1 Introduction
Due to the large number of natural and malicious events that may affect Critical Infrastructures, improving the robustness and resilience of such systems is a fundamental task. In this view, due to budget limitations (in terms of required effort), it is mandatory to identify the most critical elements of an infrastructure, in order to properly organize the available protection resources. In the last few years, the scientific community has been increasingly interested in developing effective strategies to identify the most critical elements of an infrastructure network (see, among others, [10, 11]). A large fraction of the proposed methods identifies criticality subsystems in terms of their interconnection with the other subsystems, i.e., according to a topological perspective. Specifically, a typical approach is to study the degradation of important network parameters, such as node degree, clustering coefficient, or betweenness, upon iterative removal of nodes and/or edges, thus simulating the robustness/resilience of the network with respect to intentional attacks or natural disasters [12]. Moreover, existing literature does not make particular distinction among the particular nodes, i.e., they assume that the topological parameters completely describe the robustness/resilience of the network after an adverse event, irrespectively of which pairs of nodes are actually connected by a direct link or by a path. If such an assumption is legitimate for particular networks (e.g., for a power grid, where any node might be able to provide power to the nodes connected to it by a path), it seems less justified in other sectors, such as telecommunications or transportations, where nodes might have highly heterogeneous characteristics.
Among other descriptors of network connectivity, the pairwise connectivity (PWC) [9] represents a popular metric, it that it explicitly measures the number of pairs of nodes in the network that are connected via a path. By leveraging on the PWC metric, the identification of the critical nodes is typically done by solving the so-called Critical Node Detection Problem (CNP) [6–8], which aims at identifying which nodes should be attacked (up to a given limit k) in order to create the largest possible degradation. Such an approach, however, typically requires a large number of Boolean decision variables [7] and a number of constraints that can be non-polynomial in the number of nodes of the network [8]; these factors may limit the applicability of the standard CNP methodology.
Notice that the CNP problem typically introduces some a priori hypothesis on the attack, e.g., the number of attacked nodes is upper-bounded by a small integer or different constraints are introduced to narrow the otherwise overwhelming complexity of this problem. In [2] a strategy to avoid introducing such constraints is provided by adopting a multi-objective optimization perspective where each node is characterized in terms of the effort required to attack it; in particular the approach in [2] aims at identifying those nodes that, if attacked, minimize the residual network connectivity in terms of PWC and, at the same time, correspond to the minimum effort. Notably, no a priori assumption is made on the specific attack budget and number of targets.
1.1 Contribution
In this work we propose an approach that extends the one in [2] by characterizing each node not only in terms of the effort required by the attacker to target that node, but also considering the relevance or importance the node has. Also in this case, no a priori assumption on the attacker psychology is made. In more detail, while PWC assigns the same relevance to any pair of nodes connected by a path in the network after the attack, in this paper we extend such an index by considering a different relevance for different pairs of nodes, thus accounting for the degree of heterogeneity of the network. Finally, we complement our methodology by introducing upper and lower bounds on the overall attacker’s effort, in order to specialize the proposed methodology to different classes of attackers.
1.2 Paper Outline
The paper outline is as follows: In Sect. 2, for the sake of completeness, we collect some preliminary definitions. In Sect. 3 we provide the definition of our methodology by introducing a connectivity measure for heterogeneous networks and the proposed attacker model. Results and discussions are presented in Sect. 4, where a validation is carried out for a real network. Finally, some conclusive remarks are collected in Sect. 5.
2 Preliminaries
2.1 General Preliminaries
Let us denote by |X| the cardinality of a set X; moreover, we represent vectors via boldface letters, and we use  to indicate a vector in
to indicate a vector in  whose components are all equal to k. We denote by
whose components are all equal to k. We denote by  an
an  matrix whose entries are all 0, and by
matrix whose entries are all 0, and by  the
the  identity matrix.
identity matrix.
 matrix and let B be an
matrix and let B be an  matrix; the Kronecker product of A and B is the
matrix; the Kronecker product of A and B is the  matrix
matrix

 the entry-wise sign of the matrix A, i.e.,
the entry-wise sign of the matrix A, i.e.,  .
.2.2 Graph Related Definitions
Let  denote a graph with a finite number n of nodes
denote a graph with a finite number n of nodes  and e edges
and e edges  , from node
, from node  to node
to node  . A graph is said to be undirected if
. A graph is said to be undirected if  whenever
whenever  , and it is said to be directed otherwise; in the following we will consider undirected graphs.
, and it is said to be directed otherwise; in the following we will consider undirected graphs.
The adjacency matrix of a graph G is an  matrix A such that
matrix A such that  if
if  and
and  otherwise.
otherwise.
A direct path over a graph  , starting at a node
, starting at a node  and ending at a node
and ending at a node  , is a subset of links in E that connects
, is a subset of links in E that connects  and
and  , respecting the edge orientation and without creating loops.
, respecting the edge orientation and without creating loops.
A graph  is connected if each node can be reached by each other node by means of the links in E, regardless of their orientation. A directed graph that has a direct path from each vertex to every other vertex is said to be strongly connected.
is connected if each node can be reached by each other node by means of the links in E, regardless of their orientation. A directed graph that has a direct path from each vertex to every other vertex is said to be strongly connected.
The out-degree of a node is defined as the number of edges directed out of the node.
2.3 Pairwise Connectivity

 is 1 if the pair
is 1 if the pair  is connected via a direct path in G, and is zero otherwise. In other words, the pairwise connectivity is the number of pairs of nodes that are connected via a path over G. Noting that the maximum number of couples in a graph with n nodes is
is connected via a direct path in G, and is zero otherwise. In other words, the pairwise connectivity is the number of pairs of nodes that are connected via a path over G. Noting that the maximum number of couples in a graph with n nodes is  , the normalized pairwise connectivity (NPWC) is defined as
, the normalized pairwise connectivity (NPWC) is defined as![$$\begin{aligned} NPWC(G)=\dfrac{PWC(G)}{n(n-1)} \in [0,1]. \end{aligned}$$](../images/477940_1_En_16_Chapter/477940_1_En_16_Chapter_TeX_Equ2.png)
Remark 1

 , the graph is not strongly connected, but the larger NPWC(G) is, the more G is “close" to a strongly connected graph.
, the graph is not strongly connected, but the larger NPWC(G) is, the more G is “close" to a strongly connected graph.2.4 Multi-objective Optimization
In this section we briefly review the key aspects of multi-objective optimization (MOO).
 representing n decision variables, a MOO problem can be expressed as follows
representing n decision variables, a MOO problem can be expressed as follows![$$\begin{aligned} \min f(\mathbf{x})= \min \quad [f_{ 1 }(\mathbf{x}),f_{ 2 }(\mathbf{x}),\dots ,f_{ k }(\mathbf{x})]^{ T },\quad \text{ subject } \text{ to } \mathbf{x}\in \mathcal {F}, \end{aligned}$$](../images/477940_1_En_16_Chapter/477940_1_En_16_Chapter_TeX_Equ3.png)
 and the i-th objective is given by
and the i-th objective is given by
 is the multi-objective function. The set
is the multi-objective function. The set  represents the set of feasible solutions for the problem at hand. Moreover, the multi-objective space is defined as
represents the set of feasible solutions for the problem at hand. Moreover, the multi-objective space is defined as
 that minimizes at the same time all the different objectives
that minimizes at the same time all the different objectives  . Let us consider a solution
. Let us consider a solution  for which all the objectives
for which all the objectives  are simultaneously minimized, and let us denote the associated multi-objective vector
are simultaneously minimized, and let us denote the associated multi-objective vector  by
by  . Note that, when there is no conflict among the objectives, we can solve Problem (3) by solving k scalar problems, thus obtaining
. Note that, when there is no conflict among the objectives, we can solve Problem (3) by solving k scalar problems, thus obtaining  as the ideal multi-objective vector. Due to the conflicting nature of the objectives
as the ideal multi-objective vector. Due to the conflicting nature of the objectives  , however, it is realistic to assume that
, however, it is realistic to assume that  .
.In most practical cases, therefore, there is a need to overcome the above naive definition of an optimal solution; a typical approach in the literature is to resort to the theory of Pareto optimality [4].
 and
and 

 ; we say that
; we say that  is Pareto-dominated by
is Pareto-dominated by 
 if:
if: for each
for each  and
and at least for a value of
at least for a value of  .
.
 is a Pareto optimal solution if there is no other solution
is a Pareto optimal solution if there is no other solution  such that:
such that:
 is the set of all possible Pareto optimal solutions
is the set of all possible Pareto optimal solutions  for the matter at hand, while we denote by
for the matter at hand, while we denote by  the set of values
the set of values  , in the multi-objective space, which correspond to each
, in the multi-objective space, which correspond to each  .
.3 Network Vulnerability Analysis
In this section we generalize the PWC indexes introducing the “weighted" PWC in order to discriminate among the different pairs of nodes and illustrate how such an index can be used in MOO-based framework to identify the most critical nodes. Moreover, we introduce a bound on the maximum budget for the attacker in order to discriminate different classes of attackers: criminal, terroristic and warfare scenario.
3.1 Weighted Pairwise Connectivity
As introduced in Sect. 2.3, the PWC and the NPWC consists of two indices able to estimate the degree of connectivity of a graph. In this section we generalize these indices in order to consider not only the number of the pairs of nodes, but also the relevance of each specific pair. To this end we introduce the weighted pairwise connectivity (WPWC).
 and let us define
and let us define  , whose entries satisfy
, whose entries satisfy  represents a measure of the relevance of the nodes (e.g. number of users, dimension of the town, etc.). We define the weighted pairwise connectivity as an extension of Eq. 1
represents a measure of the relevance of the nodes (e.g. number of users, dimension of the town, etc.). We define the weighted pairwise connectivity as an extension of Eq. 1

![$$\begin{aligned} NWPWC(A,\mathbf{w}) = \dfrac{\mathbf{1_n^T} \left[ P \circ \left( \mathbf{w \otimes \mathbf{1_n^T} } \right) \circ \left( { \mathbf{1_n}\otimes \mathbf w^T } \right) \right] \mathbf{1_n}}{\mathbf{1_n^T} \left[ \left( \mathbf{w \otimes \mathbf{1_n^T} } \right) \circ \left( { \mathbf{1_n}\otimes \mathbf w^T } \right) \right] \mathbf{1_n}}, \end{aligned}$$](../images/477940_1_En_16_Chapter/477940_1_En_16_Chapter_TeX_Equ7.png)
 is the
is the  matrix whose elements
matrix whose elements  are equal to 1 if exists a direct path in G from i to j, 0 otherwise. The definition of matrix P derives from the results described in [3], and is based on the property that the (i, j)-th entry of the k-th power of the adjacency matrix is equal to the number of paths of length k among the nodes
are equal to 1 if exists a direct path in G from i to j, 0 otherwise. The definition of matrix P derives from the results described in [3], and is based on the property that the (i, j)-th entry of the k-th power of the adjacency matrix is equal to the number of paths of length k among the nodes  and
and  .
.3.2 Critical Nodes Detection
Let us consider a set of n heterogeneous interdependent systems, modeled as a directed graph  whose nodes
whose nodes  represent the subsystems and each link in E consists of an interdependence relation among them.
represent the subsystems and each link in E consists of an interdependence relation among them.
Moreover, consider a vector  ; each entry
; each entry  of
of  represents the degree of importance of the i-th subsystem. Let us also define a vector
represents the degree of importance of the i-th subsystem. Let us also define a vector  , whose elements
, whose elements  represent the attack cost for the i-th node, i.e., an estimate of the effort required for the attacker in order to make the i-th system completely inoperable. In the following, we assume that, when the i-th system is attacked, it is removed from the network within all its incident links. The malicious attacker aims at maximizing the damage dealt to the network, i.e., to minimize the network WPWC; at the same time, he/she wants to minimize his/her effort, i.e., minimize the total attack cost. In order to distinguish among different classes of attackers, we assume that the available total budget for the attacker can be significantly different in the case he/she is a criminal, a terroristic organization or a state-sponsored terroristic organization.
represent the attack cost for the i-th node, i.e., an estimate of the effort required for the attacker in order to make the i-th system completely inoperable. In the following, we assume that, when the i-th system is attacked, it is removed from the network within all its incident links. The malicious attacker aims at maximizing the damage dealt to the network, i.e., to minimize the network WPWC; at the same time, he/she wants to minimize his/her effort, i.e., minimize the total attack cost. In order to distinguish among different classes of attackers, we assume that the available total budget for the attacker can be significantly different in the case he/she is a criminal, a terroristic organization or a state-sponsored terroristic organization.
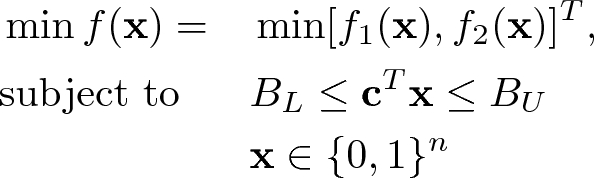
 is the attack vector and has entries
is the attack vector and has entries  if the i-th subsystem is attacked, and
if the i-th subsystem is attacked, and  ,otherwise. Morever,
,otherwise. Morever,  and
and  are, respectively, the lower and upper bounds on the attack cost. Note that the upper bound
are, respectively, the lower and upper bounds on the attack cost. Note that the upper bound  can be used to discriminate different attacker classes, while the lower bound
can be used to discriminate different attacker classes, while the lower bound  is a parameter that allows to filter non-realistic or trivial attack vectors corresponding to very limited damage/effort.
is a parameter that allows to filter non-realistic or trivial attack vectors corresponding to very limited damage/effort.
 , according to the definition in Eq. (9), represents the adjacency matrix of the graph once all the incident edges to the attacked nodes have been removed from the graph (i.e. all the entries of the associated row and columns are set to 0). In other words, it holds
, according to the definition in Eq. (9), represents the adjacency matrix of the graph once all the incident edges to the attacked nodes have been removed from the graph (i.e. all the entries of the associated row and columns are set to 0). In other words, it holds
 for a node
for a node  as
as
 is the subset of solutions in the Pareto front where node
is the subset of solutions in the Pareto front where node  is attacked, i.e.,
is attacked, i.e.,
 is the set of all the solutions in the Pareto front.
is the set of all the solutions in the Pareto front.The above index assigns greater criticality to those nodes  that are often attacked in a solution in the Pareto front, while the criticality of a node is small if it is attacked by only a few of the solutions in the Pareto front.
that are often attacked in a solution in the Pareto front, while the criticality of a node is small if it is attacked by only a few of the solutions in the Pareto front.
4 Case Study: U.S. Airport Network
 of the graph a degree of importance
of the graph a degree of importance  and an attack cost
and an attack cost  . Without loss of generality, we assume that the value
. Without loss of generality, we assume that the value  is equal to the out-degree (i.e., the number of outgoing edges) of the i-th node. In other words, we assume that the larger the out-degree is, the higher the effort will be to disconnect the node from the network (i.e,. the attack cost is directly proportional to the number of direct flight routes from the airport to other destinations). Analogously, with respect to the definition of the importance degree, we assume that
is equal to the out-degree (i.e., the number of outgoing edges) of the i-th node. In other words, we assume that the larger the out-degree is, the higher the effort will be to disconnect the node from the network (i.e,. the attack cost is directly proportional to the number of direct flight routes from the airport to other destinations). Analogously, with respect to the definition of the importance degree, we assume that  is proportional to the betweenness centrality of the i-th node. We recall that for a node
is proportional to the betweenness centrality of the i-th node. We recall that for a node  the betweenness centrality is the fraction of shortest paths that pass through
the betweenness centrality is the fraction of shortest paths that pass through  (without considering
(without considering  as source or destination of the paths). In this way, we associate a low importance to the airports with a low number of stopovers, while airports involved in high number of stopovers are considered essential for the network connectivity. For the sake of completeness, in Fig. 1, we report the distribution of out degree and betweenness centrality with reference to the analyzed network. Note that
as source or destination of the paths). In this way, we associate a low importance to the airports with a low number of stopovers, while airports involved in high number of stopovers are considered essential for the network connectivity. For the sake of completeness, in Fig. 1, we report the distribution of out degree and betweenness centrality with reference to the analyzed network. Note that  and
and  can be estimated in different ways, e.g.
can be estimated in different ways, e.g.  may be estimated on the basis of an assessment about the actual adopted security measure, and
may be estimated on the basis of an assessment about the actual adopted security measure, and  on the base of the number of citizens living in the area of the i-th airport. In this paper we adopted the aforementioned selection because it can be estimated directly from the topology of the network.
on the base of the number of citizens living in the area of the i-th airport. In this paper we adopted the aforementioned selection because it can be estimated directly from the topology of the network.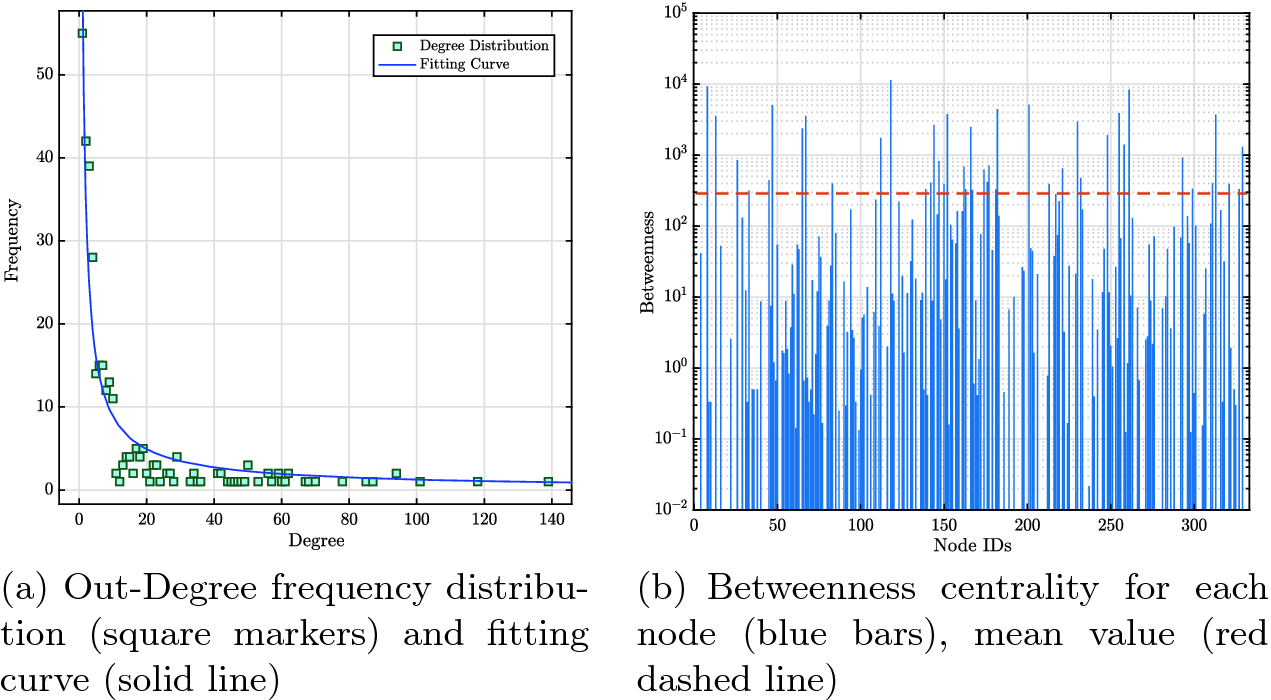
Degree and Betweenness distributions on US Airline Network.
 generated solutions1. Specifically we consider the scenarios illustrated in Table 1 which represents different classes of attackers.
generated solutions1. Specifically we consider the scenarios illustrated in Table 1 which represents different classes of attackers.Attacker classes.
Class |
| % | Scenario |
|---|---|---|---|
State-sponsored organization | 4252 | 100% | A |
Terrorist group | 1417 | 33% | B |
Criminal organization | 425 | 10% | C |
 and
and  (i.e. the upper and lower bounds on the attack cost necessary to disconnect all the nodes from the network). Note that, as illustrated in the figure, the network is completely disconnected also when a budget of just 65% of
(i.e. the upper and lower bounds on the attack cost necessary to disconnect all the nodes from the network). Note that, as illustrated in the figure, the network is completely disconnected also when a budget of just 65% of  is used.
is used.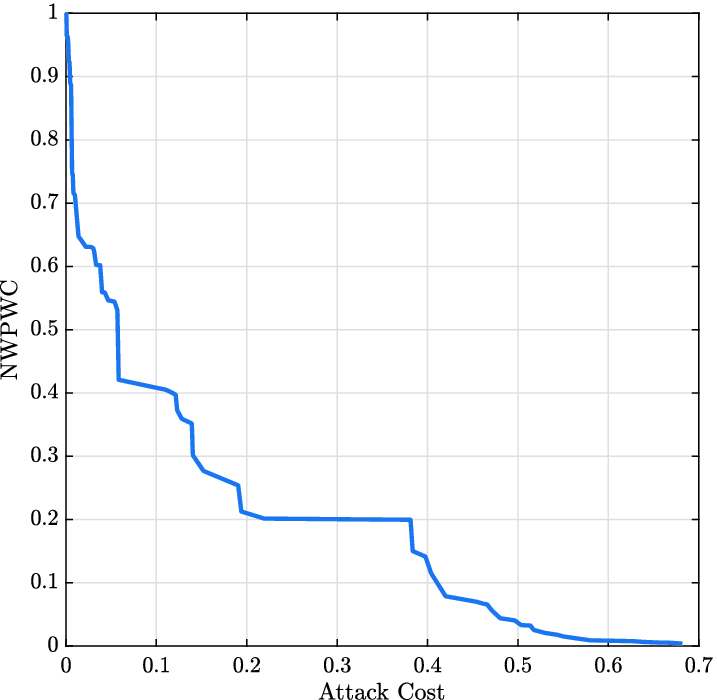
Pareto front obtained for  proportional to the node betweenness centrality measures, and
proportional to the node betweenness centrality measures, and  proportional to the node degrees.
proportional to the node degrees.
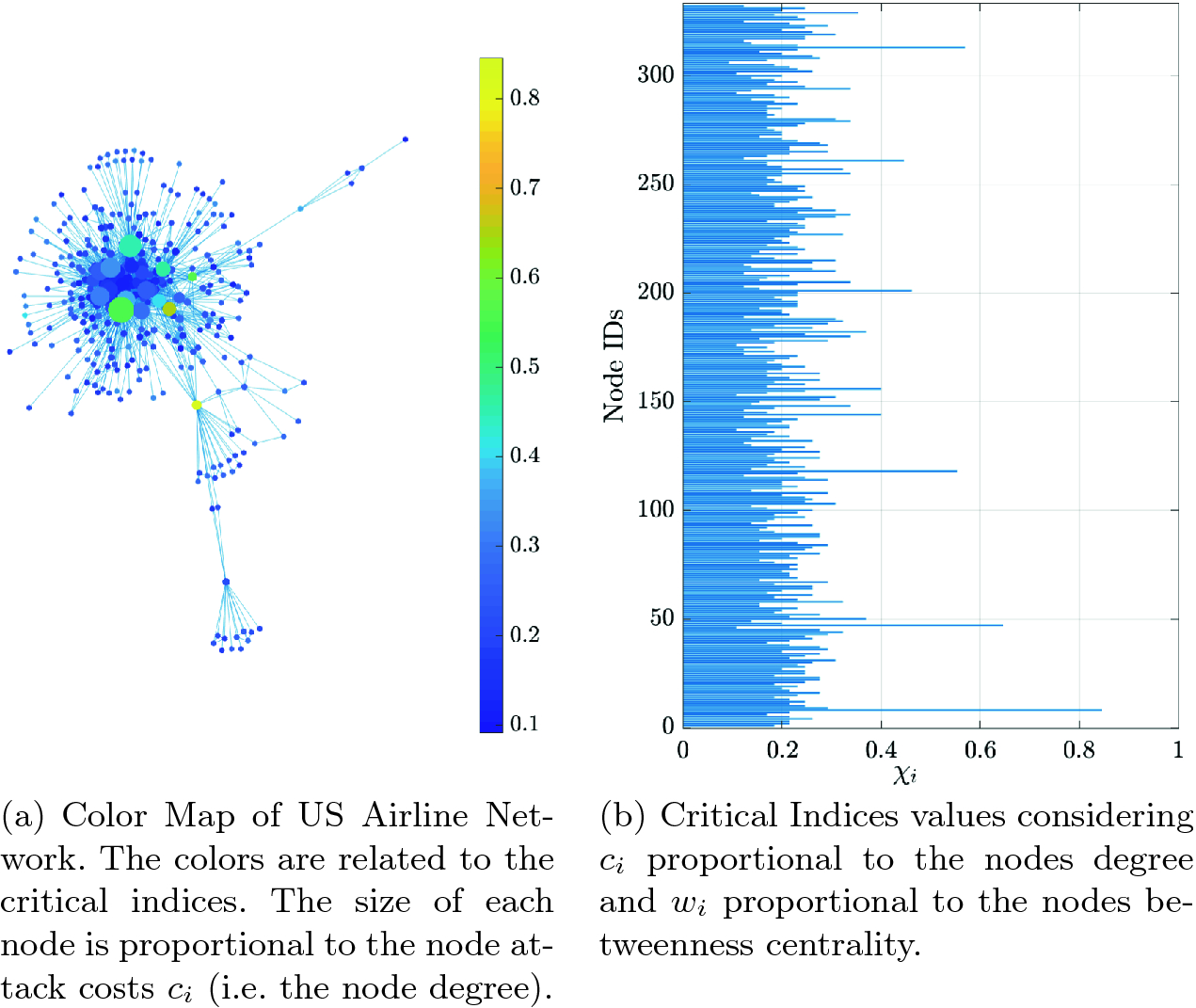
US Airline Network vulnerability analysis.
Looking at the figure, it is evident that the most critical node is the Anchorage Airport, which is involved in 84% of the generated hypothetical attack plans (this node is characterized by an attack cost  and an importance degree
and an importance degree  and its deletion disconnects the graph in several connected components.). The second most critical node is Seattle-Tacoma, which is involved in 64% of the attack plans (Seatle-Tacoma has an attack cost
and its deletion disconnects the graph in several connected components.). The second most critical node is Seattle-Tacoma, which is involved in 64% of the attack plans (Seatle-Tacoma has an attack cost  and an importance degree of
and an importance degree of  ). Note that Chicago O’Hare, although having the largest importance degree
). Note that Chicago O’Hare, although having the largest importance degree  , is involved only in 55% of the attack plans, i.e., it is ranked only fourth in terms of criticality. A reason for this lies in the high attack costs associated to it, which may imply that such an airport is too well protected and, consequently, it is not an appealing target for attackers that have limited resources. Data related to the first five most critical nodes is reported in Table 2, together with the results obtained for the other two scenarios.
, is involved only in 55% of the attack plans, i.e., it is ranked only fourth in terms of criticality. A reason for this lies in the high attack costs associated to it, which may imply that such an airport is too well protected and, consequently, it is not an appealing target for attackers that have limited resources. Data related to the first five most critical nodes is reported in Table 2, together with the results obtained for the other two scenarios.
In Scenario B, we consider an attacker belonging to a Terrorist Group. Terrorists, generally, can rely on considerable resources, although smaller than a Sate-like entity. Specifically, we impose, as illustrated in Table 1, an upper bound about the budget of the attacker equal to 33% of the maximum budget. Looking to Table 2 one can notice that the four most critical airports are the same as in Scenario A, but in this case they appear in considerably less attack plans (e.g., Anchorage airport is involved in only 76% of the hypothetical attack plans with respect to the 84% of Scenario A). This suggests that, in a terroristic scenario, the targets are larger hence more difficult to identify.
Most critical Airports in US Airline Network as in 1997.
Scenario A | Scenario B | Scenario C | |||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|
Airport |
|
|
| Airport |
|
|
| Airport |
|
|
|
Anchorage | 0.84 | 29 | 9288 | Anchorage | 0.76 | 29 | 9288 | Anchorage | 0.79 | 29 | 9288 |
Seattle-Tacoma | 0.64 | 57 | 5069 | Seattle-Tacoma | 0.58 | 57 | 5069 | Seattle-Tacoma | 0.62 | 57 | 5069 |
Honolulu | 0.56 | 24 | 3721 | Honolulu | 0.48 | 24 | 3721 | Honolulu | 0.55 | 24 | 3721 |
Chicago O’hare | 0.55 | 139 | 11377 | Chicago O’hare | 0.43 | 139 | 11377 | San Francisco | 0.41 | 68 | 5146 |
San Francisco | 0.46 | 68 | 5146 | Dallas/Fort Worth | 0.41 | 118 | 8367 | Salt Lake City | 0.41 | 59 | 2662 |
5 Conclusions
In this paper we present a novel methodology for identifying network vulnerabilities. Specifically, we formulate a multi-objective optimization problem and based on the concept of weighted pairwise connectivity, with the aim to overcome the limitations of the other formulations which consider a single class of connected nodes without differences about their relevance in the network. The proposed methodology can be used to plan the allocation of limited protection resources, with the aim to globally improve the network’s robustness. Future work will aim at applying the proposed methodology to multi-layer or hierarchical networks. Moreover, we will inspect the possibility to model the damage dealt by the attacker in terms of the reduction of flow over the network (e.g., for power or gas networks).
















