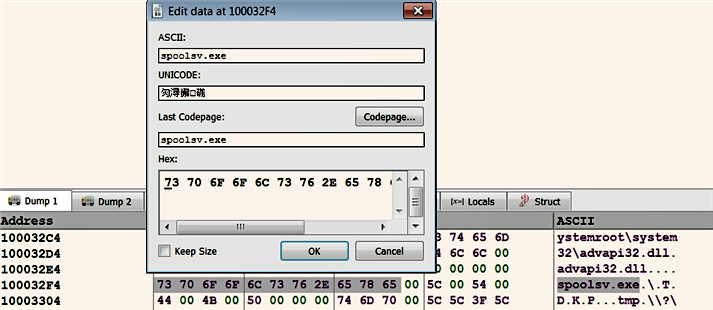
While performing malware analysis, you may want to modify the binary to change its functionality or reverse its logic to suit your needs. x64dbg allows you to modify data in the memory or instructions of a program. To modify the data in a memory, navigate to the memory address and select the sequence of bytes you want to modify, then right-click and choose Binary | Edit (Ctrl + E), which will bring up a dialog (shown as follows) that you can use to modify the data as ASCII, UNICODE, or a sequence of hex bytes:
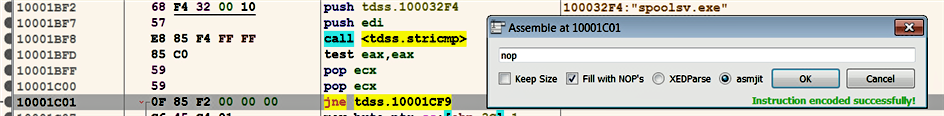
The following screenshot shows the code excerpt from the TDSS rootkit DLL (this is the same binary that was covered in the previous chapter, in the section Patching the Binary Using IDA). If you recall, this DLL used string comparison to perform a check to ensure that it was running under the spoolsv.exe process. If the string comparison fails (that is, if the DLL is not running under spoolsv.exe), then the code jumps to the end of the function and returns from the function without exhibiting malicious behavior. Suppose that you want this binary to run under any process (not just spoolsv.exe). You can modify the conditional jump instruction (JNE tdss.10001Cf9) with a nop instruction, to remove the process restriction. To do that, right-click on the conditional jump instruction and select Assemble, which will bring up the dialog shown as follows, using which you can enter the instructions. Note that, in the screenshot, the fill with NOP's option is checked, to make sure that the instruction alignment is correct:
After you have modified the data in the memory or the instruction, you can apply the patch to the file by choosing File | Patch file, which will bring up a patches dialog showing all of the modifications made to the binary. Once you are satisfied with the modifications, click on Patch file and save the file:
