Chapter 9
Sniffers
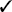 II. Analysis/Assessment
II. Analysis/Assessment
- A. Data analysis
 IV. Tools/Systems/Programs
IV. Tools/Systems/Programs
- B. Network/wireless sniffers (e.g., Wireshark, Airsnort)
Sniffing allows you to see all sorts of traffic, both protected and unprotected. In the right conditions and with the right protocols in place, an attacking party may be able to gather information that can be used for further attacks or to cause other issues for the network or system owner.
Once you have gotten to the point of sniffing, it is possible to move on to other types of attacks, including session hijacking, man-in-the-middle, and denial-of-service attacks. Taking over authenticated sessions, manipulating data, and executing commands are within the realm of possibility once sniffing can be performed. Of course before we get to these attacks, you must learn about sniffing and how sniffers work.
Understanding Sniffers
Sniffers are utilities that you, as an ethical hacker, can use to capture and scan traffic moving across a network. Sniffers are a broad category that encompasses any utility that has the ability to perform a packet-capturing function. Regardless of the build, sniffers perform their traffic-capturing function by enabling promiscuous mode on the connected network interface, thereby allowing the capture of all traffic, whether or not that traffic is intended for them. Once an interface enters promiscuous mode, it doesn’t discriminate between traffic that is destined for its address; it picks up all traffic on the wire, thereby allowing you to capture and investigate every packet.
Sniffing can be active or passive in nature. Typically, passive sniffing is considered to be any type of sniffing where traffic is looked at but not altered in any way. In active sniffing, not only is traffic monitored, but it may also be altered in some way as determined by the attacking party. Know the difference for your exam.
Most sniffer utilities have basic options that are fairly consistent across the gamut of versions. This consistency holds true regardless of whether it’s a Linux-based utility or a Windows version. We’ll dig more into types and specifics later, but first let’s look at the commonalities. On most sniffers a main pane displays the incoming packets and highlights or lists them accordingly. It is usually linear in its listing unless you specify otherwise via filters or other options. Additionally, there is commonly a subpanel that allows an in-depth view of the packet selected. It’s important to be familiar with your sniffer of choice as it will save you a lot of time and frustration in the long run. Also, having a good grasp of a sniffer’s basic functions will allow you to use many different sniffers without too many problems. So, from here, a sniffer usually has an interface selection or activation option that begins the capture phase.
Once you choose the capture button, you should see packets populating your capture pane; if not, check your network interface selection. All sniffers give you the ability to select from all available interfaces on your computer. You can easily choose a disconnected interface and sit there irritated because your sniffer isn’t working. Just double-check and you’ll be happily rewarded with real-time traffic!
Remember that a sniffer is not just a dumb utility that allows you to view only streaming traffic. A sniffer is a robust set of tools that can give you an extremely in depth and granular view of what your (or their) network is doing from the inside out. That being said, if you really want to extrapolate all the juicy tidbits and clues of each packet, save the capture and review it when time allows. I prefer to review my 20,000 packets of captured data at my local coffee shop with a hot vanilla latte and a blueberry scone. Make it easy on yourself; your target is not going anywhere soon.
Also, before we go too much into sniffers, it is important to mention that there are also things called hardware protocol analyzers. These devices plug into the network at the hardware level and can monitor traffic without manipulating traffic. Typically these hardware devices are not easily accessible to most ethical hackers due to their enormous cost in many cases (some devices have price tags in the six-figure range).
How successful sniffers are depends on the relative and inherent insecurity of certain network protocols. Protocols such as the tried and true TCP/IP were never designed with security in mind and therefore do not offer much in this area. Several protocols lend themselves to easy sniffing:
Telnet/rlogin Keystrokes, such as those including usernames and passwords, that can be easily sniffed.
HTTP Designed to send information in the clear without any protection and thus a good target for sniffing.
Simple Mail Transfer Protocol (SMTP) Commonly used in the transfer of e-mail, this protocol is efficient, but it does not include any protection against sniffing.
Network News Transfer Protocol (NNTP) All communication, including passwords and data, is sent in the clear.
Post Office Protocol (POP) Designed to retrieve e-mail from servers, this protocol does not include protection against sniffing because passwords and usernames can be intercepted.
File Transfer Protocol (FTP) A protocol designed to send and receive files; all transmissions are sent in the clear.
Internet Message Access Protocol (IMAP) Similar to SMTP in function and lack of protection.
Using a Sniffer
We touched on some of the basics of using a sniffer in the previous section, but now let’s get down and dirty. Quite a few sniffer builds are available that perform nearly identical functions. The real advantage of one over the other is the robustness of functionality in how the sniffer displays that data and what options are available to help you digest and dissect it.
Sniffing Tools
Sniffing tools are extremely common applications. A few interesting ones are:
Wireshark One of the most widely known and used packet sniffers. Offers a tremendous number of features designed to assist in the dissection and analysis of traffic.
TCPdump A well-known command-line packet analyzer. Provides the ability to intercept and observe TCP/IP and other packets during transmission over the network. Available at www.tcpdump.org.
Windump A port of the popular Linux packet sniffer TCPdump, which is a command-line tool that is great for displaying header information.
Omnipeek Manufactured by WildPackets, OmniPeek is a commercial product that is the evolution of the product EtherPeek.
Dsniff A suite of tools designed to perform sniffing with different protocols with the intent of intercepting and revealing passwords. Dsniff is designed for Unix and Linux platforms and does not have a complete equivalent on the Windows platform.
EtherApe A Linux/Unix tool designed to graphically display a system’s incoming and outgoing connections.
MSN Sniffer A sniffing utility specifically designed for sniffing traffic generated by the MSN messenger application.
NetWitness NextGen Includes a hardware-based sniffer, along with other features, designed to monitor and analyze all traffic on a network; a popular tool in use by the FBI and other law enforcement agencies.
Wireshark
As of this writing, Wireshark reigns supreme as perhaps the best sniffer on the market. Wireshark has been around for quite some time, and it has proven its worth time and time again. Wireshark is natively available on both Windows and Linux.
Sniffer builds include TCPdump, Kismet, and Ettercap, among others. A great resource for sniffers and many other security tools is www.sectools.org. All sniffers have their place in the sniffing universe, but for our purposes we will be focusing on Wireshark. Wireshark is natively available on Linux as well as Windows. First, let’s do a quick run through on Wireshark basics in Exercise 9.1.
As you can see from the live capture and saved capture, there’s a lot going on! One powerful feature of Wireshark is its search string and filtering capabilities. In a real-world capture, it is likely to be sniffing a connection that has a large number of attached clients. This is when search strings and filtering become a pen tester’s best friend. Table 9.1 shows common search string options for Wireshark. The CEH exam tests whether you can apply your understanding of this tool and its options.
TABLE 9.1 Wireshark filters
| Operator | Function | Example |
== |
Equal | ip.addr == 192.168.1.2 |
eq |
Equal | tcp.port eq 161 |
!= |
Not equal | ip.addr != 192.168.1.2 |
ne |
Not equal | ip.src ne 192.168.1.2 |
contains |
Contains specified value | http contains "http://www.site.com" |
Table 9.1 lists the basic filters that you will most likely use (and may see on the exam). As you review the examples used in the table, notice the structure or syntax of each statement and how it relates to what the filter is doing. To see how each of these examples maps to the syntax, refer to Table 9.2.
TABLE 9.2 Wireshark filter breakdown
| Protocol | Field | Operator | Value |
ip |
Addr |
== |
192.168.1.2 |
tcp |
port |
eq |
161 |
ip |
addr |
!= |
192.168.1.2 |
ip |
src |
ne |
192.168.1.2 |
http |
* |
contains |
http://www.site.com |
Table 9.3 covers Wireshark’s command-line interface (CLI) tools.
TABLE 9.3 Wireshark CLI tools
| Command | Function |
tshark |
A command-line version of Wireshark (similar to TCPdump) |
dumpcap |
Small program with the sole intent of capturing traffic |
capinfos |
Reads a capture and returns statistics on that file |
editcap |
Edits or translates the format of capture files |
mergecap |
Combines multiple capture files into one |
text2cap |
Creates a capture file from an ASCII hexdump of packets |
TCPdump
Now that you’ve seen the basics of how to use Wireshark, let’s move directly to getting our hands dirty with TCPdump. This utility is a command line–based sniffer that is quite robust in comparison to its GUI counterparts. TCPdump has been around for quite some time, and it was the tool of choice well before Wireshark came on the scene. TCPdump is native to Linux; the equivalent Windows tool is called Windump. In Exercise 9.2, you will use TCPdump to capture packets.
Sniffing a network in a quiet and effective manner is an integral skill in an ethical hacker’s toolkit. Setting up the connection properly and capturing traffic successfully is extremely important, but as a hacker you must also possess the ability to dig into the packets you’ve captured. In the next section you’ll learn how to do that. The ability to read output from a sniffer is not just a CEH exam skill. It truly is one of those integral skills that every hacker must have.
Reading Sniffer Output
Remember the original Jaws movie? Remember when Hooper and Brody cut the shark open in the middle of the movie and Hooper started pulling stuff out of the stomach...yuck! So how does this relate to sniffer output? Well, the concept is very similar. When packets are captured, each one has a slew of innards that you can dissect one piece at a time. Just as Hooper digs into the open-bellied shark, you too dig through the packet innards to find those specific morsels that will tell you what you need to know. The point here isn’t movie trivia (although I love killer shark flicks); the point you should take away from this is that each packet captured really does have an immense amount of data that you can use for reconnaissance or setting up future attacks. It’s even extremely useful as a legitimate troubleshooting tool. Figure 9.1 shows a captured packet of a basic TCP handshake. Can you find the basic three-way handshake steps?
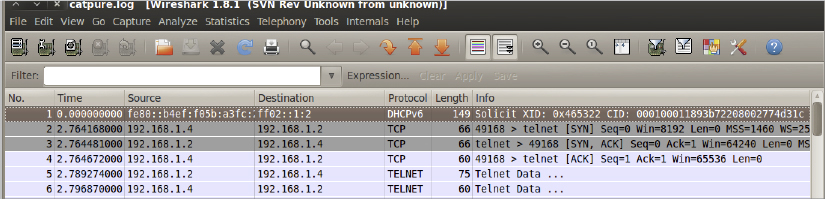
FIGURE 9.1 TCP three-way handshake packet
Lines 2, 3, and 4 in Figure 9.1 are the SYN, SYN-ACK, and ACK that we discussed in Chapter 2, “System Fundamentals.”
Packet sniffing and its interpretation can be likened to an art. There are some people who can think like a computer, take one glance at a packet, and tell you everything you ever wanted to know about where it’s going and what’s it doing. This is not your goal, nor are you expected to be able to do this for the CEH exam. As ethical hackers, we are methodical, deliberate, patient, and persistent. This applies to reading packet captures as well. In Exercise 9.3 you will step through a captured packet bit by bit. This skill will prove invaluable not just for the exam, but also for protecting your own network through traffic analysis.
Switched Network Sniffing
Switched networks present an inherent initial challenge to sniffing a network in its entirety. A wired switch doesn’t allow you to sniff the whole network. As you saw in Chapter 2, each switchport is a collision domain, so traffic within the switch doesn’t travel between ports.
Okay, enough switch talk. Your goal is to be able to sniff the network portions you want to at will. To achieve this you can use the various techniques that we’ll explore in this section.
MAC Flooding
One of the most common methods for enabling sniffing on a switch is to turn it into a device that does allow sniffing. Because a switch keeps traffic separate to each switchport (collision domain), you want to convert it into a hub-like environment. A switch keeps track of MAC addresses received by writing them to a content addressable memory (CAM) table. If a switch is flooded with MAC addresses, it may easily overwhelm the switch’s ability to write to its own CAM table. This in turn makes the switch fall into a giant hub. There are a few utilities available to accomplish this technique. One common Linux utility is Macof. Check out Figure 9.2 to see Macof in action.
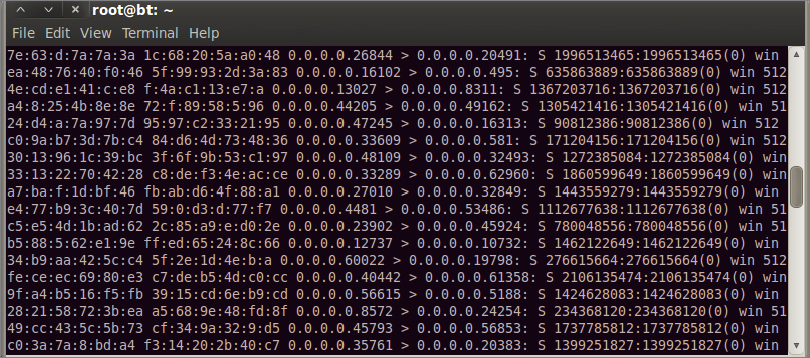
FIGURE 9.2 Macof MAC flood
Overflowing a CAM table using Ubuntu is a simple matter. The standard repositories
store the tools needed for a successful attack and can be easily obtained with aptitude. To use aptitude to obtain the required tools, su to root (or sudo) and type the following to install the dsniff suite (which includes Macof):
aptitude install dsniffOnce installation is complete, at the command prompt enter the following:
macofAt this point the utility will start flooding the CAM table with invalid MAC addresses. To stop the attack, press Ctrl+Z.
ARP Poisoning
Address Resolution Protocol (ARP) poisoning attempts to contaminate a network with improper gateway mappings. As explained in Chapter 2, ARP essentially maps IP addresses to specific MAC addresses, thereby allowing switches to know the most efficient path for the data being sent. Interestingly enough, ARP traffic doesn’t have any prerequisites for its sending or receiving process; ARP broadcasts are free to roam the network at will. The attacker takes advantage of this open traffic concept by feeding these incorrect ARP mappings to the gateway itself or to the hosts of the network. Either way, the attacker is attempting to become the hub of all network traffic. Some tools you can use to ARP-poison a host are Ettercap, Cain and Abel (see Figure 9.3), and Arpspoof.
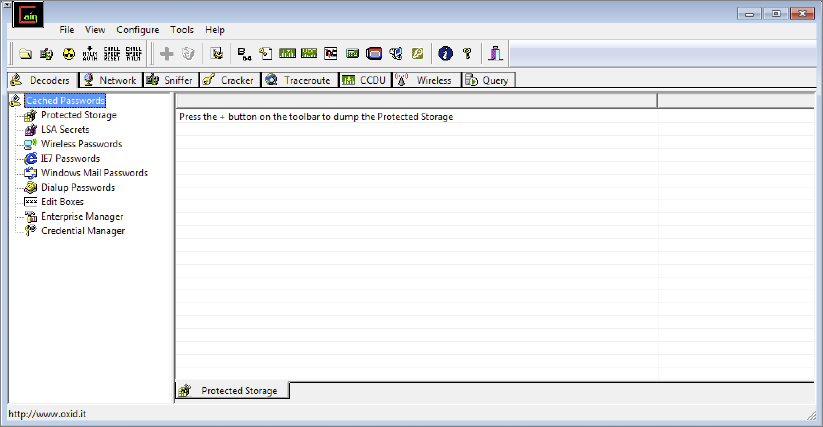
FIGURE 9.3 Cain and Abel
MAC Spoofing
MAC spoofing is a simple concept in which an attacker (or pen tester) changes their MAC address to the MAC address of an existing authenticated machine already on the network. The simplest example of when this strategy is employed is when a network administrator has applied port security to the switches on their network. Port security is a low-level security methodology that allows only a specific number of MAC addresses to attach to each switchport (usually one or two). If this number is exceeded (for example, if you take off the original machine and attach one or two unrecognized units), the port will usually shut down depending on the configuration applied. MAC spoofing isn’t necessarily a technique used to allow network-wide sniffing, but it does work to allow an unauthorized client onto the network without too much administrative hacking effort.
Port Mirror or SPAN Port
Another way to circumvent switches is through the use of physical means—getting physical access to the switch and using port mirroring or a Switched Port Analyzer (SPAN) port. This technique is used to send a copy of every network packet encountered on one switchport or a whole VLAN to another port where it may be monitored. This functionality is used to monitor network traffic either for diagnostic purposes or for the purpose of implementing devices such as network intrusion detection systems (NIDSs).
On the Defensive
As an ethical hacker, your work could very likely put you in a position of prevention rather than pen testing. Based on what we’ve covered so far in this chapter, what you know as an attacker can help you prevent the very techniques you employ from the outside in. Here are defenses against the attacks we just covered from a pen tester’s perspective:
- Use a hardware-switched network for the most sensitive portions of your network in an effort to isolate traffic to a single segment or collision domain.
- Implement IP DHCP Snooping on switches to prevent ARP-poisoning and spoofing attacks.
- Implement policies preventing promiscuous mode on network adapters.
- Be careful when deploying wireless access points, knowing that all traffic on the wireless network is subject to sniffing.
- Encrypt your sensitive traffic using an encrypting protocol such as SSH or IPSec.
Here are other methods of hardening a network against sniffing:
- Static ARP entries, which consist of preconfiguring a device with the MAC addresses of devices that it will be working with ahead of time. However, this strategy does not scale well.
- Port security is used by switches that have the ability to be programmed to allow only specific MAC addresses to send and receive data on each port.
- IPv6 has security benefits and options that IPv4 does not have.
- Replacing protocols such as FTP and Telnet with SSH is an effective defense against sniffing. If SSH is not a viable solution, consider protecting older legacy protocols with IPSec.
- Virtual private networks (VPNs) can provide an effective defense against sniffing due to their encryption aspect.
- SSL is a great defense along with IPSec.
Mitigating MAC Flooding
You can mitigate the CAM table-overflow attack by configuring port security on the switch. This will allow MAC addresses to be specified on a particular switchport, or you can specify the maximum number of MAC addresses that the switchport can learn.
Cisco IOS Mitigation
Listing 9.1 shows a sample of configuration options on the Cisco IOS.
Cisco recommends the shutdown option.
Juniper Mitigation
Listing 9.2 shows configuration options for Juniper.
Netgear Mitigation
Listing 9.3 shows configuration of a Netgear device.
Detecting Sniffing Attacks
Aside from pure defensive tactics, it is possible to be proactive and use detection techniques designed to locate any attempts to sniff and shut them down. These methods include:
- Look for systems running network cards in promiscuous mode. Under normal circumstances there is little reason for a network card to be in promiscuous mode and as such all cards running in this mode should be investigated.
- Run an NIDS to detect telltale signs of sniffing and track it down.
- Tools such as HP’s Performance Insight can provide a way to view the network and identify strange traffic.
Exam Essentials
Know the purpose of sniffing. Sniffing is a technique used to gather information as it flows across the network. Sniffing can be performed using software-based systems or through the use of hardware devices known as protocol analyzers.
Understand your targets. For each target, know what type of information you are looking for—passwords, data, or something else.
Know what makes sniffing possible. Sniffing is possible due to traffic being sent in the clear as well as access to the network. Also, having the ability to switch a network card into promiscuous mode allows you to view all traffic on the network as it flows by.
Know your defenses. Know that techniques such as encryption, IPSec, SSL, SSH, and VPNs can provide effective countermeasures against sniffing.
Summary
This chapter covered what a sniffer is and how it works. You learned about two common sniffing utilities, Wireshark and TCPdump. You saw the importance of Wireshark search strings for real-world filtering and exam preparation. This chapter briefly touched on CLI commands for Wireshark that allow similar functionality to that of the GUI version. You also captured some packets with both Wireshark and TCPdump, and learned how to dissect and analyze those packets by taking advantage of Wireshark’s robust detailed interface. You explored some basic techniques to overcome a switched network’s inherent sniffing limitations, and reviewed defensive actions that you can take to protect your networks from sniffing and subsequent attacks.
Review Questions
-
On a switch, each switchport represents a ____________.
- VLAN
- Broadcast domain
- Host
- Collision domain
-
Wireless access points function as a ____________.
- Hub
- Bridge
- Router
- Repeater
-
What mode must be configured to allow an NIC to capture all traffic on the wire?
- Extended mode
- 10/100
- Monitor mode
- Promiscuous mode
-
Which of the following prevents ARP poisoning?
- ARP Ghost
- IP DHCP Snooping
- IP Snoop
- DNSverf
-
Jason is a system administrator who is researching a technology that will secure network traffic from potential sniffing by unauthorized machines. Jason is not concerned with the future impact on legitimate troubleshooting. What technology can Jason implement?
- SNMP
- LDAP
- SSH
- FTP
-
MAC spoofing applies a legitimate MAC address to an unauthenticated host, which allows the attacker to pose as a valid user. Based on your understanding of ARP, what would indicate a bogus client?
- The MAC address doesn’t map to a manufacturer.
- The MAC address is two digits too long.
- A reverse ARP request maps to two hosts.
- The host is receiving its own traffic.
-
Bob is attempting to sniff a wired network in his first pen test contract. He sees only traffic from the segment he is connected to. What can Bob do to gather all switch traffic?
- MAC flooding
- MAC spoofing
- IP spoofing
- DOS attack
-
What technique funnels all traffic back to a single client, allowing sniffing from all connected hosts?
- ARP redirection
- ARP poisoning
- ARP flooding
- ARP partitioning
-
Which Wireshark filter displays only traffic from 192.168.1.1?
- ip.addr =! 192.168.1.1
- ip.addr ne 192.168.1.1
- ip.addr == 192.168.1.1
- ip.addr − 192.168.1.1
-
What common tool can be used for launching an ARP-poisoning attack?
- Cain and Abel
- Nmap
- Scooter
- TCPdump
-
Which command launches a CLI version of Wireshark?
Wireshkdumpcaptsharkeditcap
-
Jason is using TCPdump to capture traffic on his network. He would like to save the capture for later review. What command can Jason use?
tcpdump −r capture.logtcpdump −l capture.logtcpdump −t capture.logtcpdump −w capture.log
-
What is the generic syntax of a Wireshark filter?
- protocol.field operator value
- field.protocol operator value
- operator.protocol value field
- protocol.operator value field
-
Tiffany is analyzing a capture from a client’s network. She is particularly interested in NetBIOS traffic. What port does Tiffany filter for?
- 123
- 139
- 161
- 110
-
Based on the packet capture shown in the graphic, what is contained in the highlighted section of the packet?
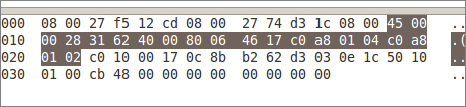
- The frame value of the packet
- The MAC address of the sending host
- Source and destination IP addresses
- The routed protocol value
-
Jason is using TCPdump to capture traffic on his network. He would like to review a capture log gathered previously. What command can Jason use?
tcpdump −r capture.logtcpdump −l capture.logtcpdump −t capture.logtcpdump −w capture.log
-
Wireshark requires a network card to be able to enter which mode to sniff all network traffic?
- Capture mode
- Promiscuous mode
- pcap mode
- Gather mode
-
Which network device can block sniffing to a single network collision domain?
- Hub
- Switch
- Router
- Bridge
-
What device will not limit the abilities of a sniffer?
- Hub
- Router
- Switch
- Gateway
-
The command-line equivalent of Windump is known as?
- Wireshark
- TCPdump
- Windump
- Netstat