1 Introduction
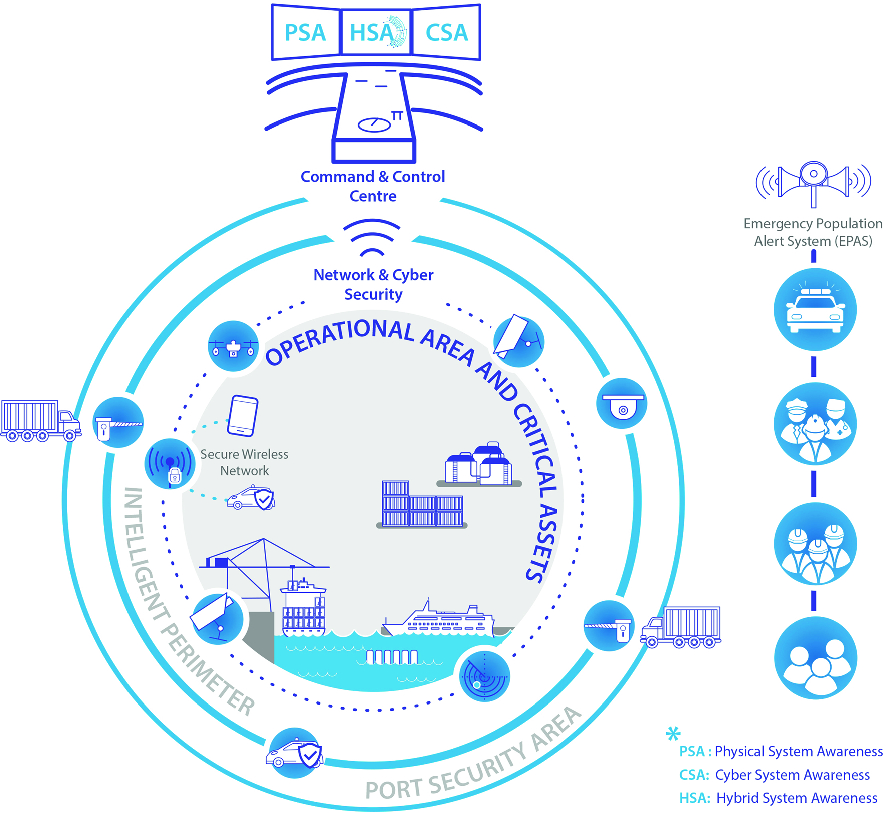
Conceptual overview on the general idea behind the SAURON project.
Technical solutions to detect and counter such attacks are at hand and port infrastructures as well as all critical infrastructures use them in their everyday business life. Physical Situational Awareness (PSA) systems provide operators with the required overview on the prevailing situation of their physical assets, aggregating information from video surveillance, access control or fire detection systems. Similarly, Cyber Situational Awareness (CSA) systems provide details on the current status of the cyber systems, utilizing network traffic analyzers, intrusion detection systems (IDS) or log file analyzers. However, if an incident is detected, none of these systems is capable of identifying and analyzing cascading effects, particularly with regards to the respective other domain. Furthermore, combined attacks, i.e., attacks using both physical and cyber attack vectors, cannot be detected by either of those systems, in general. Therefore, a holistic overview on relevant incidents originating in one of the domains and their effects on both domains is required.
In this article, we present a conceptual framework for such a Hybrid Situational Awareness (HSA), developed in the context of the SAURON project for maritime port infrastructures. This HSA is capable of determining the potential consequences of any relevant incident detected either by the PSA or the CSA and will show the potential cascading effects in the two different domains. Therefore, the HSA generates a graph representation of all assets (physical as well as cyber) within the port infrastructure, also taking their intra- and inter-domain relations into account. Using mathematical models based on Markov chains and computer simulation techniques, the HSA can calculate how an incident will propagate through this graph and which assets are most likely to be affected. To identify combined attacks, the HSA is equipped with a correlation engine which associates incidents from the physical and the cyber domain and identifies potential threats using a rule-based approach. The HSA, as described here, is designed to work within port infrastructures but can also be applied to any other critical infrastructure operating large physical premises and complex cyber systems.
2 Related Work
Situational awareness (SA) is regarded as “the perception of the elements in the environment within a volume of time and space, the comprehension of their meaning, and the projection of their status in the near future” [11]. In this relation, PSA systems consist of those providing a complete knowledge of the situation to the decision makers by preventing and detecting any kind of physical threat in real-time. Besides the classical sensors to support a PSA (e.g., video surveillance systems, smoke or presence detectors), positioning systems have become more and more important to obtain a precise overview on the organization’s premises and the location of security personnel within. For example, a 3D mapping and real-time provision of aerial images are earth observation techniques supporting crisis management [20]. However, it has been demonstrated that typical SA measurement techniques appear to be inefficient for command & control, communication, computer and intelligence systems.
In the context of critical maritime port infrastructures, the PSA is of particular importance due to the large physical premises operated by ports. A general overview on the existing different approaches in this field are given in [4, 5]. Some implemented solutions for both US and EU port scenarios are introduced in [17, 22], respectively. Finally, a cyber-physical collaborative self-assessment and management system for protecting port facilities is presented in [23].
Whereas there are several theoretical approaches and many practical implementations for physical and cyber situational awareness systems, there are little to no solutions looking at the interlink between those two domains to identify cascading effects among them. However, there are several methodologies already present in the literature for analyzing cascading effects in general. One of the first was the Cross Impact Analysis (CIA) [13, 30], which generally describes the relation between events and how one event would affect another one in the future. A more recent extension to CIA, called Cross Impact Analysis and Interpretative Structural Model (CIA-ISM) [7], is extensively used in emergency management to analyze the interaction between critical events and obtain a reasonable view on potential future consequences (cf. [31] and the references cited therein for a more detailed overview on CIA and CIA-ISM).
The CIA and its extension are based on a rather high-level model, using conditional probabilities to describe the relations between specific events. Such stochastic processes are also used in several other approaches, in particular, the application of randomness improves the modeling of sometimes unknown dynamics between these events. One example for this is percolation theory from the field of epidemics spreading [28, 29], which can also be applied in cyber security to analyze the propagation of malware spreading within an ICT and SCADA network [19]. Another approach are Interdependent Markov Chains (IDMCs) which have been originally used in the energy sector to analyze overload scenarios and to take care of the probability for a blackout [27, 32]. The most recent advances of modelling cascading effects in power systems is surveyed in [14]. The IDMCs have been extended to model the propagation of cascading effects within an infrastructure [26].
3 Physical Situational Awareness
The PSA application of the SAURON system is responsible for providing continuous SA to the decision makers in case of a declared physical attack. It is linked with both the port’s security and responder teams and, in combination with the CSA, the PSA helps the commanders evaluating the current situation. This will support more accurate decisions for mitigating the consequences of a crisis. In particular, the PSA application consists of a real-time SA system adapted to the EU ports’ requirements for their protection against any type of physical threat. This includes novel capabilities as dynamic assets and resource locations, management and monitoring of the sensors deployed on the ports. In addition, it provides innovative video processing techniques, which will improve both the access control to critical areas and the security inside the port facilities, that will be integrated in the system.
The PSA application is mainly composed of three internal modules: the Security & Privacy module is responsible for ensuring the PSA system’s security in terms of access control. The Communications Interface module is composed of several logical interfaces that ensure the integration of different types of data (e.g. video-cameras flow, units on field’s alerts, other sensor’s alerts, etc.). Further, the Physical Situation Awareness module includes the different internal sub-modules that provide the specific PSA application features. Moreover, the system will prepare the received sensor data to be displayed in a proper way in the PSA Human–Machine–Interface (HMI), avoiding information overflow for the PSA application operators and decision makers. The PSA collects information from different sources, e.g., video-cameras, units on field, geo-location (GIS) systems and other sensor, and stores everything in the central Data Management Module. The information is then analyzed in the System Kernel Module, where anomalies are identified, processed and finally visualized using the HMI Module. Based on the resulting information, the PSA users can trigger alerts which will then be sent to the HSA application for analyzing potential cascading effects (cf. Sect. 5 below).
4 Cyber Situational Awareness
Cyber Situational Awareness (CSA) refers to a system which allows to prevent and detect threats and, in case of a declared attack, mitigate the effects of the identified infection/intrusion. In SAURON, this is achieved by combining traditional cyber security monitoring tools with innovative visualization techniques and threat hunting capabilities based on anomaly detection. The CSA provides its detection capabilities by means of a cyber security monitoring platform, which is able to monitor, process and analyze data coming from multiple information sources. These sources are classified as both cooperative and non-cooperative environments, depending on the information coming from the ports’ own infrastructure or from other open sources, respectively. Data from both the cooperative and non-cooperative environment is sent to the CSA Correlation Module to generate contextualized alerts, which support SAURON operators to take decisions based on the resulting risk level. In this way, the CSA aims to identify any situation that might boil down to a potential threat for any of the port authority’s assets. The CSA is implemented using a modular layered approach consisting of a Sensoring Module, a Correlation Module and an Alert Module. In the Sensoring Module, coordinated cyber security sensors gather relevant information from different sources on a real-time basis using an agent-based architecture. These data sources include IDS, system availability signals, network usage and bandwidth monitoring as well as active vulnerabilities in the current technological infrastructure.
The collected data is further processed by the Correlation Module. The module aims are to normalize, aggregate and reduce the information towards a list of alerts pinpointing what is really relevant in terms of cyber security threats. When an event is received on this correlation platform, a set of rules is executed in the Correlation Module in real-time in order to match relevant compromised situations based on severity, alert classification, type of attack and criticality of the affected assets. When the Correlation Module determines that a particular situation is relevant for the port’s security, all gathered information about the current situation is received as an alert by the Alerts Module, helping the operators to manage alerts and make decisions. The alert is also sent to the HSA for evaluating potential cascading effects (cf. Sect. 5 below). Based on the criticality of the detected alerts and taking the information data flow into account. Therefore, the alerts are used to identify both impact and probability of a set of predefined threat groups. Additionally, the CSA system includes new visualization paradigms for the cyber space, which consist of a section in the Alerts Module showing the attack affected assets as well as the external affected IP addresses showing the attack.
5 Hybrid Situational Awareness
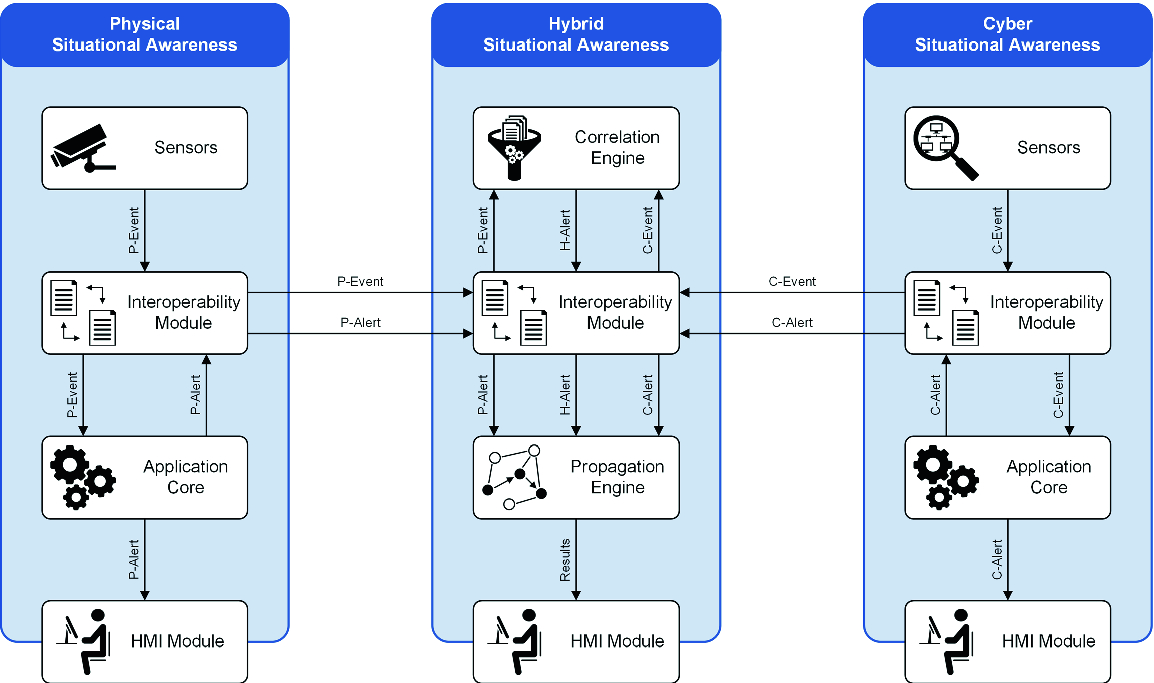
Illustration of the interplay between PSA, HSA and CSA.
5.1 Event Correlation Engine
The purpose of the Event Correlation Engine (ECE) is to interpret the detections and events provided by both the PSA and the CSA in a higher level of situational context. As the HSA receives information from both the physical world and the cyber world, it has a more comprehensive overview on the current situation. Therefore, the ECE is based on a complex event processing approach [12, 21] that intents to recognize, in real-time, specific patterns of event-objects within a flow, coming from heterogeneous sources, and triggers the corresponding actions. In this paradigm, an event-object (also shortly called event) is defined as a record of something that happens. It has a semantic representation that can be processed by a computer, is timestamped and may have a duration and a spatial localization. Its representation is not unique and is related to the purpose of its processing.
The ECE is based on Drools Fusion [24] and follows its inference rule syntax. Thus, the standard logic operators are used together with the temporal logic ones, as described in [1, 2]. Additionally, any boolean constraints can be applied on the attributes of an event in order to check contextual conditions (relatively one event to the others or to general conditions). Lastly, when the event types are defined from a hierarchical type modeling (an ontology, a class hierarchy or similar), the embedded is-a inheritance relationship is then useful to factorize definition of rules. When an event-pattern is applied for a certain type of event, it is also applicable (without any explicit marker) to all of its sub types. Therefore, the descriptive capability offered is very large and may encompass most of the threat situations the ECE has to recognize. It is stimulated each time a new event is received and is a candidate to at least one rule. All stimulated rules are latent until a satisfiability decision can be made (i.e., the event-pattern is satisfied or can’t be satisfied anymore). The rules defined in the ECE must be compliant to the necessary prior risk analysis of the port infrastructure. As the correlations are not discovered or learned but recognized, it is important to design them accordingly to the detections capabilities and the rational of the detections sources deployment. Further, it is obvious not to wait for events or patterns that never occur because neither the PSA nor the CSA are able to detect events feeding the expected schema. This is not only true for the inputs, but also for the outputs of the ECE. When some rules are triggered by a series of events, the ECE creates a Hybrid Alert, which is then sent to the Threat Propagation Engine and also displayed to the security officer.
5.2 Threat Propagation Engine
The Threat Propagation Engine (TPE) identifies the potential cascading effects of incidents coming from the physical domain, indicated as Physical Alerts, and the cyber domain, indicated by Cyber Alerts (cf. also Fig. 2). Moreover, Hybrid alerts coming from the ECE are also considered. To achieve that, the TPE builds upon a graph representation of the port’s infrastructure. The nodes in this infrastructure graph represent all assets, physical as well as cyber, within the port. The (directed) edges represent the different types of interdependencies between these assets, i.e., they describe how the assets are linked together. In the physical domain, such a dependency can mean that a machine is placed within a specific room or some rooms are located next to each other within a building. In the cyber domain, this can mean that an application is running on a specific server or two services are exchanging data for operation. Regarding dependencies between the physical and cyber domain, these can represent that an operating system is installed on a physical server, which stands in a certain room, or a service controls some physical machinery within a specific area of the port.
Each alert received by the TPE contains the information about which asset is directly affected by it. The TPE now inspects the infrastructure graph and evaluates which other assets (physical or cyber) might become affected by the incident. This evaluation builds upon a mathematical model using Markov chains previously described in a similar context [18]. Markov chains do fit the purpose quite well because, in general, cascading effects do not depend on the history but only on the current situation. Each asset itself is modeled as Markov chain which reflects the status of the asset in terms of likelihood to be affected by an incident. This likelihood and the state of each asset is represented by the labels, e.g., “normal operation”, “partly affected” or “completely affected”. The state of an asset depends on the states of its neighboring assets in the infrastructure graph. The probability that an affected asset has an effect on another dependent asset is again modeled by a Transfer Markov Chain. State changes are probabilistic and described by the transition matrix of the Markov chain; thus the non-deterministic behavior, which we regularly see in realistic scenarios, can be captured by the model.
In other words, if the TPE receives an alert, it changes the state of the affected asset; based on the model’s transition matrix, the assets next to it might become affected, too, due to their dependencies and change their status accordingly. In a next step, the dependencies between the newly affected assets and their neighbors are evaluated and additional assets change their state. This describes how an incident propagates step-by-step through the port’s physical and cyber infrastructure. The TPE simulates this propagation several times to obtain a list of the affected assets together with an estimation of their likelihood to become affected by the initial incident. As a main results of the TPE this list is then visualized for the security officer in the HSA’s HMI to support their mitigation actions.
6 Use Case Application
The use case we are focusing on here is one of two scenarios covered in the SAURON project and evolves around a terrorist group using combined attack vectors (from the physical and cyber domain) to enable a physical attack on the port’s infrastructure.
Scenario Description. The scenario takes place in a large port infrastructure, located inside a metropolitan area, operating a large container terminal. A terrorist group plans to access the port’s Terminal Operating System (TOS), which stores all container movements and their position, as well as the Port Community System (PCS), which runs all the communications between the port and their stakeholders. The main goal is to change the ID of a specific container arriving later on at the port ensuring that it is hidden within the container terminal and not subject to inspection. In this container, a small bomb equipped with some radiological substance is located. Upon arrival of the container, some members of the attacker group access the cargo area and activate the bomb. Thus, the plan is to infiltrate the TOS and the PCS by remote access or social engineering, to enter the port’s premises by exploiting weak spots in the port’s physical security and activating the bomb using a timer. The detonation on the next day would not only affect the whole port facilities due to the physical damage but also affect a large part of the city due to the spreading of the radiological substance.
Hybrid Analysis of Scenario. The described scenario combines attacks in the cyber and the physical domain. Hence, all three applications of the SAURON system, i.e., the CSA, PSA and HSA will be involved in the detection. First, the infiltration of the TOS by the attacker group leaves some traces in the network or system log files, e.g., if some exploits of the TOS are used to gain access remotely. These anomalies are detected by the sensors attached to the CSA and the CSA’s Correlation Module. Thus, an event is triggered and sent to the operator for a check as well as to the HSA for further evaluation in the ECE. In case the CSA operator identifies the event as malicious, an alert is triggered and sent to the TPE within the HSA. The cascading effects are analyzed.
In a similar way, the infiltration of the PCS and the tampering of the container’s ID by the attacker group later on can also be detected by the CSA, causing an event to be created and displayed to the CSA’s operator as well as sent to the HSA. If the CSA operator decides to create an alert, the TPE calculates the potential cascading effects of the infiltration. In detail, the TPE links the tampered data to the physical container and its location within the port, indicating that this physical asset is affected by the cyber attack. This information is also displayed to the PSA operator via the HSA’s HMI and additional personnel is sent to inspect the container as a mitigation action. In case no cyber alert is triggered, the ECE within the HSA can correlate the two events based on its predefined rule set, identify the anomalies in the TOS and the PCS as a potential malicious behavior and trigger a Hybrid Alert. For this alert, the TPE calculates the potential cascading effects and everything together is presented to the operators via the HSA’s HMI.
Looking at the physical part of the attack (and assuming that the attack has not been mitigated, yet), the intrusion of the attackers into the port’s premises is not detected by a surveillance camera. However, a presence sensor captures the attacker’s motion further within the premises. The received event is displayed in the system’s HMI and sent to the HSA’s ECE. Once verified by the PSA operator, a physical alert is created and sent to the HSA. Within the HSA, the TPE calculates the potential cascading effects of an intrusion in that area, e.g., listing the containers located there. As a mitigation action, the PSA’s GIS capabilities help to determine which security units are closest to the event location and, through the messaging module of the PSA, they are committed to move and inspect the identified area. Even if the PSA’s operator does not trigger an alert, e.g., because the signal from the presence detector is considered as a false alarm, the ECE correlates the detection event with the two events coming from the CSA. The tampering of the container’s ID in the PCS together with the signal from the presence detector in the same area where the container is located can be enough to trigger a Hybrid Alert. The alert is communicated to the operators using the HSA’s HMI and the potential cascading effects are calculated by the TPE. Thus, the operators get a hint that thought false alarm is a real alarm and with maybe severe impact.
Hence, the SAURON system is able to identify the cyber and the physical aspects of the attack individually. Moreover, in case the events triggered from the PSA and CSA are misinterpreted by the respective operators, the ECE within the HSA is also able to identify the combined attack. In this scenario, the main advantage of the hybrid view introduced by the HSA is its ability to associate the individual events as part of one sophisticated attack. Knowing this, the operator is then able to better coordinate the response and prioritize the mitigation actions. Further, the TPE allows to identify the consequences of such an attack in the physical and the cyber domain, which is very difficult if a holistic view is missing.
7 Conclusion
In this paper, we presented a framework for a Hybrid Situational Awareness system developed in the SAURON project. The HSA integrates information on security alerts coming from the physical and the cyber domain to identify cascading effects and related combined attacks. In this way, the HSA framework brings current physical and cyber situational awareness one step further towards a fusion of both domains.
As a major benefit of this system, CSA operators receive alerts regarding their domain based on the cascading effects from the physical world and PSA operators receive alerts issued from the cyber world. This allows them, on the one hand, to be aware of incidents that originate in the respective other domain but have an impact on their own infrastructure. On the other hand, the system indicates potential combined attacks which would not be detected by either a PSA or a CSA system alone. Therefore, the HSA provides a holistic overview on the overall infrastructure and supports the security officers from both domains in their decision making process.
Nevertheless, we still foresee some open issues of our approach at this time. The first potential bottleneck is the capability for a system to manage the whole security of an infrastructure. Since critical infrastructures are in general very large and rather complex organizations, there are numerous physical and cyber assets to manage. Therefore, the algorithms for implementing the ECE and the TPE (as well as other specific tasks of the HSA) need to be efficiently designed. Another issue might be the maintenance of the asset infrastructure information. In such a big organization, the configuration of assets and the inter-dependencies between them might change frequently. Another aspect that needs maintenance is the rulse set of the ECE. Thus, the SAURON system needs to guarantee that the analyses are carried out on the most accurate infrastructure configuration.
A more organizational concern evolves around the training of the operators. For the moment, there is training for physical security and training for cyber security, both carried out separately most of the time. Hence, there is no “mixed” or “hybrid” training. However, facing an increasing number of combined attacks and a respective HSA solution, operators that are trained to manage physical alerts, cyber alerts are required in both domains. The operators need to be trained to identify and manage the cascading effects from one domain to the other to reach the concept of a holistic security solution.
In general, the future of security situational awareness foresees the removal of the boundaries between these two worlds. In the past, the protection of critical infrastructures was very much connected to the physical world, in particular when it comes to maritime port infrastructures. With the increase of cyber attacks in recent years, cyber security has become more important. Therefore, the interplay and cascading effects between the physical, cyber and combined attacks - and thus a more holistic “hybrid” view - have to be considered more thoroughly in the future.
Acknowledgments
This work was supported in part by the EC in the context of the SAURON under the HORIZON 2020 Framework (Grant No. 740477).