Anti-forensics
Abstract
Digital forensic success stories are becoming widely known. That has created a keen interest in obstructing these types of investigations. Some of these obstructive techniques are so effective that they can make recovering the information virtually impossible. This is of grave concern especially in the context of public safety. To combat these anti-forensics techniques, examiners must become familiar with the various ways to hide and destroy data. They must also master the tools and methods at their disposal to overcome anti-forensic efforts.
Keywords
“There are two types of encryption: one that will prevent your sister from reading your diary and one that will prevent your government.”
—Bruce Schneier
Introduction
Hiding data
Encryption
What is encryption?
Early encryption
Table 6.1
The Alphabet with Simple Encryption (Caesar Cipher). The Key in This Example is Five.
| Plain text | A B C D E F G H I J K L M N O P Q R S T U V W X Y Z |
| Cipher text | F G H I J K L M N O P Q R S T U V W X Y Z A B C D E |
Table 6.2
A Letter-by-Letter Conversion Using the Caesar Cipher and a Key of Eight
| Plain text | F | O | R | E | N | S | I | C | S |
| Cipher text | N | W | Z | M | V | A | Q | K | A |

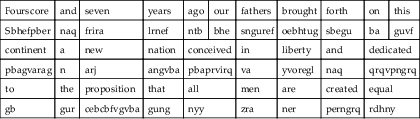
Table 6.3
The Opening of Lincoln’s Gettysburg Address Encrypted Using ROT13
| Fourscore | and | seven | years | ago | our | fathers | brought | forth | on | this |
| Sbhefpber | naq | frira | lrnef | ntb | bhe | snguref | oebhtug | sbegu | ba | guvf |
| continent | a | new | nation | conceived | in | liberty | and | dedicated | ||
| pbagvarag | n | arj | angvba | pbaprvirq | va | yvoregl | naq | qrqvpngrq | ||
| to | the | proposition | that | all | men | are | created | equal | ||
| gb | gur | cebcbfvgvba | gung | nyy | zra | ner | perngrq | rdhny | ||
Algorithms
Algorithms: it’s no secret
Key space
Some common types of encryption
Encrypting file system
Bitlocker
Apple Filevault
Truecrypt
Breaking passwords
Password attacks
Brute force attacks
Password reset
Dictionary attack
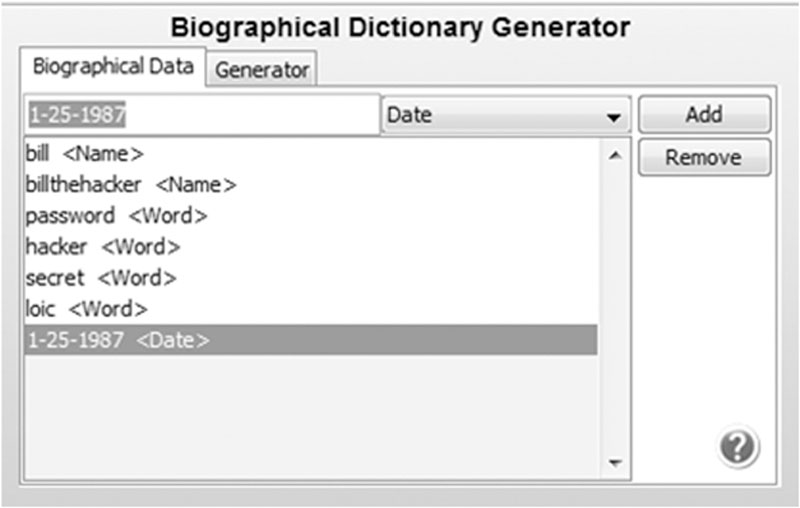
Table 6.4
A Sampling of the More Than 2,600 Keywords Generated from Our Original List of Seven
| 1 25 1987 1251987 billbill bill bill bill-bill bill_bill billb bill b bill-b bill_b billbillthehacker bill billthehacker bill-billthehacker bill_billthehacker billb bill b bill-b bill_b | b25billthehacker billthehacker251b billthehacker125b b251billthehacker b125billthehacker 25billthehacker1b 25b1billthehacker 1billthehacker25b 1b25billthehacker billthehacker1b25 b1billthehacker25 billthehacker25b1 b25billthehacker1 billthehacker25bill bill25billthehacker billthehacker251bill billthehacker125bill bill251billthehacker bill125billthehacker 25billthehacker1bill 25bill1billthehacker | 251987secret 251987 secret secret1987h h1987secret secret198725h secret251987h h198725secret h251987secret 1987secret25h 1987h25secret 25secret1987h 25h1987secret secret25h1987 h25secret1987 secret1987h25 h1987secret25 secret1987 secret 1987 1987secret 1987 secret |
Additional resources
Encryption
Steganography
“In addition, and among other things, a number of the Boston Conspirators’ Electronic Messages appear directly to concern communication by means of steganography. For example, one message, dated December 15, 2004, discussed the process of ‘decrypt[ing]’ messages embedded in images; another message, dated February 22, 2005, discussed ‘decypher[ing] [sic]’ data embedded in images. Similarly, on or about October 3, 2004, law-enforcement agents, acting pursuant to a judicial order, intercepted aural communications taking place inside the Boston townhouse. Tracey Lee Ann Foley, the defendant, was heard saying to Donald Howard Heathfield, the defendant: ‘Can we attach two files containing messages or not? Let’s say four pictures ….’ Based on my training, experience, and participation in this investigation, I believe that this was a reference to conveying messages by means of steganography—placing ‘files containing messages’ in ‘pictures.’ On or about March 7, 2010, law-enforcement agents, acting pursuant to a judicial order, intercepted aural communications taking place inside the Boston townhouse. As a final example, in or about March 2010, Foley and Heathfield were heard discussing Foley’s use of steganography and the schedule of her communications with Moscow Center.” (United States of America v. Christopher R. Metsos, 2010)
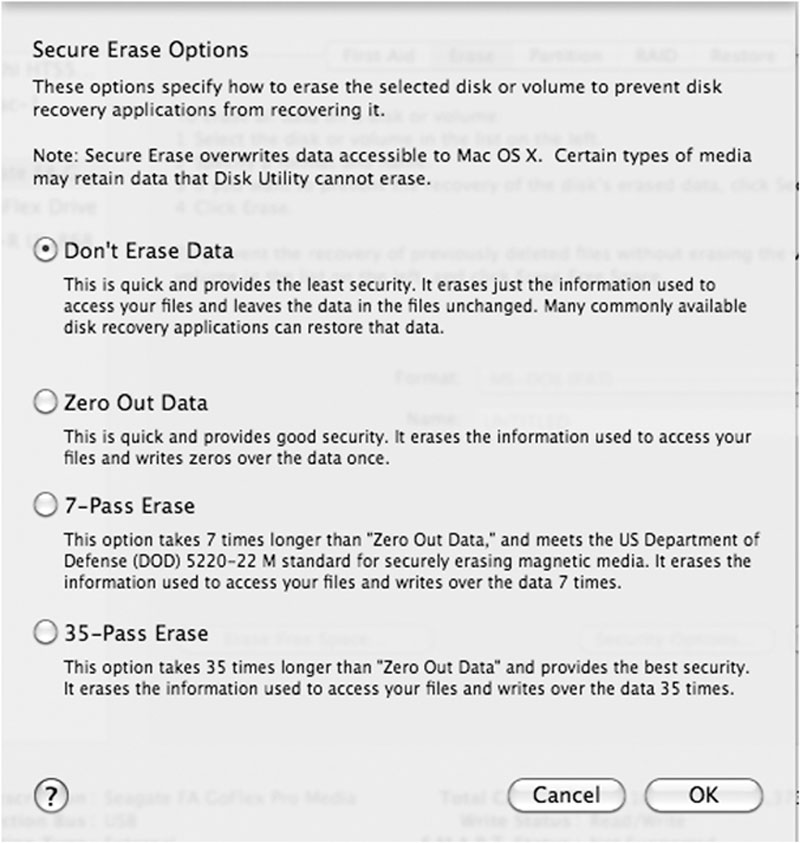
Data destruction
Drive wiping