INTRODUCTION
If you are reading this introduction, you are probably one of two types of people. The first type is someone who has worked in healthcare for a few years and whose responsibilities are becoming more dependent on information technology—and therefore information security. Perhaps you work in healthcare records management, and your organization is on its first or second evolution of the electronic healthcare record. You have been chosen to provide your records management expertise to the new digital system. Congratulations! You are clearly valued in your organization. And this book will serve you, because it will address, in a practical manner, your concerns about moving from paper-based records to digital, networked systems.
The second type of person is someone who has worked in information technology in healthcare or an industry other than healthcare. Perhaps you are a network operator who previously worked for a local bank or supermarket. Now you have the opportunity to be the firewall administrator for the community hospital. Congratulations to you as well! You are now an important person in the delivery of healthcare. You may not consider yourself a healthcare provider, but you are, and you most certainly directly support those personnel who provide patient care. Within this book, you will learn of the importance to patient care and healthcare business of providing information security and privacy in a healthcare organization. When it comes to healthcare provision, the actions or inactions of information technology practitioners can impact patient safety or clinical quality.
For those of you who do not fit into the two categories I mentioned, do not worry. This material is very much applicable to your pursuit to elevate your competency and your dedication to the profession. Having performed healthcare information security and privacy work for about two decades, I offer this book as a collection of lessons learned as much as anything else. Here, you will find real scenarios, actual issues, and practical solutions. I name no names to protect the innocent. In sum, I grew up in healthcare information security and still maintain a “healthcare first” attitude. When perfectly acceptable information security practices are applied to healthcare without considering the impact on patient care or provider practices, healthcare delivery and the patient often suffer. My goal is to provide constructive, practical guidance for professionals like you to balance the need to protect patient information and deliver quality patient care safely. Of course, an outcome of your study of this material is to obtain certification. This designation demonstrates that you understand that competent healthcare information security and privacy professionals can, in fact, enable better healthcare, improve outcomes, and advance organizational initiatives.
The contents of this book cover the entire exam outline according to the International Information System Security Certification Consortium, or (ISC)2. Each chapter is aligned with one of the seven domains tested by the HCISPP exam, as listed here, along with the percentage of questions you will see on the exam:
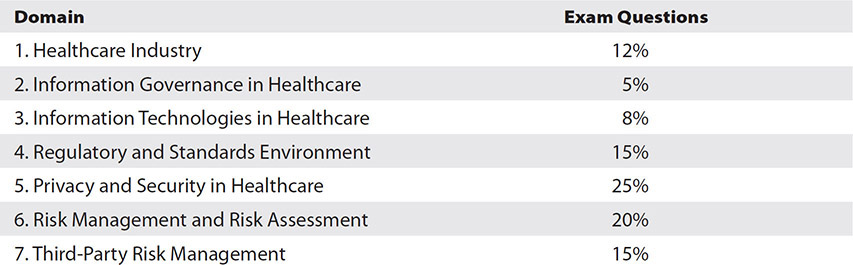
Beyond the relative importance (ISC)2 assigns to each domain based on the exam construction, you will find practical information in this book. As you work on a daily basis, and depending on your position in your organization, you may find the information presented in some chapters more valuable than information in other chapters. For this reason, I wrote these chapters with a philosophy that each chapter is 100 percent important to an HCISPP in the workplace, even if the exam applies unequal weighting. You can thank me later if the extra material also helps you in your day-to-day practices.
I hope you will enjoy reading this material as much as I have enjoyed constructing it. I welcome your feedback on any and all of the information in this book. In many ways, what you will read is the result of many discussions and commiseration sessions I have had over the years with like-minded colleagues and friends. Those conversations continue, I am glad to say. Add your voice. After you dig into the contents, let me know what you think about this book. The easiest way to reach me is on LinkedIn at https://www.linkedin.com/in/seanmurphy092009.
Why Become an HCISPP
I am passionate about the need for and value of the discussions in this book for two reasons. Some people enter healthcare from other industries, and they must understand the business of healthcare before they are able to provide healthcare information security. Others come from health information management and privacy roles as their responsibilities for protecting information include more use of digital assets and information technologies that require security controls for electronic information.
Certification demonstrates competency. But more importantly, certification through (ISC)2 demonstrates a commitment to the profession: to sit for the exam, you must meet standards, and to maintain the credential, you must continue to meet standards through continued professional education. HCISPP as a stand-alone certification demonstrates a practitioner’s experience and dedication to healthcare information security and privacy. The quality of the HCISPP is backed by (ISC)2 as the credential-granting organization. The organization maintains accreditation for the quality of HCISPP through the rigid ANSI/ISO/IEC 17024 standard, Personnel Certification – Documents and Resources.
I was proud and fortunate to participate in the first iteration of the HCISPP credentialing process. The group that came together to discuss the ideal HCISPP candidate, job task analysis, exam questions, and even the name of the credential were leaders and practitioners with a common goal. The group comprised authorities from the United States and international government and private sectors, along with academic subject matter experts. Our focus was on a credential that specifically differentiates the healthcare information security and privacy professional within the security and privacy vocations. We wanted to provide recognition for professionals who demonstrated high levels of competency within the (ISC)2 domains. After more than a year, the group hammered out the first version of HCISPP to a terrific acceptance by the healthcare industry.
Before you sign up to take an exam, make sure you understand and meet the prerequisites. As I said earlier, HCISPP is a stand-alone credential. It is also meant to be a practitioner-level recognition. That does not mean it is easy or a low bar. Before you take the HCISPP exam, (ISC)2 requires at least two years of experience, and one of those years must be in healthcare. Every candidate must have worked as an employee, and not as a volunteer, in information security or privacy roles. There is no expectation that a candidate has experience or expertise in all of the domains in the HCISPP Common Body of Knowledge (CBK). However, the prerequisites include that the experience must come from at least one of the domains related to privacy, security, and compliance. There are some caveats, too, as legal experience can satisfy requirements concerning compliance. If you have worked in information management functions, that experience can be substituted for the privacy competencies.
How to Use This Book
When I wrote my first book in 2015, it was among just a handful of books about healthcare information security and privacy available at the time. I had hoped that this would change over time and more books would be available to choose from, but it really has not. If you look at the supplemental references (ISC)2 includes on its web site (www.isc2.org), you can exhaust the list pretty quickly. An Internet search on terms such as “healthcare information security and privacy” turns up a few more options. The good news is that this book covers the material you need if your purpose is to achieve certification. The organization of the book matches the published organization of the HCISPP exam domains.
Each chapter covers one domain. However, the book is intended for more use over a longer lifespan:
• This book will help those of you who are experiencing firsthand the integration of healthcare, biomedical engineering, information security, information technology, and privacy.
• It is a terrific desk reference for those of you who already have a few years in a healthcare information security and privacy position.
• The material is valuable as part of a curriculum in healthcare information security and privacy in universities, colleges, and technical education workshops and seminars.
As you read through the book, you may note that there are some biases or rationales for how some material was emphasized beyond what may be testable. In no case does the material detract from your exam preparation, but as an HCISPP you may find these lessons learned useful in how you approach your job.
All Healthcare Is Local (Like Politics)
For the most part, we are guided more by our organizational policies and experiences than by theoretical practices and higher level regulatory pressures. That said, organizational policies and procedures should be based on laws and directives from regulators. To be effective as a healthcare information security and privacy professional, however, you will be guided more by organizational policies and procedures. This is why experience in the healthcare field is so important toward measuring competency.
With that in mind, one of the underlying themes of this book is the role you will play in developing and implementing organizational policies. As you read this book, take the opportunity to think about your own organizational policies and procedures around information protection:
• What policies and procedures are in place?
• What are their stated purposes?
• What regulations do they comply with?
• What are the roles and responsibilities presented?
Following are some of the types of policies you should look for:
• Information security program
• Information risk management
• Incident reporting process
• Information governance (information management council, configuration control board, and so on)
• Notice of privacy practices
By focusing on the organization’s policies, the book has a practical application. As you read and study, you may encounter information that does not reflect how your organization does things. There is always room and need for some variation. By comparing and gathering internal sources, you will gain a better appreciation of the general organization and structure of information protection, which should be evident in all healthcare organizations. (If nothing else, you may identify opportunities for improvement!) Again, internal policies and procedures are typically linked to a requirement that is external to the organization, such as the US Health Insurance Portability and Accountability Act (HIPAA) or the Canadian Personal Health Information Protection Act (PHIPA). Therefore, this book recognizes how important internal guidance is in understanding the application of overarching national or international regulatory frameworks and directives.
Publicly Available Sources Are Prioritized
Each chapter ends with a references section to provide a citation for where certain facts and statements can be verified. Along with the specific citations, you may find it useful to explore the material the citations come from to explore additional topics and content in those sources.
The majority of the references provided in the book are publicly available. In most cases, they are offered here with the intent of suggesting further reading. Not only are they listed to cite a particular point made, but they also point you to a wealth of additional material you may want to access. In this way, the book helps expand your knowledge base. No single book can cover every topic in sufficient detail, but narrowing the universe of information down to a manageable list of sources is possible. At the same time, obscure, hard-to-find, and proprietary sources of information are likely not available to any of us on a day-to-day basis, so these constitute a small and necessary portion of the book’s source material. The sources listed are intended to augment the material and be applicable to healthcare. Among the references are the following:
• National Institute of Standards and Technology 800 series, with special emphasis on
• SP 800-122, Guide to Protecting the Confidentiality of Personally Identifiable Information (PII)
• SP 800-66 Rev. 1, An Introductory Resource Guide for Implementing the Health Insurance Portability and Accountability Act (HIPAA) Security Rule
• SP 800-61 Rev. 2, Computer Security Incident Handling Guide
• SP 800-53 Rev. 4, Security and Privacy Controls for Federal Information Systems and Organizations (updated 2015)
• SP 800-39, Managing Information Security Risk: Organization, Mission, and Information System View
• SP 800-37 Rev. 2, Risk Management Framework for Information Systems and Organizations: A System Life Cycle Approach for Security and Privacy
• International Association of Privacy Professionals (IAPP) Privacy Advisor, accessed at https://iapp.org/news/privacy-advisor
International Coverage
If you work in the United States, you undoubtedly are concerned with HIPAA and its amendments. In this book, you will find ample material to guide you in the relevant areas of HIPAA compliance. However, as the provision of healthcare becomes global and many US healthcare providers expand their markets overseas, international healthcare laws and procedures become relevant to US-based healthcare workers. Add to that the growing market for electronic health records and cloud-based services, to name a few, that are outside the United States, and you can see that, although healthcare is still local in nature, it requires an international perspective as well.
At the same time, the target audience of this book includes all of our international colleagues in healthcare. The fact is we all share the same convergence of
• Paper-based records to digital
• Regulatory pressures to protect sensitive information
• Workforce professions with new information protection responsibilities
• Increased networking and interoperability
Because we share these common concerns, this book is inclusive of an international healthcare information security and privacy professional audience. Some may think there is too much of an international focus. Others will think there is not enough. In the end, the intent is to at least acknowledge the common concerns we all have and the similar framework and approaches we take. A special point of emphasis, this book was written as the European Union Data Protection Directive (DPD) was superseded by the General Data Protection Regulation (GDPR). More importantly, the (ISC)2 HCISPP exam includes coverage of EU DPD. There are several areas where the inclusion of EU DPD may seem confusing as we have transitioned to GDPR in practice. However, for purposes of the exam, knowing about EU DPD is necessary.
Emphasis on Risk Management
One of the central responsibilities in the practice of healthcare information security and privacy is managing information risk:
• Knowing the standards-based assessment tools
• Understanding the importance of assessing the organization and third parties
• Comprehending the process of mitigating vulnerabilities
• Communicating findings throughout the organization
• Continually assessing the organization and the risk management program for improvement
These basic concepts are foundational, and a large portion of this text is dedicated to them. This is on purpose, as risk management proficiency is a practical skill that you must have. I am not the first author to point out that no silver bullet exists—there is no perfect process or technology that will prevent all data incidents and breaches. Perfection is not the goal. Compliance is not equal to security either. What is key is your proficient application of risk management to your organization to protect, detect, correct, and recover as quickly as possible, with minimal impact, and at the least cost to the organization.
If you do these things, which are hard, your role as a healthcare information security and privacy professional can be rewarding and vital to improved patient care, enhanced organization-wide quality, and reduced costs over the long run. Not to mention, the work can be a lot fun!
Exam Expectations
It probably goes without saying that the major hurdle to becoming an HCISPP is passing the exam. You can expect a three-hour exam. You can take necessary breaks to use the restroom, but you should try and minimize these as much as possible. You may have plenty of time, but in the proctoring environment, coming and going during the exam is a pain. If there are a lot of exam-takers in the room, you may experience significant delays as the proctor has to provide secure exit and entry during the exam to ensure that candidates do not access material or bring it back into the testing area.
The exam has 125 multiple-choice questions, based on short questions and some longer scenarios. Keep in mind that approximately 25 of the questions are trial or test questions, provided to evaluate their usefulness in future exams. These questions do not count against your score. You probably will not be able to tell which questions are experimental. That said, if you come across a question that seems incomprehensible or you simply do not know the answer, do not agonize. Maybe it is an experimental question. I like to take that approach so I can concentrate better on the questions I do know. The exam is worth 1000 points, and a passing score is 700. Again, stay positive and spend energy on questions about which you feel confident. You will not get every single question right.
A final thought: If you have the experience and you have studied this book well, you are well on your way to demonstrating your professionalism and expertise in protecting health information. You will soon join the vast and growing network of credentialed healthcare information protection professionals worldwide by earning the HCISPP. The credential itself continues to top the lists of desirable certifications in health IT and security. My best wishes for your success.