This module allows you to create customized e-mails to target specific victims. The aim of this module is to integrate a payload into the attachment and send it across to the victim via a spoofed e-mail.
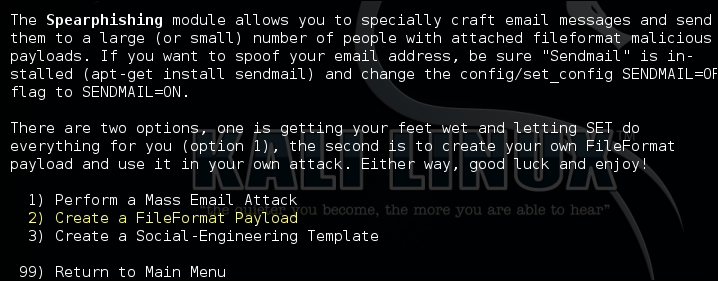
You need to select the second option, that is Create a FileFormat Payload, which will guide you to select a specific file format to exploit. The entire menu is easy to follow and self-explanatory:
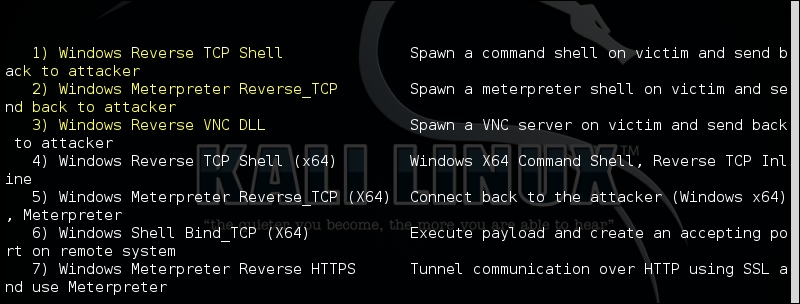
Next, select a specific payload that you want to use; it will prompt you to select the type of command shell that you want to execute when the victim machine is successfully exploited. The reverse TCP shell and meterpreter reverse TCP shell are the most useful ones as outbound traffic is more likely to be allowed through the firewall on the client side:
As you move ahead selecting some additional options, the social engineering toolkit will prompt you to select a prebuilt e-mail template or the option to build the contents of the e-mail all by yourself. The predefined e-mail templates are helpful if you are falling short of words when creating the e-mail.
Be careful when selecting the predefined template as anti-spamming systems have been tuned to filter the contents of these templates.
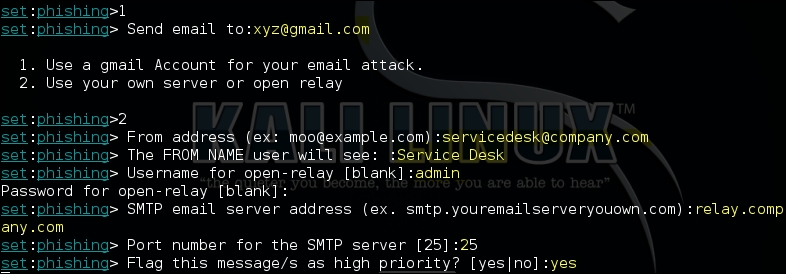
At the final stage, you are asked to either select a public mail server such as Gmail or use your own mail server. Choosing your own mail server has one distinct advantage: it allows you to spoof an e-mail address and, if the victim's mail server does not performs reverse DNS lookups, the e-mail is sure to hit the victim's mailbox.
If you want to use Kali Linux as your mailing server, you need to install sendmail and change the SENDMAIL option to ON in the set_config file. The set_config file is in the /usr/share/set/config/ directory and is the configuration file used by the social engineering toolkit:
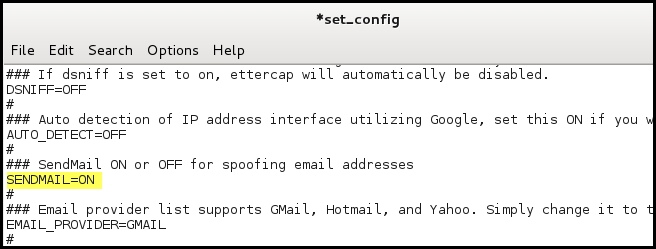
Sending the e-mail through a different e-mail provider is also possible by changing the EMAIL_PROVIDER option to Hotmail or Yahoo!.
The various options when sending the e-mail through a self-hosted mail server are shown in the following screenshot: