonrepudiation can be best explained with an example. Let Alice and Bob be two nodes, who wish to communicate with each other. Let Alice send a message (M) to Bob. Later, Alice claims that she did not send any message to Bob. Hence, the question that arises is how Bob should be protected if Alice denies any involvement in any form of communication with Bob. Nonrepudiation aims to achieve protection against communicating entities that deny that they ever participated in any sort of communication with the victim.
To prevent radio interference or jamming, the two common techniques used are frequency-hopping spread spectrum (FHSS) and direct-sequence spread spectrum (DSSS). In FHSS, the signal is modulated at frequencies such that it hops from one frequency to another in a random fashion at a fixed time interval. The transmitter and the corresponding receiver hop between frequencies using the same pseudo-random code for modulation and demodulation. If an eavesdropper intercepts a FHSS signal, unless he has prior knowledge of the spreading signal code, he will not be able to demodulate the signal. Furthermore, spreading the signal across multiple frequencies will considerably reduce interference.
In DSSS, a spreading code is used to map each data bit in the original signal to multiple bits in the transmitted signal. The pseudo-random code (spreading code) spreads the input data across a wider frequency range compared to the input frequency. In the frequency domain, the output signals appear as noise. Since the pseudo-random code provides a wide bandwidth to the input data, it allows the signal power to drop down below the noise threshold without losing any information. Therefore, this technique is hard for an eavesdropper to detect, due to lower energy levels per frequency and more tolerance to interference.
The above-mentioned schemes can provide security only as long as the hopping pattern or the spreading code is not disclosed to any adversary.
Link-layer security plays an important role in providing hop-by-hop security. Its protocols are useful in handling fair channel access, neighbor-node discovery, and frame error control. Legacy security protocols such as SSL or IPSec cannot be applied directly to WSN because they do not provide data aggregation or allow in-network processing, which are prime requirements in designing security protocols.
To prevent denial-of-service (DoS) attacks on WSN, it is proposed that each intermediate node in the active routing path perform an authentication and integrity check. However, if a few intermediate nodes in the active path have very low energy levels, and if they are forced to perform authentication checks, they would expend all their energy and disrupt the active path. On the other hand, if we look at end-to-end authentication in WSN, it is more energy-efficient, since the sink node (resource-abundant) is the only node that performs authentication and integrity checks. Nevertheless, this scheme is vulnerable to many types of security attacks (black hole, selective forwarding, and eavesdropping). Hence there is a need for adaptive schemes that consider the energy levels of each node when deciding on the authentication schemes.
Early security approaches focused on symmetric keying techniques, and authentication was achieved using Message Authentication Code (MAC). One of the common MAC schemes is a cipher block chaining message authentication code. However, this scheme is not secure for variable-length input messages. Hence the end user (sensor nodes) have to pad the input messages to be equal to a multiple of the block cipher. Therefore, each node has to waste energy padding input data. To overcome this issue, other block cipher models such as CTR and OCB have been proposed. With reference to confidentiality, symmetric encryption schemes used to protect WSN are DES, AES, RC5, and Skipjack (block ciphers) and RC4 (a stream cipher). Usually, block ciphers are preferred over stream ciphers because they allow authentication and encryption.
A few proposed link-layer security frameworks include TinySec, Sensec, SNEP, MiniSec, SecureSense (Karlof et al. 2004; Perrig et al. 2002), and ZigBee Alliance (www.zigbee.org/Specifications.aspx). However, these schemes have limitations. For example, in Tinysec a single key is manually programmed into all the sensor nodes in the network. A simple node-capture attack on any one of these nodes may result in the leakage of the secret key and compromising of the entire network. A need for a stronger keying mechanism is needed to secure TinySec. In addition, TinySec requires padding for input messages that are less than 8 bytes. It uses block cipher to encrypt messages, and for messages that are less than 8 bytes, the node will have to use extra energy to pad the message before encrypting.
Although WSN are a subclass of wireless networks, due to the resource-constrained nature of WSN, they breed a whole new set of attacks. In this chapter, we introduced the attack taxonomy for WSN and discussed various kinds of attacks on such networks. Countermeasures to these attacks were discussed from a layered perspective of the WSN stack.
Anand, M., Z. G. Ives, and I. Lee. Quantifying eavesdropping vulnerability in sensor networks. Departmental papers, Department of Computer & Information Science, University of Pennsylvania, 2005.
Douceur, J. R. The sybil attack. First International Workshop on Peer-to-Peer Systems (IPTPS ‘02). 2002.
Healy, M., T. Newe, and E. Lewis. Security for wireless sensor networks: A review. SAS 2009—IEEE Sensors Applications Symposium. IEEE, 2009, 80–85.
Karlof, C., and D. Wagner. Secure routing in wireless sensor networks: Attacks and countermeasures. First International Workshop on Sensor Network Protocols and Applications. IEEE, 2003, 113–127.
Karlof, C., N. Sastry, and D. Wagner. TinySec: A link layer security architecture for wireless sensor networks. Second ACM Conference on Embedded Networked Sensor Systems. ACM, 2004, 162–175.
Newsome, J., E. Shi, D. Song, and A. Perrig. The sybil attack in sensor networks: Analysis & defenses. Third International Symposium on Information Processing in Sensor Networks, IPSN. IEEE, 2004, 259–268.
Perrig, A., R. Szewczyk, J. Tygar, V. Wen, and D. Culler. SPINS: Security protocols for sensors. Wireless Networks 8, no. 5 (2002): 521–534.
Perrig, A., J. Stankovic, and D. Wagner. Security in wireless sensor networks. Communications of the ACM 47, no. 6 (June 2004): 53–57.
Sun, Z., X.-G. Zhang, H. Li, and A. Li. The application of TinyOS beaconing WSN routing protocol in mine safety monitoring. International Conference on Mechtronic and Embedded Systems and Applications, MESA. IEEE, 2008, 415–419.
Xu, W., W. Trappe, Y. Zhang, and T. Wood. Proceedings of the Sixth ACM International Symposium on Mobile Ad Hoc Networking and Computing (MobiHoc ‘05). ACM, 2005, 48–57.
Xu, W., W. Trappe, and Y. Zhang. Defending wireless sensor networks from radio interference through channel adaptation. ACM Transactions on Sensor Networks, 4, no. 4 (August 2008).