Response splitting can be described as a flaw that an attacker could exploit to inject data in the HTTP response header. By injecting data in the header the attacker can trick the browser of the user to perform malicious activities. This attack does not directly attack the server but is used to exploit the client.
An example would be a web application taking an input from the user via the GET method and then redirecting the user to a new web page depending on the value that the user sent. A typical scenario would be the user selecting a region and application redirecting the user to a web page tailored for that region.
The following PHP code would set the Location field in the response to the users when they are redirected to the new page:
<?php
Header("Location: http://fakewebsite.com/regions.php?region=".$_GET['region'] );
/* This code will set the location field in the header . */
Exit;
?>If the user selects the region as India, the Location field in the response header will be set as http://fakewebsite.com/regions.php?region=India as shown in the following screenshot:
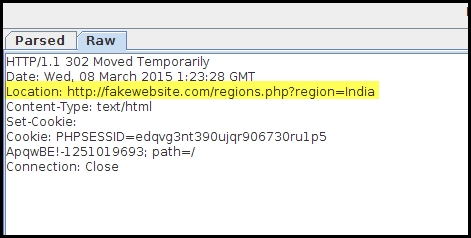
As we can see, the region parameter is directly embedded in the Location field of the response header. A vulnerable web application not performing input validation would accept other values too. Instead of sending the value India, we can send some meta-characters such as carriage return (\r) and line feed (\n), along with some additional input that would terminate the value in the Location field and create additional fields in the HTTP header.
\r and \n are two metacharacters that are used to signify a new line. With the new line characters, the attacker can inject a new header field in the browser. You can set the Cookie field in the HTTP header with the following and perform a session fixation attack:
\r\nSet-Cookie:PHPSESSID=edqvg3nt390ujqr906730ru1p5
An important point to note here is that you need to URL encode the special characters, the encoded value would look like this:
%0d%0aSet-Cookie%3APHPSESSID%3Dedqvg3nt390ujqr906730ru1p5
The final request sent to the web application instead of the value of the selected region would be as shown in the following link and a new cookie would be set for the victim when the server sends the response header:
http://fakewebsite.com/regions.php?region=%0d%0aSet-Cookie%3APHPSESSID%3Dedqvg3nt390ujqr906730ru1p5