Cross-references are very useful when analyzing malicious binary. During analysis, if you come across a string or a useful function and if you would like to know how they are used in the code, then you can use cross-references to quickly navigate to the location where the string or function is referenced. Cross-reference comments added by IDA are a great way to navigate between addresses, but there is a display limit (of two entries); as a result, you will not be able to see all of the cross-references. Consider the following data cross-reference at ➊; the ellipsis (...) indicates that there are more cross-references:
.data:00403374 dword_403374 dd ? ; DATA XREF: _main+6w
.data:00403374 ; _main+17r ... ➊
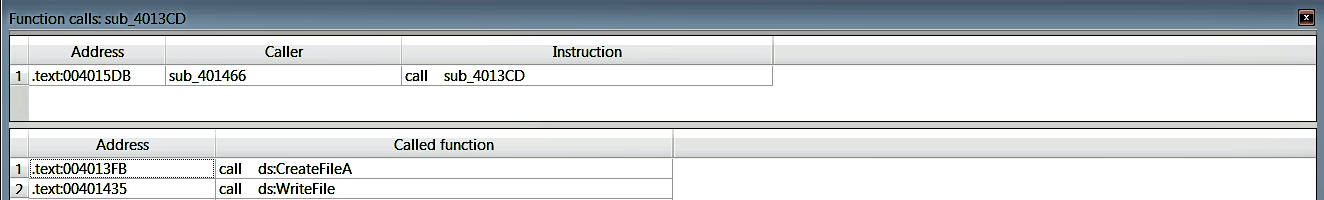
Suppose that you want to list all of the cross-references; just click on the named location such as dword_403374 and press the X key. This will bring up a window, that lists all the locations where the named location is referenced, as follows. You can double-click on any of these entries to reach the location in the program where the data is used. You can use this technique to find all of the cross-references to a string or function:
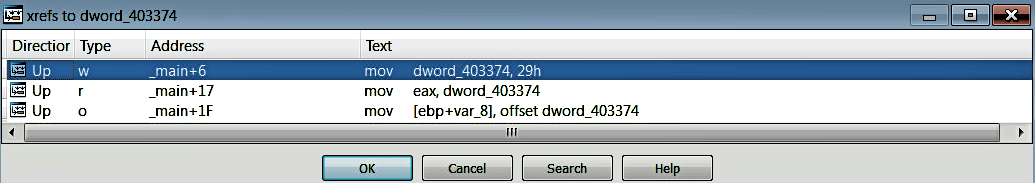
A program normally contains many functions. A single function can be called by single/multiple functions, or it can, in turn, call single or multiple functions. When performing malware analysis, you might be interested in getting a quick overview of a function. In such a case, you can highlight the function name and choose View | Open Subviews | Function Calls to get the function cross-references. The following screenshot shows the function Xrefs for the function sub_4013CD (from a malware sample). The upper half of the window tells you that the function sub_401466 calls sub_4013CD. The lower half of the window displays all of the functions that will be called by sub_4013CD; notice that the lower window displays the API functions (CreateFile and WriteFile) that will be called by sub_4013CD; based on this information, you can tell that the sub_4013CD function interacts with the filesystem: