 Syngress is an Imprint of Elsevier
Syngress is an Imprint of Elsevier
THREAT FORECASTING THREAT FORECASTING Leveraging Big Data for Predictive
Analysis
JOHN PIRC
DAVID DESANTO
IAIN DAVISON
WILL GRAGIDO
AMSTERDAM • BOSTON • HEIDELBERG • LONDON
NEW YORK • OXFORD • PARIS • SAN DIEGO
SAN FRANCISCO • SINGAPORE • SYDNEY • TOKYO
 Syngress is an Imprint of Elsevier
Syngress is an Imprint of Elsevier
Syngress is an imprint of Elsevier
50 Hampshire Street, 5th Floor, Cambridge, MA 02139, USA
Copyright # 2016 Elsevier Inc. All rights reserved.
No part of this publication may be reproduced or transmitted in any form or by any means, electronic or mechanical, including photocopying, recording, or any information storage and retrieval system, without permission in writing from the publisher. Details on how to seek permission, further information about the Publisher’s permissions policies and our arrangements with organizations such as the Copyright Clearance Center and the Copyright Licensing Agency, can be found at our website: www.elsevier.com/permissions . This book and the individual contributions contained in it are protected under copyright by the Publisher (other than as may be noted herein).
Notices
Knowledge and best practice in this field are constantly changing. As new research and experience broaden our understanding, changes in research methods, professional practices, or medical treatment may become necessary. Practitioners and researchers must always rely on their own experience and knowledge in evaluating and using any information, methods, compounds, or experiments described herein. In using such information or methods they should be mindful of their own safety and the safety of others, including parties for whom they have a professional responsibility.
To the fullest extent of the law, neither the Publisher nor the authors, contributors, or editors, assume any liability for any injury and/or damage to persons or property as a matter of products liability, negligence or otherwise, or from any use or operation of any methods, products, instructions, or ideas contained in the material herein. Library of Congress Cataloging-in-Publication Data
A catalog record for this book is available from the Library of Congress
British Library Cataloguing-in-Publication Data
A catalogue record for this book is available from the British Library
ISBN: 978-0-12-800006-9


Publisher: Todd Green
Acquisition Editor: Chris Katsaropoulos
Editorial Project Manager: Anna Valutkevich
Production Project Manager: Punithavathy Govindaradjane
Designer: Mark Rogers
Typeset by SPi Global, India
ABOUT THE AUTHORS
John Pirc has more than 19 years of experience in Security R&D,
worldwide security product management, marketing, testing,
forensics, consulting, and critical infrastructure architecting and deployment. Additionally, John is an advisor to HP’s CISO on Cyber Security and has lectured at the US Naval Post Graduate School.
John extensive expertise in the security field stems from past
work experience with the US Intelligence Community, as Chief
Technology Officer at CSG LTD, Product Manager at Cisco,
Product Line Executive for all security products at IBM Internet
Security Systems, Director at McAfee’s Network Defense Business Unit, Director of Product Management at HP Enterprise Security Products, Chief Technology Officer at NSS Labs, Co-Founder and Chief Strategy Officer at Bricata, LLC and, most recently as Director of Security Solutions for Forsythe Technology.
In addition to a BBA from the University of Texas, John also
holds the NSA-IAM and CEH certifications. He has been named
security thought leader from SANS Institute and speaks at top tier security conferences worldwide and has been published in Time Magazine, Bloomberg, CNN and other tier 1 media outlets.
David DeSanto is a network security professional with over
15 years of security research, security testing, software develop-
ment and product strategy experience. He is a strong technical
leader with a firm understanding of TCP/IP, software develop-
ment experience, including automation frameworks, and a deep knowledge in securing the enterprise network.
David is the Director, Products and Threat Research for Spirent
Communications where he drives product strategy for all applica-tion security testing solutions. He also manages the security engi-neering team responsible for the research, development and validation of new security attacks (i.e., exploits, malware, DDoS attacks) as well as development of all engine components that support them. Prior to Spirent, David’s career included roles at the industry’s top security research and testing labs, where his expertise guided these organizations in creating industry-leading security tests and solutions for enterprises, services providers and network equipment vendors.
David holds a Master of Science in Cybersecurity from New
York University School of Engineering and Bachelor of Science
in Computer Science from Millersville University. He is a frequent speaker at major international conferences on topics including
threat intelligence, cloud security, GNSS security issues and the
impacts of SSL decryption on today’s next generation security
products.
Iain Davison has over 16 years of security experience, with
many skills ranging from penetration testing to creating and
building intrusion prevention devices. This includes knowledge of programming languages, scripting, and compiling software. In his last position, Iain performed network architecture, hard-ware design, software design, and implementation.
He currently lives in Clinton, MD, with his wife Laura and two
kids Shaun age 6 and Emma age 1; he also has a dog and a cat. Iain
enjoys creating home automation devices from raspberry pi kits
along with home media and simple robotics.
Along with his experience in the cyber-security industry, Iain
has also written a book with a few of colleagues on threat forecast-
ing, it will be published in the second quarter of this year. The
book discusses some techniques used to gather intelligence, the
importance of all data not just the obvious. Looking at data from
a different perspective, something other than the norm.
Now that he is on the Exabeam team, he may be willing to write
yet another book based around UBA and all the things it can do in
the enterprise.
Will Gragido possesses over 21 years of information security
experience. A former United States Marine, Mr. Gragido began
his career in the data communications information security and
intelligence communities. After USMC, Mr. Gragido worked within several information security consultancy roles performing and leading red teaming, penetration testing, incident response, security assessments, ethical hacking, malware analysis and risk management program development. Mr. Gragido has worked with a variety of industry leading research organizations including International Network Services, Internet Security Systems/IBM Internet Security Systems X-Force, Damballa, Cassandra Security, HP DVLabs, RSA NetWitness, and now Digital Shadows. Will has deep expertise and knowledge in operations, analysis, man-agement, professional services and consultancy, pre-sales/ architecture and has a strong desire to see the industry mature, and enterprises and individuals become more secure. Will holds a CISSP and has accreditations with the National Security Agency’s Information Security Assessment Methodology (IAM) and Information Security Evaluation Methodology (IEM). Mr. Gragido is a graduate of DePaul University and is currently in graduate school. An internationally sought after speaker, Will is the co-author of Cybercrime and Espionage : An Analysis of Subversive Multi - Vector Threats and Blackhatonomics : An Inside Look At The Economics of Cybercrime .
FOREWORD
“Some things are so unexpected that no one is prepared for them.”
–Leo Rosten in Rome Wasn’t Burned in a Day
For the last decade, I’ve been engaged in helping customers
and vendors mitigate the risks of a cyberattack. If there is one
thing I’ve learned, it’s that the adversary is dynamic, fast moving,
ever changing and that their targets are usually unprepared.
How do you prepare for a threat and adversary so dynamic and
innovative? What can we learn from the adversary? How can we
intersect with where the adversary is headed? Most notably,
how we can use the strategies that are employed by the adversary
to change our posture from one of viewing the threat in the rear
view mirror to a more balanced, proactive stance. This is the crux
of Threat Forecasting .
I have spent the last 30 + years engaged with IT executives in
various leadership roles in the computing, networking and infor-mation security industry. I had the benefit of cutting my teeth in the IT industry as a young manager during the early days of net-working working at 3Com Corporation for, among others, Robert Metcalfe, one of the principal inventors of Ethernet. That experi-ence served as a launching pad for my departure from 3Com. I engaged in leadership roles in an early stage database analytic company founded and lead by the likes of Brad Silverberg and Adam Bosworth. Brad was the Microsoft executive responsible for the Windows platform. Adam Bosworth is a recognized innovator with a career arc that includes his principle role as the creator of XMS while at Microsoft, a senior executive at Google as the VP of Product Management, and now the EVP at Salesforce. com responsible for the development of their next generation platform for IoT and Cloud.
During the first decade of my career, I matured professionally
inside the tornado of the emergence of the personal computer.
My time at 3Com introduced me to the power of the network
and Metcalfe’s Law.
Metcalfe’s law states that the value of a telecommunications
network is proportional to the square of the number of connected users of the system ( n 2 ).
The fundamental premise of Metcalfe’s law is the value of
the network grows geometrically as the number of users grows.
The authors of Threat Forecasting apply this same principle to the value of intelligent threat exchange. The authors explore how your organization can benefit from intelligent analysis of real-time threat information. Just as Metcalfe’s law describes the benefit of the computer network, so too do the authors educate us about the benefit of leveraging external and internal sources of Indica-tors of Interest (IOI), Indicators of Attack (IOA) and Indicators of Compromise (IOC).
As I rode the wave of the emergence of the personal computer
and networking, I was exposed to the inherent tension between
the economic advantages of client-server, Web 1.0 and Web 2.0
architectures and the inherent challenges of maintaining security and control of the network and its sensitive data.
For the last decade, I have been deeply engaged in IT security.
Having helped countless organizations implement next genera-tion computing products and architectures. During this journey I have been continuously confronted with the inherent challenges associated with securing customer networks. That journey led me to a leadership role as the President of TippingPoint technologies, an early leader in network Intrusion Prevention Systems (IPS). TippingPoint was later acquired by 3Com, which was then acquired by Hewlett Packard Corporation. HP acquired ArcSight, the leading SIEM provider, and Fortify, the leading application security product at the time. While at HP I briefly led the product organization for the newly created Enterprise Security Products organization and ultimately was responsible for our global enter-prise security product go-to-market.
My time at HP gave me a comprehensive view of what it means
to provide defense-in-depth from the network, to the application, to the end system and data. After 18 months at HP I left to join Vormetric Data Security as its current President and CEO. As I write this forward, Vormetric is in the process of being acquired by Thales S.A., a leader in global defense and electronic systems. Their e-Security group is a leader in payment processing and general-purpose encryption hardware security modules (HSMs). The vast majority of payment transactions our touched by Thales systems each and every day. I will serve as the CEO of its global data security business unit, Thales e-Security.
I was drawn to Threat Forecasting based on my many years of
experience of being engaged with the authors. I have had the plea-sure of working directly with the authors at TippingPoint, HP and beyond. Their experience in working with the intelligence com-munity as subject matter experts used to dissecting high-profile breaches and as designers and developers of products uniquely qualifies them to speak to the benefit of Threat Forecasting.
John Pirc, David DeSanto, Iain Davison and Will Gragido bring
decades of combined experience with a unique mix of security
product development, strategy, engineering, testing, incident
response and much more. This combined expertise and the
coaching they have received from industry leaders throughout
their careers, has provided them with the insight and drive to push the security industry to the next level.
“My interest is in the future because I am going to spend the rest
of my life there.”
–C.F. Kettering
The authors are uniquely qualified to appreciate the impact
of and challenges involved in protecting us against cyber-attacks and why this remains one of the greatest challenges of our increasingly connected world.
Why Threat Forecasting is Relevant
The pace of change in our connected world is accelerating.
All one has to do is reflect on the recent spate of high-profile
breaches and the commensurate brand and financial damage
incurred to appreciate the industry needs a new approach. Yester-day’s tools and yesterday’s thinking simply no longer apply. The challenge is exacerbated with the proliferation of Internet of Things (IoT) devices, autonomous vehicles and the need for an increased level of trust between applications and devices in our more connected world.
What You Will Learn and How
You Will Benefit
“The journey of a thousand miles begins with one step.”
–Lao Tzu, Chinese Philosopher
I started this forward by citing the benefits attributed to the
network effect of Metcalfe’s Law. Metcalfe’s Law and the network
effect are a model and a metaphor for the advantages of commu-
nities of interest, which are at the crux of the power of Threat
Forecasting.
If you are a security practitioner, you will gain guidance and a
roadmap to help you begin the journey. The authors explain the
legacy of threat reporting, and compare and contrast threat
reporting with threat forecasting. You will be given a checklist of
available tools, both open source and commercial, to help you
understand the design of a security architecture that is threat fore-cast enabled.
If you are an IT or security executive (Chief Information Security
Officer), you will benefit from an education about the learning
from recent high-profile data breaches. You will gain a greater
appreciation of the efficacy of existing security solutions deployed in your network. You will gain insight into the key nomenclature in a way that is practical and easily consumable, thereby helping you engage in thoughtful dialog with your risk and security teams.
The authors present relevant, practical data that will help you
enlist the support of your colleagues, and executive management and board, to build consensus around a journey to engage in a threat forecasting initiative. Of particular relevance is an explana-tion of the power of communities of interest. You will learn the benefits of participating in a threat-sharing community of inter-est. You will learn the opportunities and risks associated with par-ticipation. You’ll learn how best to prepare your organization and existing information security infrastructure to maximize the value of the near real-time information gleaned from participation in, or subscription to, community of interest threat data.
Alan Kessler
President and CEO, Vormetric Data Security
PREFACE
Man has endeavored to see beyond his circumstances since
time immemorial. He has developed and adopted a vast and wide array of esoteric beliefs and rituals, which, over time, aided him to one degree or another in making decisions that would have ram-ifications on individuals, communities, populations, and empires. Throughout history, man’s desire to know and understand the future has encouraged him to strive toward greater and greater heights; heights that could only be reached by dismissing the eso-teric in favor of the scientific. Today, man continues to forecast and predict outcomes, only now instead of looking into the mists or at the bones, man looks at evidence; at math and contemplates probability based on a variety of factors all of which can be explained through science and articulated in such a way that the everyone can understand. This book deals with an area that is emerging. It is growing and developing, and is being nurtured by a portion of the Information Security industry, that in some ways is at a pivot point, where it is destined to move from the modern equivalent of esotericism to the new reality. In this book the concept of threat forecasting and predictive analysis is intro-duced to the reader in a manner that is easy to understand and digestible. It is delivered in 10 chapters all of which have been written and contributed to by the industry’s leading subject mat-ter experts with combined experience that can be measured in decades. This book will challenge some to look beyond the mist and embrace the scientific; the tangible. It will encourage the reader to think differently with respect to navigating and negoti-ating today’s threats, threat forecasting, security intelligence and the threat landscape itself.
Book Organization and Structure
During the following ten chapters the reader will be exposed to
concepts and ideas that they may have considered but never
employed or to those that are entirely new. Each chapter offers
a unique view of our experiences and thoughts. The book is bro-
ken down in the following manner:
Chapter 1 : Navigating Today’s Threat Landscape —We start by
discussing the issues within today’s threat landscape and show
the need for a better solution. A high-level discussion around
industry regulations will help set the tone for why threat forecast-ing is needed. We finish this chapter by challenging today’s infor-mation assurance practices.
Chapter 2 : Threat Forecasting —We discuss the foundations of
threat forecasting and compare patterns used to other types of
forecasting you may be familiar with. This chapter will also lay
some of the foundations for future chapters, including a discus-
sion around big data and its importance within threat forecasting. Chapter 3 : Security Intelligence —We will introduce you to secu-rity intelligence and help structure what a security intelligence platform should look like for your organization. This chapter will also discuss key performance indicators that are commonly asso-
ciated with security intelligence.
Chapter 4 : Identifying Knowledge Elements —We define key
terms that may be new to the reader including Indicators of Com-
promise (IOCs) and Indicators of Interest (IOIs). We help identify some issues when collecting knowledge elements and help pro-vide guidance on how to address them to get the best data possible for knowledge sharing and threat modeling.
Chapter 5 : Knowledge Sharing and Community Support —The
advantages and disadvantages to sharing knowledge elements are discussed and we reassure the reader that it is best to share and gain knowledge than be left in the dark. We outline several popular community threat intelligence feeds and how to become active within the threat intelligence community.
Chapter 6 : Data Visualization —We use this chapter to outline
the different ways to visualize your data for analysis and simula-
tion. Three-dimensional graphs are reviewed and comparisons
are drawn to other industries that leverage similar technologies.
Visualization is a key component on the road to threat forecasting. Chapter 7 : Data Simulation —In this chapter we discuss several topics as they relate to data simulation. These include compari-sons between simulation and emulation, the importance of deal-ing with knowledge elements (discussed in Chapter 4 ) and the types of engines available today. Future topics are discussed including leveraging quantum computing for faster data results. Chapter 8 : Kill Chain Modeling —We define kill chain modeling and discuss how it associates with threat forecasting. We dissect the individual components to help you better understand its necessity within this type of threat modeling. We discuss the role of big data as well as the tools available today to assist with kill
chain modeling.
Chapter 9 : Connecting The Dots —We bring together all the
individual topics discussed throughout the book and show how
not paying attention to the current landscape can impact your
organization. Real-world examples are used to show how threat
forecasting can play an integral part in protecting organizations
within all industry verticals. This chapter serves as a call to action
to begin applying the techniques that can improve your organiza-tion’s security practices and procedures.
Chapter 10 : The Road Ahead —In our final chapter, we discuss
our opinions for the future of both threat forecasting as well as the
Information Security as a whole. Our diverse background provides you with four unique views on how several key issues within the cyber security industry, as well as a unique view on the challenges that lie ahead for organizations from all industry verticals.
Closing Thoughts
Our collaboration and dedication to bringing to the market the
most comprehensive book on this subject is evident and of value
to anyone who picks it up. To the reader, we wish that you gain
knowledge and insights into the topic of threat forecasting and
predictive analysis. It is our hope that you will find this book novel, informative and educational, as it is our belief that it is one of the earliest published works on this subject. This is the combined work of four information security professionals located across three of the four time zones of the United States and was also writ-ten while the authors were traveling to various events, including speaking at international conferences, attending customer secu-rity consulting engagements and visiting our international offices. We hope you find this book to be a good travel companion on the road to threat forecasting and predictive analysis, as it was on its way from idea to inception.
ACKNOWLEDGMENTS
The journey of a thousand miles begins with one step
Lao Tzu
I want to dedicate this book to my Lord and Savior Jesus Christ,
my wife, kids, and my mom ( Judy Pirc) … I love you all. After writ-
ing two books, I didn’t think I would ever do a third. I’ve had the
pleasure to be involved in both early stage startups and well-
established high-tech security companies. I’ve been honored to
have influenced various security products working with some very strong teams. The experience has provided me with many oppor-tunities to experience what works and frankly what doesn’t. To some this concept of Threat Forecasting that I envisioned almost 4 years ago, some of the parts of which might be considered main-stream/bleeding edge security products and services, today might appear an impossible or a crazy idea.
On this journey, I quickly realized that I couldn’t take on this
project by myself and needed some of the best minds, with exper-
tise in threat intelligence, hardware design, data science, data
modeling, virtualization, SaaS, and product development; people whom I trusted to participate, to add to the project and to chal-lenge me. I decided to involve David DeSanto, Iain Davison, and Will Gragido all of whom I trust and respect, as they are not afraid of giving brutally honest feedback and it doesn’t hurt that they are close friends. After I briefed them on the original con-cept … let’s say some of my theories were challenged and they pushed me to a level of innovation that I had thought was beyond my capabilities. I’m very proud of their contributions and thought leadership in Threat Forecasting.
Lastly, I want to thank a few people that have been instrumen-
tal in my career, Stephen Northcutt, Bob Bigman, John Webster,
John Watkins, Greg Adams, Alan Kessler, Heath Peyton, John Law-rence, Ernest Rocha, Frank Oakes, Chris Morales, Dan Holden, Daniel J. Molina, Dan Seeley, Brendan Laws, Craig Lawson, Steve MacDonald, Scott Lupfer, Jacque Kernot, Brian Reed, Jason Lamar, Rees Johnson, Vik Phatak, Bob Walder, ReseAnne Sims, Kris Lamb, Eric York, David Poarch, Chris Becker, Lance Grover, Rich Raines, Andria Green, Chad Randolph, Mark Dowd, George V. Hulme, Ofir Zelnik, Donovan Kolbly, Gary Steely, Dillon Beres-ford, Ragy Magdy, Melanie Kesler Coppen, Mark Finke, Melinda
Fieldus, John Cardani-Trollinger, Chris Jobe, Enrique Rangel, Nick Selby, Gunter Ollman, Hillary Noye, Michael Jones, Thomas Skybakmoen, Jon Amato, Dave Barron, Barret Sellers, Toshikazu Murata, Adam Hils, Rafal Los, Elisa Contreras Lippincott, Nelson Brito, Chris Thomas, Dana Torgersen, Richard Stiennon, Jason Burn, Sean Brown, Youssef El Malty, Daniel Powers, Rohit Dha-mankar, Matt Wong, Mark Scianna, Tom Cross, Stefan Kors-backen, Denis Batrankov, Steve Spring, Julian McBride, Jason Hilling, Sumeet Gohri, Arun George, Russ Meyers, Val Rahmani, Scott Paisley, Munawar Hossain, Brent Fowler, Jerry Fraizer, Ralph Richardson, Stephen Driggers, and Sanjay Raja. There are many more … but thank you for investing in me!
John Pirc
First and foremost, I want to thank Liz, my wife and best friend.
Thank you for your unconditional love and unwavering support. I jumped into this project while in the middle of my Master of Sci-ence degree at NYU, which meant only your constant support (and a lot of caffeine) could make this a reality. This book could not have happened without you! Thank you for supporting my crazy ideas and being there to help me through the difficult times. I look forward to our continued journey together. Next, I would like to thank John for inviting me onto this project as well as Will and Iain for coming along for the ride. We have put together some-thing to be proud of. Our combined experiences make for a very unique perspective on Threat Forecasting. Next, I would like to thank the people throughout my career who have helped me. You have each played a role in getting me to where I am today and I thank you for constantly challenging me. Finally, I would like to thank you the reader. This book was written for those seeking new knowledge to better understand today and tomorrow’s threat landscape to best secure their organization. St. Francis of Assisi said “Start by doing what’s necessary; then do what’s possible; and suddenly you are doing the impossible.” I hope you find the knowledge you seek so that the impossible begins to become possible for you and your team.
David DeSanto
I would like to also dedicate my parts of the book to my wife
Laura and my kids Shaun and Emma. Thank you for supporting
me during this project.
Iain Davison
When I sat down to write this acknowledgment my first instinct
was to begin by thanking those closest to me for their support and
encouragement throughout the process. And though there will be some of that—thanking some key folks who supported my co-authors and me during the creative process—this will not be a dedication. This is an acknowledgment; this is an expression of gratitude and appreciation to those who played a key role in mak-ing this book a reality. I’d like to first acknowledge my wife, Tracy Gragido, and our kids. Their willingness to “share” me with my co-authors on nights and weekends made this process much easier than it would have been were that not the case. I’d also like to acknowledge my co-authors: John, David, and Iain. Thank you guys for allowing me to join you on this journey into the unknown. We set out to write a book on a topic that is nascent, emerging, and we did just that. Our ideas and thoughts (hopefully) will aid in spurring on new thought leaders and visionaries, for after all, as Arthur O’Shaughnessy said, “ … we are the music makers, we are the dreamers of dreams … ” I’d also like to acknowledge our team at Syngress, specifically Anna, for her patience and help along the way. Last but not least, I’d like to acknowledge you, the reader, for taking the time to peruse all the books on this subject and select-ing this one to add to your reading list or collection. It is my sincere hope that it aids you in finding the answers you seek.
Will Gragido

NAVIGATING TODAY’S THREAT LANDSCAPE
Introduction
Today’s threat landscape is often compared to a high stakes
game of whac-a-mole: just as security professionals focus on
thwarting one mole-like threat, others are already popping up.
Security threats emerge at a dizzying speed and security profes-
sionals are often left reeling as the threat landscape changes
around them. A vital tool in understanding these changes has
been historical threat reporting. Historical threat reports summa-rize events related to security threats over a fixed period of time. There are legions of historical threat reports available; a Google search for “cyber security threat report” yields over three million results. These reports may cover general cyber security threats or specific focus areas (e.g., web-based applications). There are quarterly threat reports and annual threat reports, but all histor-ical threat reports reflect backwards.
Historical threat reports have the valuable attribute of map-
ping out the threat landscape as it appeared in the past. And,
although many historical threat reports attempt to predict future trends and shifts, they provide only limited visibility into the threat landscapes of today and tomorrow. To combat the threats of today and predict the threats of tomorrow, enterprises need to view their security infrastructure, products and data collection in a different way. Instead of reporting after the fact, threat fore-casting looks to prevent security incidents and data breaches before they happen. The exploration of threat forecasting as laid out in this book will give organizations the tools needed to protect themselves in an ever evolving threat landscape. By adopting a Threat Forecasting. http://dx.doi.org/10.1016/B978-0-12-800006-9.00001-X 1
Copyright # 2016 Elsevier Inc. All rights reserved.
policy of threat forecasting, security professionals can stop play-ing whac-a-mole and begin to know where the next threat is likely to come from.
Why Threat Forecasting
No organization is impervious to security failures. By adopting
a systematic approach to threat forecasting, your organization can not only improve your defenses against today’s threats, but also form reasonable predictions about the threats of tomorrow. Although, it is true that no threat forecasting approach will be able to predict and stop attacks 100% of the time, when it is carried out correctly and consistently, threat forecasting will increase your organizational efficacy in detecting and preventing attacks. The side effect of preventing attacks is saving your company time, money and the embarrassment of a public data breach.
Threat forecasting allows you to apply real-world threat intel-
ligence to the data collected within your organization to identify
patterns or trends “in-the-wild” (i.e., currently active on the Inter-net) that may impact your organization. Threat forecasting enables your organization to:
• identify knowledge elements within your data for collection for
tracking/reporting (refer to Chapter 4 —Identifying Knowledge
Elements)
• subscribe to threat intelligence feeds to get a holistic view of
the greater threat landscape (refer to Chapter 5 —Knowledge
Sharing and Community Support)
• combine all datasets together and use identified trends
to determine high-risk elements and provide protection to vul-
nerable areas prior to attack/breach (refer to Chapter 6 —Data
Visualization and Chapter 7 —Data Simulation).
Please refer to Chapter 2 —Threat Forecasting for more
information.
The Effects of a Data Breach
Data breaches are becoming part of our daily lives. Adversar-
ies are better organized than ever and they are likely targeting
your company’s data. This is not a scare tactic or a way to encour-age you to go out and buy a bunch of security equipment. The message we want to convey is that no one is immune and data breaches are almost an inevitable occurrence in today’s threat landscape. Malicious threat actors are attacking all industries and are targeting both smaller startups and giant multinational
corporations. As a consequence of these malicious activities, the Incident Response (IR) market has exploded in recent years. By 2017, the IR market is expected to grow into a $ 14 billion industry. 1
With costs both tangible and intangible rapidly accumulating
in the wake of a data breach, there’s no doubt a data breach will
cost your organization big bucks. A Ponemon Institute study
found that not only have cyber-attacks increased in frequency
in recent years but also it is becoming more expensive to address
them, with the average data breach costing companies in the
study $ 3.8 million. 2 When remedying a data breach your organi-
zation will incur two types of costs: direct and indirect. Direct
costs include contracting outside forensic or IR experts, outsour-cing customer hotline support, notifying customers (both digitally as well as via mail), providing credit monitoring subscriptions for customers and offering free or discounted future products and services. Although indirect costs can be more difficult to quantify, these costs include internal investigations and communication, customer attrition and weakened customer acquisition rates. Indirect costs represent the harm a data breach can cause to your organization’s reputation and the resulting loss of customer trust. Because of the far-reaching impacts, determining how much a data breach could cost you can be tricky; per record cost estimates range from $ 0.58 3 to $ 154. 2 The lower end of cost estimates includes only direct costs while the upper end includes both direct and indirect costs. One final note on estimating cost relates to the efficacy of measuring the true impact. Neither model referenced for estimating cost applies to data breaches of over 100,000 records. The total cost of a catastrophic data breach is almost impossible to estimate. Unfortunately, most data breaches that have made the news in recent years have been catastrophic as illustrated in Fig. 1.1 .
The lag time between compromise and discovery compounds
damages incurred from a data breach. Although attackers are able to overwhelmingly compromise an organization and extract data “within minutes,” 3 it can take days for an organization to discover 1 Enterprise Incident Response Market Booms to $ 14bn as Attacks and Threats Multiply, ABI Research, Online, https://www.abiresearch.com/press/enterprise-incident-response-market-booms-to-14bn-/ .
2 2015 Cost of Data Breach Study: Global Analysis, Ponemon Institute LLC, May 2015,
WW_Security_Services&S_PKG ¼ ov34982&S_TACT ¼ 000000NJ&S_OFF_CD ¼ 10000253&downloadable at https://www-01.ibm.com/marketing/iwm/dre/signup?source ¼ ibm-uid ¼ 94450766918914542954680&cm_mc_sid_50200000 ¼ 1454295468 .ce ¼ ISM0484&ct ¼ SWG&cmp ¼ IBMSocial&cm ¼ h&cr ¼ Security&ccy ¼ US&cm_mc_ 3 Verizon Data Breach Investigations Report, Verizon, online, http://www.
verizonenterprise.com/DBIR/ .
Data breach - Lost customer records
(millions)
Ebay
JPMorgan chase
Anthem
Home depot
Target
Fig. 1.1 Data breach—lost

customer records. 0 20 40 60 80 100 120 140 160
adatabreach.Insomecases,weeksormonthspassbeforeorga-nizations uncover data breaches. In a few extreme examples, data breaches had occurred years before organizational discov-ery. Following threat forecasting practices will better position your organization to prevent data breaches, and, in addition, when a data breach does occur, threat forecasting practices will enable you to detect the intrusion quickly. But the scope of threat forecasting looks beyond the speed of organizational discovery to the speed of information sharing. It is estimated that “75% of attacks spread from Victim 0 to Victim 1 within one day (24 h).” 3 Sharing knowledge elements, such as indicators of com-promise and indicators of interest quickly with applicable plat-forms, tools and industry groups, can provide real help to likely subsequent victims.
Barriers to Adopting Threat Forecasting Practices
Given the prevalence and cost of data breaches, the need for
threat forecasting is obvious. However, many organizations have been reluctant to adopt threat forecasting practices, fearing the costs associated with the required changes. The good news is that threat forecasting relies on a foundation of solid security practices and infrastructure. You may be surprised to discover that your organization has already deployed tools that can be leveraged to begin incorporating a practice of threat forecasting. Moreover, the organizational implementation of threat forecasting practices
lends itself to a phased approach, so changes can be made (and
any associated costs incurred) incrementally.
Going Beyond Historical Threat Reporting
As previously mentioned, there is no shortage of historical
threat reporting. Many prominent companies including Verizon, HP, IBM, Symantec and McAfee release periodic threat reports. These reports detail trends and changes to the threat landscape over the preceding year, quarter or other specified time period. Although reports are generally jam-packed with useful informa-tion, the findings can be perceived as out of date since these reports are typically released sometimes months after the time period they cover. Based on these reports, many organizations will make adjustments to their security policies and procedures by focusing on key areas in the reports they have reviewed as applicable to their infrastructure. Because these reports draw data from the past, they are helpful for understanding yesterday’s threat landscape. When looking for guidance on the threat land-scape of today and tomorrow, these reports have limited use. When reviewing the information provided in these reports it is helpful to be mindful of their key limitations: timing and generalization.
STRENGTHS OF HISTORICAL THREAT REPORTS
Please don’t think we’re discounting the usefulness of historical threat
reports; they are vital tools for any IT organization or security profes-
sional. Because our focus is moving toward a threat forecasting mindset,
we’ve spent time in this chapter establishing a need to look beyond his-
torical threat reports. But make no mistake, historical threat reports
often present a wealth of information in an organized and concise man-
ner. They are invaluable tools for understanding the security threat land-
scape and security trends during the period of time in which they cover.
For more information on the uses of Historical Threat Reports, please
 refer to Chapter 9 .
refer to Chapter 9 .
Timing
Threat forecasting goes beyond historical threat reporting. By
accounting for the changing threat landscape in real time, risk is
reduced, security attacks can be prevented and infrastructure
compromises can be detected earlier. Historical threat reporting on the other hand presents the following three challenges for
organizations attempting to react to today’s landscape. They are
stale data, nimble adversaries and emerging technology.
• Stale data —As noted, by the time historical threat reports are
released the data is often stale. Instead of relying on yesterday’s
data, threat forecasting aims to quickly analyze data in as close
to real time as possible. By analyzing data and trends earlier,
you reduce your exposure to risk.
• Nimble adversaries —Security professionals aren’t the only
ones reading historical threat reports. Most adversaries will
change their tactics, techniques and procedures once they
have been identified. While this aspect of timing is intimately
related to stale data, it still bears mentioning.
• Emerging technology —Historical threat reports cannot ade-
quately account for emerging technology. By comparison,
threat forecasting can account for products on the cutting edge
of technology. Shifts in the threat landscape are often indica-
tive of new and emerging technologies in the realms of soft-
ware, web applications or hardware; threat forecasting can
make accommodations for these shifts as they occur instead
of falling behind the pace of innovation.
Generalization
Nothing is a substitute for analyzing your own data and com-
bining this with the power of global threat intelligence. Security
topics commonly covered in historical threat reports are often
subject to a great variation and may change from year to year
(or whatever the defined cycle is for the authors of the historical
threat report). By employing threat forecasting techniques, your organization can move beyond the generalizations found in his-torical threat reports to define specific threat profiles facing not just your industry but also your organization.
The State of Regulatory Compliance
In spite of the threats posed by cyber-attacks and data
breaches, there are few federal cyber security regulations in place. Most regulations that exist are industry or government specific (at the state or federal level). Today’s regulations mostly avoid pre-scribing specific cyber security measures that should be deployed but instead set forth a standard of a “reasonable” level of security. As such it is best to consider regulatory standards as minimum requirements and build up your security infrastructure accord-ingly. The following discussion of cyber security regulations is
not exhaustive, however is, instead, an overview of selected items we feel currently have the most impact on today’s security land-scape, standards and best practices. Please thoroughly familiarize yourself with the federal, state and industry-specific regulations impacting your organization.
Industry Specific Guidelines
Although there are relatively few federal cyber security regu-
lations, both the healthcare and the financial sectors are notable because of the established regulations in these industries. If your organization falls into either of these sectors they will be subject to the specified regulatory requirements. Please note that both healthcare and finance are considered critical infrastructures and as such will rely heavily on the National Institute of StandardsandTechnology(NIST)frameworkdiscussedinthe next section.
Healthcare Institutions
The healthcare industry and its associated institutions are pri-
marily regulated by the guidelines defined in the Health Insurance Portability and Accountability Act (HIPAA) that was passed in
1996. Prior to HIPAA being enacted, there was basically no gener-
ally accepted security standard nor was there any general require-ments for the protection of health information. It is comprised of multiple sections, or rules, that must be followed in order to remain in compliance. The rule that we would like to discuss is the Security Rule, as it provides the governance with respect to technology and the protection of electronic protected health infor-mation (e-PHI). According to the HIPAA Security Rule Summary, 4 the Security Rule requires covered entities to maintain reasonable and appropriate administrative, technical, and physical safe-guards for protecting e-PHI. Specifically, covered entities must: • ensure the confidentiality, integrity, and availability of all e-PHI
created, received, maintained or transmitted
• identify and protect against reasonably anticipated threats to
the security or integrity of protected information
• protect against reasonably anticipated, impermissible uses or
disclosures of e-PHI
• ensure compliance to the HIPAA Security Rule of all employees.
4 Summary of the HIPAA Security Rule, Office for Civil Rights Headquarters—U.S.
Department of Health & Human Services, Online, http://www.hhs.gov/hipaa/for-
professionals/security/laws-regulations/index.html .
The Security Rule defines “confidentiality” as meaning that
e-PHI is not to be made available or disclosed to anyone
unauthorized to access it and it follows the definition of “con-
fidentiality” as outlined in the HIPAA Privacy Rule. The Secu-
rity Rule also defines several other key areas that must be
considered while operating within the healthcare industry
including:
• Risk Analysis and Management —Performing regular risk anal-
ysis as part of the defined security management process
• Administrative Safeguards —Designating an official security
officer, putting in place the proper security management
process to oversee items like risk analysis and performing reg-
ular workforce training
• Physical Safeguards —Securing facility access as well as access
to workstations and devices that may have access to e-PHI
• Technical Safeguards —Having proper access control, audit-
ability, integrity controls and secure transmissions when
accessing e-PHI
• Policies and Procedures and Documentation Requirement —
Adopting reasonable and appropriate policies to comply with
all requirements of the Security Rule as well as maintaining a
defined document retention policy.
To dive more deeply into HIPAA, please refer to the Health
Information Privacy section of the U.S. Department of Health &
Human Services website ( http://www.hhs.gov/hipaa ).
Financial Institutions
The financial industry is subject to a number of different reg-
ulatory requirements. A patchwork quilt of regulation exists
because the regulatory environment has evolved over several
decades. This patchwork nature of legislation can make navigat-
ing the regulatory environment challenging for financial institu-tions. New legislation often not only sets forth added regulatory requirements, but also amends and updates previous legislation and regulatory requirements. The Center for Strategic and Inter-national Studies has released a report that covers the evolution of the financial industry regulatory environment in depth; we rec-ommend this report for those interested in a more detailed picture than the one provided in this chapter. 5
5 The Evolution of Cybersecurity Requirements for the U.S. Financial Industry, D. Zheng, Center for Strategic & International Studies, Online, http://csis.org/publication/ evolution-cybersecurity-requirements-us-financial-industry .
Most of the regulations we will reference in this chapter do
not explicitly spell out cyber security requirements. Instead these regulations require organizations to implement “information security systems” for various purposes (e.g., consumer data pro-tection, identity theft protection and reporting requirements). As legislation has been updated and amended over the years, the meaning of “information security systems” has evolved in an attempt to address the needs of today’s cyber security environ-ment. Table 1.1 below provides a summary of some legislation pertinent to our discussion; it is not meant to be an exhaustive list.

In part because of the lack of specificity in many regulations,
financial institutions often turn to the guidance, standards
and frameworks provided by outside organizations. Regulatory
authorities have found that 90% of financial institutions examined used one or more of these frameworks or standards. 6 We will dis-cuss two of these (PCI DSS and NIST) in the next section, Best Practices, Standards and Framework.
Cyber Security Information Sharing Legislation: Watch this Space
Of course, as the cyber security landscape continues to change,
so too will the regulatory landscape. For example, the Cybersecu-rity Information Sharing Act (CISA) is a bill newly enacted at the time of this writing. The CISA seeks to facilitate information shar-ing between the government and private companies: “In essence, the law allows companies to directly share information with the Department of Defense (DoD) (including the National Security Agency (NSA)) without fear of being sued.” 7 Time is needed before the impact of information sharing legislation can be assessed, but individuals within the information technology and information security community should keep abreast of this and other legisla-tive efforts as they emerge.
Best Practices, Standards, and Frameworks
Because the regulations that do exist mostly avoid prescribing
specific cyber security measures, organizations have turned to
security standards and frameworks. These provide templates
upon which organizations can model their cyber security pro-
grams. These standards and frameworks help an organization
build a solid foundation of cyber security practices. Following
these guidelines will help an organization meet the “reasonable”
standard set forth in the few existing federal guidelines. However, to effectively engage in threat forecasting, we believe organiza-tions treat these guidelines as just that. They provide guidance, but you often must add to your cyber security infrastructure and practices in order to reap the benefits of threat forecasting. 6 Report on Cybersecurity Practices, Financial Industry Regulatory Authority, Online, https://www.finra.org/sites/default/files/p602363 Report on Cybersecurity
Practices_0.pdf.
7 The controversial ’surveillance’ act Obama just signed, CNBC, LLC, Online,
http://www.cnbc.com/2015/12/22/the-controversial-surveillance-act-obama-just-signed.html .
PCI DSS
First published in May 2009, the Payment Card Industry Data
Security Standards (PCI DSS) establishes guidelines for “all mer-
chants and organizations that store, process or transmit” 8 payment card data. Because of the prevalent use of payment cards, these standards reach industries far beyond the financial sector. Although not mandated by federal regulations, compliance with PCI DSS is nonetheless important. Mandatory compliance is established and enforced by major payment card brands. The PCI DSS establishes data security standards for merchants and card processors (see Ta b le 1 .2 ) and outlines an ongoing process of PCI DSS compliance. If an organization accepts or processes payment cards, it must comply with PCI DSS. The PCI security standards establish rea-sonable goals for organizations dealing with payment cards and actions required to meet those goals. These goals and require-ments are set forth as common sense steps an organization must

8 Document Library, PCI Security Standards Council, Online, https://www.
pcisecuritystandards.org/document_library .
take in order to establish a reasonable level of security. As previ-
ously noted, these requirements are a starting point and should
be viewed as necessary but not sufficient in organizations striving to build a robust security environment. Table 1.2 summarizes the established goals and requirements.
In order to maintain PCI DSS compliance, the Standards
require an ongoing three step process and provide Independent
Qualified Security Assessors to monitor and validate compliance. Although the PCI DSS sets overarching industry standards, each major payment card brand maintains its own compliance pro-gram. The three step process established by the PCI DSS is in line with cyber security best practices and requires organizations to take steps to assess, remediate and report on their card processing cyber security environments on an ongoing basis ( Fig. 1.2 ). Affected organizations must assess their payment card transaction environments, examining cyber security infrastructure, policies and procedure for vulnerabilities. As identified, steps must be taken to remediate vulnerabilities. Necessary reports must then be compiled to document vulnerabilities identified and steps taken to remediate. As noted, these steps are ongoing, and orga-nizations are expected to incorporate these three steps into their cyber security and IT practices regularly.
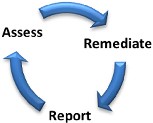
Fig. 1.2 PCI DSS three step process.
NIST Cyber Security Framework
The National Institute of Standards and Technology (NIST)
Cybersecurity Framework (CSF) was created specifically to
strengthen protection for companies classified as critical infra-
structure, however the CSF’s sphere of influence has quickly
expanded. Organizations beyond those classified as critical infra-structure have also been looking to the CSF for guidance. Although compliance with the CSF standards is voluntary, it has emerged as the standard against which organizations are judged after a data breach occurs.
The CSF is organized into five core functions: Identify, Protect,
Detect, Respond, and Recover. These core functions are then fur-ther branched into several tiers “which describe the level of sophistication and rigor an organization employs in applying its cyber security practices.” 9 Much has been written about the CSF, its core functions and organizational impacts, so we won’t dive too deeply into the framework. Please familiarize yourself with these standards as they apply to your organization. When you begin the process of implementing threat forecasting prac-tices in your organization (explained in Chapter 9 ), the NIST CSF may be a useful starting point when implementing phase one and evaluating your organization’s current cyber security practices, policies and procedures.
Defense in Depth
We strongly believe that defense in depth is the correct deploy-
ment strategy for any organization. While it may be more conve-
nient to have a single appliance solution from a deployment
standpoint, no single appliance is capable of successfully facing
all security challenges. Furthermore, we recommend a blended
security vendor environment within your infrastructure. Deploy-ing a single vendor environment, even if it is multiple products from that security vendor, only allows you to benefit from one research team. Deploying a blended vendor environment gives you access to multiple research teams who may have access to dif-ferent attack vectors (i.e., different research data) and thus pro-vides better security coverage. In our book Blackhatonomics ,10 we discuss defense in depth in terms of tier 1 and tier 2 technol-ogies. Especially in large corporations, these are the basic building blocks, in the form of tools and technologies, for building a secu-rity infrastructure.
Tier 1 Security Technologies
According to current best practices and regulations, the follow-
ing tier 1 technologies are considered “need to have” when build-
ing out a reasonably secure infrastructure:
• Firewall or next-generation firewall
• Desktop anti-virus
9 Understanding NIST’s Cybersecurity Framework, C. Thomas, Tenable Network
Security, https://www.tenable.com/blog/understanding-nist-s-cybersecurity-
framework .
10 Blackhatonomics, Chapter 7 , W. Gragido, Syngress, 05 December 2012, http://store. elsevier.com/product.jsp?isbn ¼ 9781597497404 .
• Secure web gateway
• Messaging security
• Intrusion detection/prevention systems
• Encryption (in transit or at rest)
• Security information event management.
Tier 2 Security Technologies
Tier 2 security technologies are often considered “nice to
have” when building out a security infrastructure. These tech-
nologies are used by organizations with more sophisticated
security infrastructures. They are also often purchased by orga-
nizations in the aftermath of a major security data breach. Build-ing an infrastructure that combines tier 1 and tier 2 security technologies provides the most robust risk protection. Tier 2 technologies include:
• Advanced threat detection
• Network and desktop forensics
• Network and desktop data leakage protection
• Behavioral-based analysis
• Security/threat intelligence feeds
• Threat forecasting and modeling.
Update and Evaluate Security Products and Technologies
Do not focus myopically on new security vulnerabilities. IT and
security teams can display very reactionary behavior when it
comes to new vulnerabilities and it is our opinion that you should
understand your infrastructure and its potential weaknesses as
opposed to reacting to every new announcement (though note
we are not saying it is not important to stay abreast of new
threats). The Verizon 2015 Data Breach Investigations Report
(DBIR) found that when attacks exploit a known vulnerability,
“99.9% of the exploited vulnerabilities had been compromised
more than a year after the associated common vulnerabilities
and exposures (CVE) was published.” 3 This highlights the need
for organizations to develop thoughtful policies and procedures
for installing patches and updates on existing infrastructure (both endpoints and network devices). Organizations that do not keep abreast of release notes and update devices accordingly are at greater risk of a data breach.
Cyber Security and the Human Factor
No discussion of security best practices can be considered
complete without factoring in employee behavior. From phishing scams to social engineering, your employees are likely your largest security vulnerability. We believe every employee should be security-minded. Although turning your employees from security liabilities to champions requires organizational effort, a thorough (and engaging) training effort can pay dividends. The Target data breach is believed to be associated with the successful social engi-neering of one of Target’s suppliers. For more information on this data breach, please refer to Chapter 9 (Connecting the Dots). Today’s Information Assurance Needs
Increasingly, organizations are managing information systems
and information-related risks with the same thoughtfulness
applied to more traditional systems (i.e., computer systems and
networks). This practice is known as information assurance
(IA). IA experts “seek to protect and defend information and infor-mation systems by ensuring confidentiality, integrity, authentica-tion, availability, and nonrepudiation.” Essentially, “IA is the process of ensuring that authorized users have access to autho-rized information at the authorized time.” 11 Meeting IA needs today requires the ability to mesh regulatory requirements, best practices and infrastructure needs with a view towards the security landscape of today and tomorrow. By deploying threat forecasting techniques within your organization, you will undoubtedly enhance the security position of your organization. Because the last thing you want to do is invoke your IR plan, threat forecasting helps you head off the next threat.
Welcome to threat forecasting.
11 Iowa State University Information Assurance Center, http://www.iac.iastate.edu/ .

THREAT FORECASTING
Synopsis
In this chapter you will learn about the high-level concepts that
are associated with big data collection and how they are applied to threat forecasting. You will learn how the similarities of weather forecasting, epidemiology, and high frequency trading algorithms play an important role in threat forecasting. You will be intro-duced to concepts that play a greater role in Chapter 3 and beyond, all of which influence the process of forecasting and pre-dicting threat.
Introduction
This chapter will cover the definition of threat forecasting.
Additionally, the chapter will cover the reasons why threat fore-
casting is needed and how this will aid any enterprise and
small-to-medium business with information that is specific to
industry vertical, geographical location, gold corporate image