All of our examples and demos so far, were on rooted devices. Some of our readers might argue that not many devices are rooted and there isn't much we can do for non-rooted devices
In this section, we will see how we can examine the internal memory of apps on non-rooted devices using the backup feature. Taking backup of a specific app or the device allows us to examine it for security issues.
We will use WhatsApp lock as our target app for this demo; this is the same application we used during the shared preferences section:
C:\ >adb pull /data/data/com.whatsapplock/shared_prefs/ com.whatsapplock_preferences.xml failed to copy '/data/data/com.whatsapplock/shared_prefs/ com.whatsapplock_preferences.xml' to 'com.whatsapplock_preferences.xml': Permission denied
As you can see, we get the permission denied error, as our adb is not running as root.
Now let's use the backup technique of android to find security issues by following these steps:
- Backup the app data using the
adb backupcommand. - Convert the
.abformat to the.tarformat using the android backup extractor. - Extract the TAR file using the pax or star utility.
- Analyze the extracted content from the previous step for security issues.
Android allows us to back up entire phone data or a specific application data by using the inbuilt adb backup command.
You can see the options provided by the adb backup command in the following screenshot:
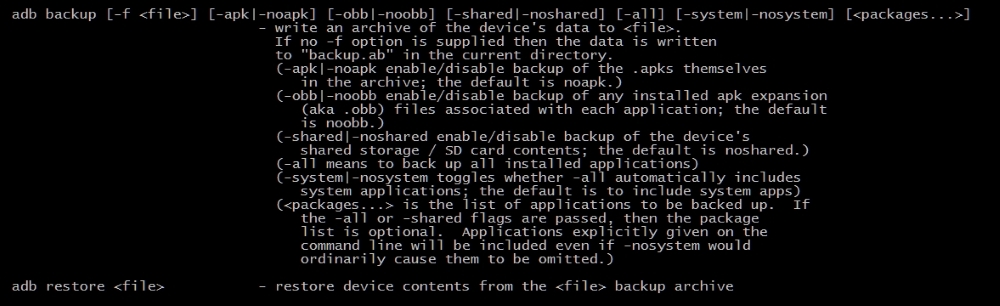
As we can see, we have lots of options to tweak our backup needs.
We can backup an entire android phone using the following command:
adb backup –all –shared –apk
We can also store only a specific app using the following command:
adb backup -f <filename> <package name>
In our case, it will be as follows:
adb backup –f backup.ab com.whatsapplock
Running the command gives us the following output:
C:\> adb backup -f backup.ab com.whatsapplock
Now unlock your device and confirm the backup operation.
As we can see, the above command suggests to us to unlock the screen and click on the Back up my data button on the device. It also provides provision to encrypt the backup, you can type in the password if you wish to use encryption:
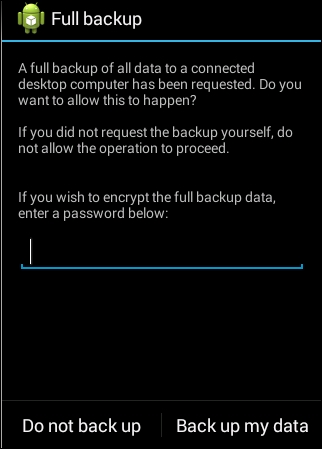
Once you click the button, it will create a new file in our working directory called backup.ab:
C:\backup>dir Volume in drive C is System Volume Serial Number is 9E95-4121 Directory of C:\backup 25-Jan-16 11:59 AM <DIR> . 25-Jan-16 11:59 AM <DIR> .. 25-Jan-16 11:59 AM 4,447 backup.ab C:\backup>
Even though we have got the backup.ab file, we cannot directly read the contents of this file. We need to first convert it into a format which we can understand. We will use one of our favorite tools, Android backup extractor, to convert our .ab file into .tar format.
Let's download Android Backup Extractor from the following URL:
http://sourceforge.net/projects/adbextractor/
Once we extract the ZIP file, we should see the following files and folders:
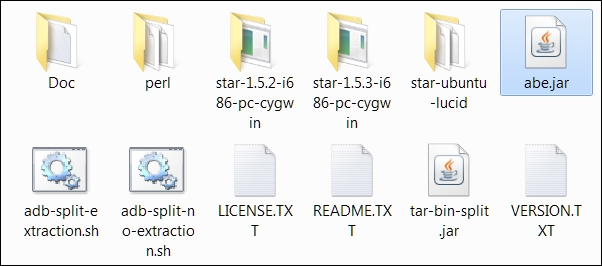
Though each of these files and folders serve some purpose, we are only interested in abe.jar. Copy the abe.jar file into the backup directory where we have kept our backup.ab file:
C:\backup>dir Volume in drive C is System Volume Serial Number is 9E95-4121 Directory of C:\backup 25-Jan-16 12:03 PM <DIR> . 25-Jan-16 12:03 PM <DIR> .. 03-Nov-15 01:10 AM 6,167,026 abe.jar 25-Jan-16 11:59 AM 4,447 backup.ab C:\backup>
Let's look at the command flags provided by this tool by issuing the following command:
C:\backup>java -jar abe.jar --help Android backup extractor v20151102 Cipher.getMaxAllowedKeyLength("AES") = 128 Strong AES encryption allowed, MaxKeyLenght is >= 256 Usage: info: abe [-debug] [-useenv=yourenv] info <backup.ab> [password] unpack: abe [-debug] [-useenv=yourenv] unpack <backup.ab> <backup.tar> [password] pack: abe [-debug] [-useenv=yourenv] pack <backup.tar> <backup.ab> [password] pack 4.4.3+: abe [-debug] [-useenv=yourenv] pack-kk <backup.tar> <backup.ab> [password] If -useenv is used, yourenv is tried when password is not given If -debug is used, information and passwords may be shown If the filename is '-', then data is read from standard input or written to standard output
As we can see, we can use abe.jar to pack or unpack the backup file. So, let us use the unpack option to unpack the backup file. As we can see in the help, we need to specify the target file as .tar:
C:\backup>java -jar abe.jar -debug unpack backup.ab backup.tar Strong AES encryption allowed Magic: ANDROID BACKUP Version: 1 Compressed: 1 Algorithm: none 116224 bytes written to backup.tar
As shown above, the backup file is converted into a TAR file and it should be present in our working directory:
android@laptop /cygdrive/c/backup $ dir abe.jar backup.ab backup.tar
We should now extract the contents by using the star utility which is available in Android backup extractor software or pax utility from Cygwin.
The syntax for star.exe is as follows:
C:\backup> star.exe –x backup.tar
Let's use the pax utility from Cygwin to extract contents of backup.tar.
First, we need to install Cygwin, binutils, and pax modules from its repositories. After the installation, open the Cygwin terminal and you will be greeted with the following terminal window:
android@laptop ~ $ pwd /home/android android@laptop ~ $
As we can see, we are not in the c:\backup directory. To access the c drive you need to go into cygdrive, then into C drive by using the following command:
android@laptop ~ $ cd /cygdrive/c/backup $ ls abe.jar backup.ab backup.tar
Finally, extract the TAR file using the pax command:
$ pax -r < backup.tar
The preceding command creates the apps folder in the present directory, which you can see by using the ls command:
android@laptop /cygdrive/c/backup $ ls abe.jar apps backup.ab backup.tar
Let's review the content of apps to see if we can find anything interesting:
android@laptop /cygdrive/c/backup $ cd apps android@laptop /cygdrive/c/backup/apps $ ls com.whatsapplock android@laptop /cygdrive/c/backup/apps $ cd com.whatsapplock/ android@laptop /cygdrive/c/backup/apps/com.whatsapplock $ ls _manifest db f r sp
As we can see, there is a folder with the name of the com.whatsapplock package, which contains the following folders:
_manifest– theAndroidManifest.xmlfile of the appdb– contains.dbfiles used by the applicationf– the folder used to store the filessp– stores shared preferences XML filesr– holds views, logs, and so on
Since we already know this app stores PINs in the shared preferences folder, let's review it for insecure shared_preferences:
android@laptop /cygdrive/c/backup/apps/com.whatsapplock $ cd sp/ android@laptop /cygdrive/c/backup/apps/com.whatsapplock/sp $ dir com.whatsapplock_preferences.xml inmobiAppAnalyticsAppId.xml IMAdTrackerStatusUpload.xml inmobiAppAnalyticsSession.xml impref.xml WhatsLock.xml android@laptop /cygdrive/c/backup/apps/com.whatsapplock/sp $ cat com.whatsapplock_preferences.xml <?xml version='1.0' encoding='utf-8' standalone='yes' ?> <map> <string name="entryCode">1234</string> <int name="revstatus" value="1" /> </map> android@laptop /cygdrive/c/backup/apps/com.whatsapplock/sp $
As we can see in the preceding excerpt, if we have a backup of a specific app we can analyze the data of that application without having root access on the device. This is really useful when we have to show a proof of concept without a rooted device. Many Android forensics tools also use this backup technique to extract data from the device without root access.
We can also make changes to the backup file that we have extracted. If you wish to make changes to the backup and restore it on the device then you can follow the following steps to accomplish it:
- Backup the target app:
adb backup -f backup.ab com.whatsapplock - Remove the header and save the modified file using the
ddcommand. Save the list of files to preserve their order:dd if=backup.ab bs=24 skip=1| openssl zlib -d > backup.tar tar -tf backup.tar > backup.list
- Extract the tar file and make the required changes to the content of the app, like changing the PIN, changing preferences, and so on:
tar -xf backup.tar - Create the
.tarfile from the modified files:star -c -v -f newbackup.tar -no-dirslash list=backup.list - Append the header from the original
.abfile to the new file:dd if=mybackup.ab bs=24 count=1 of=newbackup.ab - Append the modified content to the header:
openssl zlib -in newbackup.tar >> newbackup.ab - Restore the backup with the modified content:
adb restore newbackup.ab
Just like data backup, data restore needs user confirmation, please click on the button Restore my data to complete the restore process:
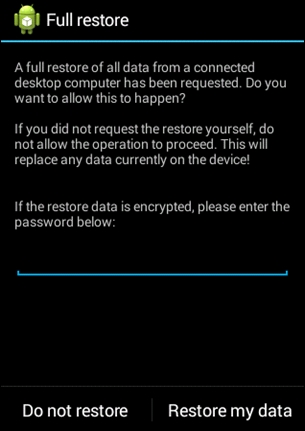
It's obvious now that an attacker with physical access to the device can do anything. In the coming few chapters we will also see that the presence of lock screens doesn't hinder an attacker much in accomplishing his goals.