1 Background of the Critical Infrastructure Protection (CIP) in Japan
In the last few decades, remarkable developments in ICT (Information and Communication Technology) and OT (Operational Technology) have been promoted and a variety of hardware, software or networks have been implemented to the operations and controls of the national critical infrastructure (CI) services. In addition to this trend, many CI service providers have been aggressive in introducing outsourcing, multi-platform technologies, open-architecture design, cloud computing, big data analysis, or IoT (Internet of Things) to achieve more effective and flexible operations with less costs and more efficiency. As a result, our society is enjoying higher value-added and flexible CI services but at the same time, the dependency of CI operations and service delivery on ICT and OT have been increased dramatically. We have started to experience critical disruptions of CI services caused by ICT and/or OT failures and also by intentional cyberattacks.
Defined 13 critical infrastructure sectors and major systems (Cybersecurity Policy for Critical Infrastructure Protection, 2017)

- (1)
Information and Communication Services
- (2)
Financial Services (Banking/Insurance/Securities)
- (3)
Aviation Services
- (4)
Railway Services
- (5)
Electric Power Supply Services
- (6)
Gas Supply Services
- (7)
Government and Administrative Services
- (8)
Medical Services
- (9)
Water Services
- (10)
Logistics Services (Freight and Shipping)
In 2016, the following three CI sectors were added considering increasing socioeconomic impact of its disruptions;
- (11)
Chemical Industries
- (12)
Credit Card Services
- (13)
Petroleum Industries
and Airport Services (including terminal operations, ground handling, and immigration/customs operations) will be added as the 14th CI in 2018 which are separated from the Aviation Services, the third defined CI.
2 Challenges of the PPP (Public-Private Partnership) and Intensive Efforts Through Annual Cross-Sector Cybersecurity Exercises
Overview of the cross-sector cybersecurity exercises in 2006–2008 (based on published data from NISC)
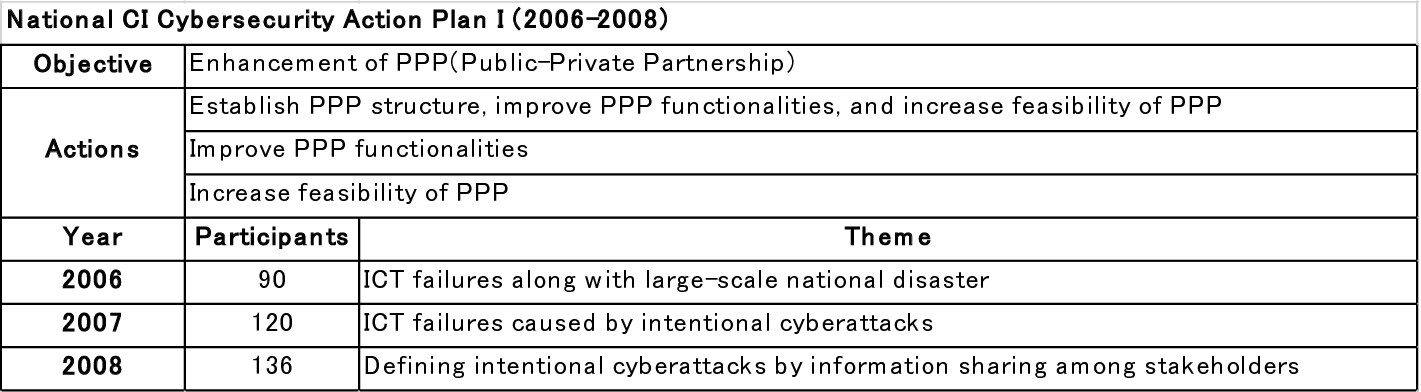
In the 2006 exercise, 90 people participated from the original ten CI sectors and their regulatory agencies. The motivation of the participating CI service providers was not so high because of the presence of their responsible regulatory agencies.
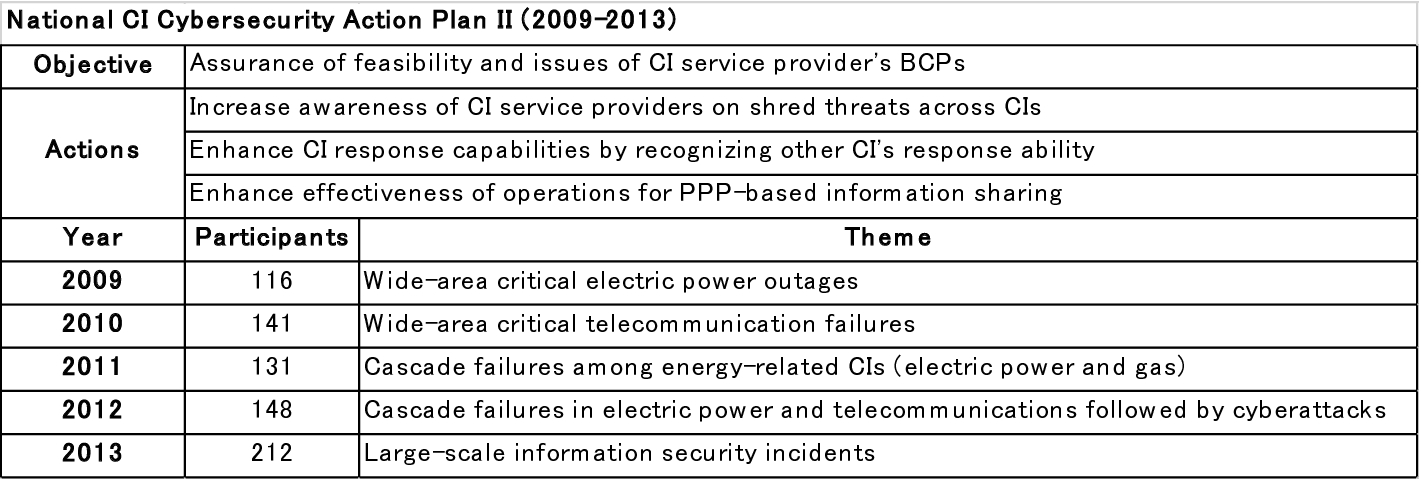
Overview of the cross-sector cybersecurity exercises in 2009–2013 (based on published data from NISC)
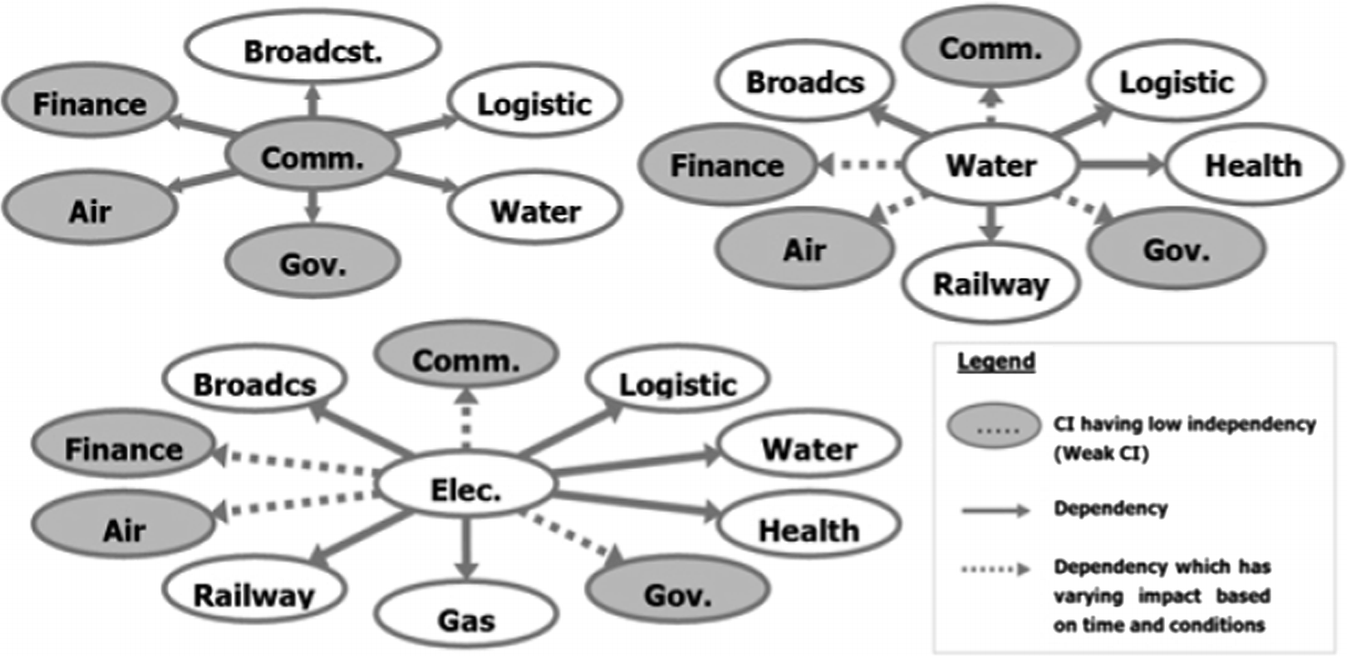
Result of dependencies among CIs (NISC, 2007 translated by Z. Aung.)
The case study analyzed cascaded incidents among CIs after the earthquake hit and evaluated interdependency of each CI and dependencies among CIs. (The solid arrows indicate clearly recognized dependencies and the dotted arrows indicate partially recognized dependencies)
The committee’s analysis works examined and utilized the existing frameworks and methodologies including an analytical planning framework for hypothesizing, formulating, and mitigating vulnerability in CIs [4, 5].
Overview of the cross-sector cybersecurity exercises in 2014–2016 (based on published data from NISC)
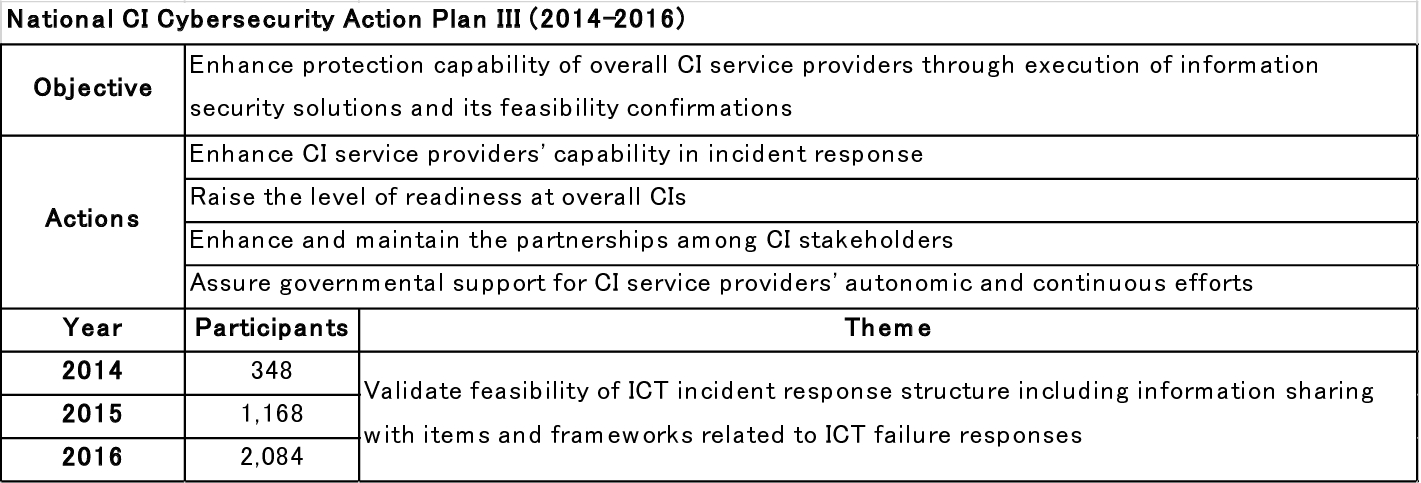
Maintenance and Promotion of the Safety Principles
Enhancement of Information Sharing System
Enhancement of Incident Response Capability
Implement Risk Management Framework and Preparation of Incident Readiness
Enhancement of the Basis for CIP
and The Cybersecurity Strategic Headquarters strongly recommended CI service providers to apply PDCA (Plan-Do-Check-Act) management cycle in their cybersecurity enhancement efforts with BCM (Business Continuity Management) framework and at the same time, the annual cross-sector cybersecurity exercises have been aggressively enriched in scenario and operations. The fundamental objectives of the exercises were almost same and included information sharing among stakeholders in the public and private sectors related to the CIs. The establishment of interoperability for the coordinated incident responses was promoted.

“To Be” structure for Information Sharing and Shared Incident Response (Cybersecurity Policy for Critical Infra-structure Protection, 2017)
Need to learn how to devise a wide range of response patterns based on limited information
Need to consider response with limited resources to attacks that occur late at night or in the weekend
Need to apply lessons identified in the exercises to improve CIP or CIIP (Critical Infrastructure Information Protection) at each CI service provider.
Those outcomes have been reflected on the Developing Guideline for Safety Standards at Critical Infrastructures to Assure Information Security [6].
3 Limitations of NISC’s Cross-Sector Cybersecurity Exercises and Alternative Approaches that Complement It
NISC’s over ten years’ arrangement for the cross-sector cybersecurity exercises have had limitations in designing advanced scenarios for experienced CI service providers and in dynamic on-site scenario arrangements along with each response of the exercise players. This is because the basic scenario of NISC’s exercise is to raise awareness on the necessity of building PPP-based interoperability in cyber incident responses with broadening the horizon of participants from CI service providers. As a result, the scenario which is used at the exercises has been pre-set and shared with all participants with a few options which will be provided by sub-controllers assigned for each CI sector.
On more thing is the lack of aspect of “region” because the basic structure of the exercise arrangements are made by industry in collaboration with their applicable responsible governmental agencies. This situation makes it difficult to assure interoperability across the CIs in responding to chained cyber incidents caused by dependencies among CIs in a specific region.
In order to compliment the limitations, CIs in Nagoya (4th largest city in Japan) district have started region-focused cross-sector cybersecurity exercises with dynamic dependent scenario while working with local police and municipal governments. The range of participants is wider than NISC’s definition and include major manufacturing industries (mainly automotive) which the area heavily depend on to keep up its economy and employment. Their first exercise was on the same date of the NISC’s exercise in 2017 and based on NISC’s scenario but many customized additional scenarios injected. One of the major injection forced one of the CIs to shut down their system proactively and required the CI to notify other CIs and also local governments to evacuate and shelter the citizens.
Stability: Stable services with expected quality and state
Robustness: Capable of performing without failure under a wide range of conditions
Availability: Assured quality or state of being available
Expandability: Capacity to increase the extent, number, volume, or scope
Safety: Condition of being safe from external intrusions and internal leakages
Flexibility: Ready capability to adapt to new, different, or changing requirements
Reliability: Quality or state of being reliable
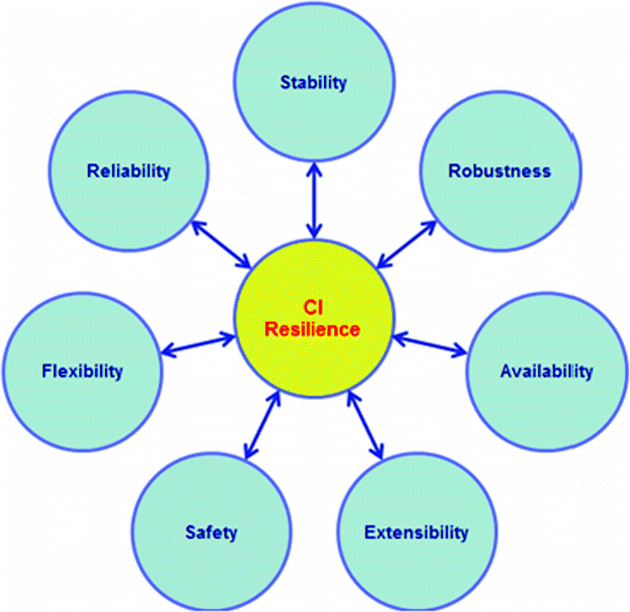
Functional requirements for CI operations and systems

Functional requirements in the case of natural disasters
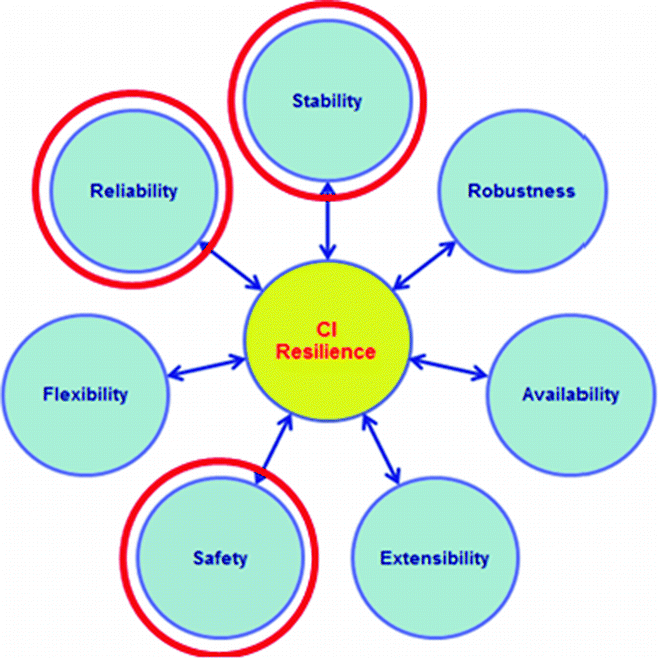
Functional requirements in the case of cyberattacks targeting CI control systems

Cyber incident response structure by pre-determined emergency level
Many Japanese CI service providers had experiences in emergency response to the severe situations caused by the large-scale natural disasters in the past such as earthquake, typhoon, or flood with the command and control structure headed by their CEO. However, in the exercise with a cyberattack scenario, several hesitations had been observed in escalation or reporting, and decision making for proactive shutdown of their control systems because of its impact to the socioeconomic activities and the citizen’s life.
4 Conclusions and the Next Steps and Challenges of CIP with PPP-Based Cyber Resilience Enhancement in Japan
With the intensive efforts in the CIP lead by the Japanese Government, readiness for cybersecurity incidents in CIs has been enhanced during the last over ten years. However, at the same time, CIs’ dependencies on ICT and OT have increased and cyberattack techniques have advanced. The Japanese PPP-based efforts for cybersecurity in CIs are facing the following challenges for which the CI service providers and government sectors have to work together more tightly to make next steps dynamically to enhance cyber resilience of our society:
(1) Dynamic and interoperable PPP-based operations
Need more organic and trust–based information sharing and coordinated incident responses among stakeholders in the CI service providers, responsible government agencies, and major CI users. Bilateral CI-CI exercises and region-focused exercises such as the Nagoya’s exercise addition to the centralized NISC’s exercises will be effective to make the PPP-based operations more dynamic and interoperable.
(2) Proactive incident response structure at CI service providers
Leverage existing CSIRTs (Computer Security Incident Response Teams) and SOCs (Security Operation Centers) in the process of BIA (Business Impact Analysis) and SIA (Social Impact Analysis) and make them as “interpreters” between cybersecurity operational level and enterprise management judgement level. Some of the CI service providers have already integrated their incident response operations for cybersecurity and for natural disasters.
(3) Professional development and networking
Develop professionals who understand cybersecurity, business administration, and emergency response in order to achieve (1) and (2). In 2017, the Japanese Government has launched an one year intensive professional development course that invited full-time participants from major CI service providers and the first 50 graduates are expected in June, 2018. Mid-long term career development strategy will be required and also a networking scheme among professionals in the stakeholder organizations of CI service providers and responsible governmental agencies is necessary.
(4) Local government involvement for regional cyber resilience enhancement
Considering the emerging possibility of cyberattacks targeting disruptions of CI services and social disorders in a specific city or in a specific event period, information sharing and shared incident response structure with interoperability among stakeholders in a specific city or area are necessary. In this structure, it is very important to involve local governments to protect safety and well-being of the people (residents, workers, and visitors) [8]. In 2018, local governments (prefectures and cities) and more local police departments are expected to join the Nagoya’s region-focused cross-sector exercise.