6

BETWEEN WAR AND PEACE
[W]ar will not be waged by armies but by groups whom today we call terrorists, guerillas, bandits and robbers, but who will undoubtedly hit on more formal titles to describe themselves.
—Martin van Creveld, The Transformation of War1
[T]here is a gray area between peace and war, and the struggle will be largely decided in that area.
—Richard M. Nixon, The Real Peace2
IN 1988,five years after the U.S. military’s walkover invasion of the Caribbean island of Grenada, and a year before the Berlin Wall crumbled, an obscure lecturer on information warfare announced at Beijing’s National Defense University that the battlefield of the future would be invisible. That battlefield would consist, he said, of “information space.” The phrases “information warfare” and “information space” elicited quizzical expressions among military officers and civilians alike, in China as well as in the United States, in the 1980s. Apart from top-secret practitioners of electronic spying, at which China was decidedly in the minor leagues, only a few cognoscenti had any idea what such phrases meant. Nonetheless, the lecturer insisted that the main factor in determining future victors would not be heavy armaments and massed armies, but information. And the objective in warfare would not be killing or occupying territory, but rather paralyzing the enemy’s military and financial computer networks and its telecommunications. How? By taking out the enemy’s power system. Control, not bloodshed, would be the goal.
The lecturer’s name was Dr. Shen Weiguang, and although he’s now regarded as the founding sage of Chinese information warfare theory, his views were then on the fringe in strategic circles in the Middle Kingdom. “Virus-infected microchips can be put in weapon systems,” he pointed out. “An arms manufacturer can be asked to write a virus into software, or a biological weapon can be embedded into the computer system of an enemy nation and then activated as needed. . . . Preparation for a military invasion can include hiding self-destructing microchips in systems designed for export.” Tactics like these, he said, could have profound strategic implications if carried out carefully and systematically. They could “destroy the enemy’s political, economic, and military information infrastructures, and, perhaps, even the information infrastructure for all of society.” If China could do that, Shen said, it could achieve the greatest of all strategic military objectives: It could “destroy the enemy’s will to launch a war or wage a war.”3
This was a startling and completely untested application of strategic theory in the new information age, but Shen was firmly within China’s ancient tradition of strategic thinking. Subduing the enemy without battle, the salient abandoned because no longer defensible, the manipulation of the enemy’s mind-set: these concepts are familiar to readers of Sun Tzu’s twenty-five-hundred-year-old Art of War. But Shen was now proposing to apply them in a new way. His military audience must have been skeptical. The People’s Liberation Army was Mao Tse-tung’s army, and Mao had founded it on long marches, popular uprisings, and human wave attacks by masses of peasant soldiers fed on millet. “People’s war” was bedrock PLA doctrine. “The richest source of power to wage war lies in the masses of the people,” Mao had taught. “[D]estruction of the enemy is the primary object of war . . . because only by destroying the enemy in large numbers can one effectively preserve oneself.”4
Against this history, the notion of “invisible battlefields” must have seemed bizarre. It was also overstated, as many all-too-visible battlefields have demonstrated in the intervening years. Shen had nevertheless grasped a fundamental truth, but it would take more than a lecture to awaken the PLA to what was happening to modern warfare.
Wake-Up Call
The wake-up shock arrived in January 1991. The previous August, the Iraqi army under Saddam Hussein had invaded Kuwait, installed a puppet regime, and begun looting the country. International condemnation quickly ensued, and in the following months the United States assembled a remarkable coalition of international military forces on the Saudi side of the Iraqi border. President George H. W. Bush issued an ultimatum to Saddam: Get out of Kuwait by January 15 or be attacked. Saddam was unmoved. On January 17, coalition aircraft began a thirty-eight-day bombing campaign as a prelude to invasion. The coalition then launched a ground war against the Iraqi army and Republican Guard—a fight regarded as more evenly matched than the air campaign. That was an illusion. By the time the Americans called a halt a mere one hundred hours later, the Iraqi army had suffered tens of thousands of casualties, and many had died. It had completely fallen apart. In contrast, the entire coalition suffered only about a thousand casualties, mostly wounded. Although Bush’s skill in quickly cobbling together an international coalition was of paramount political importance, the war itself was fundamentally an American affair. Indeed, none of the other coalition armies, even the British, were technologically equipped to fight on the same battlefield with the Americans. And the results were awesome. One much-quoted Chinese source summed it up this way: “The U.S.-led multinational force crushed 42 Iraqi divisions, and the Iraqi forces suffered 30,000 casualties and 80,000 prisoners; 3,847 tanks, 1,450 armored vehicles, and 2,917 artillery pieces were destroyed, while the U.S. forces only lost 184 people, but incurred the enormous cost of $61 billion.”5
The first Persian Gulf War made the Chinese sit up straight and pay attention. They had seen an Iraqi army of some 650,000 men (backed largely by Chinese tanks) utterly smashed in its own backyard, with unheard-of speed. They were shocked. If the Americans could do that to the Iraqis, what would stop them from destroying the PLA? From the Chinese point of view, the Gulf War “changed the world.”6 There would be no repeat of Chinese victories in 1950, when waves of Red Army troops swept across the Yalu River into Korea and forced Allied troops under General Douglas MacArthur into retreat. For decades to come, a head-to-head fight with the Americans would be suicide.
So, like other militaries around the world, the PLA went to school on what the Americans had done and how they did it. And what they saw was a global electronic system of communications, command, control, and intelligence—C3I—that took their breath away. Here’s an amazed Chinese account of how Patriot missile defenses worked during that war: “After a [support] satellite identified a target, an alarm was sent to a ground station in Australia, which was then sent to the central command post in Riyadh through the U.S. Cheyenne Mountain command post, after which the ‘Patriot’ operators were ordered to take their battle stations, all of which took place in the mere ninety-second alarm stage.”7 Computerized command and control meant almost instantaneous information, and the Chinese war planners began to understand that control of information was, as they put it, “the new strategic high ground”8 and the linchpin of the modern American way of war. Nor did the Chinese fail to notice the birth of a new age of “overnight” alliances, bringing to an end, some of them thought, to “the age of fixed-form alliances which had begun with the signing of the military alliance between Germany and Austria-Hungary in 1879.”9 Finally, the Chinese saw that war—and therefore national security—was a matter of economics. Who else but the Americans could spend $61 billion on a war halfway around the world with the world’s best armor and weapons supported by a network of satellites and far-flung ground stations? The Soviets had tried—and had gone bankrupt trying. By the end of 1991 the Soviet Union had collapsed without a shot being fired, a victim of American economic warfare—or, as we would say, of competition. If you could not compete with the Americans economically, you could not fight with them either—at least, not on a grand scale.
Meanwhile, an influential group of American thinkers was cheerfully reaching the same conclusion. But this group, which consisted principally of neoconservatives, went further. In their view, the fog of war, the inevitable confusion that envelops commanders and soldiers alike in the heat and confusion of battle, had been permanently dissipated. With the world’s best C3I, perfect, total situational awareness during battle was now achievable. No nation, they concluded, could ever again challenge the United States militarily. This assessment had profound implications for the future structure of American military forces, and it was an important factor in making U.S. forces lighter, more flexible, and more technologically dependent. We could begin to move away from a heavy army, heavy equipment, and heavy but immobile artillery.
Donald Rumsfeld was among the group that saw this possibility, and when he again became defense secretary under President George W. Bush, he pushed this agenda hard. But like any really important idea, when pushed too far it led to serious mistakes. Victory may teach lessons, but it also breeds self-satisfaction. Defeat and fear are better instructors. So as the victorious Americans were preening over what they had done, the Chinese were drawing other conclusions. If the Americans could not be directly confronted militarily, at least for another twenty-five years, who said China’s challenge to the United States had to come as a direct military confrontation? There were other ways to weaken the beast. China would rise economically and assert itself diplomatically. It would become an innovator, not a copier (like the Japanese). And if China needed technology faster than it could invent it, China could steal it—electronically. As for the U.S. military, C3I might be its greatest strength, but the Chinese saw that C3I was fragile, so it was also the American military’s point of greatest vulnerability. Just as control of information had been the key to the American victory, paralyzing or corrupting information systems would be the key to preventing American victory. If the U.S. military could be made suddenly blind and deaf, it would be a useless instrument. The fog of war had not disappeared permanently. On the contrary, with the right preparation it could be reimposed at will. This would be information warfare. Dr. Shen had been right all along.
Eight years later, 1999
NATO is conducting bombing operations against Serbian forces that were seizing large parts of Kosovo and systematically killing Albanians and Muslims. James Rubin, the State Department spokesman, is explaining why NATO, which had the power to take down the Internet in Serbia and Kosovo, was keeping it open: “Full and open access to the Internet,” he proclaims, “can only help the Serbian people know the ugly truth about the atrocities and crimes against humanity being perpetrated in Kosovo by the Milosevic regime.”10 Translation: We can keep  from using the Internet by taking it down, but if we do that, then we won’t be able to use it either. And we need it.
from using the Internet by taking it down, but if we do that, then we won’t be able to use it either. And we need it.
The Kosovo conflict is sometimes described as the first war on the Internet, but Kosovo did not involve a battle to take the Internet down or control its use; the United States decided not to do that. Rather, the conflict involved a struggle for hearts and minds in which the Internet was the main tool. Governments and nongovernment organizations competed fiercely on the Internet to put out their own stories and attack one another. Hackers and activists used it to assail the Belgrade regime or NATO—or both—and to deface each other’s Web sites. Individuals used it to describe the horrors they had been through—all for an international audience.11 In this sense Kosovo was merely a new chapter in the ancient tradition of wartime propaganda, but with one very big difference. The mass propaganda machines of the twentieth century had been perfected in the era of radio, whose potential the Nazis had immediately grasped, and which they exploited brilliantly. Mass radio, and later television, were easily controlled by totalitarian regimes. You broadcast from one place that was easy to find, using equipment that was difficult to hide, and your point of view was disseminated to the world. The input was centralized and active, the listeners dispersed and passive. The Internet was different. Users were dispersed but they were not passive; input came from everywhere. The Internet was becoming the chief tool of mass communications, especially when radio and TV stations could be destroyed or silenced. If NATO wanted to keep the Net open, it had no choice but to let its enemies use it too. And they did. Not only were the Serbs using the Net to communicate; they were also using it to harass their enemies. Hackers in Belgrade, for example, sent streams of ping commands to NATO’s Web servers in an elementary denial-of-service attack—a tactic first used a year earlier by Tamil insurgents in Sri Lanka. (“We are the Internet Black Tigers and we’re doing this to disrupt your communications.”12) In this kind of war, where was the information advantage? Nor could NATO reply in kind, because so long as NATO wanted to use the Internet too, its forces had no targets to hit. Here was an asymmetric advantage to the weak side.
Meanwhile, a version of war fog was creeping in through the backdoor, unnoticed by NATO air commanders. NATO battle-damage analysts did not figure it out until later, but the Serbs were impressively adept at spoofing juicy bombing targets with decoy tanks and aircraft, which they made using painted canvas and wooden frames. Some of the decoys even had heat sources to attract heat-seeking missiles from NATO aircraft.13 This was a low-tech deception triumph against the world’s most high-tech aircraft. In the classical fog of war you knew when you were confused. Here, in contrast, deception was masquerading as perfect clarity, aided by NATO’s wonderfully self-convincing real-time aerial video of blown-up matériel. Only a systematic study of after-action photographs of the supposedly destroyed armor would later disclose the truth.
The Chinese watched all of this, fascinated.14 As a leading PLA source on information warfare put it, “[I]n spite of NATO’s near total information superiority, its battlespace awareness was manipulated by the Serbian armed forces” repeatedly and effectively, and “Serbian civilian and military personnel were able to use civilian telephone and radio links to pass military information.”15 At the same time, the American information masters were finding that too much information could lead to the same result as too little. Admiral James Ellis, the American commander in Kosovo, called it “information saturation.” And as every meteorologist knows, when the atmosphere becomes saturated, the result is fog.16
The United States and its NATO allies achieved some of their aims during the Kosovo campaign, but they did not succeed in removing 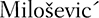 from power. The Balkan forests and mountains were not the Iraqi desert, in which destroying massed armor had been like shooting fish in a barrel for unmolested allied aircraft. And Serbs were not Iraqis. Culture and terrain still mattered in war. In spite of overwhelming technical disadvantages, the Serbs continued to communicate effectively on the Internet during the conflict, and their low-tech deception campaign had been enormously successful in distracting coalition aircraft from high-value targets, inducing them instead to waste tons of expensive ordnance on worthless decoys.
from power. The Balkan forests and mountains were not the Iraqi desert, in which destroying massed armor had been like shooting fish in a barrel for unmolested allied aircraft. And Serbs were not Iraqis. Culture and terrain still mattered in war. In spite of overwhelming technical disadvantages, the Serbs continued to communicate effectively on the Internet during the conflict, and their low-tech deception campaign had been enormously successful in distracting coalition aircraft from high-value targets, inducing them instead to waste tons of expensive ordnance on worthless decoys.
Information dominance remains a bedrock principle in both U.S. and Chinese war-fighting doctrine, essential to establishing naval and air superiority.17 In Kosovo, however, the Chinese saw the issue through the other end of the telescope. By corrupting NATO’s information flow, the Serbs had significantly reduced the importance of air superiority. Here was an example in information space of a venerable concept in Chinese strategic thought: the defeat of the superior by the inferior. But the Chinese were not interested in partial success and canvas decoys. They saw bigger possibilities.
“The War God’s Face Has Become Indistinct”18
If the First Gulf War made PLA military planners pay close attention to American battle prowess, the appearance in Beijing in 1999 of a volume called Unrestricted Warfare returned the favor. This book gave Pentagon strategists an alarming window into Chinese thinking about the nature of their engagement with the Western world, particularly the United States. The authors were two senior PLA colonels from China’s rising military elite, Qiao Liang and Wang Xiangsui, whose work obviously had official sanction.19 Qiao and Wang argued that China should use all means, armed and unarmed, military and nonmilitary, and lethal and nonlethal, to compel the enemy to accept its interests.20 That sounds ominous—it was meant to sound ominous—but the thesis is actually pretty ordinary. How else and why else does any nation use its military and nonmilitary levers of power? But the authors’ shrewd and brash analysis of the impact of technology on warfare and communications since the first Gulf War, their embrace of electronic operations, and their discussion of virtually all international engagement in the vocabulary of war gave their work a sharp edge among the small cadre of professionals who think about such things.
Three years later the alarm bells grew louder when an obscure publisher in Panama published an English translation of the book with the subtitle China’s Master Plan to Destroy America, along with a color cover photo of the burning towers of the World Trade Center.21 Those embellishments distorted a work that was less bellicose but more deeply threatening than images of 9/11 could convey. The authors were also highly intelligent and displayed an impressive familiarity with Western sources—literary and philosophical as well as military. The Prussian Carl von Clausewitz, and Mao after him, had called war “politics by other means.” Qiao and Wang seemed to be saying the reverse: Politics—and economics and communications and everything else—was war by other means. And while von Clausewitz had preached the doctrine of the decisive battle, Qiao and Wang said there would be no more decisive battles. Henceforth, they said (paraphrasing Eliot), when empires perished they would crumble like the Soviet Union, “not with a rumble, but a snicker.”22
The agents of imperial demise would certainly be backed up by military power—the Chinese have never wavered in that view—but the agents would be many and varied: economic, legal, public relations—and electronic sabotage. The success of George Soros’s then recent speculative attack on the currencies of several East Asian nations impressed but appalled the Chinese (who have pegged their own currency to the dollar in part to discourage such tactics). Soros and his traders had driven down the value of these currencies, forcing them into line with their true worth! But that point was lost on Qiao and Wang, as it was lost on noncapitalists (i.e., most people) around the world, who saw only economic chaos in Asia created by Western capitalists. To the authors of Unrestricted Warfare, these attacks were a form of economic terrorism on par with bin Laden’s bombings of U.S. embassies in East Africa, Aum Shinrikyo’s sarin gas attack in the Tokyo subway, and the depredations of malicious hackers on the Internet. They “represent semi-warfare, quasi-warfare, and sub-warfare, that is, the embryonic form of another kind of warfare.” Such warfare knows no boundaries, and against it, borders have no meaning.23
This was the kind of warfare that Qiao and Wang predicted and advocated. The American military could be stopped in its tracks because its command and control rode on porous networks that could be penetrated, corrupted, or brought down altogether. Only arrogance could make Americans think that their seamless electronic brilliance had brought an end to the fog of war, for as any grade-school dialectician knows, every capability calls into being its countercapability. Military commanders and strategists (whether Chinese or American) who could think only in terms of heat, blast, and fragmentation would be left in the past—quietly outgunned, one might say, by the nonmilitary war actions happening around them. “[T]hose who only understand an imposing array of troops on the battlefield and who think that war is just killing people,” wrote Qiao and Wang, “. . . have been unable to understand this point.”24
From now on, according to the two Chinese colonels, it would be “difficult for the military sphere to serve as the automatic dominant sphere in every war. War will be conducted in nonwar spheres.”25 Using financial instruments to attack a nation’s currency could be seen as a form of battle. A CNN broadcast that showed the naked corpse of an American solider being dragged through the streets of Mogadishu could affect America’s determination to fight. In effect, CNN was conducting a nonmilitary action with warlike results. Nonwar actions like these, the colonels said, were what future war would be about. It would transcend all boundaries and limits. It would be, in short, “unrestricted warfare.”26 Theirs was not a Hitlerian vision of total war, however. Bloodshed and lebensraum were not its goals. “‘Although ancient states were great,’” the colonels warned, quoting the ancient Chinese strategist Sima Rangju, “‘they inevitably perished when they were fond of war.’”27 Could Americans understand these things? Qiao and Wang thought not. Americans, they said, only understand technology.
THE POSSIBILITIES FOR cyberconflict went on prime-time display in April 2007, in the tiny Baltic republic of Estonia. The Estonians had decided to remove a monument to the Russian war dead of World War II from the center of their capital, Tallinn, and move it to a military cemetery. To them the Russians weren’t liberators from the Nazis; they were just the next occupiers. Russian nationalists were insulted; Russia had lost tens of millions to combat, massacres, disease, and starvation in the war against the Nazis, and the perceived insult to their war dead produced widespread outrage. The Russian-speaking population in Estonia went on a two-day rampage. At the same time, Estonian governmental and financial institutions were hammered with a distributed denial-of-service attack from thousands of captive computers organized into botnets. Estonian banks were shut down, remittances from abroad didn’t arrive, and government departments came to a standstill. In self-defense, the big credit card issuers shut down their networks, which made the situation worse. Not surprisingly, many of these attacks could be traced to Russia, some perhaps to the Kremlin. Estonia closed its electronic borders and began adding redundant capacity to their external connections as fast as they could, but the attacks continued for weeks.28
The Russian government took a “who, me?” approach to international accusations of complicity while refusing to cooperate in an investigation that could have proven who was involved. The following year an ethnic Russian Estonian was convicted of participating in the attack and, according to a report commissioned by the U.S. Air Force, “[c]onsiderable evidence suggests that he had help from parts of the Russian mafiya, which helped organize the hijacked computers for him, but there is still no solid evidence that the Russian state was involved.”29 That the Kremlin was complicit in these attacks seemed obvious, but in what ways? Did the government simply turn a blind eye? Were the attacks perpetrated by outraged Russian nationalists or by Russian criminal organizations that deal in botnet scams day in and day out? Did the Russian government at least implicitly encourage the attacks? Were the criminals in some cases working at arm’s length for the Russian security services? The answer to all of these questions is probably yes—but to what degree we don’t know. Very likely what began as a spontaneous and disorganized affair received state encouragement and cover, but so long as the Kremlin refuses to permit an investigation, nobody can prove it.
Was this “war”? In the law and culture of the West, war and peace are an on-off toggle switch. Peace is what you have when you don’t have war, and wars are declared. There is no middle ground.30 Such dualism is naive—and never more so than in the period since the end of World War II. Since 1945 the U.S. military has fought three conventional wars for a cumulative period of less than four years. In the same period it has engaged in counterinsurgency operations lasting a cumulative twenty-three years.31 In Estonia the war/not war inquiry was not an idle question. Estonia was by then a member of NATO, and some in Tallinn were calling for the government to invoke Article V of the NATO treaty, which states that an attack on one NATO member is an attack on all of them. NATO members, including the United States, glanced over the brink of this cliff and said no. And there must have been at least three good reasons. First, declaring war means you must go to war. No American president could afford to declare war and then fail to make war. Nor was there a rule that a conflict that began in cyberspace had to remain there. American doctrine states that the United States is not obliged to respond in kind to an attack: cyber for cyber, missile for missile. We reserve the right to respond in whatever manner we think fit. A cyberwar could therefore have turned hot quickly. Second, the attacks had produced no physical damage and no death. Calling such a cyberattack “war” would therefore have lowered the threshold definition dramatically. And third, when you declare war, you must declare it against somebody specific. In this case, if the cyberattacks had produced physical damage and death, the evidence of Russian involvement might have sufficed, but the precedent of declaring war in a case with ambiguous attribution, when the identity of an attacker can be spoofed, could not have been appealing.
In the end, the cyberattack on Estonia did not produce war among states, but it did result in NATO beginning to pay lots of attention to cybervulnerabilities.32 Nevertheless many Western commentators began to refer to Estonia as the “first cyber war.” But that’s not how the Chinese saw it. They remembered earlier U.S. cyberoperations against Iraqi networks on the eve of the first Gulf War, and they knew very well that they had themselves turned a blind eye, much as the Russians did, toward semiorganized attacks by their own nationalistic hackers against anti-Chinese targets in Vietnam, Indonesia, and elsewhere, beginning as early as 1997.33
The Chinese see conflict on all fronts—but they do not see conflict as inconsistent with cooperation where interests intersect. They refer to conflict as “warfare” or “subwarfare” in the international arena as readily as Americans refer to various domestic programs as “wars” against this, that, or the other undesirable social condition. In contrast, the rigidity of American doctrinal dualism—either we’re at war or we’re enjoying peace—crudely simplifies our understanding of international relations. To the Chinese, it must seem childish. But within the American national security establishment, the vocabulary of conflict is also warlike in the absence of declared war: We are stocked with self-described cyberwarriors who for the most part are not soldiers in the usual sense but geeks employed by a military or intelligence organization. Alvin and Heidi Toffler foresaw this happening as early as 1993, when they wrote, “If the tools of warfare are no longer tanks and artillery, but rather computer viruses and microrobots, then we can no longer say that nations are the only armed groups or that soldiers are the only ones in possession of the tools of war.”34 This blurring creates genuine confusion about who’s a soldier and who’s not, and this confusion is both substantive and legal, since a nonsoldier engaged in war is an irregular combatant and not entitled to the protections of the Geneva Conventions.
War talk has changed in other ways too. As Colonels Qiao and Wang see it, “All of the prevailing concepts about the breadth, depth and height of the operational space already appear to be old-fashioned and obsolete.”35 Strategists everywhere have therefore stopped talking about “battlefields.” They now talk about “battlespace,” which has created confusion about who’s in that space and where that space is. As the colonels point out, this confusion is deepened with the dissolution of the boundary between military and civilian technology. In their view, the battlespace is now everywhere.36
“Water does not have a constant shape.”37
The Chinese are forcing Mao’s PLA into the twenty-first century as fast as they can, and have launched the most ambitious naval modernization program since the PRC was founded in 1949.38 Yet the principle of the “people’s war” remains a pillar of military doctrine as well as national mythology, and they have not abandoned it.39 But instead of embodying this principle in masses of poorly armed peasants, the Chinese now see it living in legions of hackers ready to defend the nation in cyberspace. “In the high-tech local war which we will face in the future,” writes a prominent military strategist who enjoys official approval, “the role of the masses” looms large, and the “great power of the people’s war” will be unleashed through military and nonmilitary means in all aspects of life.40 As applied in cyberspace, however, this was a doctrine chasing the reality of hacker life in China. In 1997 there were just seven Chinese hacker Web sites, all of them rudimentary, all of them with content copied from abroad. That began to change when anti-Chinese riots broke out in Indonesia in 1998, and nationalistic hacker groups like the Green Army and the Red Hacker Alliance retaliated against Indonesian networks.41 All of a sudden, patriotic hacker groups were blooming like a hundred flowers all over China.
In May 1999 the Red Hacker movement got a huge boost of energy when NATO bombed the Chinese embassy in Belgrade during the Kosovo War.42 Red Hackers were outraged and quickly launched a powerful DDOS attack that shut down the White House Web site for three days.43 “Never has such an emotional impact on a nation occurred since the advent of the Internet,” declared one Chinese blogger three days later. “Even though I was just facing a computer monitor, I could feel the patriotic spirit of my friends on the Internet.” Another pleaded, “Hackers, who love and protect the motherland, please teach me how to hack the Yanks. I hope you will accept me as a follower so that I can make my contribution to the motherland.” The outpouring of electronic patriotism in the face of national injury was overwhelming. New members of another hacker group, the Chinese Eagle Union, solemnly pledged “to put the interests of the Chinese nation above everything else” and “to do everything in my power to make the Chinese rise up.”44 No Western country has experienced such a spontaneous wave of unofficial support from a self-identified cyber national guard, and a prominent Chinese hacker explained why: “Unlike our Western counterparts, most of who [sic] are individualists or anarchists, Chinese hackers tend to get more involved with politics because most of them are young, passionate and patriotic.”45
The midair collision two years later over the South China Sea between a U.S. Navy EP-3 reconnaissance plane and a PLA fighter—the latter piloted by a cowboy whose risky antics were well-known to our crews—set off another round of electronic skirmishes. Never mind that our plane was in international airspace or that the collision was caused by the recklessness of the Chinese pilot; the Red Hacker community was enraged. Members of these groups are not controlled by the central government, which from time to time has arrested some of them for criminal behavior. Yet the government whips them into a frenzy when it suits its purposes, with patriotic injunctions to counter “foreign forces subverting China via the Internet,” and so on.46 The PRC recruits its own network techies through hacker Web sites to harness this energy.47
Between these amorphous hacker groups and the PLA’s network professionals lies a murky middle layer whose shape, not surprisingly, is indistinct, but whose mission—information warfare (IW)—is not. In 1998 the PRC launched what may have been its first experiment with a cybermilitia: a forty-person unit in a state-owned enterprise in Datong City, Shanxi Province, which had a rich talent pool drawn from some twenty universities, institutes, and companies.48 Militias are neither official government cadres nor freelance hackers. They operate in ambiguous space, connected to one or another government office by a loose string. A twitch of a government finger tightens the string, either to restrain or direct an operation. The PLA has been actively creating IW militias since about 2002, recruiting from universities, research institutes, and commercial IT companies, especially telecom firms. Some accounts call these cadres an “active reserve,” comprising eight million network operators under direct state control.49 We can’t count on the accuracy of these estimates, but we do know that such cadres receive government funding, work in government-affiliated institutions or front companies, and are subject to some degree of government control. We also know that China’s Academy of Military Science has endorsed the formation of cybermilitias and “directed the PLA to make the creation of such units a priority.” In some cases they undergo light military indoctrination.50
The Chinese attacks on Google in late 2009 allowed us to glimpse how some of these militia units work.51 The attacks were based on a previously unknown vulnerability in Microsoft’s Internet Explorer that had been mentioned in Chinese language publications. The attacks themselves were pulled off by a combination of security professionals, contractors, and consultants, and at least some of them were routed through servers at two Chinese educational institutions. Routing an attack through an educational institution makes attribution especially difficult, because the user of any particular machine is often impossible to identify, and security practices at universities are notoriously weak. As we saw in chapter 3, one of the institutions was Lanxiang Vocational School. Lanxiang is particularly close to the government. It actually helped create one of China’s principal censorship tools, which is known as the Great Firewall of China, and many of Lanxiang’s graduates end up as network operators in the PLA. Of course both Lanxiang and Jiao Tong denied any involvement—which may simply mean (if it’s true) that the academic administration was not involved. Could a group of students or faculty have organized these attacks without the knowledge of the schools’ administrations? Perhaps. Was it technically possible for third-country actors to run these attacks through China? Yes, if they also had cyberwarriors fluent in Chinese who had combed Chinese language journals in search of the code involved. In that case, however, the Chinese had the forensic tools to trace the attacks backward from Chinese servers to their source. Yet the PRC kept mum. And why would a third-country actor have used the attacks to spy on internal Chinese dissidents—which is what happened? As we saw earlier, we now have other intelligence that confirms the attacks were authorized by high officials of the Chinese state—but conducted at arm’s length from the government.
The Chinese never tire of criticizing Americans’ lack of subtlety, even as they praise us for our flexibility, adaptability, and ingenuity. “Most Americans,” Shen said dismissively, “see IW as a way of fighting. This is because they approach IW mainly on a technical or purely military level.” Chinese thinkers find this tendency “childish.”52 No doubt the Phrygian elders similarly thought Alexander childish when, according to legend, he was unable to untie the Gordian knot. Alexander’s method of resolving the conundrum—he cut the knot with his sword—was certainly not subtle, but it proved entirely effective. The American dislike of subtlety and our bias toward technical and military solutions are undeniable; so is our difficulty with dialectics and other modes of nonlinear thought. Airs of intellectual superiority are the first refuge of an old culture resenting the new, however; and military officers who see inevitable conflict between China and the United States are probably more common there than here. Chinese and American military doctrines regarding cyberspace are today quite similar,53 though our idioms differ. As we’ve seen, the Chinese often speak of war when referring to any point on the continuum from economic competition to armed conflict. Americans are careful (for legal as well as operational reasons) to distinguish computer network exploitation from computer network attacks. Exploitation is espionage; attacks are attempts to degrade or paralyze an adversary’s information systems. The Chinese speak of “informationalized” warfare, whereas Americans speak of “netcentric” warfare.54 Both mean essentially the same thing. Both seek “information superiority . . . capable of putting disparity in the enemy commander’s mind between reality and his perception of reality.”55 Both seek to employ “the core capabilities of influence operations, electronic warfare operations, network warfare operations, in concert with specified integrated control enablers, to influence, disrupt, corrupt or usurp adversarial human and automated decision making while protecting our own.”56
So why did Unrestricted Warfare create a furor among American military thinkers when it appeared in 1999? Because it made plain that the Chinese saw information warfare as a means of disruption, whereas military planners in Washington in the 1990s saw nothing but unchallenged information superiority and unobstructed operations long into the future. Americans saw their superiority as so great that we could enter an era of “not fighting,” because no one would challenge us. The Chinese saw instead a new way of fighting. According to Timothy Thomas of the U.S. Foreign Military Studies Office, the West hoped notions of not fighting would lead to clean information warfare rules to play by—“no casualties, just a victory from a stand-off position.” Unrestricted War upset this thinking. It showed that some in China might actually prefer conflict that wasn’t so clean. In information control, Americans had seen efficiency and order, command and control. The Chinese saw that too, but they also saw the value of chaos and asymmetric advantage. As Colonel Qiao put it, “[T]he stronger side is never the first to break the rules and use irregular methods.”57 This sounded like a bald threat to strike first in an electronic war.
In Chinese thought, asymmetric information warfare holds the potential to maneuver the United States—not into open traditional warfare, but rather into inaction. China has made no secret of how it would fight the United States, if it came to a fight. PLA strategy calls for combining network and electronic warfare against an adversary’s information systems at the start of any conflict.58 They would target the communication and control nodes and so lead us to distrust our own systems59 and undermine our decision making, operations, and morale. Electricity, transportation, and financial networks would be punched out. Blindness and paralysis would follow—at least, that would be the plan.60 The PLA lays special emphasis on “public opinion war” and “psychological war.”61 Their goals are to “force the enemy side to regard their goal as our goal” and to “force the opponent to give up the will to resist and end the confrontation.”62 All this would be coordinated with hard power,63 until finally the enemy—that would be us—would be “forced to sign a dishonorable peace.”64
Let’s see how that strategy might play out.