Glossary
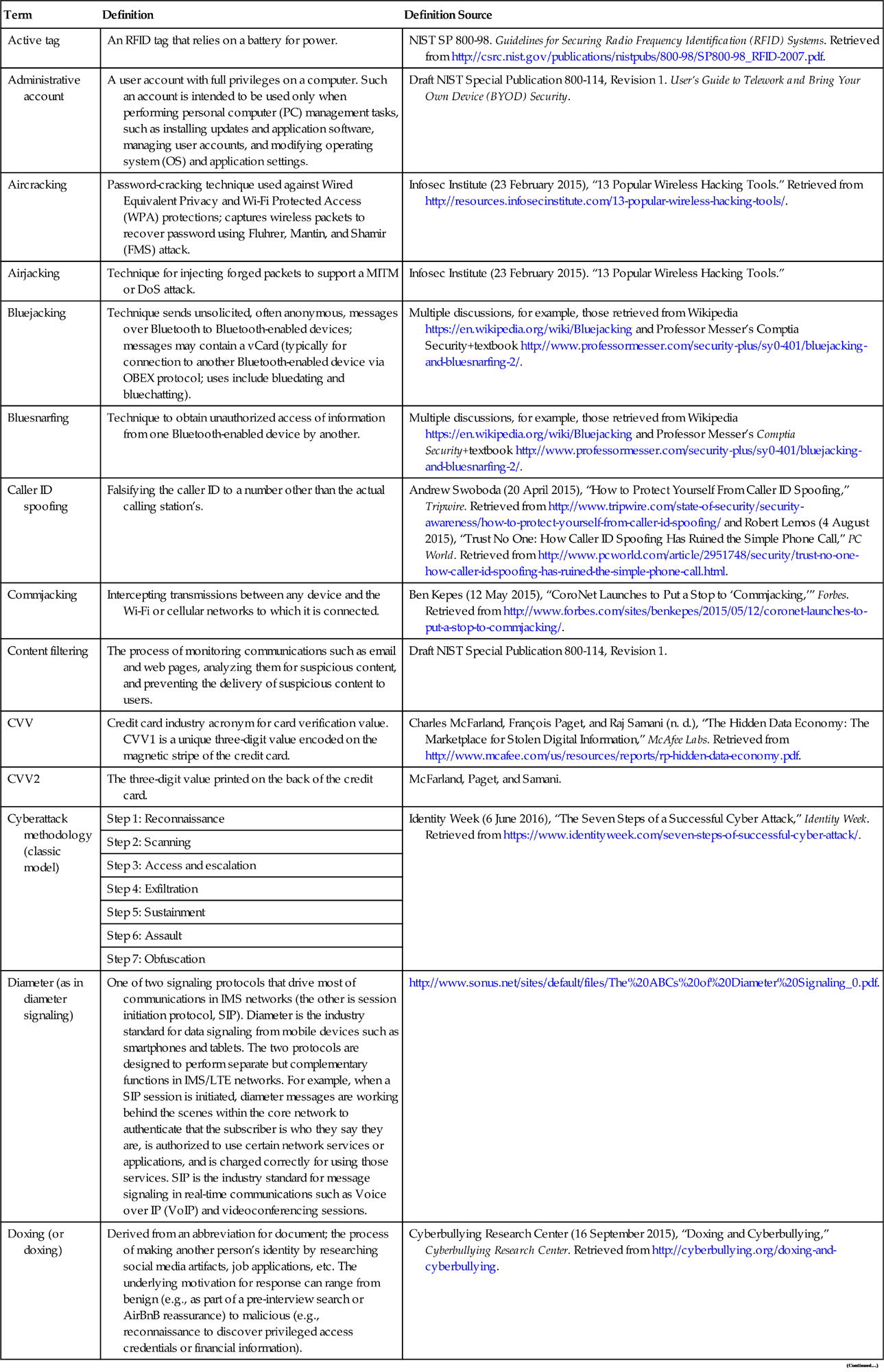
| Term | Definition | Definition Source |
| Active tag | An RFID tag that relies on a battery for power. | NIST SP 800-98. Guidelines for Securing Radio Frequency Identification (RFID) Systems. Retrieved from http://csrc.nist.gov/publications/nistpubs/800-98/SP800-98_RFID-2007.pdf. |
| Administrative account | A user account with full privileges on a computer. Such an account is intended to be used only when performing personal computer (PC) management tasks, such as installing updates and application software, managing user accounts, and modifying operating system (OS) and application settings. | Draft NIST Special Publication 800-114, Revision 1. User’s Guide to Telework and Bring Your Own Device (BYOD) Security. |
| Aircracking | Password-cracking technique used against Wired Equivalent Privacy and Wi-Fi Protected Access (WPA) protections; captures wireless packets to recover password using Fluhrer, Mantin, and Shamir (FMS) attack. | Infosec Institute (23 February 2015), “13 Popular Wireless Hacking Tools.” Retrieved from http://resources.infosecinstitute.com/13-popular-wireless-hacking-tools/. |
| Airjacking | Technique for injecting forged packets to support a MITM or DoS attack. | Infosec Institute (23 February 2015). “13 Popular Wireless Hacking Tools.” |
| Bluejacking | Technique sends unsolicited, often anonymous, messages over Bluetooth to Bluetooth-enabled devices; messages may contain a vCard (typically for connection to another Bluetooth-enabled device via OBEX protocol; uses include bluedating and bluechatting). | Multiple discussions, for example, those retrieved from Wikipedia https://en.wikipedia.org/wiki/Bluejacking and Professor Messer’s Comptia Security+textbook http://www.professormesser.com/security-plus/sy0-401/bluejacking-and-bluesnarfing-2/. |
| Bluesnarfing | Technique to obtain unauthorized access of information from one Bluetooth-enabled device by another. | Multiple discussions, for example, those retrieved from Wikipedia https://en.wikipedia.org/wiki/Bluejacking and Professor Messer’s Comptia Security+textbook http://www.professormesser.com/security-plus/sy0-401/bluejacking-and-bluesnarfing-2/. |
| Caller ID spoofing | Falsifying the caller ID to a number other than the actual calling station’s. | Andrew Swoboda (20 April 2015), “How to Protect Yourself From Caller ID Spoofing,” Tripwire. Retrieved from http://www.tripwire.com/state-of-security/security-awareness/how-to-protect-yourself-from-caller-id-spoofing/ and Robert Lemos (4 August 2015), “Trust No One: How Caller ID Spoofing Has Ruined the Simple Phone Call,” PC World. Retrieved from http://www.pcworld.com/article/2951748/security/trust-no-one-how-caller-id-spoofing-has-ruined-the-simple-phone-call.html. |
| Commjacking | Intercepting transmissions between any device and the Wi-Fi or cellular networks to which it is connected. | Ben Kepes (12 May 2015), “CoroNet Launches to Put a Stop to ‘Commjacking,’” Forbes. Retrieved from http://www.forbes.com/sites/benkepes/2015/05/12/coronet-launches-to-put-a-stop-to-commjacking/. |
| Content filtering | The process of monitoring communications such as email and web pages, analyzing them for suspicious content, and preventing the delivery of suspicious content to users. | Draft NIST Special Publication 800-114, Revision 1. |
| CVV | Credit card industry acronym for card verification value. CVV1 is a unique three-digit value encoded on the magnetic stripe of the credit card. | Charles McFarland, François Paget, and Raj Samani (n. d.), “The Hidden Data Economy: The Marketplace for Stolen Digital Information,” McAfee Labs. Retrieved from http://www.mcafee.com/us/resources/reports/rp-hidden-data-economy.pdf. |
| CVV2 | The three-digit value printed on the back of the credit card. | McFarland, Paget, and Samani. |
| Cyberattack methodology (classic model) | Step 1: Reconnaissance | Identity Week (6 June 2016), “The Seven Steps of a Successful Cyber Attack,” Identity Week. Retrieved from https://www.identityweek.com/seven-steps-of-successful-cyber-attack/. |
| Step 2: Scanning | ||
| Step 3: Access and escalation | ||
| Step 4: Exfiltration | ||
| Step 5: Sustainment | ||
| Step 6: Assault | ||
| Step 7: Obfuscation | ||
| Diameter (as in diameter signaling) | One of two signaling protocols that drive most of communications in IMS networks (the other is session initiation protocol, SIP). Diameter is the industry standard for data signaling from mobile devices such as smartphones and tablets. The two protocols are designed to perform separate but complementary functions in IMS/LTE networks. For example, when a SIP session is initiated, diameter messages are working behind the scenes within the core network to authenticate that the subscriber is who they say they are, is authorized to use certain network services or applications, and is charged correctly for using those services. SIP is the industry standard for message signaling in real-time communications such as Voice over IP (VoIP) and videoconferencing sessions. | http://www.sonus.net/sites/default/files/The%20ABCs%20of%20Diameter%20Signaling_0.pdf. |
| Doxing (or doxing) | Derived from an abbreviation for document; the process of making another person’s identity by researching social media artifacts, job applications, etc. The underlying motivation for response can range from benign (e.g., as part of a pre-interview search or AirBnB reassurance) to malicious (e.g., reconnaissance to discover privileged access credentials or financial information). | Cyberbullying Research Center (16 September 2015), “Doxing and Cyberbullying,” Cyberbullying Research Center. Retrieved from http://cyberbullying.org/doxing-and-cyberbullying. |
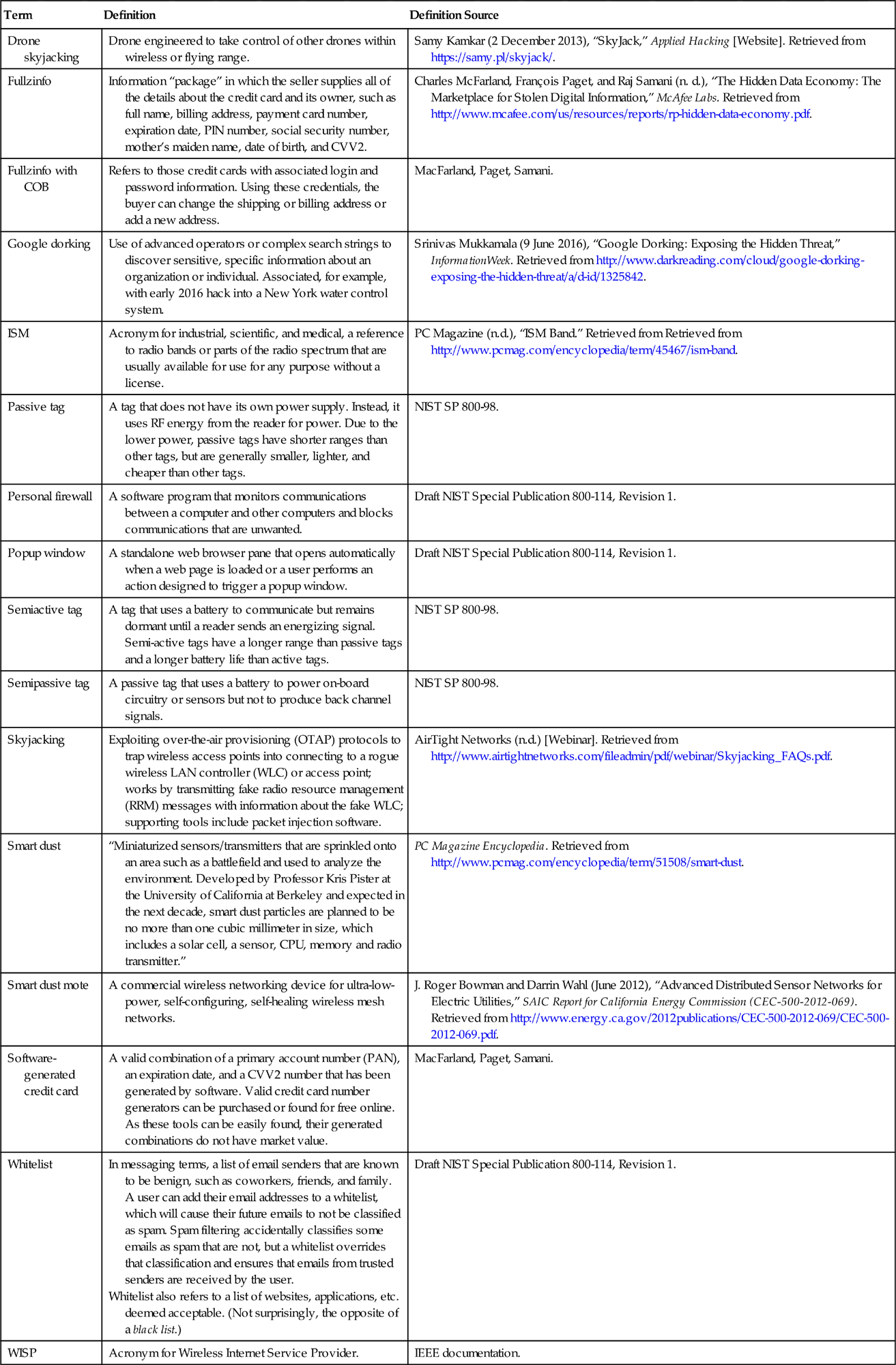
| Drone skyjacking | Drone engineered to take control of other drones within wireless or flying range. | Samy Kamkar (2 December 2013), “SkyJack,” Applied Hacking [Website]. Retrieved from https://samy.pl/skyjack/. |
| Fullzinfo | Information “package” in which the seller supplies all of the details about the credit card and its owner, such as full name, billing address, payment card number, expiration date, PIN number, social security number, mother’s maiden name, date of birth, and CVV2. | Charles McFarland, François Paget, and Raj Samani (n. d.), “The Hidden Data Economy: The Marketplace for Stolen Digital Information,” McAfee Labs. Retrieved from http://www.mcafee.com/us/resources/reports/rp-hidden-data-economy.pdf. |
| Fullzinfo with COB | Refers to those credit cards with associated login and password information. Using these credentials, the buyer can change the shipping or billing address or add a new address. | MacFarland, Paget, Samani. |
| Google dorking | Use of advanced operators or complex search strings to discover sensitive, specific information about an organization or individual. Associated, for example, with early 2016 hack into a New York water control system. | Srinivas Mukkamala (9 June 2016), “Google Dorking: Exposing the Hidden Threat,” InformationWeek. Retrieved from http://www.darkreading.com/cloud/google-dorking-exposing-the-hidden-threat/a/d-id/1325842. |
| ISM | Acronym for industrial, scientific, and medical, a reference to radio bands or parts of the radio spectrum that are usually available for use for any purpose without a license. | PC Magazine (n.d.), “ISM Band.” Retrieved from Retrieved from http://www.pcmag.com/encyclopedia/term/45467/ism-band. |
| Passive tag | A tag that does not have its own power supply. Instead, it uses RF energy from the reader for power. Due to the lower power, passive tags have shorter ranges than other tags, but are generally smaller, lighter, and cheaper than other tags. | NIST SP 800-98. |
| Personal firewall | A software program that monitors communications between a computer and other computers and blocks communications that are unwanted. | Draft NIST Special Publication 800-114, Revision 1. |
| Popup window | A standalone web browser pane that opens automatically when a web page is loaded or a user performs an action designed to trigger a popup window. | Draft NIST Special Publication 800-114, Revision 1. |
| Semiactive tag | A tag that uses a battery to communicate but remains dormant until a reader sends an energizing signal. Semi-active tags have a longer range than passive tags and a longer battery life than active tags. | NIST SP 800-98. |
| Semipassive tag | A passive tag that uses a battery to power on-board circuitry or sensors but not to produce back channel signals. | NIST SP 800-98. |
| Skyjacking | Exploiting over-the-air provisioning (OTAP) protocols to trap wireless access points into connecting to a rogue wireless LAN controller (WLC) or access point; works by transmitting fake radio resource management (RRM) messages with information about the fake WLC; supporting tools include packet injection software. | AirTight Networks (n.d.) [Webinar]. Retrieved from http://www.airtightnetworks.com/fileadmin/pdf/webinar/Skyjacking_FAQs.pdf. |
| Smart dust | “Miniaturized sensors/transmitters that are sprinkled onto an area such as a battlefield and used to analyze the environment. Developed by Professor Kris Pister at the University of California at Berkeley and expected in the next decade, smart dust particles are planned to be no more than one cubic millimeter in size, which includes a solar cell, a sensor, CPU, memory and radio transmitter.” | PC Magazine Encyclopedia. Retrieved from http://www.pcmag.com/encyclopedia/term/51508/smart-dust. |
| Smart dust mote | A commercial wireless networking device for ultra-low-power, self-configuring, self-healing wireless mesh networks. | J. Roger Bowman and Darrin Wahl (June 2012), “Advanced Distributed Sensor Networks for Electric Utilities,” SAIC Report for California Energy Commission (CEC-500-2012-069). Retrieved from http://www.energy.ca.gov/2012publications/CEC-500-2012-069/CEC-500-2012-069.pdf. |
| Software-generated credit card | A valid combination of a primary account number (PAN), an expiration date, and a CVV2 number that has been generated by software. Valid credit card number generators can be purchased or found for free online. As these tools can be easily found, their generated combinations do not have market value. | MacFarland, Paget, Samani. |
| Whitelist | In messaging terms, a list of email senders that are known to be benign, such as coworkers, friends, and family. A user can add their email addresses to a whitelist, which will cause their future emails to not be classified as spam. Spam filtering accidentally classifies some emails as spam that are not, but a whitelist overrides that classification and ensures that emails from trusted senders are received by the user. Whitelist also refers to a list of websites, applications, etc. deemed acceptable. (Not surprisingly, the opposite of a black list.) |
Draft NIST Special Publication 800-114, Revision 1. |
| WISP | Acronym for Wireless Internet Service Provider. | IEEE documentation. |