The main aim of a penetration test is to hack into a web application in a way that a real-world malicious hacker would do it. Tor provides an interesting option to emulate the steps that a black hat hacker uses to protect his or her identity and location. Although an ethical hacker trying to improve the security of a web application should be not be concerned about hiding his or her location, by using Tor it gives you an additional option of testing the edge security systems such as network firewalls, web application firewalls, and IPS devices.
Black hat hackers try every method to protect their location and true identity; they do not use a permanent IP address and constantly change it in order to fool the cybercrime investigators. You would find port scanning requests from a different range of IP addresses and the actual exploitation having the source IP address that your edge security systems are logging for the first time. With the necessary written approval from the client, you can use Tor to emulate an attacker by connecting to the web application from an unknown IP address that the system does not usually see connections from. Using Tor makes it more difficult to trace back the intrusion attempt to the actual attacker.
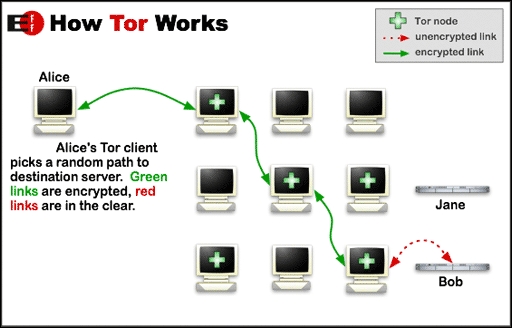
Tor uses a virtual circuit of interconnected network relays to bounce encrypted data packets, the encryption is multi layered and the final network relay releasing the data to the public Internet cannot identify the source of the communication as the entire packet was encrypted and only a part of it is decrypted at each node. The destination computer sees the final exit point of the data packet as the source of the communication, thus protecting the real identify and location of the user. The following diagram explains this process:
Following are the steps to install Privoxy and Tor:
- Web browsers are notorious for leaking personal information about the user and we would use Privoxy, which is a web proxy to protect against such leaks. It's a highly customizable proxy that can be used to defend against web browsers leaking private information. The primary focus of Privoxy is privacy enhancement. Since the proxy is sitting between your web browser and the Internet, it is the best place to filter out outbound personal information that the web browser is leaking. Similarly, install Tor. Tor and Privoxy are both proxies. The web browser forwards the request to Privoxy and in turn Privoxy forwards it to be Tor to be anonymized:
- Next, edit the Privoxy configuration file and add the parameters, as shown here. Here, we are configuring Privoxy to send all
socks4acompliant web traffic to port9050where Tor is listening:
- Now, edit the
torrcfile placed at the/etc/tor/directory and add the following at the end (the lines with a#are comments):SafeSocks 1 WarnUnsafeSocks 1 SocksListenAddress 127.0.0.1 SocksPort 9050 ControlPort auto
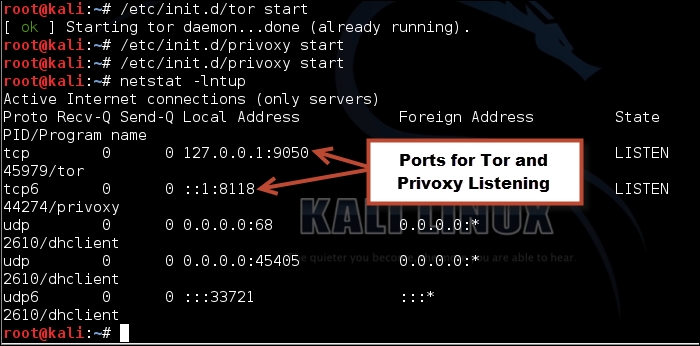
- Verify services and listening ports:
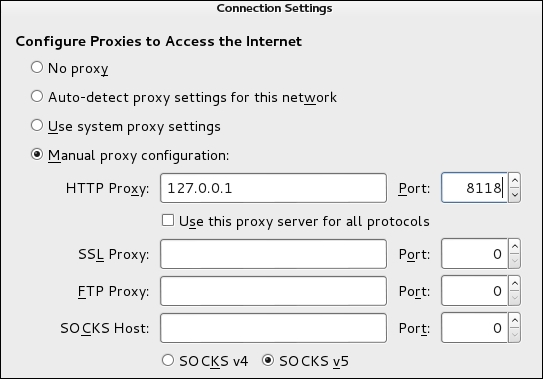
- Configure web browser to use Privoxy as the proxy:
- Finally, visit the website
check.torproject.orgto verify if your requests are indeed flowing through the Tor network: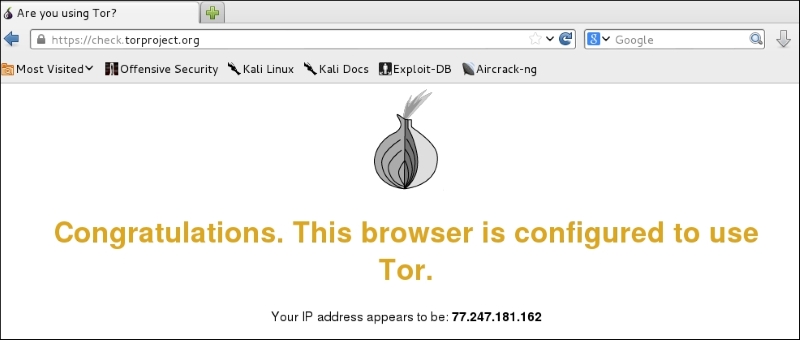
The IP address shown here is surely not the one assigned by my ISP but is somewhere in Europe, working as the exit node for the Tor network.
So this is how the packets are flowing on the network. The web browser forwards the request to Privoxy, which sanitizes the request and removes all the information that can reveal the true identity of the client and forward the request to the Tor proxy on the client. The request from the Tor proxy is then encrypted and routed using the huge list of relays in the Tor network to be finally released by the exit node to be delivered to the actual destination:
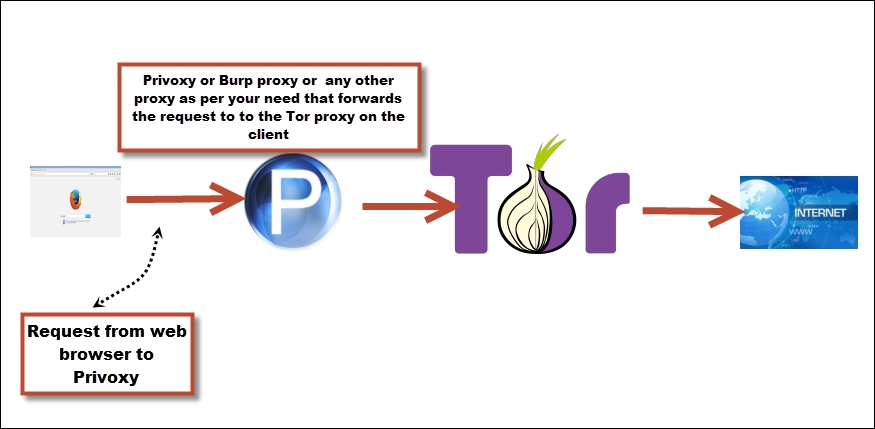
Following are the final words for Tor:
- The
torrcconfiguration file for Tor is highly customizable. You can choose specific exit nodes from your country of choice. You can also configure Tor to reject insecureSOCKSmethod that could reveal the true IP address of the user. These are just a few options; spend some time on it and you would truly know its power. - Tor also has a graphical user interface known as Vidalia, which can be downloaded separately, that can be used to start and stop Tor and configure a few more settings.
- Tor is non-transparent proxy. The Internet-bound data from each application that you want to anonymize should be separately configured to use Tor. For example, if you want the wget to use Tor through the Privoxy proxy, you will have to add in the
http_proxyenvironment variable as follows: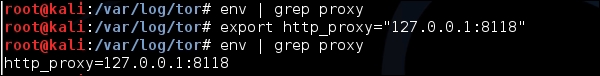
- The Tor network can also be used to host hidden website that can only be accessed when a client is connected to the tor network, it is hidden from the public Internet. Recently, these website have gained attention from law enforcement agencies for conducting illegal business. The experts from these law enforcement agencies were able to penetrate into the Tor network and we are able to expose the source of these website using unknown flaws. This surprised many as the Tor network was seen as uncrackable.