Chapter 21
Protecting Windows
Get ready to . . .
⇒ Understand Computer Security
⇒ Understand Windows Update Options
⇒ Run Windows Update
⇒ Set Up Trusted and Restricted Websites
⇒ Enable Windows Firewall
⇒ Change Your Password
⇒ Allow Firewall Exceptions
Your computer contains software and files that can be damaged in several different ways. One major source of damage is from malicious attacks that are delivered via the Internet. Some people create damaging programs called viruses specifically designed to get into your computer’s hard drive and destroy or scramble data. Companies might download adware on your computer, which causes pop-up ads to appear, slowing down your computer’s performance. Spyware is another form of malicious software that you might download by clicking a link or opening a file attachment; spyware sits on your computer and tracks your activities, whether for use by a legitimate company in selling products to you or by a criminal element to steal your identity.
Microsoft provides security features within Windows 8 that help to keep your computer and information safe, whether you’re at home or travelling with a laptop computer.
In this chapter, I introduce you to the major concepts of computer security and cover Windows 8 security features that allow you to do the following:
⇒ Run periodic updates to Windows, which install security solutions and patches (essentially, patches fix problems) to the software.
⇒ Enable a firewall, which is a security feature that keeps your computer safe from outsiders and helps you avoid several kinds of attacks on your data.
⇒ Change the password used to protect your computer from others.
⇒ Protect yourself against spyware.
Understand Computer Security
Every day you carry around a wallet full of cash and credit cards, and you take certain measures to protect its contents. Your computer also contains valuable items in the form of data, and it’s just as important that you protect it from thieves and damage. Your computer comes with an operating system (such as Microsoft Windows) preinstalled, and that operating system has security features to protect your valuable data. Sometimes the operating system has flaws or new threats emerge, and you need to get an update to keep your computer secure.
In addition, as you use your computer you’re exposing it to dangerous conditions and situations that you have to guard against. Threats to your computer security can come from a file you copy from a disc you insert into your computer, but most of the time the danger is from a program that you downloaded from the Internet. These downloads can happen when you click a link, open an attachment in an e-mail, or download a piece of software without realizing that the malware is attached to it.
You can use Windows security tools such as Windows Defender, or third-party antivirus or antispyware programs (see Figure 21-1) to protect your computer from dangerous computer programs collectively known as malware. See Chapter 13 for more detail about threats and protections from malware.

Figure 21-1
Understand Windows Update Options
When a new operating system such as Windows 8 is released, it has been thoroughly tested; however, when the product is in general use, the manufacturer begins to find a few problems or security gaps that it couldn’t anticipate. For that reason, companies such as Microsoft release updates to their software, both to fix those problems and deal with new threats to computers that appear after the software release.
Windows Update is a tool you can use to make sure your computer has the most up-to-date security measures in place. You can set Windows Update to work in a few different ways from the Control Panel by choosing System and Security⇒Windows Update⇒Change Settings. In the resulting dialog box (see Figure 21-2), click the Important Updates drop-down list and you find these settings:
⇒ Install Updates Automatically: With this setting, Windows Update starts at a time of day you specify, but your computer must be on for it to work. If you’ve turned off your computer, the automatic update will start when you next turn on your computer, and it might shut down your computer in the middle of your work to complete the installation.
⇒ Download Updates but Let Me Choose Whether to Install Them: You can set up Windows Update to download updates and have Windows notify you (through a little pop-up message on your taskbar) when they’re available, but you get to decide when the updates are installed and when your computer reboots (turns off and then on) to complete the installation. This is my preferred setting because I have control and won’t be caught unawares by a computer reboot.
⇒ Check for Updates but Let Me Choose Whether to Download and Install Them: With this setting, you neither download nor install updates until you say so, but Windows notifies you that new updates are available.
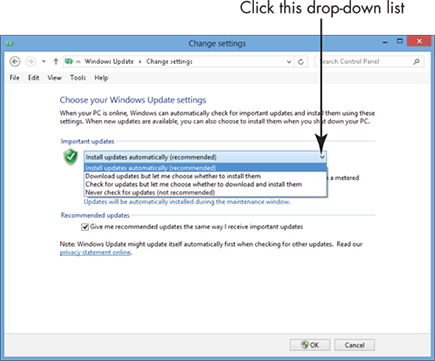
Figure 21-2
⇒ Never Check for Updates: You can stop Windows from checking for updates and check for them yourself, manually (see the following task). This puts your computer at a bit more risk, but it’s useful for you to know how to perform a manual update. For instance, you might discover that you can’t proceed with a certain task (such printing a document or using French in your correspondence) until you run a specific update.
Run Windows Update
1. Press Win+I and click Change PC Settings. In the PC Settings window, click Windows Update.
2. In the resulting window, as shown in Figure 21-3, click the Check for Updates Now link to see all updates.
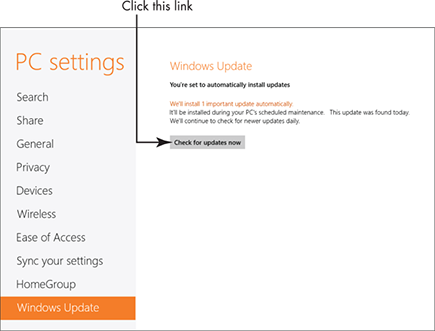
Figure 21-3
3. In the following window, which shows the available updates (see Figure 21-4), click to select available critical or optional updates that you want to install. Then click the Install button.
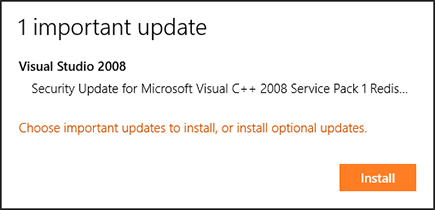
Figure 21-4
4. A window appears, showing the progress of your installation. When the installation is complete, you might get a message telling you that it’s a good idea to restart your computer to complete the installation. Click Restart Now.
 If you keep the Windows Update to Never Check for Updates setting selected, it’s very important that you perform a manual update on a regular basis.
If you keep the Windows Update to Never Check for Updates setting selected, it’s very important that you perform a manual update on a regular basis.
 Running Windows Update either automatically or manually on a regular basis ensures that you get the latest security updates to the operating system, and it’s a good idea to stay current.
Running Windows Update either automatically or manually on a regular basis ensures that you get the latest security updates to the operating system, and it’s a good idea to stay current.
Set Up Trusted and Restricted Websites
1. You can set up Internet Explorer to recognize websites you trust and those you don’t want IE to take you to. Click the Internet Explorer icon in the desktop taskbar to start your browser.
2. Choose Tools⇒Internet Options.
3. In the Internet Options dialog box (see Figure 21-5), click the Security tab.
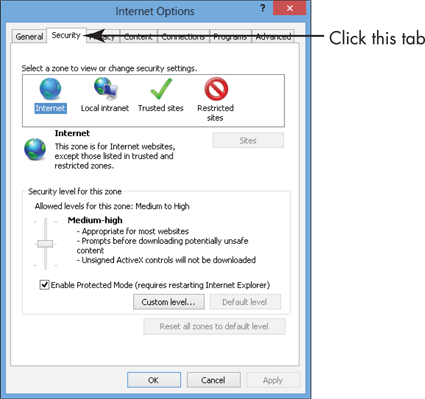
Figure 21-5
4. Click the Trusted Sites icon and then click the Sites button.
5. In the resulting Trusted Sites dialog box, enter a URL in the Add This Web Site to the Zone text box for a website you want to allow your computer to access. If you want any locations for a particular company, such as Microsoft, to be allowed, you can use a wild card in the form of an asterisk, as shown in Figure 21-6.
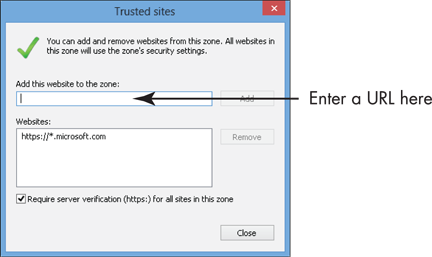
Figure 21-6
6. Click Add to add the site to the list of websites.
7. Repeat Steps 3–6 to add more sites.
8. When you’re done, click Close and then click OK to close the Internet Options dialog box.
9. Repeat Steps 1–8, clicking the Restricted Sites icon rather than Trusted Sites (in Step 4) to designate sites that you don’t want your computer to access.
 If the Require Server Verification (https:) for All Sites in This Zone check box is selected in the Trusted Sites dialog box, any trusted site you add must use the https prefix, which indicates that the site has a secure connection that can protect you during online payment transactions.
If the Require Server Verification (https:) for All Sites in This Zone check box is selected in the Trusted Sites dialog box, any trusted site you add must use the https prefix, which indicates that the site has a secure connection that can protect you during online payment transactions.
 You can establish a Privacy setting on the Privacy tab of the Internet Options dialog box to control which sites are allowed to download cookies to your computer. Cookies are tiny files that a site uses to track your online activity and recognize you when you return to the source site. Trusted sites are sites that you allow to download cookies to your computer even though the privacy setting you’ve made might not allow any other sites to do so. Restricted sites, on the other hand, can never download cookies to your computer, no matter what your privacy setting is. See Chapter 13 for more information about the options on the Privacy tab.
You can establish a Privacy setting on the Privacy tab of the Internet Options dialog box to control which sites are allowed to download cookies to your computer. Cookies are tiny files that a site uses to track your online activity and recognize you when you return to the source site. Trusted sites are sites that you allow to download cookies to your computer even though the privacy setting you’ve made might not allow any other sites to do so. Restricted sites, on the other hand, can never download cookies to your computer, no matter what your privacy setting is. See Chapter 13 for more information about the options on the Privacy tab.
Enable Windows Firewall
1. A firewall keeps outsiders from accessing your computer via an Internet connection. Begin typing Control Panel from the Start screen and click Control Panel in the search results.
2. Click⇒System and Security⇒Windows Firewall.
3. In the Windows Firewall window that appears (see Figure 21-7), make sure that Windows Firewall is On. If it isn’t, click the Turn Windows Firewall On or Off link in the left pane of the window.
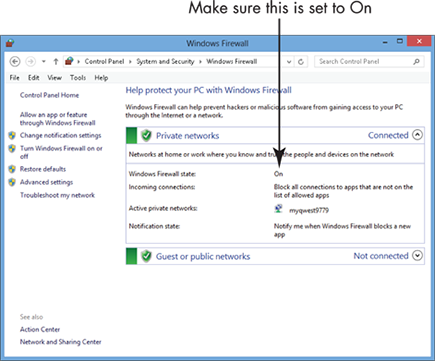
Figure 21-7
4. In the resulting Customize Settings window (see Figure 21-8), select the Turn on Windows Firewall radio button for Private Networks (such as your home network) and/or Public Networks (such as a coffee shop) and then click OK.
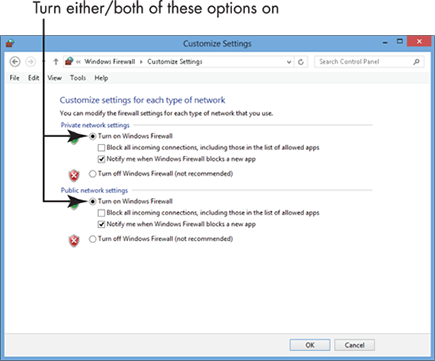
Figure 21-8
5. Click the Close button to close Windows Security Center and the Control Panel.
 A firewall is a program that protects your computer from the outside world. This is generally a good thing, unless you use a Virtual Private Network (VPN), often used by corporations. Using a firewall with a VPN can restrict you from sharing files and using some other VPN features.
A firewall is a program that protects your computer from the outside world. This is generally a good thing, unless you use a Virtual Private Network (VPN), often used by corporations. Using a firewall with a VPN can restrict you from sharing files and using some other VPN features.
 Antivirus and security software programs may offer their own firewall protection and may display a message asking if you want to switch. Check their features against Windows and then decide, but usually most firewall features are comparable. The important thing is to have one activated.
Antivirus and security software programs may offer their own firewall protection and may display a message asking if you want to switch. Check their features against Windows and then decide, but usually most firewall features are comparable. The important thing is to have one activated.
Change Your Password
1. If you log into Windows using an online account, your password is the password associated with your Windows Live account. If you set up a local account not associated with an online account, you create a password when you set up the account. To change a password, press Win+I, click Change PC Settings, and then click Users.
2. In the Users panel, shown in Figure 21-9, click the Change Your Password link.

Figure 21-9
3. In the Change Your Password screen, shown in Figure 21-10, enter your current password, and then enter the new password and confirm it.
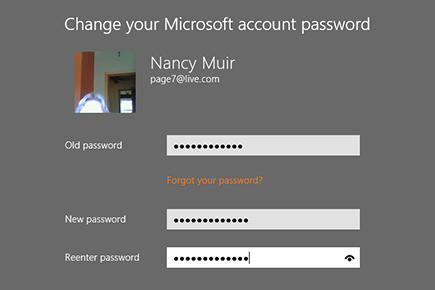
Figure 21-10
4. Click Next.
5. Click Finish.
 You can use a similar procedure by clicking Change PIN in the PC User Settings to assign a four-character PIN for logging into your account, rather than a password. PINs are typically shorter than passwords, so they save you time if you log on and off Windows during the day.
You can use a similar procedure by clicking Change PIN in the PC User Settings to assign a four-character PIN for logging into your account, rather than a password. PINs are typically shorter than passwords, so they save you time if you log on and off Windows during the day.
 After you create a password, you can go to the PC Settings window and change it at any time by clicking Change Your Password.
After you create a password, you can go to the PC Settings window and change it at any time by clicking Change Your Password.
Allow Firewall Exceptions
1. When you have a firewall active you can allow certain programs to communicate through that firewall. For example, you might want to allow live apps such as Weather or Video to send information or content to your computer. Begin typing Control Panel and then click the Control Panel app in the results. Click System and Security.
2. In the resulting System and Security window (see Figure 21-11), click Windows Firewall and then click Allow an App through Windows Firewall.
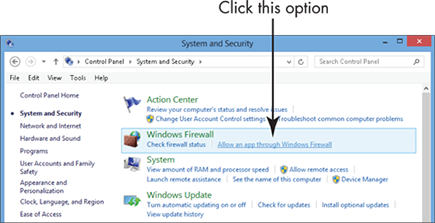
Figure 21-11
3. In the Allowed Apps window that appears (see Figure 21-12), click the Change Settings button, and then select the check box for apps on your computer that you want to allow to communicate over the Internet without being stopped by Firewall.
4. Click the Private and Public check box to narrow down whether you want just networks that are secure to allow this communication, or also public and nonsecure networks to do so.
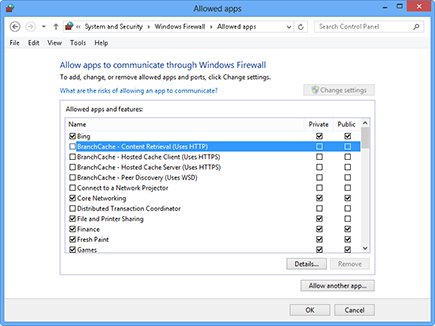
Figure 21-12
5. Click OK.
 If you allow apps to communicate across your firewall, it’s very important that you do have antivirus and antispyware software installed on your computer, and that you run updates to them on a regular basis. These types of programs help you avoid downloading malware to your computer that could cause advertising pop-ups, slow your computer’s performance, damage computer files, or even track your keystrokes as you type to steal your identity and more. If you don’t want to pay for such a program, consider a free solution such as Spyware Terminator (
If you allow apps to communicate across your firewall, it’s very important that you do have antivirus and antispyware software installed on your computer, and that you run updates to them on a regular basis. These types of programs help you avoid downloading malware to your computer that could cause advertising pop-ups, slow your computer’s performance, damage computer files, or even track your keystrokes as you type to steal your identity and more. If you don’t want to pay for such a program, consider a free solution such as Spyware Terminator (www.spywareterminator.com).