Using websites to launch a social engineering attack allows the attack to target a large number of users. The website attack module in the social engineering toolkit includes various methods to build a social engineering attack using a website.
The following methods are included in the social engineering toolkit:
- Java applet attack
- Credential Harvester attack
- Web jacking attack
- Metasploit browser exploit
- Tabnabbing attack
The Java applet attack method creates a Java applet infected with a malicious payload. The payload is a shell or meterpreter code that provides shell access to the victim's machine. To build a complete attack, the tool will prompt if you want to clone a website that you know the victim would trust and spend time browsing on. The applet is then loaded on to the cloned website.
The important step is to entice the user to visit the website which will load the applet and provide shell access to the attacker. URL shortener service can be used to hide the URL or a similar domain name can be registered to trick the user.
In this method, we are not exploiting any client-side flaws but tricking the user into browsing a website that loads a malicious Java applet. Since the applet is not signed by a trusted certificate authority, it will display a warning when the applet loads which most users would ignore and proceed anyway.
The Java applet attack method has been successfully tested against a wide range of web browsers and operating systems.
The following dialog box is displayed at the time the Java applet is loaded:

Stealing the credentials of the user has always been very attractive for attackers. Using the credential harvester attack method you can clone a website that requires the user to log in, for example a social networking website such as Facebook or Twitter.
Like the other attack methods, you have to host the cloned website that you created using the social engineering toolkit on a domain with a similar name to increase the probability of a user interacting and browsing the website.
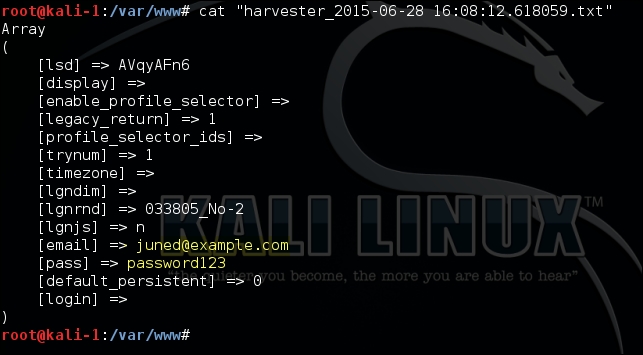
The user visits the website assuming it to be the real one and types in credentials which are captured by the attacker and can be used to impersonate the victim. The social engineering tool retrieves the username and password by capturing all POST requests on the website and identifies predictable field names from it.
The data captured is saved in /var/www directory and its contents can be viewed as shown in the following screenshot:
The success of all social engineering attacks depends on the level of user interaction.
The web jacking attack is similar to the credential harvesting attack with a few additional tricks. Using this method, the attacker creates a fake website and when the user clicks on the link a web page appears with a message stating that the website has been moved and that you need to click on the message which includes the link to the website, as shown in the following screenshot:
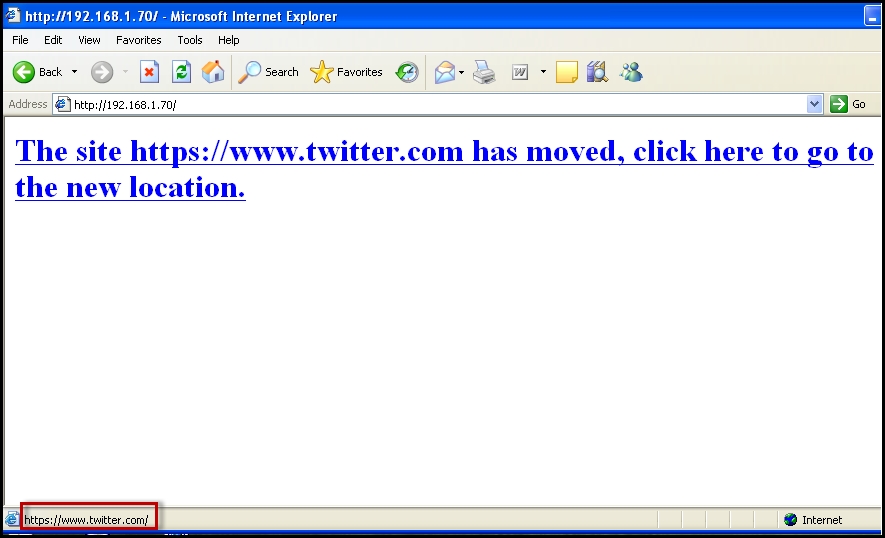
If the user hovers over the message, the correct URL of the website is shown in the status bar at the bottom. But as soon as the user clicks on the message, the browser is redirected to the fake website that the social engineering toolkit cloned.
The steps to build a web jacking attack are similar to the credential harvesting attack. These modules from the social engineering toolkit should be used to impart training to the users and educate them on ways to respond to such attacks.
With the integration of the social engineering toolkit and Metasploit, you can use the client-side exploits available in Metasploit directly from the interface of SET. The Metasploit browser exploit method is part of the website attack module.
Using this attack module, you can get shell access on the victim's computer by exploiting multiple client-side softwares listed as follows. For example, a malicious website can exploit the memory corruption vulnerability in Microsoft Internet Explorer and inject shell into it. Similarly, other client-side software can be exploited using malicious files:
- Microsoft Internet explorer
- Java
- Adobe Flash Player
- Apple QuickTime
- Firefox
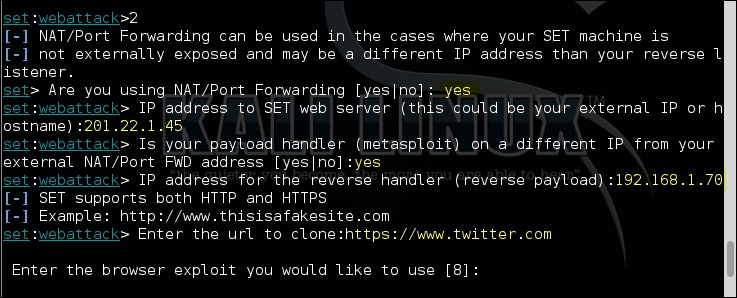
Metasploit has multiple exploits for client-side software. Using a malicious website, you can exploit the vulnerabilities in these softwares and inject a shell into the machine of the end user. The malicious website can be created by using prebuilt templates or can be cloned from a live website which can entice the user. Along with the exploit, you also have to select the payload. The reverse TCP shell is the recommended payload as the client will create an outbound connection to your server, which can help circumvent any firewall rules. Once you have selected the exploit, payload SET will ask for a few details as shown in the following screenshot. In order for the reverse shell to connect back to the attacker's machine, you need to specify the IP address of the Kali Linux machine when configuring the attack. If Kali Linux is behind a firewall and NAT is implemented, you will also have to provide the public IP address so that the victim can reach the clone website as shown here. Also, make sure you have the port forwarding and NAT rules correctly configured:
All the major web browsers have introduced the tabbed browsing feature that allows the user to open multiple web pages in a single browser window. Each section of the browser window is known as a tab. The tabnabbing attack makes use of this feature to open a fake website on the browser when the tab is not in focus and the user is viewing another web page in a different tab. The JavaScript on the malicious page will redirect itself to the cloned website.
The tabnabbing attack is deployed when you want to redirect the user to a malicious website that you control. This website is normally a cloned web page of a popular website the user uses.
Here are steps that we would follow to build the attack:
- You need to clone a website to entice the user, which can be done from the social engineering toolkit interface.
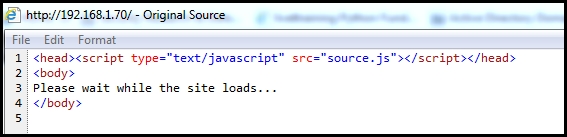
- Next you need to trick the user into opening the URL. When the URL is clicked, the following web page shows up asking the user to wait until the web page is loaded:
- As soon as the user switches to another tab, the web page is redirected to the fake website that you created. If you view the source of this URL, you will see JavaScript is used to perform the redirect when the tab is not in focus. Once the cloned website opens and the user moves back to the tab, they might assume the website to be the real one. The attacker can clone the login page of the web page to steal the credentials: