This chapter gives an overview of Android app internals. It is essential to understand how apps are being built under the hood, what it looks like when it is installed on the device, how they are run, and so on. We make use of this knowledge in other chapters, where we discuss topics such as reverse engineering and pentesting Android apps. This chapter covers the following topics:
- Basics of Android apps
- App build process
- Understanding how Android apps run on an Android device
- Dalvik Virtual Machine (DVM) and Android Runtime (ART)
- Basic building blocks of Android apps
Every app that we download and install from the Play Store or any other source has the extension .apk. These APK files are compressed archive files, which contain other files and folders that we will discuss in a moment. Typically, the end users download these apps and install them by accepting the required permissions and then use them. Let's dive into the technical details such as what these apps contain and how they are actually packaged, what happens when we install them, and so on.
First let's start with the final binary that we use as an end user. As mentioned earlier, Android apps have the extension .APK (short for Android Application Package), which is an archive of various files and folders. This is typically what an end user or a penetration tester would get. Since an Android app is an archive file, we can uncompress it using any traditional extraction tool. The following diagram shows the folder structure of an uncompressed APK file. Universally, this is the same with any APK with some minor differences such as having an extra lib folder when there are additional libraries included in the app:
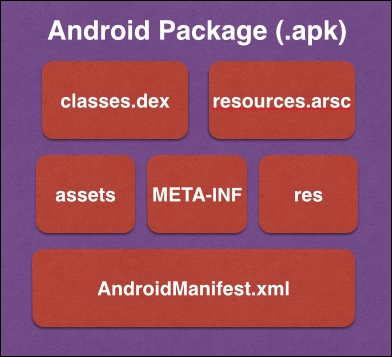
Steps to uncompress an APK file:
- Change the file extension from
.apkto.zip. - In Linux/Mac, use the following command for uncompressing the file:
Unzip filename.zip - In Windows, we can use 7-Zip, WinRAR, or any other similar tool to extract the contents.
Let's see what each of these files/folders contain:
AndroidManifest.xml: This file holds most of the configuration details about the app. It also includes the package name, details about the app components that are used in the app, security settings for each app component, permissions that are requested by the application, and so on.classes.dex: This file contains the Dalvik Bytecode generated from the source code written by developers. This DEX file is what is executed on the device when the app runs. In a later section of this chapter, we will see how this DEX file can be manually generated and executed on an Android device.resources.arsc: This file holds the compiled resources.Res: This folder consists of raw resources that are required by the application. Examples would be images such as app icons.Assets: This folder allows a developer to place the files of his interest such as music, video, preinstalled databases, and so on. These files will be bundled with the app.META-INF: This folder contains the application certificate along with the SHA1 digests of all the files used in the application.
If you want to get a specific APK file of your choice, the following are the ways to get it:
If the app is already installed on your device, pulling APK files from the device is a matter of a few adb commands.
Depending upon who installed the app and what extra options are provided during the installation, there are different storage locations on Android devices. Let's look at each of them.
Apps that are installed by the user will be placed under this location. Let's look at the file permissions of the apps installed under this folder. The following excerpt shows that all these files are world readable and that anyone can copy them out without requiring additional privileges:
root@android:/data/app # ls -l -rw-r--r-- system system 11586584 1981-07-11 12:37 OfficeSuitePro_SE_Viewer.apk -rw-r--r-- system system 252627 1981-07-11 12:37 PlayNowClientArvato.apk -rw-r--r-- system system 14686076 2015-11-14 02:28 com.android.vending-1.apk -rw-r--r-- system system 5949763 2015-11-13 17:39 com.estrongs.android.pop-1.apk -rw-r--r-- system system 39060930 2015-11-14 02:32 com.google.android.gms-2.apk -rw-r--r-- system system 677200 1981-07-11 12:37 neoreader.apk -rw-r--r-- system system 4378733 2015-11-13 15:22 si.modula.android.instantheartrate-1.apk -rw-r--r-- system system 5656443 1981-07-11 12:37 trackid.apk root@android:/data/app #
The preceding excerpt shows the world read permissions of APK files under the /data/app/ folder.
Apps that come with system image will be placed under this location. Let's look at the file permissions of the apps installed under this folder. The following excerpt shows that all these files are world readable and that anyone can copy them out without requiring additional privileges:
root@android:/system/app # ls -l *.apk -rw-r--r-- root root 1147434 2013-02-01 01:52 ATSFunctionTest.apk -rw-r--r-- root root 4675 2013-02-01 01:52 AccessoryKeyDispatcher.apk -rw-r--r-- root root 51595 2013-02-01 01:52 AddWidget.apk -rw-r--r-- root root 21568 2013-02-01 01:52 ApplicationsProvider.apk -rw-r--r-- root root 2856 2013-02-01 01:52 ArimaIllumination.apk -rw-r--r-- root root 7372 2013-02-01 01:52 AudioEffectService.apk -rw-r--r-- root root 147655 2013-02-01 01:52 BackupRestoreConfirmation.apk -rw-r--r-- root root 619609 2013-02-01 01:52 Bluetooth.apk -rw-r--r-- root root 5735427 2013-02-01 01:52 Books.apk -rw-r--r-- root root 2441128 2013-02-01 01:52 Browser.apk -rw-r--r-- root root 11847 2013-02-01 01:52 CABLService.apk -rw-r--r-- root root 200199 2013-02-01 01:52 Calculator.apk -rw-r--r-- root root 92263 2013-02-01 01:52 CalendarProvider.apk -rw-r--r-- root root 3345 2013-02-01 01:52 CameraExtensionPermission.apk -rw-r--r-- root root 141003 2013-02-01 01:52 CertInstaller.apk -rw-r--r-- root root 215780 2013-02-01 01:52 ChromeBookmarksSyncAdapter.apk -rw-r--r-- root root 7645090 2013-02-01 01:52 ChromeWithBrowser.apk -rw-r--r-- root root 1034453 2013-02-01 01:52 ClockWidgets.apk -rw-r--r-- root root 1213839 2013-02-01 01:52 ContactsImport.apk -rw-r--r-- root root 2100200 2013-02-01 01:52 Conversations.apk -rw-r--r-- root root 182403 2013-02-01 01:52 CredentialManagerService.apk -rw-r--r-- root root 12255 2013-02-01 01:52 CustomizationProvider.apk -rw-r--r-- root root 18081 2013-02-01 01:52 CustomizedApplicationInstaller.apk -rw-r--r-- root root 66178 2013-02-01 01:52 CustomizedSettings.apk -rw-r--r-- root root 11816 2013-02-01 01:52 DefaultCapabilities.apk -rw-r--r-- root root 10989 2013-02-01 01:52 DefaultContainerService.apk -rw-r--r-- root root 731338 2013-02-01 01:52 DeskClockGoogle.apk
Apps that require special copy protection on the device usually are under this folder. Users who do not have sufficient privileges cannot copy apps installed under this location. But, it is still possible to extract these APKs if we have root access on the device.
Now, let's see how we can extract an app of our choice from the device. This is essentially a three-step process:
- Find the package name.
- Find the path of the APK file on the device.
- Pull it out from the device.
Let's see it in action. The following examples are shown on a real Android device running Android 4.1.1.
If we know the name of the app, we can use the following command to find the package name of the application:
adb shell –d pm list packages | find "your app"
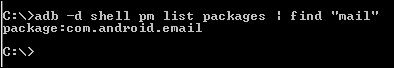
As we can see in the previous screenshot, this will show us the package name.
Now, the next step is to find the path of the APK associated with this package. Again, we can use the following command to achieve this:
adb –d shell pm path [package name]
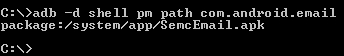
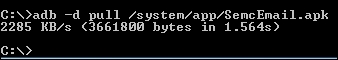
As expected, it is located under the /system/app/ directory since it is a preinstalled application. The last step is to pull it out from the device. We can now pull it out using the following command:
adb –d pull /system/app/[file.apk]
Similar to the process with preinstalled apps, if we know the name of the app, we can use the following command to find the package name of the application installed by the user:
adb shell –d pm list packages | find "your app"
This time, I am looking for an app called heartrate that is installed from the Play Store. This can be downloaded from the following link in case you want to install it on your device:
https://play.google.com/store/apps/details?id=si.modula.android.instantheartrate&hl=en
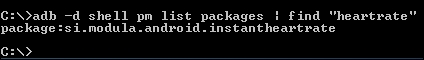
Well, as we can see in the previous screenshot, we have got the package name. We can use the following command to find its APK path:
adb –d shell pm path [package name]
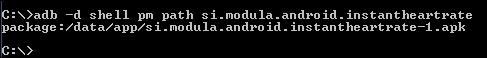
This APK is under the /data/app/ directory since it is a user installed application.
Finally, we can pull this app from the device using the following command similar to how we did previously with preinstalled apps:
adb –d pull /data/app/[file.apk]
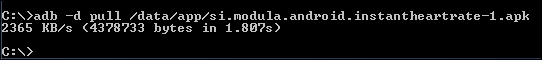
Apart from the APK files, you may also notice .odex files if you navigate to the /system/app/ directory using the adb shell. These .odex files are optimized .dex files that are usually created on an apps first run. Creation of these .odex files is internally done using a tool called dexopt. This process improves app performance and it is usually done during the first start up process of Android OS.
When you do the preceding mentioned process on the latest version of an Android device, the location of these APK files are slightly different from what we have seen. The following is the specification of the emulator used to test this:
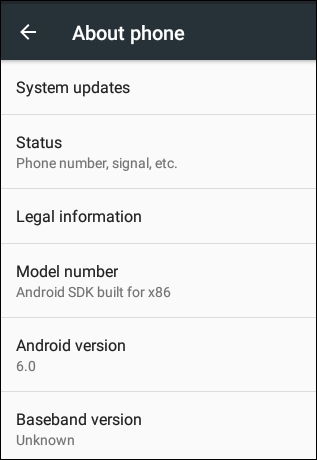
Each APK has got its own directory inside the path /data/app/ and /system/app/ for user installed apps and preinstalled apps respectively.
A sample location of a preinstalled app:
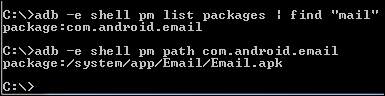
A sample location of a user installed app:
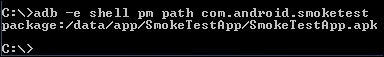
In this case, if you explore the file system using the adb shell, each .odex file that is associated with the app is placed inside the app's own directory shown in the previous screenshot rather than /system/app/.