WAPs in Commercial and Industrial Contexts
Abstract
Smart is the new black for marketing technology applications: It goes with everything, including built space that is not intended for private, residential use, but for industrial and commercial uses. Improved cost efficiency and convenience are touted as benefits of making these spaces smarter for controlling environmental settings, surveillance, access, machinery, and automated processes. When the point-to-point connectivity between devices and controllers (even the human controller) is interrupted by deploying insufficiently robust wireless solutions, a gap is created between signal transmitter and signal receiver that can—and in some cases has—become the playground for enterprising hackers. Vulnerable automated systems are found throughout critical infrastructure sectors, many of which in the United States are under private (not government) control, for example, utility companies, water treatment plants, and prisons. NIST has compiled a solid list of guidelines for addressing security in automated systems including those interconnected through WAPs.
Keywords
Access control; surveillance; industrial control system; SCADA; Stuxnet; gateway; industrial sabotage
Overview
Smart is the new black for marketing technology applications: It goes with everything, whether applied to cars, shoes, mattresses,1 or structures. This chapter looks at WAPs in built space that is not intended for private, residential use, but for industrial and commercial uses. Industrial facilities—classified here as environments in which the majority of the space is dedicated to the protection and care of machinery (e.g., manufacturing or food processing plants, power-generating facilities)—have a long history of embedded technology to control mechanical processes. Commercial spaces, on the other hand, are classified here as those environments in which the majority of the space is dedicated to sheltering products and people engaged in wakeful activities (e.g., retail stores and shopping centers, sports arenas and other entertainment areas, transportation depots, office complexes). Enabling the drive to make these venues smarter—a frequent euphemism for remotely controlled and programmable—wireless installations for connecting monitoring and sensing devices reduce the cost and disruption associated with upgrading hardwired cable plants. In addition to interrupting the point-to-point connectivity between devices, remote access to devices is effected by entrusting commands to IP connections for which the security of these mediated connections between devices and architecture was not initially designed. A gap is created between signal transmitter and signal receiver. That gap is the playground for enterprising hackers.
Being smart is not synonymous with having good judgment.
Opportunities
When making the calculation about which target will derive the highest yield, “A device that is both connected to the Internet and enables third-party remote access is an external attacker’s prized desire.”2 The cost to the attacker of attempting digital access to a structure or asset—calculated as the risks of being caught or identified, wounded or killed by a security guard, prosecuted legally, incarcerated or otherwise penalized—is considerably lower than attempting simple brute force or even socially engineered physical access (e.g., tailgating, ID spoofing, distraction burglary). Granted, the digital hacker likely has more financial investment in tools and training. The immediate negative consequences of attempting a break-and-entry of a structure by using digital crowbars against wireless restraints are minimal, however, and physical access can be abetted by digital reconnaissance that enables disruption of locking mechanisms or surveillance and alarm equipment. Even improvements in digital forensics tools’ techniques are neutralized by improvements in hacker tools that effectively mask or erase evidence of the intrusion attempt. Lag time between incident and detection—and between detection and response—is frequently lamented by security professionals and appreciated by hackers. Evidence includes high-profile cases like Sony, RSA, Target, JP Morgan Chase, Home Depot, and others.
Hacks leading to data compromise display a variety of incident patterns, as captured in Table 5.1, which shows results from analyzing three years of large data breach incidents investigated by Verizon and others who contributed field reports for inclusion in the data digest. The results are sorted by primary North American Industry Classification Standard (NAICS) codes of the compromised organizations. Cyber-espionage figures especially prominently in critical infrastructure sectors like manufacturing, transportation, and utilities. These are also industry sectors that share certain technology platform characteristics, which will be discussed in the section on industrial applications.
Table 5.1
Three Years of Attacks Leading to Data Breachesa
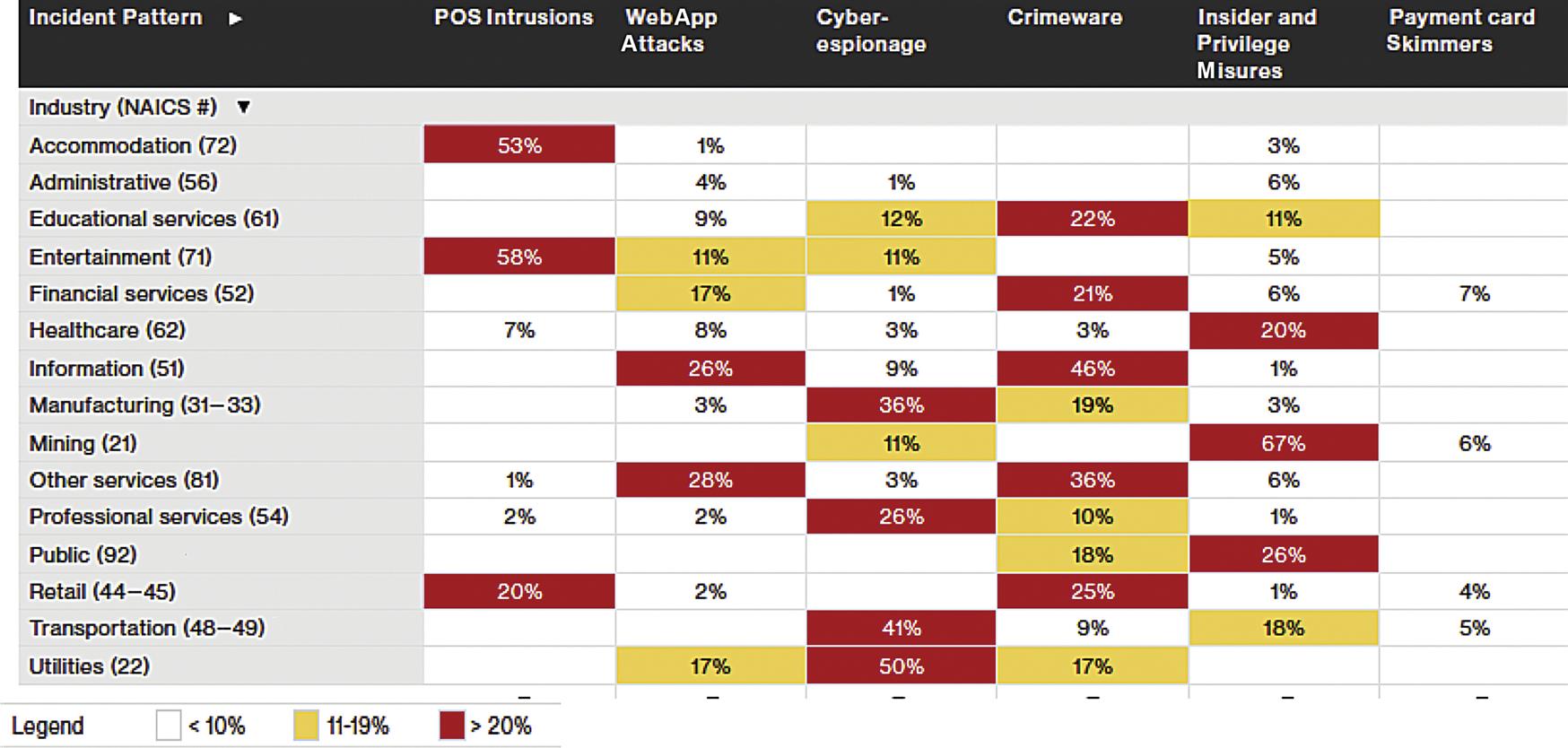
aVerizon Enterprise Solutions (March 2016), Data Breach Digest: Scenarios from the Field. Retrieved from http://www.verizonenterprise.com/resources/reports/rp_data-breach-digest_xg_en.pdf.
Commercial Space Taxonomy
All commercial spaces are not created equal with respect to how assets are valued by facility owners, managers, stakeholders, and potential hackers. These spaces also vary widely in terms of purpose, traffic, layout, and technology. They generally cluster along the “Four Ps” of access control preferences—promiscuous, permissive, prudent, paranoid—with respect to how physical access into the area is controlled. Existing technology implementations do not always align with and enable these declared access control preferences, however, and can create a serious disconnect between the level of physical and digital access control desired and the level actually achieved. This is especially evident in industry sectors that still rely on technology platforms built for point-to-point, direct connectivity (rather than the networked connectivity). Table 5.2 shows a general taxonomy of commercial spaces cross-referenced by physical access control philosophy and digital access control platform vulnerability. This will set the stage for discussion of attack scenarios based on hacking WAPs used in industrial and commercial applications.
Table 5.2
Comparison of Representative Commercial Venues, Physical Access Control Philosophy, and Digital Access Control Vulnerability
| Representative Venues | Physical Access Control Philosophy | Digital Access Control Vulnerability | ||||||
| Paranoid | Prudent | Permissive | Promiscuous | Paranoid | Prudent | Permissive | Promiscuous | |
| Church, synagogue | X | X | X | |||||
| Concert hall lobby | X | X | ||||||
| Gym | X | X | X | |||||
| K12 school | X | X | X | X | ||||
| Manufacturing facility | X | X | X | X | ||||
| Medical care | X | X | X | |||||
| Office building (government) | X | X | X | X | X | X | ||
| Office building (private) | X | X | X | X | ||||
| Prison, jail | X | X | ||||||
| Research laboratory | X | X | X | |||||
| Retail shop | X | X | X | |||||
| Shopping mall | X | X | X | |||||
| Sports arena | X | X | X | |||||
| Transportation lobby | X | X | ||||||
| University/college classroom | X | X | X | |||||
| University/college residence | X | X | X | X | X | X | ||
| Utility company | X | X | X | X | ||||
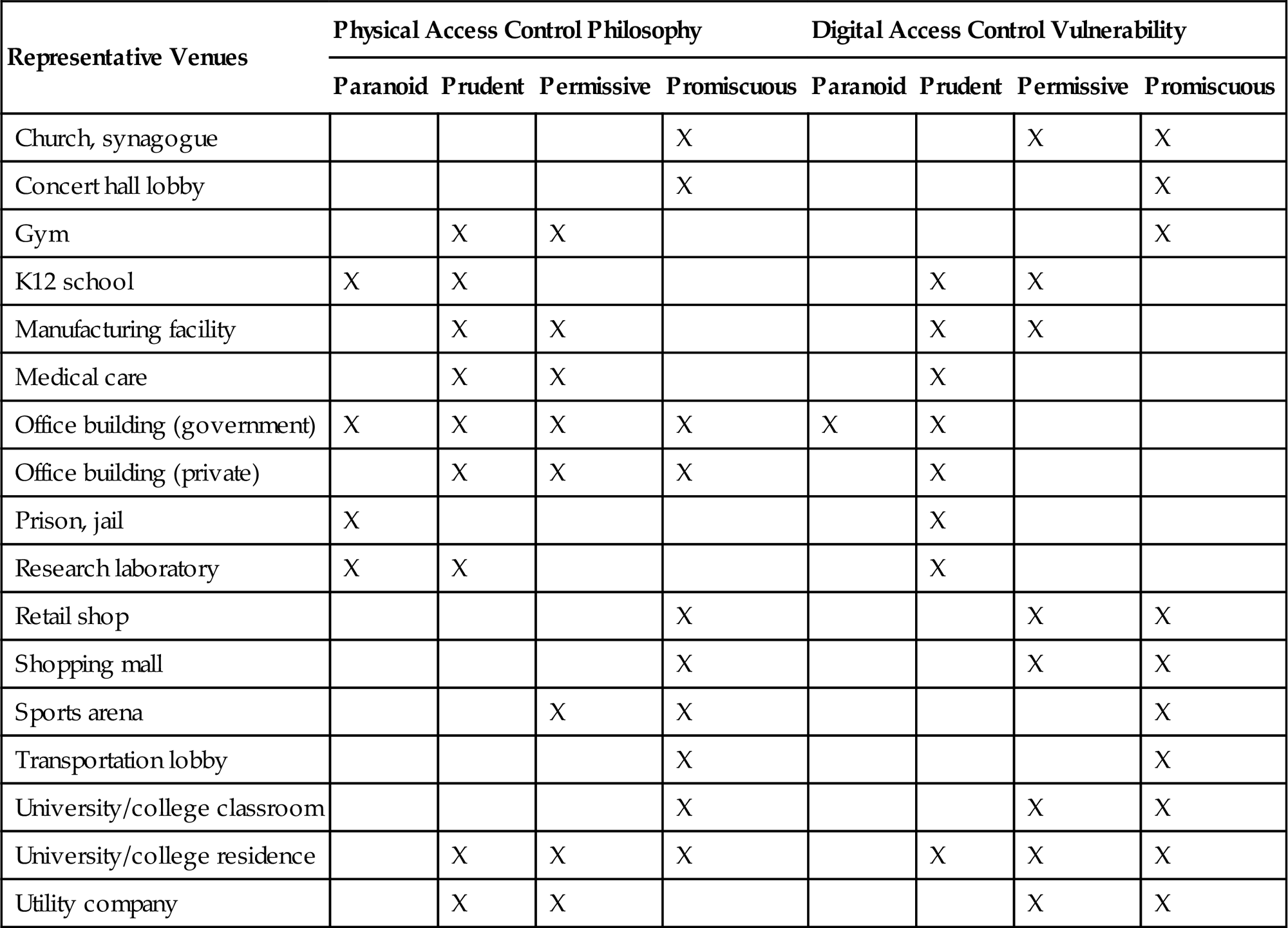
Using shopping centers and malls as an example, one can see that implementing sophisticated technology, even technology explicitly designed for Internet connectivity (as opposed to legacy systems designed for point-to-point connectivity), can open gaping holes in security systems and even abet attacks on remote targets if the technology is not deployed with the understanding that connected devices are WAPs. Intentionally promiscuous with respect to allowing anyone to enter physically, shopping malls are investing increasingly in sophisticated surveillance technology and training for security officers and retail/concessionaire employees. The International Council of Shopping Centers has invested $2 million to develop courses for security officers. A large (one million square foot (SF)) shopping center will invest up to that amount in annual security measures that include hundreds of surveillance cameras.3 As often is the case, however, that security investment can be undermined when insufficient attention is paid to the WAP nature of those cameras, which are part of a small computer system. Failure to harden cameras with robust login credentials (e.g., not changing manufacturer’s default passwords) or restrictions on connection requests enables botnet recruitment and malware downloading.4 This can work to the advantage of hackers looking to launch a distributed denial of service (DDoS) attack by exploiting Shellshock vulnerabilities5 and still-enabled Telnet ports.6
Industrial Applications
ICS encompass a range of systems and connected devices (e.g., SCADA systems; distributed control systems; and programmable logic controllers, PLCs). They are “combinations of control components (e.g., electrical, mechanical, hydraulic, pneumatic) that act together to achieve an industrial objective (e.g., manufacturing, transportation of matter or energy).”7 They are frequently systems that were intended for use within a local, confined physical area and not over shared communications channels: Point-to-point connectivity or direct physical access was required to make configuration changes. Similarly, these systems typically cannot be upgraded or patched from a central location. The systems are designed as long-term solutions with very limited downtime. As a consequence, fixes are applied irregularly and legacy systems are not assigned an end-of-service date as are components of an IT system.
Control systems can be classified according to whether they are intended for manufacturing use case scenarios or distribution. The former features more closely defined physical boundaries and direct communications links (i.e., wired vs. wireless, although that is changing with improvements in wireless reliability and throughput), whereas the latter often features broad geographic dispersion and switched or wireless communications links. Because signal latency can hinder the effectiveness of either category of control systems, some security practices recommended for hardening an IT system are contraindicated for an ICS.
The security triad of CIA still applies, but unlike most applications in which confidentiality is the most valued objective, here the continued availability of systems is the primary objective, followed by integrity and then confidentiality.
A partial list of attendees (Fig. 5.1) at the annual ICS cyber security conference, first held in 2002, hints at the variety of industry sectors that rely on ICS and are concerned about their vulnerabilities.

Burrow Attack: Stuxnet (Industrial Sabotage)
Hacker Objective: Command and control (C&C) over mechanical systems (most famously, an Iranian nuclear reactor)
Hacker Technique: Multilayer, multiple techniques (social engineering, credential compromise, four zero-day exploits)
Victim Impact: Physical damage to centrifuges; disruption of processes dependent on centrifuges (used to separate uranium isotopes: U-235 from U-238)9
Stuxnet was the big wakeup call that proved, even to skeptics, that the postulated disruption of mechanical systems—demonstrated in 2007 with the cyber-kinetic takedown of an industrial turbine by Idaho National Laboratory researchers—was feasible. The staged attack in 2007 prompted both mass media publicity and cautions against hype. The acting undersecretary of DHS’s National Protection and Programs Directorate at the time stated, “several conditions have to be in place. … You first have to gain access to that individual control system. [It] has to be a control system that is vulnerable to this type of attack. … It is a serious concern. But I want to point out that there is no threat, there is no indication that anybody is trying to take advantage of this individual vulnerability.”10
The (most likely) nation-state-produced, but not staged, attack against an Iranian nuclear reactor in 2009 demonstrated irrefutably that a well-funded, determined hacker team with insider knowledge about the Siemens s7 PLC could successfully compromise even hardened ICS. (A PLC vulnerability enabled infection spread via a compromised USB drive.) The attack against the Natanz uranium enrichment site was just one of the state-sponsored attacks in Iran.11 Under development since at least 2005, the actual Stuxnet attack against Iran’s Natanz site combined social engineering, MITM attack of the PLC (through compromised credentials), and four zero-day exploits.
Victim’s Chronology12
1. An infected USB drive is inserted into a computer on the Natanz network, whether intentionally (deliberate insider threat) or accidentally (e.g., the “dropped USB” ploy discussed earlier). The worm then uploaded to the facility’s network.
2. Stuxnet worm follows its programmed code to discover system-controlling software (Siemens s7).
3. Stuxnet takes over control of the centrifuges under the software’s control and either reprograms valves to close (version 0.5) or to alternate centrifuge cycle speeds (version 1.x), thereby accelerating centrifuges until spinning dangerously, then decelerating over a series of months.13
4. Weakened centrifuges had to be replaced: approximately 20%.
Just as attacks on biological systems wreak particular havoc when they cross species, so do attacks on cyber-kinetic-mechanical systems. The Stuxnet worm, for example, traveled to an estimated 100,000 computers, most of which were not associated with the initial target, Iran’s nuclear power assets. Different versions are at play. Although the original version (0.5) did not exploit Microsoft vulnerabilities and compromise centrifuge speed, later versions (1.x) did. Version 0.5 spread through removable media and email attachments. It contacted four C&C servers, hosted by commercial providers, which appeared to belong to an Internet advertising agency: Media Suffix. Version 1.x is more aggressive and created more collateral damage.14
Other attacks against industrial systems, attacks like Night Dragon (data theft)15 and Shamoon (sabotage through the destruction of data)16 that have targeted assets in the oil and gas industry (e.g., Saudi Aramco in 2012), reveal the persistent, methodical, multilayered techniques characteristic of state-sponsored activity. WAP exploitation provides an additional potential entry point for these malware products. It can accelerate their proliferation through the immediately targeted system and contribute to collateral damage that occurs when related systems are infected. Common attack surfaces are compromised individual mobile laptops (via spear phishing), although other common “business productivity” devices can also be compromised. The use of under-protected, off-the-shelf, consumer-grade applications—in conjunction with ICS environments that have historically been kept in isolation—is as potentially dangerous as sharing kindergarten toys would be for someone lacking effective immune systems (“boy in the bubble” syndrome).
At the individual consumer level, we are highly dependent on, but largely ignorant of, these ICS environments that represent critical infrastructure sectors, in particular, the chemical, dams, transportation systems, critical manufacturing, energy, nuclear reactors (and materials and waste), and water and wastewater sectors. Some medical equipment is susceptible to the kind of sabotage wreaked by Shamoon and Night Dragon when data or programmed code is either overwritten or intercepted. With the advent of smart cities, transportation systems, and even individual vehicles, the challenge of securing wireless devices from malicious attack becomes more urgent.
Commercial Applications
Other scenarios for using automated system are not as closely associated with the control of heavy-duty machinery and mechanical processes. Found in use cases like digital locks, sensors, environmental controls, and surveillance/physical security equipment, these commercial applications are frequently managed through WAPs. Smart buildings fall under this category.
Being more responsible and sustainable—more green—is frequently touted as the best justification for investing in smart technology for regulating building energy use, as is cost savings. But what is the total cost of ownership if security is not built into systems before deployment? Again, what is convenient for facilities managers is also convenient for hackers looking for a vulnerable WAP as an entry point. Indeed, the dilemma for the hacker might be to choose just one. Cisco’s openBerlin Innovation Center illustrates just how many sensors it can take to automate HVAC and illumination and eliminate manual switches: About 10,000 sensors are estimated for the 13,000 SF building.17 During regular work hours that equates to about 100 sensors per employee; the ratio changes, of course, nights, weekends, and holidays.
Again, in the tradeoff between cost and security, the latter can lose out. Consider the importance of centrally controlled, digital locks in maximum security prisons, for example, as a compensating control for the lopsided ratio of prisoners to guards. The central locking systems have cascading release functions, that is, they “fail open” in case of fire or other such emergency. One Florida prison experienced a couple of seemingly spontaneous “cascading releases” in its maximum security wing in 2013 that set all prisoners there free.18 Whether a malfunction, internal collusion, or external hack the concern is nonetheless vivid.
The locking systems implemented in prisons are often not sufficiently hardened. Usually the PLCs that control mechanisms like doors are programmed using Ladder Logic, a simple program that is convenient for programmers—and vulnerable to exploitation. Prepackaged exploits are available online at <Exploit-DB.com>.19 PLCs reduce wiring costs (as do wireless networks) and are desirable in these early examples of smart buildings that use electronic systems to control intercoms, illumination, surveillance, water, bathing facilities, and so on. Good news for the would-be hacker: “Access to any part, such as a remote intercom station, might provide access to all parts.”19
Due to the “always on” requirement for PLCs that control the physical world (e.g., door locks, environmental controls, surveillance), deploying an intrusion prevention system (IPS) is not desirable. The IPS is built to interrupt processes if an anomaly is detected. Consider, for example, the fail-open design of building egress or even prison cell doors. Although the PLC default position might be locked, during a power failure or emergency doors are programmed to open so that people are not trapped. Downtime for maintenance thus is closely coordinated and minimized. The weekly patching schedule common in an IT system (in contrast to an IC system) would not be practical.
These PLC environments cannot be disconnected from the Internet without disrupting business activities. In the case of prisons, for example, both operations (e.g., commissary replenishment and other supply chain coordination activities) and administration (e.g., mandatory reporting to federal oversight agencies) require connectivity to the outside world. Wireless channels are used for improved surveillance coverage, reduced network cabling costs, and for mobile applications. Patrol cars covering a facility’s perimeter, for example, transmit videos wirelessly and unencrypted to guards inside. Those and other videos are easy to find on YouTube and various other mass media websites.19
Automated sensors like motion- and heat-detection devices are also used for perimeter control in built environments ranging from residential neighborhoods to skyscrapers to civilian and military government facilities to transportation depots to power-generating stations. High-value, albeit geographically remote and minimally manned, assets like power transmission stations present an attractive use case scenario for deploying sensors to detect physical intrusions, geophysical disturbances (e.g., earth tremors), utility equipment condition, and environmental hazards (e.g., fire). Using ultra low-power, tiny sensors, which are immune to high voltage, in a mesh network can offer coverage over a broad area surrounding transmission stations, eliminating the need for on-site personnel and fixed equipment installation like cameras.20 The security challenge is not trivial, however. Requirements for low battery use compete with the energy drain presented by the more intensive processing power needed for encryption or an IPS (to protect the digital information). Each solution seems to beget another potential vulnerability.
In addition to building access control, other uses for ICS in any smart building (not just a personnel containment facility) underscore the dependence on consistent power supply and automated controls for which availability—continuous functioning—overshadows latent concerns about confidentiality and integrity. Smart buildings act as a microgrid; with increased deployment of solar and other alternative sources of energy, this characteristic will become even more prevalent. Wireless sensors are used to help control energy use; detect smoke and fire; monitor HVAC systems (essential to maintaining temperature control for heat-averse servers and other computing equipment) for fault detection, diagnosis, and prognosis; promote worker safety and reduce injury in manufacturing facilities. Other sensors are used to support human comfort and hygiene needs, for example, lighting and touch-free water faucets, soap dispensers, and hand dryers.
Takeaways
What is convenient for one is also often convenient for another. Likewise, a cost savings for one can also mean a cost savings to another. Relying on a uniformly digital strategy, even one that uses an array of products for protecting various OSI layers, is less diverse than one that integrates analog along with digital products.21 Raising a hacker’s cost of exploitation by layering digital and analog control mechanisms can reduce your attractiveness as a target; the risk-averse, profit-motivated hacker may move on. (All bets are off, however, for the state-sponsored hacker.)
Depending on technology alone as the hardening guarantor for any system is a disingenuous way of outsourcing responsibility and falls short of meeting due care and due diligence commitments. Facilities managers may hope to simplify their job responsibilities and costs by avoiding the vagaries of recruiting, managing, training, and retaining people, and accommodating occasional personnel “outages” (e.g., holidays, weekends, sickness, resignation/termination). Automated systems can be set up as “always on” (given sufficient redundancy) with reduced expectation of malfunction. Still, the possibility of cascading failures across systems that are all interconnected digitally requires their hardening and, perhaps, their digital discontinuity through the implementation of analog components as additional security gates. If the legitimate remote administrator cannot move laterally across networks, neither can others (as happened to Target).
What does a hacker not want to encounter?
![]() Isolated, hardened credentials that are stored prudently (no password files entitled passwords or access codes, etc.)
Isolated, hardened credentials that are stored prudently (no password files entitled passwords or access codes, etc.)
![]() Unique administrator accounts that do not use manufacturer defaults
Unique administrator accounts that do not use manufacturer defaults
![]() Mechanical systems that require physical access
Mechanical systems that require physical access
![]() Security that lives with data under all three states—at rest, in motion, or in process—as well as at the edge of communications networks
Security that lives with data under all three states—at rest, in motion, or in process—as well as at the edge of communications networks
NIST has compiled a solid list of guidelines for addressing security in automated systems. These guidelines should apply at all layers of the embedded architecture including WAPs. The latter must be hardened and protected as well. The NIST guidelines recommend the following security objectives:
![]() Restrict logical access to the ICS network and network activity
Restrict logical access to the ICS network and network activity
![]() Restrict physical access to the ICS network and devices
Restrict physical access to the ICS network and devices
![]() Protect individual ICS components from exploitation
Protect individual ICS components from exploitation
![]() Restrict unauthorized modification of data
Restrict unauthorized modification of data
![]() Detect security incidents and incidents
Detect security incidents and incidents
![]() Maintain functionality during adverse conditions
Maintain functionality during adverse conditions
![]() Restore the system after an incident22
Restore the system after an incident22
Implementing these objectives successfully requires thoughtful deployment of technology, policies, and personnel. User activity with respect to devices, including WAPs, should be tracked by individuals rather than by user role accounts (e.g., system administrator). The business-to-business or machine-to-machine activity must also be tracked and parameters for normal behavior set to facilitate anomaly detection.
Segregation of ICS from internal administrative networks and both from public access networks within facilities should be seriously considered. The FAA, for example, has mandated that on-board Internet access on aircraft have no common components with the communications infrastructure used to control and communicate with the aircraft. This is to protect against hackers taking down an airplane. Such a best practice should be adopted by ICS users since the cost of multiple wireless systems in a facility (each with its own unique encryption passcode) can be much less than the cost of recovery after a breach (approximately $179 per record compromised23).
Connectivity between ICS, administrative networks, and public access networks should be tightly controlled and monitored. Gateways between the networks should be limited and provisioned with policies to restrict the flow of data. Anomalies should be routed and handled by personnel to ensure the communications are appropriate. Security should not be relaxed to support a business partner. These best practices have been successfully used by the US Department of Defense (DoD); businesses need to adopt these practices in their ICS environments. Approximately 82% of critical infrastructure that is dependent on ICS is owned and managed by private sector, nongovernmental organizations.
Remote communications into ICS and administrative networks should be secured through the use of VPNs, and possibly additional encryption mechanisms, because nonsecure communications over the Internet and over WAPs make industrial espionage easier. When designing the wireless network architecture, latency issues must be considered: Mission-critical controls on ICS require a dedicated network without encryption. Monitoring the ICS remotely does not require subsection response time. Here one should use encryption with the remote monitoring (via a gateway, not any ICS device) so hackers cannot see this traffic.
These three features (network separation of functions, strong controls of information flows across networks, and secure remote communications) will make organizations and companies a less desirable target of convenience. For critical infrastructures and critical manufacturing and processing (e.g., food and medical) organizations, these features are necessary but not sufficient to protect against industrial espionage and sabotage. Here intrusion detection systems (IDS) and analysis of device logs (e.g., database access, performance and utilization logs for robotics) for anomalies can act as an early warning system for attempted and actual breaches of networks. An IDS is preferable to an IPS because the latter can be gamed by a hacker to shut down the system. While it is likely APT will most likely occur on one’s public network, monitoring of all networks is needed to ensure that malware is not (intentionally or unintentionally) introduced into the administrative and ICS networks.
Automated business-to-business activities generate a significant amount of IoT value: as much as 70% according to one analyst group.24 Individual, robust (not manufacturer’s default) passwords are essential, as is separation of duties on the part of administrators wherever possible. External access by vendors should be limited and segregated from other network access—and vendor internal security policies should align with those of customers so that neither becomes a target (or Target). The convergence of the physical and digital environments presents challenges when disparate security priorities—confidentiality, integrity, security—compete for precedence within the same organization. The health care industry combines those environmental challenges with critical, life-and-death consequences when a WAP failure in either the IT or IC systems bleeds into the other.