Mobile Security
A Practitioner’s Perspective
S. Tully*; Y. Mohanraj† * Sydney, NSW, Australia
† Chennai, TN, India
Abstract
This chapter looks at some of the sociological aspects of the increase in the use of mobile devices as the world transforms rapidly in a move toward mobile ubiquity. It then describes the challenges surrounding mobile device security for practitioners, highlighting the key risks for individuals and the key concerns for organizations interacting with a digital native workforce who rely on these mobile devices. It offers insights on various threats, risks, issues, mitigations, and mobile security strategies, as well as sections covering privacy, forensics, and individual versus organizational impacts. Finally, it concludes with 10 suggested steps to secure mobile devices.
Keywords
Mobile device; Mobile security; Smartphone; Tablets; Privacy; Encryption; Forensics; Individuals; Organizations; Sociology
Acknowledgments
Our warmest thanks goes to Scott McIntyre for his devil’s advocacy and to Catherine Brown for her emerging technology and sociological insights; also to Dr Kim-Kwang Raymond Choo from the University of South Australia for his kind invitation to contribute a chapter.
1 Mobile Security
In this chapter, we look at how users and organizations interact with mobile devices, as well as the security that is needed to keep abreast of the rapid changes in mobile computing.
After discussing various issues, such as privacy, location and jurisdictional issues, threats, risks and mitigations, and individual versus organizational impacts, this chapter outlines steps to take to ensure that your mobile devices—and everything that’s on them—stays safe.
The world is transforming dramatically in a way that is having a significant impact on how people and enterprises operate (Soulodre, 2015). The telephone network has come a long way within the last century, from physical offices attended by technicians in telephone installation trucks to mobile devices and information available, anywhere, at any time.
Today, business is increasingly likely to be a mobile enterprise, conducted using devices that might not have even existed 5 years ago. This is affecting the technology, systems, and processes that are designed and built to support them. Work is no longer a place we “go,” instead it’s something we “do.”
Mobile devices and portable media1 add significant value to people and organizations through increased efficiency and productivity. However, their proliferation in the workplace is a serious and expanding threat to both security and privacy; that is, keeping corporate information secure and keeping certain data private.
Knowledge workers and the new generation of mobile-first and mobile-only masses are now the 21st century’s “digital native” workforce. Besides the corporate environment, the cell phone has become the adult's transitional object, replacing the toddler's teddy bear for comfort and a sense of belonging.2Toffler (1970) predicted the relationships between people and machines, including emotional relationships, in his book Future Shock back in 1970. Prof. H.D. Block at Cornell University pointed out that people often develop emotional attachments to the machines they use. He suggests that we shall have to give attention to the “ethical” questions arising from our treatment of “these mechanical objects of our affection and passion.” A serious inquiry into these issues is to be found in an article by Puccetti (1967) in The British Journal for the Philosophy of Science, 1967, pp. 39–51.3 Other research in this area includes work by Choi, who is writing a piece on the Emotional Attachment to Mobile Devices4 and further work by Cheever, Rosen, Carrier, and Chavez called Out of Sight is Not Out of Mind: The Impact of Restricting Wireless Mobile Device Use on Anxiety Levels Among Low, Moderate and High Users in Computers in Human Behaviour.5 The strength of this attachment to mobile devices was reiterated by Holden, who said “I want to be buried with a mobile phone, just in case I'm not dead.”6
These agents of change with digital attitudes and real-time expectations influence where, when, and how things are done. Their demands come from an “always-on” lifestyle with instant, on-demand expectations. Executives and employees are expecting, even demanding, access to their work resources through a variety of mobile devices. And, perhaps crucially, this expectation and demand is without time restrictions. It's not just a 9–5 solution, which has both positive as well as negative implications. The potential for abuse of employees by employers who provide this access must be taken into account.
Being connected has made us more efficient, but there is now the risk of reacting so quickly that we don’t give the same attention to data protection that we might have given just 5 years ago.7 Most people have not noticed—or simply ignored—the shift in responsibility. When data/information was managed by centralized IT departments, it was clearly someone else's role to protect it. Now that information is literally in the palm of your people’s hands, but people have not caught up with this shift in responsibility; they don't understand it and they don't manage it. Connected with this is the socio-psychological aspect of human nature and the inclination to trust. With people having access to data almost instantly, there is the temptation to keep personal emails, calendar items, notes, mobile banking credentials, and other useful data to get through day-to-day activities, often stored insecurely. Over time, this personal data can quickly build up, and if the mobile device were lost or stolen, it could leave an easy-to-compromise digital footprint of the user, particularly if it is left unmanaged and not cleaned up regularly. Additionally, by being so connected, users are increasingly vulnerable to cyber adversaries.8
1.1 Global Growth in Mobile Use
It is important to note just how long mobile security has been a real issue. This section provides a brief timeline that helps build a sense of how we got to where we are today.
Cabir, the first Trojan horse for smartphones, was detected in Aug. 2004.9 The Australian Communications and Media Authority demonstrated the growth and ubiquity of Australian mobile devices in their Communications Report 2011–12, which noted “the total number of mobile services in operation increased by three per cent to reach 30.2 million, approximately four mobile services to every three people in Australia.”10
Furthermore, online and mobile use in China shows 668 million people access the Internet as of Jun. 2015. Of that, 89% (594 million) access the Internet via smartphones. For context, this means the number of people using smart phones in China is equal to 25 times the population of Australia. Similar trends can be seen in Vietnam, where there are 128.3 million mobile phone accounts for a population of 90.7 million. Vietnam is seeing explosive growth in mobile Internet adoption, as the Vietnamese bypass fixed Internet uptake and moved straight to mobile, creating an environment of innovation.
The security and privacy challenges in this dynamic digital landscape is for enterprise agility to implement a mobile security strategy to keep up with the people connecting with the things that surround them. This is especially true for those mobile device users who struggle to get by from day to day securely, sustained by a kind of security passivity. This security passivity can be summed up by a Japanese phrase “Shikata ga-nai” which loosely translated means “It can’t be helped.”11
2 Principles
To minimize the risk of mobile device usage and to maximize the value associated with it, some high-level principles should be applied in order to provide a structure for safer mobile device use. While the guiding principles may not be exhaustive, they provide a reasonable basis for managing the security of mobile devices.
These mobile security principles can be broken into two broad categories: principles for mobile device end-users and principles for organizational mobile device management (MDM), including mobile application software developers.
For mobile device end-users, principles include:
• Accept the updates (unless it is a fake security update on Android, which is a common malware vector, so be warned!). Keep the operating system fully updated to the latest version available from the vendor. If the vendor has ceased supporting operating system updates on your device, which is a particular Android problem, then upgrade the device.
• Ensure software updates, in general, for all applications.
• Keep a clean machine by removing old, unused apps.
• Avoid questionable apps. Be aware of applications that want to access your data (e.g., by accessing your contacts) and consider using applications such as 1Password or other encrypted content managers to ensure that sensitive data is protected.
• Practice personal data management.
• Protect your personal information by storing the least amount of personal information as possible on devices. Android doesn’t give you a lot of control currently, but that may change over time, whereas iOS does give you that control.
• Cleaning up or removing personal information from devices so that you don’t leave data on the device if it is lost. This will avoid future users of the device finding information about you left on the device.
• Wipe the data on your mobile device before disposing of it. Also enable a remote wipe feature in case the mobile device is lost or stolen. Understand that using a remote wipe may include features that will delete stored data on your mobile device if a password is entered incorrectly after a certain number of times.
• Back up your data. Mobile devices are easy to backup, and users should make the most of this option.
• Stay safely behind bars. Ensure you do NOT jailbreak/root the device and ONLY install applications from the primary distribution points for the operating system (Apple Store, Google Play, and similar app stores).
• Use malware detection software, which predicts and stops mobile attacks, such as Lookout.
• Install privacy apps that explain all of the access to private data that installed apps require.
For organizational mobile device security, principles include:
• Embed security for mobile devices in corporate governance, risk management, and compliance (GRC) strategies.
• Establish security governance over mobile devices.
N.B. This step may not be necessary, but it is part of the risk-based discussion and GRC strategy that an organization should undertake. Organizations may decide NOT to impose governance over devices, and that is their prerogative. Enforcement comes at a price, and not all organizations are willing to pay that price.
• Perform regular mobile device software testing, such as checking runtime interpretation of code for errors.
• Perform regular mobile device security audits focused on applications and software that run on them. Of course, you are then left with the frustrating problem of “what can I do about it?” when the operating system is not something that most organizations can really customize in any way.
• One of the key areas to search for are device defaults; that is, what services are open, authentication defaults, and so on. This is less focused on smartphones and more on things like portable Wi-Fi/mobile hotspots.
For mobile application software developers, principles include:
• Building security and privacy into every phase of development.
• Ensuring sensitive data is protected in transit.
• Ensuring security by design and privacy by design by locking down the security and privacy settings of your mobile device app.
• Ensure source code review and application penetration testing.
Further useful information in this area can be found in ISACA’s Securing Mobile Devices Using COBIT® 5 for Information Security (See ISACA, n.d.).
3 Application Stores
Application stores, or app stores, refer to online stores for purchasing and downloading software applications and mobile apps for computers and mobile devices.
The term in most cases refers to Apple’s App Store, but it is also frequently used for similar online stores that sell mobile apps, including Amazon's Appstore for its Kindle and other Android-powered devices, the Android Market for Android devices, Google Play, Blackberry’s App World for Blackberry devices, and Nokia’s Ovi Store.
Official app stores tend to have stricter guidelines as to what sort of apps can be uploaded, as well as how they interact with the device and collect information about users and the device itself. Applications that grab your phone number, call history, GPS location, Wi-Fi password, and other data can be a concern. The point here is to start thinking, “Wow—that's scary. I don’t want someone to access THAT!”
Applications can sometimes contain viruses or malware that can steal any important information from the phone. Most official app stores have screening processes that detect malicious software and behavior embedded within applications, but these processes are not perfect and there have been instances of suspicious or malicious apps getting through screening and into general availability. Winn Schwartau, Chairman of MobileActiveDefense.com said, “App stores and mobile apps are the greatest hostile code and malware delivery mechanism ever created.”12
Recently, various reports have shown multiple exploits of app stores via exploiting flaws13 and zero-day exploits,14 as well as by installing malicious apps that bypass app store review processes,15 such as by sideloading, which means installing applications without using the official app store. The motivations for an end-user to sideload an application from a illegitimate source can be varied, such as empowering the user, allowing the use to fine-tune the app experience, allowing the ability to work offline, avoiding registration, or login to use the app, remove phoning-home code, or remove in-app advertising. The risk is that your phone is now more vulnerable to attacks from applications and that you accept all the responsibility that comes with downloading the app. It makes sense: you can’t hold the app store responsible for applications you downloaded elsewhere.
4 Approved Applications
Poor implementation of a legitimate application’s usage of device information and authentication credentials can thereby expose sensitive data to third parties. Some examples of this sensitive data include location, owner identification (e.g., name, number, and device ID), authentication credentials, and authorization tokens. Smartphone apps can give automatic access to near-field communications (NFC) payments, SMS, roaming data, premium rate phone calls, etc. Apps with privileged access to such application programming interfaces (APIs) can allow attackers to take advantage of this to abuse the user’s financial resources, with subsequent monetary impact. For example, if an API was able to access the PayPal account details of a user and subsequently use these details to make a purchase from a different device, it shows that the security consequences of mobile security aren’t limited to just the mobile device.
Data segregation is an approach whereby personal and corporate data are separated, allowing different controls to be applied to each. Although this is less important on corporate-owned devices used only for corporate work, it can be extremely useful in other ownership scenarios, such as personally owned devices which are also used for work.
Increasingly, mobile operating system vendors and third-party software vendors are implementing features to better support personally owned, mixed-use devices. The challenge with smartphones and tablets is different from that of laptops, as the owner of a smartphone or tablet is not likely to be running as an administrative user on their device. A current approach is “containerization,” where corporate data is contained within a single app that can enforce protections from other apps and from the user or attackers.
4.1 App Containerization
Containerization of mobile devices such as smartphones and tablets through the separation of personal applications and data from business applications and data is a control mechanism for either the individual or for the business.
App containerization involves segmenting mobile devices into personal and business regions or domains. If this is done with, for example, a bring your own device (BYOD) phone, it lets employees do whatever they want on their side of the border, while corporate IT retains control of the other.
Applications exist that can containerize complete work environments in a secure sandbox or wrap individual apps within a centrally managed container, such as Teopad, Good, and AirWatch. There are different approaches to containers as well, namely on a per-app basis or on entire groups of applications. Application sandboxes create a secure working environment on the mobile device that holds not only locally installed enterprise apps, but also app data and preferences. The runtime environment is protected from the personal home screen and associated apps and the experience is separate: a user is in either an organizational or personal workspace, as illustrated in Fig. 1. However, when app compartmentalization is implemented poorly, it’s actually a leading cause of people trying to work around it. People want the natural flow of information in native ways, which the mobile OS provides. Containers and compartmentalization create barriers that many try to work around, and containerized applications are often quite out of date in comparison to their public versions because of a lack in features and functionality. That gets to be really annoying! There is a security implication here as well; containerized apps may not be updated for security flaws/updates as quickly as public versions.
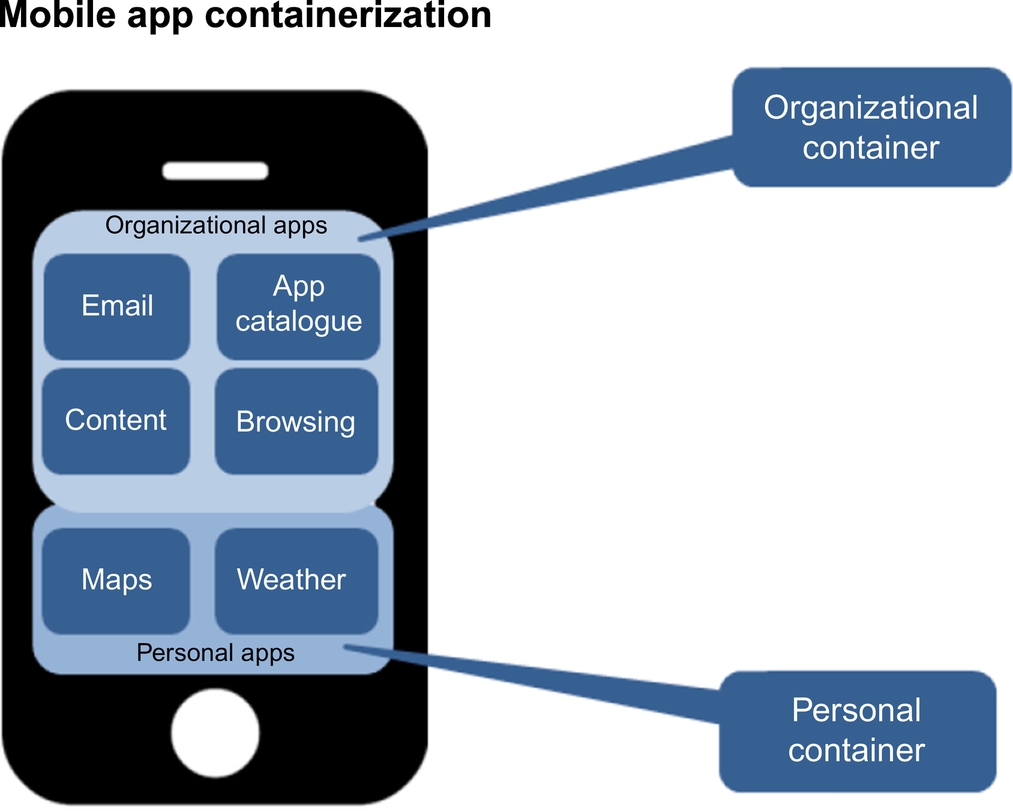
A business may want to remotely wipe business data in a business container or a containerized app after someone leaves an organization, for example, but doesn’t want to remotely wipe and destroy the unique and personal images that the device owner may have stored.
4.2 Software Watermarking
Software watermarking, which is a form of steganography, involves embedding a unique identifier within a piece of software.16 Watermarking provides a means to identify the owner of the software and/or the origin of the software and is something that a developer could do for creating enterprise apps. Although originally conceived to discourage software theft, the concept has the potential to be used for validating approved mobile applications. One advantage is that the hidden watermark can be extracted at a later date, by the use of a recognizer to validate the origin of the software. This also has useful applicability for mobile device forensics.
4.2.1 Online-Based Services (Accessible Via Mobile)
If it is possible for data from a mobile device to be emailed to an external account or uploaded to an online-based service such as Dropbox, then, inevitably, some or all control may be lost.
Attacks against online-based services have become increasingly prevalent, with inappropriate access through poor authentication controls, a lack of monitoring/logging, and unknown persons accessing online stored data. Insecure API and poor transport layer security (TLS) are a common man-in-the middle (MITM) target, as is token/credential hijacking. Mobile applications interact with APIs using well-known REST/Web Services or non-REST/Web Services proprietary protocols. Insecure implementation of APIs or services and not keeping the platform hardened/patched could allow attackers to compromise data on the mobile device when transferred to the platform, or to attack the platform through the mobile application. The importance of TLS to provide communication security should be considered as well.
Popular cloud storage services such as Dropbox and Google Drive can be manipulated and subsequently abused by malicious enterprises using phishing against data in a cloud account with poor authentication controls to prevent social engineering attacks. One well-publicized targeted attack involving data leakage of nude celebrity photos occurred recently and focused on user names, passwords, and security questions of user accounts.17
5 Identity Management Issues
One of the most challenging aspects of mobile information security is that of identity management. The ability to swiftly and accurately identify an individual and manage that identity is an absolute necessity in this space, yet without detailed planning and governance, various identity management issues arise as highlighted in the following section.
• Emergence of what you have (mobile device) being an identity rather than a factor of authentication. For example:
• your mobile phone is the identity in mobile payments
• your mobile phone is the identity to access the extended corporate website
• what you know PIN or password is still as used as an authentication factor
• Lack of federated identity at the operating system level due to tight integration with the application store is a common identity management issue. For example, can a user log in with an Apple ID on an Android device? If not, then the user has two identity credentials to manage.
• Collision of identities on a platform that was not designed for multiple identities. The following are different levels of identity at play in a mobile device:
• Mobile number-based identity (e.g., IMSI)
• OEM-supplied identity (e.g., Samsung Galaxy Apps)
• Application store-based identity (e.g., Apple iTunes, Google play)
• Social network-provided ID (LinkedIn, Facebook)
• Messaging services-based ID (Snapchat, WhatsApp)
• Corporate ID
• Personal Banking ID
• Payments-specific ID (e.g., PayPal)
• App-specific ID (the more apps you use, the greater the number of identities you have)
• How much personal information is stored within these respective identities and whose responsibility is it to protect them? Is it the responsibility of the person who stores it or the person that created it? Taking a WhatsApp identity as an example, one of the questions that needs to be considered in some detail is whose responsibility is it to protect my WhatsApp ID? The responsible parties could be:
• WhatsApp as the application author
• Google as the maker of the Android operating system
• Samsung as the OEM, who may have modified Google's Android for their specific device
• the individual who decided to use WhatsApp in the first place
• all of the above
• Data stolen from mobile devices by apps with privileged access as outlined previously, such as identity data and credit card details, can be sold by an attacker on encrypted “dark net” sites or hidden forums. The inconvenience caused to the initial user involves recreating identity credentials or replacing credit cards and verifying any suspect online payments made.
The Jericho Forum produced an informative and enlightening paper on Identity18 that distinguishes core identity, different personas, attributes, privacy, and trust.
The limiting of attributes in each persona minimizes the risk of other people connecting our different personas, which is a privacy-enhancing technique used to retain control over our personas and their related attributes. For example, the attributes assigned to your persona for a library or gym membership should be quite limited, whereas the attributes assigned to opening a bank account should be greater.
This is an especially effective technique to employ for users of mobile devices. In essence, it’s about identity compartmentalization that complements app compartmentalization mentioned previously.
One group addressing these challenges is the Global Identity Foundation,19 who is working on providing enhanced security and privacy for users and which is completely under their control. Human identities are fragmented, since we are different things in different communities, so to be able to control different personas is a step forward in an enabling an ecosystem of assured trust for digital transactions.
6 Privacy
6.1 The Need for Privacy
What are the issues relating to privacy, and why is there a need for privacy? Not everyone understands the privacy concept, but most understand the concept of secrets. Secrets are harder to keep in the information age. This is bad news for all who value their privacy! Long-lasting secrets, like the formula for Coca-Cola, are few and far between.
With few exceptions, our secrets are stored on computers, networks, and mobile devices, which may be vulnerable to hacking. Publishing someone's private information and communications is bad, because in a free and diverse society, people should have private space to think and act in ways that are different to how they think and act in public.
Users of mobile devices, particularly if they are using social media, need to be aware that they will be attractive targets to adversaries through their online presence. Users posting information about their travel plans, such as when someone is home and not home, is frequently used as a cue to perform breaking and entering. Involvement in high-profile or international events unknowingly provides people with information that can be used to elicit information from them or to tailor social engineering campaigns to compromise an organization’s network. Users should assume everything posted on social networking websites is permanent and can be viewed by your enemies, the government, your competitors, and so on.
To prevent being the target of a privacy-exposing campaign, users should:
• Carefully consider the type and amount of information posted.
• Restrict the amount of personal information posted.
• Consider limiting access to posted personal data; for example, using the “Friends Only” option for posting on Facebook.
• Be aware of and be willing to learn about the conditions stipulated in the permissions of apps before allowing access.
• Be aware of location sharing of personal information such as tagging locations in posts on social networking sites. Location services are often used by apps to provide directions or “check in” to your local store, coffee shop, or other locations and share that information on various social networks. Not all apps need this data to function, and the ones that do should clearly explain how your location data will be used.
• Make an informed decision regarding geotagging on your mobile device for the camera and other apps that do not require your current location. For example, be aware of the risks and consequences, especially if you are sharing an image with this data still intact and don't want to reveal your true location.
Many apps collect information about the user for marketing purposes, diagnostics, or as part of the service they provide. This could include information such as your contact list, your SMS messages (or other instant messages), your physical location, and potentially even your photographs and Wi-Fi password. This information may be stored or distributed to third parties by the app developer, as well as stolen or intercepted by unauthorized users. Consequently, it is important to read the user agreement and consider the information an app can access.
One of the greater issues for privacy relates to continuing consumer trust in the digital economy. In the span of a few short years, social networking on the Internet has become the platform for communication among many mobile device users using apps like Twitter, Instagram, Facebook, or WhatsApp. Just because people are much more public in the nature and extent of information they share online does not mean privacy is dead. Crompton (2015), Australia’s former Privacy Commissioner from 1999 to 2004, covers this in his book, Privacy Incorporated: The Business of Trust in the Digital World.
New apps, computing technologies, and channels are facilitating business processes that involve instantaneous streaming and linking of data from many networked sources. If organizations are going to use personal information in innovative ways, there is the question of who bears the risk when things go wrong. Organizations using personal data in this way contribute to people’s sense of being out of control and the sense that things are going wrong and need to be fixed.
Individuals will be confident and trusting where they:
• Feel in control and secure
• Find that use of personal information is based on expectations
• Are never surprised
• Receive quick, effective resolution of their issues
6.2 Privacy Implications
There are multiple implications, including legal ones, extending to the privacy of personal information held on mobile devices.
Some privacy implications include:
• Access to personal or corporate email.
• Access to SMS.
• Access to images.
• Access to network (personal, wireless, corporate, VPN).
• Access to corporate apps and data.
• Ability to send SMS to premium rated services (e.g., “Toll Fraud”).
• Privacy threats may be caused by applications that are not necessarily malicious, but gather or use more sensitive information than is necessary to perform their function.
• Organizations that let employees use personal mobile devices should consider the BYOD privacy issues and other legal concerns that may arise.
• Use of location-based services technology such as a global positioning system (GPS).
• Outsourcing of MDM; that is, where staff from the outsourcer may act in an unethical way regarding access to privacy-related information.
• Legal compliance with privacy laws. This is often jurisdictionally bound, but for a multinational corporation, it can present some cross-border jurisdiction issues.
• The Internet never forgets. It's not just what is seen at the time, but also what is archived and recorded by countless services. Just because you delete a tweet doesn't mean it can't be used against you!
With regard to jurisdiction based upon territoriality, even though individuals using IT systems have a specific physical location, the location of mobile devices can change during a usage session. For instance, a person with a mobile computing device (e.g., a tablet or smartphone) can initiate several database updates or queries for processing by a cloud-based service. As those updates and queries take place, the user may move to a different location. Any state from which the individual has operated enjoys jurisdiction because the individual and the devices involved were located on its territory when so used.
Furthermore, even with technology such as mobile cloud computing, the devices from which the human user is initiating requests can be geolocated; software services and applications may track the geocoordinates of the computing devices (e.g., Wi-Fi connection location or device GPS location). It is possible under certain circumstances for someone who does not wish to be tracked to spoof the geocoordinates advertised by their computing device. It is also possible that user location will not be made available by the infrastructure or service provider, or by the application or device itself. Actual physical presence is required and is sufficient for jurisdiction based on territoriality; spoofed presence does not suffice.20
Location is an important piece of personal information that should be managed. This personal information could be revealed by tagging locations in posts on a social networking site that advertises your current location or revealed by posts or in images through geotagging.
Organizations should have policies in place to manage mobile devices, including those owned by their employees, that are used in the workplace. Organizations should have the ability to access, recover, wipe, or protect data on mobile devices (e.g., when an employee ceases employment or a device is lost).
Mobile applications should ensure compliance with relevant data privacy laws, such as the Australian Privacy Principles.21 In the European Union, it is mandatory to obtain user consent for the collection of personally identifiable information (PII).22
As mobile apps increase in popularity, many of them are seeking access to large amounts of personal information without adequately explaining how that information is being used. In 2014, the second annual Global Privacy Enforcement Network (GPEN) Privacy Sweep of more than 1200 mobile apps found that almost 70% of apps looked at failed to provide the user with a privacy policy or terms and conditions that addressed privacy prior to the app being downloaded.23
7 Vulnerabilities
Despite all the security improvements and architectural changes that have occurred within mobile applications, some categories of “classic” vulnerabilities show no sign of diminishing. The lesson is that we haven't learned our lesson. Despite many security flaws having been known about for decades, we're continuing to repeat those flaws in new platforms without having implemented the established fixes and improvements that have also been known about for some time. These include defects in business logic, failure to properly apply access controls, and other design issues. Another important point is that 20- to 30-year-old problems are not magically going away because users have gone mobile. If anything, they have become more prevalent due to accessibility to coding and lack of formalized security training and education. Even in a world of bolted-together application components and everything-as-a-service, these timeless issues are likely to remain widespread.
Vulnerabilities are commonly associated with applications that are installed on mobile devices. However, it is important to recognize that vulnerabilities can be exploited at all levels in the mobile device stack.
8 Threats
Protecting mobile device data against today’s threats is crucial (Whitlock et al., 2014). The recent growth in the use of mobile devices (smart phone, tablets, etc.) has greatly outpaced the ability to control the location and protection of information. The figures below explain why:
• In Australia at the end of Jun. 2014, there were more than 12.4 million Internet subscribers and almost 20.6 million subscribers to mobile services with an Internet connection.24 Cybercrime affected 5 million Australians in 2013 and cost $1.06 billion.25 The 2013 Norton Report from Symantec (2013) revealed that 57% of Australian mobile device users were not aware of security options for mobile devices, leaving their devices susceptible to attack.
• The average cost of a malware incident is $56,000 for a small-medium size business (SMB) and $649,000 for a large enterprise.26
• It is estimated 12,000 laptops will be stolen this week worldwide.
• Malware has increased year-over-year by 77%.
Given the sheer size of the figures above, it is clear that for both individuals and organizations, protecting mobile device data is important.
Market analysts predicted that smartphones would outnumber PCs by 2013 and that they would be the most common device for accessing the Internet. Today, there are 2.6 billion smartphone subscriptions globally27 and are expected to reach 6.1 billion by 2020. Given that specific mobile threats exist, mobile threat testing should be conducted before a mobile app goes live.
As with most changes, these figures have included some new attacks and variations on existing attacks.
As Pete Singer and Allan Friedman point out in their book Cybersecurity and Cyberwar, What Everyone Needs To Know(Singer and Friedman, 2014), there are three basic factors needed to evaluate a threat: “The feasibility of adversaries being able to identify and exploit your vulnerabilities, the effect that would happen if they were able to take advantage of these vulnerabilities, and, finally, the likelihood that they will, in fact, be willing to do so.”
Like viruses and spyware that can compromise your PC, there are a variety of security threats that can affect mobile devices. These mobile threats and risks can be divided into several categories: application-based, web-based, network-based, physical, overseas travel, and unintentional disclosure of data.
8.1 Application-Based Threats
Downloadable or preinstalled applications can present many types of security issues for mobile devices. Preinstalled applications are especially a problem in Android, where bloatware often includes insecure applications which present immediate "out-of-the-box" security and privacy risks. “Malicious apps” may look fine on a download site, but they are designed to do all sorts of things, such as capture passwords, retrieve information, collect personal information about the end-user without their knowledge, commit fraud, collect information for targeted advertising, or facilitate mischief (e.g., exploit a machine to become part of a botnet). Even some legitimate software can be exploited for fraudulent purposes. Application-based threats generally fit into one or more of the following categories:
8.1.1 Malware
• Malware is software that performs malicious actions while installed on your phone. Without your knowledge, malware can make charges to your phone bill, send unsolicited messages to your contact list, or give an attacker control over your device.
8.1.2 Electronic Tracking (Spyware or Adware)
• Spyware is designed to collect or use private data without your knowledge or approval. Data commonly targeted by spyware includes phone call history, text messages, user location, browser history, contact list, email, and private photos. This stolen information could be used for identity theft or financial fraud.
• Adware is typically installed unwittingly by the end-user and is a common component of free software such as file sharing applications. It collects information about the user that can be used for targeted advertisements in the form of banners, pop-ups, and privacy invasion through the tracking of cookies to correlate online behavior to identify a specific individual, which aids in targeted attacks.
8.1.3 Vulnerable Applications
• Vulnerable applications are apps that contain flaws that can be exploited for malicious purposes. Such vulnerabilities allow an attacker to access sensitive information, perform undesirable actions, stop a service from functioning correctly, or download apps to your device without your knowledge.
• Cybersecurity experts are expecting mobile payment security threats to grow over the next 12 months. Some 87% of the 900 experts interviewed for the industry body’s 2015 Mobile Payment Security Study28 claimed data breaches would increase over the coming year. In fact, just 23% said they thought mobile payments keep personal information safe, while 47 claimed mobile payments are definitely not secure. Interestingly, it seems that despite these security concerns, adoption of mobile payment is unlikely to be affected significantly. Users should consider how much sensitive information they store on a mobile device when making mobile payments using contactless enabled payment mechanisms. Some malware recently encountered includes Bitcoin-mining malware that targets Android devices.
8.1.4 Ransomware
• Another development is file-hting ransomware targeting mobile devices. Examples include Simplocker, CryptoLocker, and since Feb. 2016, Locky. Users will not be able to uninstall the malicious app by traditional uninstall means as one would normally do because the system or even the antivirus (AV) user interface is always “covered” by the malware’s user interface.
To protect against these application-based threats, users should consider installing malware, spyware, and adware detection software on their mobile devices.
8.2 Internet-Based Threats
Since mobile devices are almost constantly connected to the Internet and frequently used to access Internet-based services, web-based threats pose persistent issues for mobile devices. Groups such as the Mobile Web Initiative’s29 mission includes ensuring that the web is available on as many kind of devices as possible. This includes ongoing work around mobile web best practices and mobile web application best practices. As Berners-Lee said “The Mobile Web Initiative is important. Information must be made seamlessly available on any device.”30
Internet-based threats generally fit into one or more of the following categories:
8.2.1 Denial of Service (DoS)/Distributed Denial of Service (DDoS) Threats
• While actual DoS and DDoS attacks capture headlines, it is imperative that organizations also fully understand the impact of inadvertent, harmless outages for mobile devices. Up to now, most DoS attacks have been an infrequent and short-lived annoyance, one that most organizations are relatively well equipped to deal with. If the core of the Internet is impacted by a malicious attack or inadvertent outage, we all suffer because the Internet has become our lifeblood in terms of how we work, live, play, and learn. From a mobile device perspective, the focus may revolve around users' own networks and data, network, and data services that organizations provide to their customers, or a combination of both.
8.2.2 Bots
• Bots are one of the most sophisticated and popular types of cybercrime today. They allow hackers to take control of many mobile devices or computers at a time and turn them into "zombies,” which operate as part of a powerful "botnet" to spread viruses, generate spam, and commit other types of online crime and fraud. Bots sneak onto a person’s device in many ways. Bots often spread themselves across the Internet by searching for vulnerable, unprotected devices to infect. When they find an exposed device, they quickly infect it and then report back to their master. Their goal is to stay hidden until they are instructed to carry out a task.
The growth of mobile and other Internet-connected devices is allowing the bots to evolve. We are starting to see devices hijacked and turned into DDoS bots, creating a blended threat with the DoS/DDoS threat mentioned above, thereby increasing the barrier to detect and prevent DoS attempts.
8.2.3 Advanced Persistent Threats (APTs)
• Smartphones, tablets, and other mobile devices are getting hit by highly targeted attacks known as APTs intended to steal sensitive data. Mobile devices used in organizations are often the entry point for an APT-style attack aimed at specific individuals to gain access to corporate information. The types of technologies organizations need to invest in to protect against these threats include application control, data loss prevention, MDM, and device control.
8.2.4 Phishing Scams
• Phishing scams are about providing data of value to criminals. That can include usernames, passwords, other personally identifying information (PII), financial data, and more. In most cases, it's the lack of ability to validate the source of a message (no way to view full headers in email) and difficulty in viewing full links on the small form factor of a mobile device. Plus, the on-over hovering is tough to replicate on mobile devices.
8.2.5 Social Engineering
• Social engineering threats for mobile devices can occur through mobile malicious advertising (or malvertising), which is the promotion of malicious apps that look like legitimate apps or apps that claim to be for “security.” As Lacey points out in his book, social engineering can be much safer and easier when the attacker is operating across a network.31
Unlike ads displayed inside PC web browsers, ads displayed within mobile apps are delivered by code that is part of the applications themselves. This could represent a backdoor into the device. There are examples of malware from the Google Play store, and Trojanised Android apps through third-party stores, some even installing and executing adware on the device.
8.2.6 Drive-By Downloads
• Drive-by downloads prompt for an application package to be installed, usually under the guise of a security certificate update, but sometimes something as straightforward as a MMS message. For example, the Stagefright Android hack opened the possibility of silent execution of malicious code. The exploit happened when a hacker sent an MMS message containing a video that included malware code. What’s most alarming about it is that the victim did not have to open the message or watch the video in order to activate it. As such, a hacker could gain control of the device before the victim even knew about the text message, and even if the phone owner found the message right away, there was nothing to be done to prevent the malware from taking over the device. The hacker would have access to all data and the ability to copy or delete it, as well as have access to the microphone, the camera and all pictures on the device, and Bluetooth.
8.2.7 Browser Exploits
• Browser exploits take advantage of vulnerabilities in your mobile web browser or software launched by the browser such as a Flash player, PDF reader, or image viewer. Simply by visiting an unsafe web page, you can trigger a browser exploit that can install malware or perform other actions on your device.
8.3 Network Threats
Avoid or limit the use of open, public 802.11 wireless networks. Additionally, ensure that you are using the later, stricter security protocols such as WPA2 and avoid the earlier flawed protocols such as WEP and WPA. Where possible, use a virtual private network (VPN) to connect to your organization’s secure network. However, a poor VPN technology that doesn’t use “pinning” or a similar technology to validate an encrypted authentication session may not do you any good if you’re using a fully insecure, crypto-less Wi-Fi network; as cyber adversaries may be able to access your username, password, or passphrase, as well as other private information by a MITM attack tracking your keystrokes. Mobile devices typically support cellular networks, as well as local wireless networks (Wi-Fi) and Bluetooth. Each of these types of networks can host different classes of threats:
8.3.1 Network Exploits
• Network exploits take advantage of flaws in the mobile operating system or other software that operates on local or cellular networks, such as an International Mobile Subscriber Identity (IMSI) catcher. Once connected, they can intercept your data connections and find a way to inject malicious software on your phone without your knowledge.
8.3.2 Electronic Eavesdropping Such as Wi-Fi Sniffing and Bluetooth/Bluejacking
• Wi-Fi sniffing intercepts data as it is traveling through the air between the device and the Wi-Fi access point. Many applications do not use proper security measures, sending unencrypted data across the network that can be easily read by someone who is grabbing data as it travels. Shared encryption is just as bad. Public sites such as coffee shops, restaurants, and bookstores may have WPA2, but it is likely that anyone with the password can decrypt your packets.
• Bluetooth threats are serious. People who leave BT on all the time leave themselves vulnerable to pairing from nefarious devices and the uploading of spyware.
Bluejacking is an older-style attack where someone will use another person’s Bluetooth-enabled device. Bluejacking refers to sending of unsolicited data (vCards, etc.) to open Bluetooth listeners in the area. It has more recently been used for marketing, but many more modern smartphones are less vulnerable to Bluetooth stack exploits. This can lead to phishing attempts and the spread of malware or viruses.
8.3.3 Location Detection
• Location tracking, through user-controlled location push apps, where someone checks in and intentionally shares their location. Apps such as Facebook, Foursquare, Swarm, Tinder, Twitter, Uber, and similar hold and share information about where you are exactly at what moment, not to mention a history of where you were.
• Location detection, through bypassing enhanced LTE (4G) security measures with IMSI attacks, also known as IMSI catchers. The thought of a cyber adversary triangulating someone's mobile device to determine their location is a threat that could be used for many purposes such as criminals targeting high-profile individuals and professionals. Using an IMSI catcher to track someone, who has not intentionally used user-controlled location sharing apps, is quite a different threat than the threat above.
8.3.4 Hotel or Conference Facility Networks
• Savvy cyber intruders have been known to exploit hotel or conference facility networks to gain access to mobile devices. Avoid communicating any sensitive information on devices that are not connected to a secure network. Where possible, try to avoid using hotel Internet kiosks or Internet cafes to send or receive important data. Do not connect to open, public Wi-Fi networks for business purposes. Only wireless communications that are needed and can be secured should be enabled.
8.4 Physical Threats
Mobile devices are small, valuable, and we carry them everywhere with us, so their physical security is also an important consideration.
8.4.1 Stolen Data Due to Loss, Theft, or Disposal of Devices
• Lost or stolen mobile devices are a significant risk to the security and privacy of data. The mobile device is valuable not only because the hardware itself can be resold to third parties on the black market, but more importantly because of the sensitive personal and corporate data it may contain. Mobile/smartphone/tablet data leakage is a possible consequence, which may have legal implications, data breach implications, and so on.
• Data can also be stolen via attacks on decommissioned mobiles, smartphones, or tablets. In these cases, the attacker has the potential to recover the information over a longer time frame, as the previous owner or user of the device is typically no longer expecting an attempt to exploit their information. Selling a used device on eBay or Gumtree, for example, without a proper device wipe that has been verified, can leave personal information on the device that may be recovered by the next owner and used for attacks against the previous owner. Indeed, it's been shown that many Android/MDM device wipes don't actually securely wipe data from devices. iOS does, but this means there's a continued risk of data access by third parties if the wipe has not been properly validated.
8.4.2 Unauthorized Access
• Many smartphone users do not have a password lock on their phones when they turn them on or wake them from sleep mode. That widespread lack of security makes any mobile device a tempting target for unauthorized access, which can subsequently lead to data leakage and system infection. Some of the consequences of this include, in iOS, the passphrase or PIN is used to encrypt the filesystem, and having a password permits advanced features such as automatic-wipe on bad password entries.
8.4.3 Gifting
• It is common to receive USB thumb drives as a gift when attending industry events. The area of concern is people with malicious intent may use these opportunities to gift electronic devices that are preloaded with malicious software. A gift of a mobile phone or tablet, rather than a mouse with a microphone powered by USB, is more an area of concern as they have very different threat profiles. When these devices are used or connected to an organization’s network or personal device, malicious software may install and run.
8.5 Travel Threats
• If traveling with an electronic device while at high-profile or international events, consider that the compromise of a company-issued mobile device could have an impact on your organization, its information, and its reputation. In most countries, you should have no expectation of privacy in hotels, Internet cafes, offices, or public places. The implications of any compromise are different depending on the use of the device; for example, corporate devices have different implications than personal devices.
8.6 Unintentional Disclosure of Data Threats
• Poorly implemented applications usage of device information and authentication credentials by a developer can expose sensitive data to third parties, including location, owner identification (such as name, number, and device ID), authentication credentials, and authorization tokens. Smartphone apps can give automatic access to NFC payments, premium rate phone calls, roaming data, SMS, etc. Apps with privileged access to such APIs can allow cyber adversaries to take advantage of this, among other things, to abuse the user’s financial resources with subsequent financial impact.
What should be generally evident is that outside of malicious insiders, configuration management failure, or DoS attacks, the likelihood of accomplishing a compromise requires very few steps and little complexity.
9 Risks
A lot of security terms are being used in an improperly interchangeable way. Three security terms, in particular—risk, threat, and vulnerability—are explained here for clarity. The term "risk" refers to the likelihood of being targeted by a given attack, of an attack being successful, and general exposure to a given threat. The likelihood of the risk materializing also needs to be taken into consideration. Likelihood can be expressed in terms such as Rare, Unlikely, Possible, Likely, and Almost Certain, with each category increasing in magnitude of likelihood. The term "threat" refers to the source and means of a particular type of attack. The term "vulnerability" refers to the security flaws in a system that allows an attack to be successful.
There is a common formula, R = TV (or Risk = Threat × Vulnerability). As an example, using this formula to address risk for illustrative purposes, if there is a vulnerability but no threat, then there is no risk; alternatively, if there is a threat but no vulnerability, there is also no risk. If there is both threat and a vulnerability and the likelihood of the risk materializing is likely or almost certain, then the risk is high.
As information technology advances, more powerful and diverse functionality can be found in smartphones, tablets, and other types of mobile devices. While tailoring guidance may support allocating particular security controls to a specific technology or device whilst leaving out other controls, any residual risk associated with the absence of those missing controls must be addressed in risk assessments to adequately protect organizational operations and assets, individuals, and other organizations.
Despite offering much of the functionality of full computers, smartphones, and tablets do not have the same control models or security controls as computers; therefore, attempting to apply a computer’s security policies and procedures to such devices will not work. Mobile devices have their own security models, and some may even be more secure than laptops. For example, iOS having full filesystem encryption for several years is way ahead of most corporate laptops and their endpoint encryption. MDM technology often provides far greater granularity of controls, as well as flexibility, than standard PC antimalware. Plus, mobile devices try to make more use of sandboxing technologies by default, something that is still rare at the desktop level (other than OS X and their app store sandboxes). Even within each class of device, there is immense variety; iPhones have a different risk profile than Android phones and, to further complicate the matter, different versions of the same device can have different risk profiles.
The threat and attack vectors for mobile devices are often composed of overlapping versions of attacks aimed at other endpoint devices, mixed with significantly different motivations and goals by the attackers. For example, one attack vector might be social engineering or phishing to gain the identity or credentials to a mobile phone, which can be used by someone else to access the phone as if they were the phone’s owner, with the intent to extract other information (e.g., banking credentials stored on the mobile phone) in order to obtain a financial reward at a later time.
A number of lists exist that cover the risks for mobile devices; each has a slightly different focus and identifies different risks. Various organizations like ENISA,32 NIST,33 the Open Web Application Security Project (OWASP),34 and Veracode35 all publish mobile risk lists. However, it is wise to avoid checklist-based security models only. Mobile risk is a complex field and there are many ways of evaluating the risk; therefore determining what is best and most appropriate for individuals and organizations may take some shopping around of the various lists that have been highlighted above and that exist elsewhere.
Instead, the goal of understanding mobile risk should be to focus on how an organization or an individual can identify the security gaps they have regarding threats, as well as the real-world problems faced in large numbers every day, which will translate to their risk profile. Consequently, there should be more awareness of risk points, rather than specific steps to take. There are actually some very secure ways to store incredibly sensitive data on a mobile device, which is something that is improving all the time.
10 Mobile Security Strategy for Organizations that Develop Mobile Applications
A typical company isn't going to do code review or developer training since they're not developing apps. However, for any organization that develops mobile applications, a mobile security strategy should be developed prior to any actual corporate mobile access deployment. The items listed below provide a high-level framework of key areas for consideration:
10.1 Architecture
The architecture should be flexible and robust enough to support devices, apps, and any back-end infrastructure and associated networks. The mobility revolution puts incredible power in the hands of the end-user, but that power depends on-access to back-end information systems. This means that for the existing systems, a new mobile application architecture needs to be built around them.
10.2 Basic Device Management
Where the organization issues mobile devices, the devices should be exclusively used for work, and no work at all should be allowed on personal devices.
10.3 Secure Software Development Life Cycles (SDLC)
Mobile apps should be subject to regular source code reviews throughout the secure software development lifecycle to detect and remove any code vulnerabilities as early and as often as possible.
10.4 Data Validation
Develop and enforce sound app security processes to prevent unauthorized code manipulation.
10.4.1 Developer Training
If developing mobile apps, developers should undertake mobile security awareness training.
Code analysis through a combined approach of static and automated software analysis and expert review by trained professionals. The network-centric position of mobile application development requires specialized understanding and expertise.
10.4.2 Session Management
Implement appropriate session management as the form factor for mobile often means applications use long-lasting tokens for authentication/authorization, as well as session management.
10.4.3 Cryptography
Minimum cryptography settings for mobile devices should be defined and enforced.
Make sure that device encryption is enabled on the device. While some device manufacturers enable encryption by default, others require that encryption is enabled in the device settings. If the device is owned by an individual, then individual device encryption should be used. If the device is owned and managed by an organization, then enterprise encryption is recommended.
10.4.4 Data Confidentiality
Consider what the default data confidentiality setting should be for mobile device apps.
10.4.5 Environmental and Biometric Sensors
Environmental and biometric sensors in the device (such as acceleration, ambient temperature, fingerprint or iris scan, geolocation, humidity, motion, orientation, proximity, sound, video/still image capture, etc.) should comply with the organization's data capture policies, and their use should be selectively controlled by MDM.
10.4.6 App Penetration Testing
Mobile apps should be subject to a multilevel approach. Test the application to ensure it complies with policies and best practices, but since it is a mobile app, also test the network functionality and any APIs or servers the application may connect to. Furthermore, the mobile apps should be subject to application penetration testing before being loaded to an app store and before going live.
10.4.7 Handle Identity Management
User Authentication
Require confirmation of the user's identity as described in a corporate directory service before giving access to secured data or software.
Two-factor authentication is recommended for confidential data, such as a user name/password combination plus a successfully answered challenge question or positive fingerprint identification.
N.B. It’s worth calling out the three forms of authentication in general use:
• Single-factor authentication (e.g., password or PIN).
• Multifactor authentication (e.g., single-factor plus a software- or hardware-generated token code, or a smart card).
• Multistep authentication (e.g., single-factor plus a code sent to the user out-of-band).
Usually, the second step in multistep authentication involves the user receiving a code via SMS or an app such as Duo and entering it alongside (or after) their PIN/password. The phone could be considered as “something you have,” thus qualifying this as two-factor authentication. However, the code that is actually used, as well as the credentials used to access the account/device which receives the code, in the second step is still a "something you know.”
Two-factor authentication refers specifically and exclusively to authentication mechanisms where the two authentication elements fall under different categories with respect to “something you know,” “something you have,” and “something you are.”
An example of “something you know” is a password. This is the most common kind of authentication used for humans. We use passwords every day to access our systems. Unfortunately, something that you know can become something you just forgot. And if you write it down, other people might find it. An example of “something you have” is a smart card. This form of authentication removes the problem of forgetting something you know, but some object now must be accessible by you any time you want to be authenticated. Such an object might be stolen and then become something the attacker has. An example of “something you are” is a fingerprint, which is something intrinsic to the user being authenticated. After all, it's much harder to lose a fingerprint than a wallet.
Multistep authentication that requires two physical keys, two passwords, or two forms of biometric identification is not two-factor, but the two steps are still valuable.
Device Authentication
Confirm the unique identity of the physical device; it must meet security and configuration requirements, independent of any of its users.
Device Access Control
Protect physical access to the device by requiring successful recognition of a policy-defined password, pattern swipe, biometric scan, voice, or facial recognition.
10.4.8 Bring Your Own Device (BYOD)
If BYOD is allowed, organizations should consider limiting users to certain types of devices and not others in order to support a limited fleet of devices, rather than a vast array of different devices that will consume a significant amount of time, effort, and support resources.
10.4.9 Mobile Device Management
A well-thought-out MDM strategy is a key ingredient for any successful mobility deployment.
Ideally, the organization’s IT section should be at least aware of every smartphone and tablet used in an organization, from activation to retirement. Accomplishing this requires a cohesive plan for MDM. It is advised that assets are defined and how mobile apps use these assets.
Include capability for over-the-air device wipe (i.e., erase all applications and data on the device), device lock (i.e., block device access), and remote device configuration.
10.4.10 Mobile Application Management
Decide on relevant acceptable use policies to help set expectations. Make sure employees are clear on which applications are blacklisted and which they’re allowed to access.
Consider an enterprise app store, which provides a central online location for distributing, downloading, and tracking policy-compliant mobile apps for use by employees.
Use mobile application management (MAM) tools to transparently install and configure business or security apps, especially if you allow BYOD; you can’t always count on employees to do it correctly on their own.
Establish a way to track app downloads and ongoing usage, monitor to detect outdated or disabled apps, and enforce the removal of blacklisted apps.
10.4.11 Decommissioning
A process should be in place to decommission legacy or end-of-life mobile devices to avoid leaving vulnerable devices in use. This will help reduce the technical debt of the organization and reduce the attack surface.
10.4.12 Auditing
Regular auditing should be carried out to ensure the strategy is effective and that no gaps have been introduced into the organization.
11 Mitigations
With the increased penetration of mobile devices into the enterprise, the need for mobile device security has also grown. This section aims to show users how to do it correctly and see some of the wins possible. Each individual and/or organization needs to independently assess the risks that are salient for their use cases and environment and consider mitigations as appropriate.
Some mitigations that will assist individuals in addressing mobile device security issues include:
• Maintain up-to-date software through normal lifecycle management
• Ensure strong passphrases are used, where possible. A passphrase should never be written down and stored with the device.
• Sync or back up your mobile device to avoid the risk of lost/stolen devices, as well as ensuring that it is part of an overall resilience strategy for the individual.
• Educate yourself on best practices regarding mobile devices. There are a lot of bad ideas and bad suggestions out there, so verifying the advice you read is a fundamental step. Use as many of the best practices as practically possible to ensure you are not relying on a single control to protect yourself.
• Limit personal attributes stored on the device.
• Review privacy settings.
• Restrict apps and resources, such as denying access to specific device features or data sources on iOS for camera, browser, Google play, YouTube, music, and photo-sharing apps such as Instagram and Snapchat, etc. N.B. On Android, there are fewer ways to restrict apps and resources and to limit what these applications can do.
• Disable your device’s ability to install apps from sources outside of the standard app stores, such as Google Play, and double check the developer of the app you want to download and be very meticulous of the app reviews to verify any apps’ legitimacy.
• Configure device security such as encryption of data at rest.
• Overall device and account hygiene is important, so delete any social media accounts that you no longer use as the terms and conditions may change.
• Disable Bluetooth and wireless capabilities and the ability to “auto-join” a network if possible. This will prevent your device from inadvertently connecting to untrusted networks.
• If wireless capabilities are required, ensure the use of the most secure wireless authentication that your device can support, rather than using older, less secure protocols. For example, use WPA2 for wireless authentication.
• Disable premium calls and in-app purchases.
• Use a search engine to research your digital shadow to see if unexpected content about you is available online that may have originated from a mobile device and manage what is sent digitally. N.B. This activity is not trivial to accomplish and may involve changing the settings for various apps to restrict content, as well as following up with web site owners to remove unexpected and unwanted content.
• Only attach your mobile device to a trusted computer. In some cases, by inserting your devices into an unknown computer, you are exposing your mobile devices to unknown risks, and great care should be taken before doing so. Attaching your mobile device to an untrusted computer is not just a malware concern, but also a rooting/jailbreaking one, as physical access is often required for many of these exploits. You also have to consider data access such as backups and replication in order to protect your data.
• When charging mobile devices, you should only use a trusted computer to connect to the device charger, or go directly into the wall. You can also use a USB charger which removes the data pins and only provides charging pins.
In addition to the above mitigations for individuals, some further mitigations will assist organizations in addressing mobile device security issues.
Mobile device mitigations that are of specific focus for organizations include:
• Whitelist specific applications (or blacklist applications as a second preference) similar to the way firewalls work, where it is best by default to block all and allow only known good sites rather than by default to allow all and block only known bad sites.
• Educate your users on best practices regarding mobile devices.
• Creating a balanced approach for corporate and employee-owned phones, which respects the needs of both sides. If the devices are owned by the employees, there are many restrictions about what an employer can and cannot do. Location tracking, for example, may contravene the workplace surveillance act. It is also a privacy invasion.
• When connecting to enterprise resources, only connect through secure technologies, such as corporate-secured Wi-Fi and VPN services.
• Enforce security policies to protect corporate data.
• Enforce secure BYOD policies if you allow staff to use their devices inside the network.
• Keep highly sensitive organizational data off mobile devices, or as a secondary measure, identify and protect sensitive organizational data on the mobile device.
• Disallow removable media, such as SD cards, in corporate mobile devices by logging the devices in a mobile device inventory solution, then blocking unwanted memory cards. For example, a USB card may be allowed by the policy, while an SD card may be blocked.
• Block attachment execution or downloading to media by blocking unwanted memory cards as above.
• Detect and prevent use of jailbroken or rooted devices by maintaining baseline device information, through both MDM and MAM solutions, managed by the organization.
• Internal segregation controls on what access mobile devices have inside the network, for example, VLAN separation or network filtering.
• Expedite handling of secure lost, stolen, or retired smartphones through full and selective wipe.
• Provide rogue app protection, as well as inventories of installed apps.
• Ensure secure distribution/provisioning of mobile applications.
• Define and enforce allowed device types, operating systems, and patch levels.
• Keep back-end APIs (services) and platforms (servers) secure by implementing, for example, the latest TLS to provide communication security, the right ciphers, DDoS protection, and regular security assessments.
• Secure data interaction with third-party applications and services.
• Comply with the requirements of the Privacy Act in relation to the concept of consent. For example, pay specific attention to the collection and storage of consent that has been given by a user for the collection and use of that user’s data.
In addressing the mitigations, it should be recognized that there are shared/overlapping concerns for individuals and organizations. With the increased use of BYOD policies, there is a trend to connect these two worlds anyway, which means there is overlap that blurs the distinction between the two.
11.1 Exploit Mitigation
Exploit mitigation technologies attempt to prevent the abuse of vulnerabilities. They typically achieve this by making the execution of unauthorized code difficult or impossible while not affecting legitimate programs such as address space layout randomization (ASLR) and similar techniques.
Recent versions of smartphone and tablet operating systems have seen significant improvements in exploit mitigation technologies. Vendors are strongly motivated to implement and develop such technologies, not only because they can help to protect users, but they can also make jailbreaking less likely, as jailbreaks rely on abuse of security vulnerabilities.
N.B. There is very little that an organization or an individual can do about vendor-provided exploit mitigation technologies—short of ensuring that your platform is updated to the most recent version of hardware and software available. You can’t enable these technologies yourself (the vendor has to do it for you), and you need to procure the software/hardware that is compatible.
11.2 Travel Mitigation
For corporate-issued devices, prior to departure, consult your IT security team. They can confirm that your device’s configuration is correct and that all updates, patches, encryption, and AV software have been installed and baseline the device prior to departure and again on return to look for any signs of compromise.
Remove all nonessential data from the device. In particular, reconsider the need to take sensitive information overseas.
Maintain physical control over mobile devices (whether they are your own or company-issued), not only to minimize the risk of theft or loss, but also to protect the confidentiality of information stored on the device. It is advisable to keep your device in your possession at all times and not trust hotels, room safes, or other services to provide physical protection of equipment. When traveling, never check your device in as luggage; devices should be taken on board as hand luggage.
Avoid connecting to unsecured Wi-Fi networks for business purposes when traveling overseas. Only wireless communications, such as a password-protected business Wi-Fi or a trusted Wi-Fi network, should be utilized. Where possible, connect back to your organization’s VPN to use the Internet. N.B. You may not be able to do this without using Wi-Fi, and there is still an issue of trust with the VPN process because of what happens prior to the VPN being established. For example, a lot of devices still leak information after joining a network.
Finally, when you return, advise your IT security staff if the device was taken out of your possession for any reason, particularly if you have traveled to a high-risk country. Also advise them if you left your device in your hotel room for an extended period of time. IT security staff should be able to check the device for any malicious software or evidence of compromise.
12 Mobile Security Technical Controls
This section contains suggestions for a number of technical controls covered under mobile device security. There are a multitude of technical controls that can be used to mitigate the risks that arise from the use of mobile devices; however, not all apply to all types of mobile device.
In order to help mitigate the risk of lost, stolen, or misplaced devices, below are some actions that can be taken to protect your own data and that of others.
12.1 Passwords, Passphrases, and Biometrics
Passwords are a key control, as a weak password can enable the bypass or deactivation of many other controls. As mentioned earlier, a key bypass risk is having a simple PIN as a protection and the lost/stolen device being attached to a computer to conduct a brute force attack and mount the filesystem.
Laptop passwords can be long and complex without adversely affecting users, as laptops typically have full keyboards, allowing easy entry of the password.
It can be particularly challenging to ensure that users select secure passwords for smartphones and tablets, as they are typically accessed frequently throughout the day, with users regularly checking information in brief spurts rather than engaging in extended work periods.
Password or passphrase protect your device and enable auto-lock. Handle password credentials securely on the device, such as choosing the strongest alphanumeric passcode or passphrase that your device can support.
Users often think making good passphrases is harder than it really is. It is worth the effort, as a strong passphrase is harder to detect than for a password that may be fairly easily subjected to a dictionary attack.
Examples of good passphrases that are also mobile friendly are “scratchybrownvinyl420” which uses random common words and some numbers that includes 21 characters, or “Back2dafewture!” which is a short, easily remembered 15-character phrase that includes a capital letter, a number, a substituted word, a misspelt word, and a special character—although there is the hassle of typing them all in. Other example passphrases could be “x-Ray vision Is g00d,” or using a foreign word mixed with a different language—say an English phrase with a Malaysian word in the middle.
It should also be noted that some modern mobile devices have biometric locks, which typically provide more secure access control and are a supplementary or alternate control.
12.2 Encryption
Although encryption has been a staple of IT systems for decades, their implementation in mobile devices has its obvious limitations with the ever-growing number of devices to be managed, hence the use of automated enterprise systems. There is a reason that certain phone brand costs are prohibitively high for certain economies, paving the way for the proliferation of Android or Windows phones that do not include this special chip, making them three to four times cheaper. As stated by Auguste Kerckhoffs, even in mobile devices, everything about the encryption can be public knowledge other than the key. This stresses the importance of secure generation of key material either for link encryption or data protection.
12.2.1 Code Encryption
There are multiple reasons for a developer or an organization to encrypt the code used in their mobile application. From an operating system perspective, it helps in maintaining system integrity by providing a facility to detect code integrity violation. From a user perspective, this protects them from information theft or privacy violation.
Code encryption is not implemented by default by all mobile operating system providers. iOS, for example, does binary encryption by default; however, this is not necessarily the case with Android-based devices. It has to be noted that code signing is not the same as code encryption, as both the major mobile application curators require the apps to be signed to varying degrees. We will discuss this further later on.
Code encryption may help in preventing reverse engineering or code modification; however, the effectiveness of this control has been contested by many practitioners. While poor key management practices and implementation of insecure algorithms heavily degrade the effectiveness of code encryption, the question being raised by these practitioners is what is the point in encrypting code when it must be decrypted on the device before loading it into the processor for execution. At this point in runtime, taking a snapshot of the decrypted code in memory is trivial at best.
Identity-based code execution utilizing code signing techniques may very well be addressing most of the security and privacy concerns and could overcome many of the limitations not fully addressed by code encryption alone. As with any technical control, it is imperative that the intent is not lost during implementation. Certificates and key management techniques should cover appropriate process and technical controls to realize benefits of implementing code signing. Self-signed certificates and poorly managed private keys offer no real benefit of code signing.
12.2.2 Data Encryption
Data encryption deals with protecting user/consumer data and privacy. Although application code is also data for all practical purposes, the delineation can be drawn at the prime control objectives for each data type. The delineation is more easily seen in defining "whose data is it"—is it from me and based on things I know and do, or is it from the application, based on the intellectual property of the developers, their infrastructure, and architecture? When it comes to code, the prime control objective, in our justifiable view, should be integrity. This doesn’t mean that code confidentiality is unimportant, but there is little point in protecting intellectual property when its integrity cannot be assured. For example, how can you be sure the information out there is what you actually released if you can’t assure integrity? One would expect that the user-generated content in a mobile device is stored locally in a device. However, there are cases where data is not local, and that has implications not just for security/privacy, but for resilience and business continuity. User data is stored both locally and in the cloud. Let’s look at the security controls offered in both environments below:
Local
With the growing concern over privacy and the quest to make the mobile OS suitable for Enterprise IT, almost all mobile operating systems are providing some form of a full-disk encryption solution in their recent releases. In this context, full-disk encryption only refers to the process where data is encrypted before committing to the disk and decrypted before supplying data back to the calling process. This does not mean the entire disk is encrypted; as a matter of fact, some mobile device providers allow only encrypting certain volumes, but still call it full-disk encryption.
Cloud
Cloud storage is offered by mobile application curators, and mobile developers themselves in some instances, as a means to back up your data and provide multiple-device support and synchronization, as is the fact that they want to mine your personal data to sell it to third parties and generate ads.
Below are some of the types of data that are frequently stored in the cloud, as well as existing security controls offered by some of these storage providers.
Types of data that are potentially stored in the cloud:
• Browser bookmarks
• Chat logs
• System and application specific settings and logs
• Downloaded free and paid content including apps
• Passwords (such as saved passwords like those of your Wi-Fi network)
• Photos
• Game progress
Actually, nearly any function that is available on a mobile application that involves data could potentially be transmitted/stored on servers online. The downside of online servers is that they require a full-time data connection.
It is safe to assume that the data at rest that is leaving your device can be read by others unless it is encrypted locally within the mobile device with a key generated in the mobile device by user-supplied input.
Quite often we see companies claim that their product is secure because they use protocols such as TLS. While it is true that they address transport level security issues, they have no effect on the security of data at rest in cloud storage. Protection of data at rest can be best assured if the solution seeks user input for encryption and decryption of data.
The following implementation can offer some level of protection for your data that is stored in the cloud:
• The key generation process happens on your device.
• This key is encrypted using user-supplied input.
• The personal data is encrypted using this key.
• Only the encrypted data encryption key and the encrypted data are ever stored in the cloud.
• The data is only decrypted after bringing it back to the device.
Any other implementation of key management design is questionable. For example, Hardware Security Modules (HSMs) are not built to handle millions of keys. There is a theoretical limit on all of them, including those that are attached to cloud resources but behave pretty much the traditional way. You can have HSM-like features in the device, like Trusted Platform Module (TPM) and Apple's crypto processors, which bring it back to the device as the approach suggests here. It is never a good design to put millions of keys in a solution even if it supports it theoretically, as your solution will likely become a bottleneck due to the overhead.
Key Management Design
Key management design describes how cryptographic keys are protected, managed, and distributed. At the core, any key management design follows quite a similar approach. While device or platform specific implementation may vary, the following are the main components:
Chain of trust
This is the starting point of the key hierarchy, the seed. This seed in most cases is the unique device identifier (UID) of your mobile device. There are multiple claims from different sources that this UID cannot be seen or extracted by anyone including the device manufacturer, which is equally being challenged, too. For the purpose of this book and for a general understanding of the concept, unless this seed is generated by the user of the device within the device only, we cannot be certain about the ability, or lack thereof, of a device manufacturer to gain access to your data. Having said that, we would like to reiterate that cryptography is the science of delaying access to the data, not preventing it.
Master key
The master key can be created utilizing the UID, or in the devices where UID is not used, some cryptographic library functions are utilized to generate this master key. These functions may utilize environment variables to generate this key. Some manufacturers make claims that they only use a kernel-level key derivation function. The intent of such deep-rooted functions is to be able to encrypt the media at the block level, rather than any real security benefit. This master key is used to encrypt key stores or other keys including the data-encrypting key.
User-supplied PIN/Passphrase
In most cases, this user-supplied variable (referred only as PIN hereafter) is utilized to encrypt the master key only. Designwise, there is a good reason for not including it in the actual key generation process of the data encryption key. By design, the user-supplied PIN is expected to change frequently. When a user changes a PIN, unless the key that is encrypting the data is intact, the entire volume would need to be decrypted and then reencrypted with the new key. While we don't see any major design constraint in utilizing this user-supplied variable for generating the master key, such an implementation is not common, for reasons not known to us. This should be one of the most important items, given that nobody else is talking about it. It is only covered here at a high level, but it is a topic that needs to be covered in depth elsewhere, as it does not align with the intention or the tone of the book to go into that detail here.
Key Stores
Also called key bags in certain implementations, these are software constructs for storing the encryption keys. These key stores reside in your device and are also utilized to transport the keys over to other systems, like the device you authorize for backup/sync, and management servers.
Even with such a complex implementation, the data is only protected until you boot up or unlock your device after boot up (depending upon implementation), by which point the media is decrypted and the data is available in the clear. This is not a terrible thing because that is where the control cycle of a solution like full-disk encryption ends. This is the case with any implementation of a full-disk encryption solution on any type of device, including laptops and workstations. The key observation to note here is that the data should not be decrypted after boot up until the user authenticates themselves during the unlock process. It pays to reiterate that when a system has been unlocked after a reboot, the only protection that is available to safeguard your data on the device is your PIN. Fig. 2 from NIST Special Publication 800-63 shows the difficulty in guessing a password (expressed as entropy) in relation to its length.
While the design described above is common, it is not universal. We encourage readers to learn more and ask questions of their vendors and solution providers. This is the only way to have detailed assurances as to the security of a solution.
12.2.3 Key Management
Key management usually lies at the foundation of any other security activity, as most protection mechanisms rely on cryptographic keys one way or another. There are just too many keys with varying degrees of complexity (some perceived) with inadequate key management infrastructure. The figure below represents the global perception in terms of the relevant complexity in managing each key type. It has been realized that there are opportunities for some quick wins in this area with clear definition of the requirements and some perception management, with relatively little investment in technology.
Having said that, we acknowledge the challenge in managing the ever-growing number of keys utilized in public key infrastructure and persistent data protection. The key management systems, if any, have not scaled up to manage the proliferation of keys and the applicable requirements in protecting those keys. Further, some of the technologies utilized as key management systems were not intended for that purpose. For example, in the figure below, we can observe a strong notion globally that a Certificate Authority (CA) is a key management system, although it was not designed to be one (Fig. 3).
In our view, a key management system/solution is an integrated approach for generating, distributing, and managing cryptographic keys, not certificates, for devices and applications. The effectiveness of cryptographic techniques is highly dependent on the effectiveness of the systems and processes that are protecting the keys. If the integrity of the key cannot be assured, the integrity of the encrypted data cannot be assured either. Encryption only, without proper key management defeats the purpose of the control. Key lifecycle management covers keys through their lifecycle starting from creation, initiation, distribution, activation, deactivation, and termination.
12.3 VPN
VPNs are frequently used by mobile workers who are unable to guarantee a secure connection, yet might need to access an organization’s resources. If properly configured, a VPN prevents attackers from intercepting and modifying traffic, while allowing approved access to internal resources. However, a VPN does not offer security if the attacker has a presence on the mobile device or the network to which it is connected, such as the network at a coffee shop operator, hotel, the ISP/Telco, or even the VPN endpoint operator. Poorly configured and secured VPNs can pose a risk, as they could expose sensitive assets and potentially give an attacker access to the organization’s internal network, information systems, or credentials, enabling them to gain a foothold within the organization as the first step to a subsequent attack. One method to enhance the VPN’s security utility is to deploy multistep authentication or multifactor authentication to strengthen the VPNs security posture.
Three main types of VPN are available:
• IPsec VPNs, which are useful for point-to-point connections when the network endpoints are known and remain fixed.
• SSL VPNs, which provide for access through a web browser and are commonly used by remote workers (telecommuting workers or business travelers).
• Mobile VPNs, which provide mobile devices with access to network resources and software applications on a network, when they connect via other wireless or wired networks. Mobile VPNs are used in environments where workers need to keep application sessions open at all times throughout the working day, as they connect via various wireless networks, encounter gaps in coverage, or suspend and resume their devices to preserve battery life. A conventional VPN cannot survive such events because the network tunnel is disrupted, causing applications to disconnect, time out, fail, or even the computing device itself to crash. Mobile VPNs are being adopted more and more by mobile professionals and white-collar workers. They are commonly used in public safety, home care, hospital settings, field service management, utilities, and other industries.
12.4 User Training
User training is even more important than technical controls. An educated user on a device with poor security is safer than an uneducated user on a device with "strong" security.
The importance of how to actually use all of the security controls that are in place, information asset value awareness, and understanding the big picture are hugely important and should be a focus of any training program.
N.B. This is a hugely important topic that deserves additional consideration. All the technical controls in the world won’t matter if you don’t have the right knowledge and understanding by the users, or for that matter, mobile application developers.
12.5 Jailbreaking and Rooting
Jailbreaking and rooting refers to the process of removing limitations put in place by a device’s manufacturer, modifying the operating system so that the native operating system restrictions are removed and modifications can be made to any part of the operating system and underlying filesystem. This allows the end-user to install third-party software from outside the app store. Essentially, jailbreaking allows you to use software of which the manufacturer does not approve.
Companies don’t want users jailbreaking their devices to get past the operating system limitations so you can change the default programs or run third-party applications. To perform a jailbreak, someone has to find a security vulnerability that allows the device to be “exploited” in order to get around the manufacturer’s safeguards.
Android allows users to install third-party applications from outside the Google Play Store right out of the box, so Android doesn’t need to be jailbroken. This is both a great feature and a threat to the security of the operating system. Users need to balance this and understand the trade-off if they install such third-party applications.
Rooting is the process of gaining “root access” to a device, which refers to gaining privileged control or administrative access to a device and getting around Android’s security architecture that is designed so that the user does not have full administrative access for good reasons; in the vast majority of cases, users won’t ever need it.
N.B. This is generally performed on Android devices, giving the user the ability to perform operations that are otherwise inaccessible to a normal user, but rooting can also occur on other devices.
On some devices, rooting may need to be accomplished via a security exploit. Just like jailbreaking, manufacturers generally don’t want you rooting, since it can affect device performance and behavior and potentially lead to support issues. If you make changes to the underlying operating system and applications, then things can behave erratically, which drives up customer complaints and could lead to a poor user experience.
It should be noted, that jailbroken, rooted, nonmanufacturer devices may not respond to the wipe command to pose risks to users’ sensitive information if a device is lost stolen or misplaced.
12.6 Patching
Patching is the process by which software flaws are fixed and features improved. Smartphones and tablets require patching as vulnerabilities are discovered. However, since apps are restricted in terms of what they can do if properly coded in the right modern mobile operating system, the significant attack surface is the operating system itself. It should be noted, however, that jailbreaking/rooting destroys this protection. As such, many attackers, security professionals, and jailbreakers attempt to find security issues in mobile OS, or more frequently, in vendor-distributed applications that serve as a gateway to OS exploits. As an example, Apple’s iOS 9 upgrade improved/fixed about 100 security issues from the last release of iOS 8.
12.7 Asset Management
Asset management is an important control for organizations in deciding policy and monitoring its implementation, as well as allowing an effective response to breaches or security issues.
MDM software is available from many vendors, each offering a range of features, in addition to simple asset lists. However, MDM software rarely adds controls to a smartphone or tablet operating system; instead, it simply provides convenient access to built-in controls on the device itself. The level of control that an MDM solution can offer is therefore dependent on the device and, occasionally, on the version and even the manufacturer of the device.
12.8 Mobile Device Management
MDM solutions provide features such as secure access to corporate email, automatic device configuration, certificate-based security, and selective wipe of enterprise data for both corporate and user-owned devices.
MDM software can often indicate whether a device has been jailbroken. Jailbreaking deactivates or bypasses many crucial security controls and it is therefore recommended to track it and deprovision any jailbroken devices, which should be prevented from accessing the organization’s resources.
The following sections cover some specific MDM areas for organizations:
12.8.1 Inventory
An organization’s MDM should maintain a list of devices to be managed; that is, a mobile asset inventory.
The MDM inventory may include:
Device Inventory
Beyond the basics (e.g., device ID, hardware model, firmware version), an MDM can help record and report on related assets like wireless adapters and removable memory.
Inventory Classification
An MDM might autoclassify devices by mobile OS/version or state (e.g., unknown, authorized, provisioned, decommissioned).
Inventory Maintenance
An MDM might be used to periodically poll devices, check for changes at network connect, or carry out administration-initiated audits.
Physical Tracking
With many smartphones now supporting GPS, location-based MDM features are possible.
Database Integration
An MDM may be able to integrate managed mobile device records into a common database using inventory exports or reports.
12.8.2 Device Eligibility
Device eligibility depends on many characteristics, including operating system and vendor/model/version that the organization is prepared to support. The organization needs to decide what platforms (e.g., Apple iOS, BlackBerry OS, Google Android, Microsoft Windows Phone) and minimum models/versions (e.g., Samsung SAFE devices running Android 4 +) to support. Device-independent management choices should be made wherever possible and practical while establishing baseline acceptance criteria for specific business uses (e.g., hardware-encrypted devices with remote find/wipe capability).
12.8.3 Device Registration/User Enrolment
MDMs can help administrators register organization-issued mobile devices, or let users register their own devices (e.g., through enrollment portals), or some combination thereof.
With good MDM, users can quickly self-enroll their mobile devices.
12.8.4 Lockout screen
If a mobile device is found to be out of policy, lost, or stolen, or if an employee leaves the organization, an MDM server can take action to protect corporate information in a number of ways.
To permanently delete all media and data on the device and restore it to factory settings, MDM can remotely wipe the device. If a user is still looking for the device, the IT section can also choose to send a remote lock command to the device. This locks the screen and requires the user’s passcode to unlock it.
12.8.5 Policy
To gain user acceptance, organizational policies might need to balance a user’s desire for access and the organization’s desire for security. Policy should be developed with an understanding of business and user requirements, as experience indicates that users will attempt to bypass or otherwise render ineffective controls that they feel are overly restrictive. Users should therefore be educated as to the reason for the restrictions and the implications of bypassing them.
12.8.6 BYOD vs. Choose Your Own Device (CYOD)
If BYOD personal smartphones and tablets are used for business purposes, it is recommended that they be managed using MDM software, as this can ensure that organizational policies are followed.
An alternative to BYOD is CYOD. Offering employees a choice of approved devices provides more control for IT, compared to allowing them to bring any smartphone or tablet they want.
However, CYOD strategies also mean less freedom for employees and may not provide as high a satisfaction as BYOD.
Businesses can let employees choose from devices that they are sure can be managed and secured to the required extent. This is useful for dealing with Android fragmentation, meaning the multitude of different Android versions on different phones on the market. CYOD ensures that only the most up-to-date and secure versions of the OS are supported.
12.8.7 Remote Wiping BYOD Devices
Many configurations will allow a corporate administrator to wipe a personal device that has been enabled for BYOD usage. A capable MDM solution that actually can per-app-wipe and only touch organizational data i.e., a “selective wipe” that only removes corporate information, shouldn't need a full device wipe. However, in some cases, an administrator will need to wipe the entire device; for example, if there aren’t containers around corporate data it can increase this requirement, meaning that personal data will be lost in the process. An entirely possible use case involves the loss of an employee’s phone that contains family photos not saved on any other device. An administrator might wish to wipe the device to ensure the safety of the organization’s data, while an employee might prefer to wait in the hope that the device is recovered. Wiping the device could potentially present the organization with legal issues.
Policy and user education is therefore vitally important, so organizations supporting personal devices are strongly encouraged to design a policy that takes remote wipe into account and to ensure that users are aware of the implications. Likewise, users need to do their homework as to what their MDM solution provides and to take into account what their organizational policies may require.
12.9 Mobile Application Management
Successful enterprise mobility management requires a MAM solution that has an enterprise app storefront, as well as the ability to secure mobile applications on the device, authenticate end-users, separate business and personal apps, monitor application performance and usage, remotely wipe data from managed applications, and retire apps when necessary.
MAM focuses on application management and differs from MDM. It provides a lower degree of control over the device, but a higher level of control over applications. MDM solutions manage the device by saying what major operating system is required, the configuration settings and can include management of all applications and application data, and crucially, things like accounts (e.g., email accounts), network connections (VPNs, Wi-Fi), etc.
12.10 Remote Track and Wipe
Remote track and wipe is slightly different from remote wiping, as described in the previous section. Remote track and wipe aims to mitigate the risk of device theft or loss. For many, this is about the end-user having a self-service and “native” capability under their control. iOS has this built-in, and recent Android devices may support it as well. It works by having the device maintain or regularly establish a connection over the Internet to check for updates or to phone “home.”
Most modern smartphone and tablet platforms have remote wiping and tracking built into the operating system. As tablets may not always have a mobile Internet connection, it may be more difficult to track or wipe a tablet until it is connected to a data network and is once again reachable for review and potential wiping.
12.11 Antivirus/Antimalware
AV solutions are helpful controls against common malware types. The flaw in older AV solutions is that a sample of malware has to be detected and analyzed before it can be identified by an AV product, but this style of AV is not that common anymore. Many newer mobile solutions use behavioral analytics and signaling back to a remote cloud server to analyze malware; signatures are still used, but other approaches are growing.
Regardless of ownership, where corporate systems are using Windows, having an AV solution in place is of higher value, given that is also where the threat is. Furthermore, since AV is dependent upon updates in order to work effectively, policies should ensure that the AV is able to update.
AV solutions for iOS and Windows devices, such as the iPhone, iPad, and Windows Phone devices, offer security “controls” built into the operating system, which contain the security risk. Consequently, AV on these devices is typically limited to scanning specific files rather than offering background, on-access scanning of files. If AV could operate freely on the platform that would imply that malware could as well. However, this is a trade-off that is worth encouraging. You don't want any software to have full and unrestricted access to the operating system/device—only the operating system kernel and tightly restricted APIs.
Android is a different matter, though, as the operating system is more permissive, which is also the problem. Permissiveness comes at a cost, and if the user is willing to accept that cost, it may mean they also have to bring on board additional controls and protections. Malware has been found on Android devices, hence an AV product could potentially provide a useful function in the same way it does on a laptop.
12.12 Transmission Security
Since the majority of smartphones are capable of using multiple network mechanisms including Wi-Fi, provider network (3G, 4G, CDMA, GSM, LTE, and others), Bluetooth, etc., sensitive data passing through insecure channels could be intercepted if the user explicitly runs applications to permit this. Therefore, it is advisable that where the device is the receiver of data to disable wireless access, such as Wi-Fi or Bluetooth, when not in use so as to prevent unauthorized wireless access to the device.
12.13 Mobile Usage Controls
Mobile phone telecommunication service providers have various options for controlling mobile devices including controls for privacy and usage, filtering content, and location and monitoring settings.
12.13.1 Usage Controls
Most companies will allow users to turn off features, such as downloading videos or images, texting, premium call numbers, overseas calls, and Internet access. These controls can also be used to limit the number of calls or texts and set time restrictions.
12.13.2 Content Filtering
These controls can block certain websites to allow for safer mobile browsing on the Internet. Some filters can also limit videos and other multimedia.
12.13.3 Location and Monitoring Settings
These controls allow users to track their mobile device’s whereabouts using GPS systems that are built into the phone.
12.14 Memory
Most modern mobile devices contain a combination of SIM cards and removable storage, such as an SD card, and most devices have some amount of internal storage. If you are intending to replace your mobile device with a new device, before disposing an old mobile device, it is important to consider deleting all of your personal information, photos, messages, and contacts from the SIM, removable storage, and internal storage. However, it is worth noting, some information may still be stored on the device in locations you missed or are restricted by the manufacturer.
12.15 Cross-Border Data Theft
Mobile devices as a vector for data to leave the organization is nothing new, as the inherent mobility beginning with laptops has always made it impossible to rely on a strong perimeter for adequate protection. The cloud computing revolution and the myriad of hosted application services that are not geographically fixed has made it easier for data to cross national borders. With the increased use of mobile, the applications and data stored in mobile devices used locally and globally may put both users and organizations at risk. In addition, data traveling on the mobile devices is typically subject to laws and regulations that will vary from one jurisdiction to another. There are many legal/jurisdictional issues with this architecture, and organizations are just now starting to work through them.
The cross-border nature of cybercrime means that organizations should ensure good document protection practices by improving digital document security techniques. A second aspect is for organizations that have international offices, where cross-border document exchange is known, should establish proactive relationships with colleagues in international locations to identify and minimize barriers to swift and effective international cooperation in response to cross-border data theft.
12.16 Regulatory Retention
The amount of data that can be stored and processed in mobile devices has grown dramatically.
The increased use of the inherent storage and computing capacity of mobile devices has created a new data retention risk. As an example, one trend is the popularity of iPads for use by company board members to access confidential corporate data and board reports. While the electronic copies of board papers made available on a device may be secure, annotations made to/for a document on the device itself, which constitute legal documents, are not captured or stored under corporate ownership. This is important for complying with statutory recordkeeping requirements and for preventing legal risks, such as Income Tax Assessment Acts, which require entities to keep records that note and explain all transactions and other acts relevant to the Act for a number of years. The same goes for Corporations Acts, which require companies to retain documents that disclose the company’s transactions, financial position, and performance for a number of years after the transactions covered by the records are completed. The period of retention for these and similar Acts may vary, depending on the country involved.
13 Forensics
Mobile device forensics relates to the recovery of digital evidence or data from a mobile device under sound conditions due to the necessity to preserve “evidence” when it comes to legal proceedings.
With the ubiquity of mobile devices, forensic evidence extracted from mobile as well as other electronic devices can be an invaluable source of evidence for investigators in both civil and criminal prosecution cases. Smarter, more powerful mobile devices hide a potential treasure trove of evidence for investigators and prosecutors alike. Mobile device data can be extracted and then used to generate reports on a range of data including an individual’s communication, location, and travel habits. For example, in a criminal investigation, the data, which includes transaction information such as calendar events, call history, emails, messages (SMS/MMS/emails), and photos, are often able to be supplied to an investigating official in a report format. For the evidence to be admissible in a court of law, relevant forensic procedures must be followed.
A number of frameworks exist to provide guidance for the conduct of digital forensics that form the basis of these procedures. Digital forensics frameworks have been published (Kent et al., 2006; McKemmish, 1999; Martini and Choo, 2012), as have mobile forensic procedures and tools (Me and Rossi, 2008; Owen and Thomas, 2011; Savoldi and Gubian, 2008). This has enabled practitioners to make sound decisions in the development of high-level forensic procedures, as well as in specific cases using specific tools (Guo et al., 2009).
One of the key strategic challenges presented to digital forensic practitioners, particularly those in law enforcement, is maintaining capability in an environment of rapid development of communication and information technologies and its ready adoption by the public and offenders (Adams, 2008; Choo, 2011). Smart mobile devices, for example, are much more complex than traditional mobile phones and with a range of personal data management facilities, these mobile devices more resemble personal computers than they do phones. By holding a significant amount of data that could be of interest to a forensic investigator, it makes smart mobile devices particularly interesting for analysis. The 2016 lawsuit of FBI v. Apple wanting to unlock the San Bernardino shooter’s phone received widespread media coverage, but was far from an isolated case.36 As Nate Smith of URX.COM says, “The future of mobile means a more intricately connected ecosystem of applications! The “walled gardens” will be torn down and roads and bridges between apps will be constructed. The relationships between the apps that a user has installed on their phone will become exponentially more important, to both the consumer and the businesses themselves.” However, the method of collecting evidence for mobile devices is quite different when compared with traditional forensic computer hard disks.
14 Summary
This chapter provides information on awareness of mobile device risks for individuals, as well as items to consider for organizations.
It suggests 10 steps to secure mobile devices for the digital age, which were mentioned near the start of this chapter.
Application builders, mobile device manufacturers, and telecommunications providers all need to provide assurance for users that they are acting responsibly in protecting mobile device information and thereby building trust for the digital economy. This means applications responsibly accessing data, the secure storage of data on the mobile device, and the secure transmission of data by telecommunication providers. When all three of these act responsibly together, trust will be built-in line with the individual’s expectations.
Some of the key risks for individuals to be aware of are:
– Information exposure. Be aware of the risks of keeping highly sensitive or confidential personal data on mobile devices.
– Privacy implications that come along with the technological capabilities that mobile devices provide.
– If the device is lost or stolen, the information goes with it and can potentially be viewed by unauthorized individuals.
– Every person who has or will have a mobile device means that every mobile device is a target that can be exploited.
– Lack of protection of data through not implementing encryption can lead to straightforward data exposure. For example, inclination to trust default mobile device settings will result in continued exposure.
– The scope and risk of mobile device information exposure is extended by the remote-control capability to spy.
Some of the key concerns for organizations are:
– It is essential that organizations have suitable strategies in place for securing mobile devices.37
– That there are implications in place for the confidentiality of information for business.
– Organizations must shift their focus to data-centric models rather than system or device-centric models, to ensure they have appropriate security coverage because the risks have already shifted.
– MDM controls can help with general security. However, it isn't a universal cure-all, and products vary significantly with respect to functionality and approach.
– Protection of data through encryption.
– Mobile testing before a mobile application, or app, goes live.
– Privacy concerns.
– Identity management.
– Security awareness training for mobile devices for staff.
– Maintaining digital trust with customers.
– Consideration of BYOD programs and the implications for organizational policy and security relating to integration within the organization.
This can be summarized in the following diagram, showing the overlap between individuals and organizations (Fig. 4):
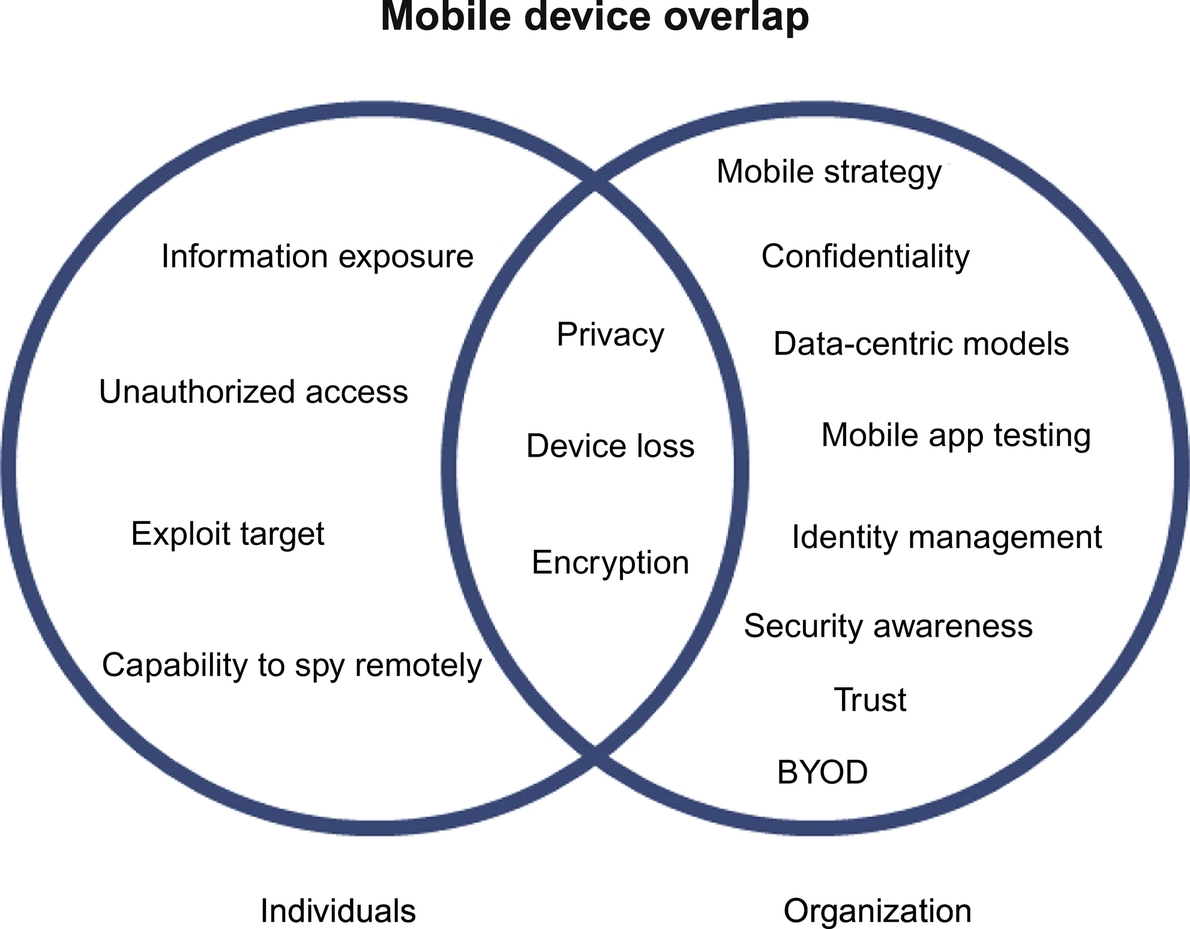
Below are 10 steps to share in the quest of realizing a safe, private life in the digital age and to make sure that your mobile devices—and everything that’s on them—stays safe:
1. Lock your mobile device when you’re not using it.
Be sure to use a strong and unique passphrase, pattern sequence, or biometrics. It’s a lot harder for people to gain access to your valuable information if the device is secured with a strong password or “passphrase” (a series of three of four words and some numbers together).
2. Consider encrypting your data to prevent unauthorized access.
Make sure that device encryption is enabled on your device. While some device manufacturers enable encryption by default, others require that you enable this in the device settings. If your device is lost or stolen, contact your mobile device manufacturer/operating system maker as soon as possible. Your manufacturer/operating system maker may have the native functionality capability to remotely wipe or disable the device to prevent unauthorized access or remove the data stored on the device. Additionally, contact your telecommunications service provider, who has the ability to manage charges due to unsolicited messages sent from your device by malware, and can disable the device from being able to register on the mobile network.
In the case of theft, contact your local police agency as they may be able to work with your service provider to track and recover your device if reported promptly.
3. Update your device.
Install updates for both the operating system and the apps running on your device. These updates often provide functionality improvements and security enhancements to prevent malicious attacks.
4. Know your apps and only use trusted sources for downloading them.
Use official app stores, which are more likely to screen for malicious or counterfeit apps, and you are more likely to be notified if you have downloaded a suspect app than if you use alternative download sites.
Be sure to read the user agreements and research the information to which an app has access. If you are uncomfortable with the permissions the app is requesting, consider not installing it.
5. Turn off location services or disable location services for specific apps.
Location services can often be disabled entirely or allowed on an app-by-app basis. Consider disabling location services or limiting which apps can access location services. Doing so does not prevent your service provider or law enforcement from using your location information.
6. Limit your use of applications or browsers over open and unprotected Wi-Fi.
It’s often impossible to know if the Wi-Fi you’re accessing is secure. If you’re not sure, don’t use your mobile device, or limit your use of it.
Most free public Wi-Fi networks are unencrypted or open, so it is preferable to use your mobile data or a trusted, password-protected Wi-Fi network for activities like Internet banking or sending and receiving sensitive materials.
If you have a smartphone, use a VPN with it to provide another layer of security and protection, especially when you send sensitive information. A VPN encrypts data while in transit, both through regular and wireless networks.
7. Turn off Bluetooth when not using it.
Disable Bluetooth-enabled services when not required to help prevent phishing attempts and the spread of malware or viruses.
8. Don’t root or jailbreak your device.
Not only does rooting or jailbreaking violate the terms of service of most device manufacturers, it potentially exposes your device to greater harm from malicious apps.
9. Back up your device.
Sync or back up your mobile device. Many mobile devices have the ability to be synced and backed up to your personal computer or the cloud. Loss, damage, and even software updates can cause you to lose all of your data. If you don’t have a backup, your important phone numbers, favorite photos, and other data could be lost forever.
10. Be sure to wipe your device prior to trading it in, selling, donating or otherwise disposing of it.
Delete all your personal information, photos, messages, and contacts from all SIM cards, removable memory, and internal memory.
Consider taking your device to your service provider or dealer to be wiped and reset to factory defaults in order to remove information that may still be stored on the device in locations you missed or are restricted from accessing by the manufacturer.
15 Mobile Device Security Resources
A multitude of security resources exist for mobile device users, developers, and enterprises. Some useful security resources include:
ENISA Smartphone secure development guidelines at http://www.enisa.europa.eu/activities/application-security/smartphone-security-1/smartphone-secure-development-guidelines
Google Identity Platform Mobile App Best Practices at https://developers.google.com/identity/work/saas-mobile-apps
Mobile device security information for IT Managers from the Trusted Information Sharing Network at http://www.tisn.gov.au/documents/mobiledevicesecurityinformationforitmanagers.pdf
NIST Mobile Device Security Project with best practices for mobile security at https://nccoe.nist.gov/projects/building_blocks/mobile_device_security
NIST Computer Security at http://csrc.nist.gov/publications/nistpubs/800-57/sp800-57_PART3_key-management_Dec2009.pdf
OWASP Mobile Security Project at https://www.owasp.org/index.php/Mobile
OWASP Top 10 Mobile Controls at https://www.owasp.org/index.php/Mobile#Top_10_Mobile_Controls
OWASP Top 10 Mobile Risks at https://www.owasp.org/index.php/Projects/OWASP_Mobile_Security_Project_-_Top_Ten_Mobile_Risks
Security Tips and Tricks for the iPhone 6 s/6 s Plus at https://blog.malwarebytes.org/mobile-2/2015/10/security-tips-tricks-for-the-iphone-6s6s-plus/
Stay Safe Online mobile safety information at https://www.staysafeonline.org/stay-safe-online/mobile-and-on-the-go/mobile-devices
The Mobile Web Initiative at http://www.w3.org/Mobile/
 Tip: Be aware of your social network privacy settings and know that if you are using social media and your post is public, anyone can see it!
Tip: Be aware of your social network privacy settings and know that if you are using social media and your post is public, anyone can see it! Individual implications
Individual implications Organizational implications
Organizational implications Individual implications
Individual implications Organizational implications
Organizational implications Individual implications
Individual implications Organizational implications
Organizational implications Individual implications
Individual implications Organizational implications
Organizational implications Callout: Maybe it is worthwhile to think about the number of applications or platforms that asked for your input to generate a key for backup encryption before storing it in the cloud. There aren’t too many, you say? We are not surprised!
Callout: Maybe it is worthwhile to think about the number of applications or platforms that asked for your input to generate a key for backup encryption before storing it in the cloud. There aren’t too many, you say? We are not surprised! Tip: Removing hardware restrictions (e.g., rooting on Android, and jailbreaking on Apple) on your mobile device in order to install unapproved third-party apps or features can weaken built-in security protections, leaving your phone susceptible to malware.
Tip: Removing hardware restrictions (e.g., rooting on Android, and jailbreaking on Apple) on your mobile device in order to install unapproved third-party apps or features can weaken built-in security protections, leaving your phone susceptible to malware. Tip: Regardless of the phone you use, it is vital to keep your operating system and apps up-to-date by enabling automatic updates. Old versions of software can have security issues and fraudsters can exploit these to access your data.
Tip: Regardless of the phone you use, it is vital to keep your operating system and apps up-to-date by enabling automatic updates. Old versions of software can have security issues and fraudsters can exploit these to access your data. Tip: Location services on mobile devices are great to help you find your way or locate nearby services. It can also be used to share details of your location. But sharing this information publicly could place the user at risk.
Tip: Location services on mobile devices are great to help you find your way or locate nearby services. It can also be used to share details of your location. But sharing this information publicly could place the user at risk. Individual implications
Individual implications Organizational implications
Organizational implications Individual implications
Individual implications Organizational implications
Organizational implications