This book is focused more on concepts rather than tools. However, automated tools often save us some time during penetration tests. The following are some of the most common automated tools that are available for automated assessments of Android applications.
Drozer and Quark are two different tools that may come in handy during your Android app assessments.
We will discuss many techniques such as hooking into application processes and performing runtime manipulations, reverse engineering, manually discovering and exploiting vulnerabilities, and so on. However, this section focuses on using automated tools such as Drozer and Quark in order to get you started with the assessments.
Drozer is a framework for Android security assessments developed by MWR labs. As of writing this book, Drozer is one of the best tools available for Android Security Assessments. According to their official documentation, "Drozer allows you to assume the role of an Android app and to interact with other apps, through Android's Inter-Process Communication (IPC) mechanism, and the underlying operating system".
When dealing with most of the automated security assessment tools in the Web world, we need to provide the target application details, go and have a cup of coffee, and come back to get the report. Unlike regular automated scanners, Drozer is interactive in nature. To perform a security assessment using Drozer, the user has to run the commands on a console on his workstation. Drozer sends them to the agent sitting on the device to execute the relevant task.
Drozer installation instructions were shown in Chapter 1, Setting Up the Lab.
First, launch the Drozer terminal, as shown following:
This section gives you a brief idea about how to get started with Drozer for your security assessments. We will take an example of how to exploit vulnerable activities, which are exported. We will discuss these vulnerabilities without using Drozer in more detail later in this book.
We can install the app in a real device or emulator. In my case, I am using an emulator for this demo.
Let's install the testapp application using the following command:
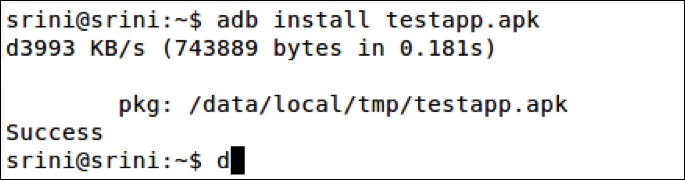
The testapp.apk that we are using in this example has an exported activity. Activities when exported can be launched by any other application running on the device. So, let's see how we can make use of Drozer to perform a security assessment of this app.
The following are some useful commands available in Drozer.
dz> list
The preceding command shows the list of all Drozer modules that can be executed in the current session:
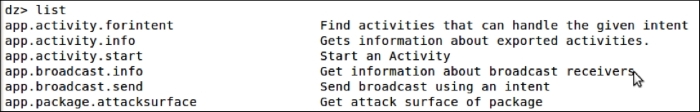
The previous screenshot shows the list of modules that can be used (The output is truncated for brevity).
To list out all the packages installed on the emulator, run the following command:
dz> run app.package.list
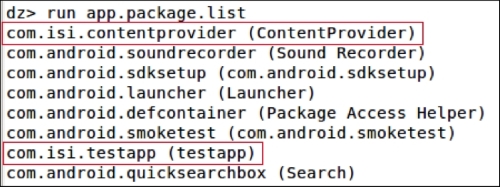
Now, to figure out the package name of a specific app, we can specify the flag -f with the string we are looking for:
dz> run app.package.list –f [string to be searched]
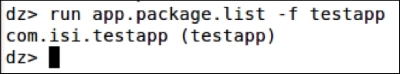
As we can see in the previous screenshot, we got our target app listed following:
com.isi.testapp
To see some basic information about the package, we can run the following command:
dz> run app.package.info –a [package name]
In our case:
dz> run app.package.info –a com.isi.testapp
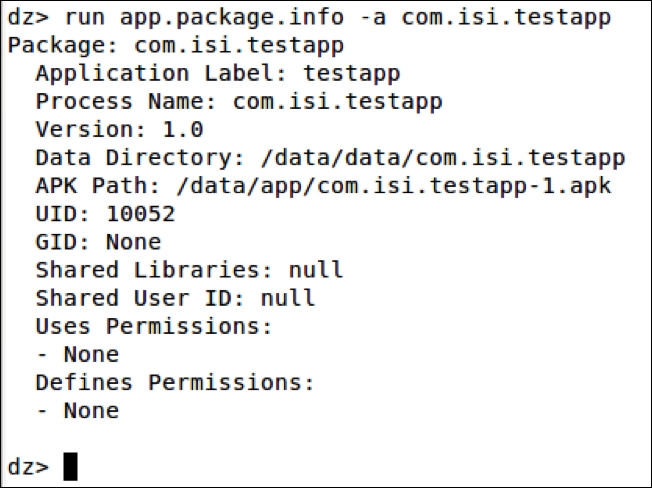
We can see a lot of information about the app. The preceding output shows where the app data is residing on the file system, APK path, if it has any shared User ID, and so on.