Mobile Security
End Users are the Weakest Link in the System
L. Lau Asia Pacific Association of Technology and Society (APATAS), Hong Kong Special Administrative Region
Abstract
With the commercialization and widespread usage of the Internet over the past three decades in both the developed economy (global North) and less-developed economy (global South), it was estimated that in Jun. 2014, 39% of the world population was surfing the Internet daily.
With a vast number of individuals now using the Internet, particularly in recent years, there is a growing adoption rate of mobile and portable devices witnessed in the developing economies (global South). Nevertheless, mobile security is increasingly a concern, as more and more commercial activities are migrating from a traditional personal computer (PC)-based platform to a mobile phone platform. While multinational corporations have likely been investing considerable financial and human resources in order to beef up their cyber and mobile security … although still small number may not up there yet, but overall it is relatively mature on cyber and mobile security, especially their internal network security. However, small and medium businesses are fragmented in terms of their investment in cyber and mobile security due to the inherent financial constraints. The situation for individual Internet and mobile end users may be even more dire because of proliferation of individual and personalized portable devices. These individuals are reluctant to invest money in adding security software to their different portable devices, perhaps because they are unaware of their vulnerability to uninvited third parties who might access those devices. As a result, Internet and mobile end users are the weakest link on the mobile security chain. In this chapter, our discussion will highlight some of the risks within the mobile ecosystem, the reasons that end users are the weakest link in the chain, and what can be done to break this weakest link, if anything.
Keywords
Mobile security; End users
1 Definition: Security “Internetwork”
There are various definitions of computer system security. According to the Oxford dictionary, “security” generally means any system that is consistently free from danger or threat. For example, if we strictly follow this definition, the “internetwork” system must be designed to provide maximum security against any “malicious” attack or “uninvited access” into the system; that is, it must be a practically air-tight system that nobody can penetrate or access. Other definitions for internetwork security include a more traditional definition made up of three criteria to protect the physical machine, even though the data inside the machine are worth more than the machine itself. These criteria are: (i) to prevent others stealing or damaging the computer hardware, (ii) to prevent others stealing or damaging the computer data, and (iii) to minimize or prevent disruption of computer service. Another definition is more specifically related to Internet security, of which, broadly speaking, there are two levels. These are: (i) security for the Internet browser, and (ii) security for the operating system as a whole (i.e., “network security”). Internet browser security is the first layer of Internet defense, protecting the network data and computer systems from uninvited attacks, as the browser is basically a software application for retrieving, presenting, and traversing information resources on the World Wide Web (WWW). Whenever a browser communicates with a website, as part of that communication the website collects some information about the browser to be able to process the formatting of the page to be delivered and made readable for the human user. Therefore, the browser security methodology typically used is called “perimeter defense.” This involves a firewall and a filtering proxy server, which block unsavory websites and perform antivirus scans of any file data downloaded, thereby blocking malicious network data before they reach the browser.
However, network security is far more complex than browser security because it involves the core function of the Internet; that is, the “heart and mind of the Internet” in the operating system, or the “engine” of the Internet. Typically, this involves a different layer or “suite” of security protocols. Mainly these are: a network layer security protocol, which largely consists of two additional types of protocol, the Transmission Control Protocol (TCP) and the Internet Protocol (IP). Both provide end-to-end connectivity and format how data should be packetized, addressed, and transmitted until it is received at the destination. TCP and IP are secured through cryptographic methods and security protocols. Internet Protocol Security (IPSec) is specifically designed to protect TCP/IP communication in a secure manner using encryption and consists of two protocols, the Encapsulating Security Payload (ESP) and the Authentication Header (AH) protocols. These two protocols provide data integrity, data origin authentication, and an antireplay service. They can be used alone or in combination to provide the desired set of security services for the IP layer.
As discussed, there is no single definition for computer system security, but instead a range of definitions that make up information technology (IT) security. For convenience, the definition of Internet security is adopted in this chapter. Technically speaking, today's smartphone largely functions as a PC that is smaller and more mobile than the traditional PC. This brings the smartphone within the ambit of computer security.
2 Growth of Smartphone Breaches
With the commercialization of the Internet and the proliferation of its usage over the past three decades, it has been estimated that by Jun. 2014, 39% of the world population was surfing the internet daily, which included both the developed economies (global North) and the less-developed economies (global South).
With such a vast number of individuals now using the Internet, particularly in recent years, there has been a growing adoption rate of mobile devices, even in the developing economies (global South). As a result, mobile security has increasingly become a concern, as more and more commercial activities migrate from the traditional PC-based platform to the mobile phone platform.
Smartphone ownership is no longer confined to the privileged few who can afford high-priced technology, as increasingly cheaper devices are being introduced into the consumer market by manufacturers in Asia. For example, purchasing an Xiaomi1 smartmobile can be as cheap as $140 per device in mainland China. As a result, according to the Pew Research Center Technology Ownership Survey of Oct. 2015,2 68% of American adults owned a smartphone, compared with only 35% in 2011. In the 18–29 age group, almost 90% had a smartphone, while ownership among those aged 30–49 stood at 83%.
Similarly, smartphone ownership in Asia is also high; for example, as the BBC reported in Sept. 2015, there were 2.5 billion mobile smartphone users in Asia, a high number of whom were addicted to their smartphones. The BBC News explained:
Asia and its 2.5bn smartphone users provides a stream of phone-related ‘mishap news’, such as the Taiwanese tourist who had to be rescued after she walked off a pier while checking Facebook on her phone. Or the woman from China’s Sichuan province rescued by fire fighters after falling into a drain while looking at her [smart-] phone.3
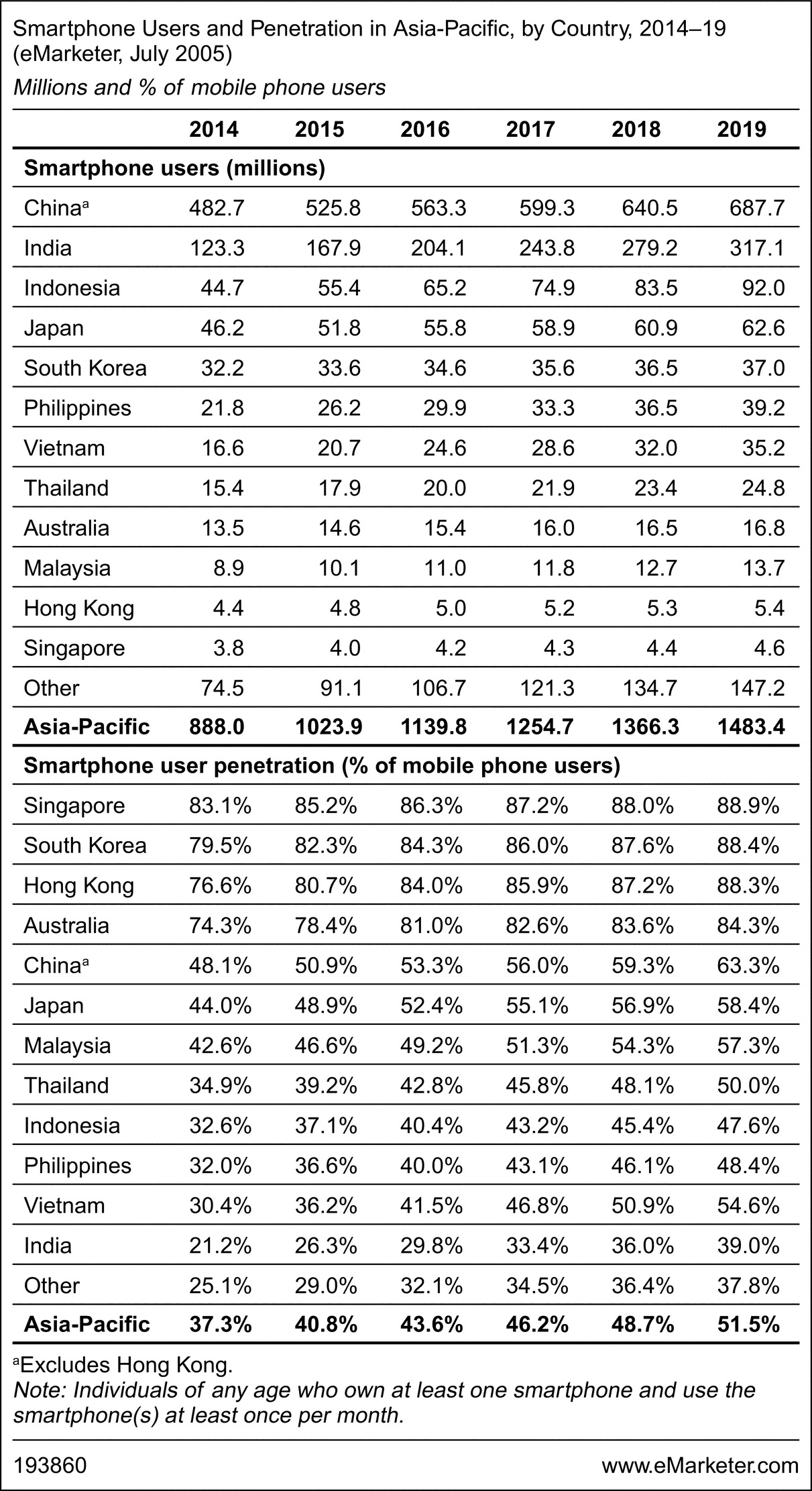
Fig. 14 highlights the number of smartphone users and the penetration rate in the Asia Pacific region. As indicated in the table, the percentage of smartphone users is high and has led the way for the mobile phone revolution, especially in Mainland China.
As Mobile Marketing reported on Sept. 1, 2015, the smartphone adoption rate in Asia has risen year over year:
Demand for smartphones in Southeast Asia has hit new heights in the first half of 2015, with sales up nine per cent year-on-year and almost 40 million units shipped in the first six months of the year alone. Consumers across seven of the region’s key markets (Singapore, Malaysia, Thailand, Indonesia, Vietnam, Philippines and Cambodia) have generated more than $8bn (£5.2bn) in sales value so far this year, with 3.2m more smartphones sold between January and June 2015 compared to the same period last year.5
According to Statista,6 the two market leaders in smartphones are Samsung and Apple.
So far, this has all been positive news for both smartphone manufacturers and end users alike. End users are spoiled for choice and enjoy lower prices, too, as most smartphones are manufactured in Asia, such as Samsung, Huawei, and Xiaomi; even the Apple iPhone is produced in Asia.
However, along with the new benefits that every new technology delivers, there come new risks, too. The smartphone is no exception, especially regarding the security risk to smartmobile data. For example, according to the Mobile Industry Review,7 there are a number of risks with smartphones. These include nation state-sponsored “license to kill” spyware, with the Communist party in Mainland China known to plant a hidden spyware app on smartphones in order to seek out individual user information, especially on Xiaomi's phones, as widely reported in the media. Likewise, both the US and British governments are known to be setting up mobile towers to eavesdrop on people and monitor their conversations.
Another example concerns smartphone security and privacy in regard to adware and Trojan horse malware. This involves sending a text message that contains Trojan horse malware that captures the unknowing smartphone user's financial details, such as credit card information.
According to PC World, individual end users are still the weakest link to security:
You can implement rock solid network security; enforce strong, complex passwords; and install the best anti-malware tools available. Most security experts agree, however, that there is no security in the world that can guard against human error …8
A similar comment from Science Nordic (“You (individuals) are the weakest link in IT security”) went on to say that:
Hackers often gain access to IT systems by exploiting the weakest link in IT security—the users. New social IT security system aims to weed out the human factor. Why bother to hack into complex security systems when it’s so much easier to hack into people, by using social engineering technique …9
For example, spear phishing is the technique often used to exploit individual users' smartphone and information technology devices. Bloomberg Businessweek reported that “the U.S. Justice Department told the source that a common spear phishing attack was used by hackers to gain access to several companies after malicious individuals obtained usernames and passwords from users themselves. In 2013 alone, there were 450,000 reported phishing attacks, which resulted in $5.9 billion in losses.”10
In another instance, individual mobile apps with weak passwords were the problem. As widely reported in the news, phantom thieves withdrew money from individual Starbucks app accounts in the United States:
Maria Nistri, 48, was a victim this week. Criminals stole the Orlando wom[a]n’s $34.77 in value she had loaded onto her Starbucks app, then another $25 after it was auto-loaded into her card because her balance hit 0. Then, the criminals upped the ante, changing her auto reload amount to $75, and stealing that amount, too. All within 7 minutes. … The trouble started at 7:11 a.m. on Wednesday when she received an automated email saying her username and password had been changed, and if she hadn’t authorized the change, she should call customer service. She tried, but the number she called notified her an operator couldn’t answer until 8 a.m. Whoever did this knew the right time to do it, she said. When Nistri launched her phone’s Starbucks app, she could actually see the thieves stealing first the $25, then $75, in real-time as it happened—and other Starbucks app users report suffering similar thefts, too.11
The examples cited above provide only a snapshot of potential security issues, but they reinforce the truth that the individual end user is likely to be the weakest point in the cybersecurity chain. According to various reports, over 70% of cyber-related incidents, including smartphone attack incidents, pointed to human error, and, even though the corporation itself and its information technology system is relatively secure, it is the individual who brings the cyber system down. One reason for this vulnerability in individuals lies in how we define information technology (IT) security itself, and there are many ways we can define, promote, or project what computer security is.
3 Organization Internetwork Security
The main objective of a commercial corporation is to pursue profit for its shareholders. Therefore, a commercial organization's internetwork system is designed to focus on business growth. In general, an internetwork system security is designed at an acceptable or standard level that meets regulatory requirements at home and abroad. As a result, it is fair to say that organizations' computer networks are not designed with security as their most important goal; in fact, only military-classified computer systems are designed with security as their most important objective.
Nevertheless, multinational corporations, for a number of reasons, have worked to improve their internetwork security. First, there is compliance with national legislation, as most countries have been updating their existing legislation or have passed new laws on cyber-related issues; in particular, legislation has addressed data protection and individual clients' personal details as related to privacy protocols or protection. Furthermore, panregional trading blocs and global institutions have been active in this area. For example, the European Union (EU) Parliament has passed cyber legislation and regional conventions that set the standard on cybersecurity for organizations that are based in the EU, such as the Council of Europe Convention on CyberCrime. Moreover, the United Nations has written a guideline treaty for itself and its member countries to follow the best practices set forth by the United Nations Convention or Protocol on Cybersecurity and Cybercrime. All of these new cyber-related laws, conventions, and treaties, both at home and aboard, have forced multinational organizations to seriously beef up their provisions on data protection and security so they can satisfy and meet the required trading standards.
Second, political groups and parties have put pressure on multinational organizations to shore up their cyber security due to pressure from their respective voters and members. Third, nongovernmental organizations (NGOs), such as consumer rights groups, have also been very actively lobbying on behalf of consumers to pressure governments to legislate and regulate multinational organizations on cybersecurity. Finally, the public and the consumers themselves are actively putting pressure on multinational organizations by way of boycotting organizations whose e-commerce websites do not meet the standards required by law or the industrial conventions on cybersecurity. For all of these reasons, multinational organizations must patch up their cybersecurity. More importantly, multinational organizations have the financial means to do so, including the human resources required to maintain the requisite cybersecurity. This is especially so with global banks and financial investment organizations. As a result, the security measures on multinational organizations' network systems are largely mature.
In theory, small-medium enterprises (SMEs) and their internetwork security are subject to the same regulatory oversight as multinational organizations because SMEs play a major role in the economies of most countries, particularly in providing employment and alleviating poverty. In practice, however, there is likely to be a gap between SMEs and multinational organizations in cybersecurity practice. This is because SMEs are inherently constrained by a number of characteristics. First, SMEs' financial and human resources are much more limited than those of multinational organizations. For instance, if the business environment changes, especially regarding the ever-present technology changes coming onto the market, SMEs may not have readily available resources to respond to change as efficiently as multinational organizations because their resources for acquiring information about the market are limited. Second, as single-business firms, SMEs largely operate locally, although some may operate at a regional level within their respective country or trading bloc. This means that if the business environment changes, the options for SMEs are limited by the firm's resources, location, and industry, whereas multinational organizations can respond by exiting from one of its business areas. Third, SMEs tend to be at different developmental stages; the developmental stage of one SME is not necessarily representative of other SMEs.
While SMEs are subject to the same regulatory controls on cybersecurity, they are not likely to receive the same degree of attention from politicians and the public as multinational organizations, and they are also likely to be treated more leniently. One probable reason for this is when an SME fails, the effect on society is not as far-reaching as when a multinational organization fails because the number of people affected (in terms of the number of customers and the geographical coverage of the operation) is much smaller. When a multinational organization fails, the effect on society is far greater, with sometimes millions of customers being affected; therefore the public's expectations are much higher and oversight from the regulatory authority is stricter. Nevertheless, in recent years, even SMEs are moving towards investing more of their limited resources in cybersecurity because having a recognized, secure website improves sales figure and retains customers who can be confident of the internetwork system. Moreover, in recent years, internetwork safety awareness has increased within the business community, as a number of high-profile, global online breaches reported in the news media has increased interest in cybercrime prevention at management and even executive levels. In turn, SMEs have increased their budgets for cybersecurity. However, the survival of any business depends on how well it satisfies its customers' needs, which includes the expectation that a business website is easy to access with minimal barriers, such as lengthy online authentication procedures. Given that it is human nature to turn away when confronted by a barrier, an enterprise is likely to have made strategic business decisions so that it can provide its customers with ease of access to its online store, which in some cases involves scaling down website safety measures by removing or limiting strict authentication processes.
4 Individual Internet Security
As discussed, nobody likes barriers, and they will go to great lengths to avoid them. However, there is no law in place to coerce individuals to install antivirus software to protect them from falling victim to smartphone crime, or to be their first line of defense against spyware or Trojan horse malware being installed on their devices, including their smartphone. It is completely at the discretion of individuals whether they purchase and install antivirus software for their smartphone, even if it means suffering psychological and or financial losses should an individual become the victim of a smartphone crime. Statistically speaking, the potential for falling victim to smartphone crime is not that remote; with active Facebook users numbering 1.6 billion globally (as of Nov. 201512) and email users sending almost 300 million messages a day, there is a large pool of personal data that can be stolen. For example, perpetrators can obtain valid names and other personal data through phishing on social network sites, as Yachi Chiang explained:
[T]he privacy setting options of Facebook are difficult for users to understand. While users need to learn about user privacy options, under pressure from the privacy protection movement, Facebook has changed its privacy option models on a frequent basis, which has made the relationship between Facebook and privacy even more complicated … It seems, therefore, that there are many privacy traps on Facebook that users often ignore.13
Chiang, 2015, p. 230.
It is not clear why users ignore social networking sites' stronger privacy protection options, but there are a number of possible explanations. First, as discussed earlier, there is the rapid growth in modern technology owners and users, particularly of mobile devices and smartphones that we have witnessed in recent years, especially in Asia. Now, newer technology devices are no longer confined to being used by technology geeks in advanced science laboratories or universities; instead, it is members of the ordinary general public who purchase and use them. The late 20th century has seen hyperconsumerism combined with a clever marketing drive for modern technological devices, such as the smartphone, making these devices not only a tool for verbal communications, but also a commodity and lifestyle product. Mobile devices have become fashion trends with a very short product lifecycle with ever-extending add-on accessories, such as Bluetooth headsets. Second, as more and more new technology devices flood the marketplace, competition inevitably reduces the price of these products with each newer generation. This is especially so in Asia, not only are most of these technological devices manufactured in here, but also because this is where the majority of the world population lives. Further, as more and more consumers purchase these products, they do not necessarily understand fully what is required to protect their privacy from uninvited third parties. This problem will only grow and multiply as the number of consumers buying smart devices continues grows. The third reason is directly linked to the second one, as Nick Sulvited of Symentec outlined:
Individual [consumers of technological devices] lack of awareness of security … well over 70 percent of smart-phone breaches were largely due to lack of awareness of the individual end-users, this problem would only grow as more and more users migrate to smart-phones …14
Individual end users' lack of awareness of their smartphone security and privacy can result in a bitter aftertaste. Here is a real-life example: On Nov. 5, 2015 it was reported by Eurosport15 that a woman from Perth, Australia, expressed her delight in scooping AU$900 after backing 100-to-1 shot Prince of Penzance in the Melbourne Cup horse race by taking selfies of herself flashing the winning betting slip, which she then posted on Facebook. Her post was accompanied with the message: “Winner winner chicken dinner!!” However, her delight was short-lived, as someone soon poached the barcode from her photo on the smartphone, then cashed out the winnings at an automated machine through another smartphone.
This smartphone user did not realize that the digital photo on her Facebook is basically a 0-and-1 binary code, and that the barcode on her betting slip is valid on any smartphone. This lack of knowledge may come down to several factors. First, individual end users are currently too dependent on others laying down internetwork security for them; particularly, as discussed, end users rely on the organizations they access to provide cybersecurity, and organizations must provide this if they want individual end users to use their online shopping services. Additionally, organizations are coerced by law to do so, whereas individuals are not. However, even when individual end users want to equip their smartphones with security software, the standards of the many different products on the market are various and fragmented.
As a result, individual end users are probably not adequately armed with sufficient knowledge to choose one security product over another. Moreover, reliable security products tend to involve personal expenditure, and with the reliance on organizations providing cybersecurity, an inertia has developed, with end users tending not to purchase antivirus software for their smartphones. Second, most countries do not automatically provide public smartphone security protection awareness campaigns or education, especially in the developed economies in the West, because there is a strong belief that users should be the ones who pay, not the public. This is the sentiment, despite the fact that when smartphone breaches do occur, society as whole also pays for it in some way, whether by the cost of the police investigation or in taking measures to prevent the same breach happening again. However, in addition to the ethical and moral issues, the costs of cybercrime, including smartphone crime for individuals, organizations, and governments, are expected to increase year over year. As we have seen, there is a combination of causes for this. Not enough attention is given to cybercrime, with governments assigning it only limited resources and seeing it as a low political priority. It depends on the individual end users; the mindset they have acquired for their desktop PCs needs to change for their mobile devices, but such a skill set is slow to pick up because the knowledge isn't the same for desktop as it is for mobile. Additionally, individual smartphone users need to realize that they themselves have to take responsibility for personal security on their mobile devices, such as by purchasing reliable antivirus software.
5 Conclusion
As shown in this chapter, the multinational corporations have invested large financial and human resources to beef up their cyber and mobile security. Although a small number may not be up there yet, overall multinationals are relatively mature on cyber and mobile security, especially regarding their internal network. However, SMEs are fragmented in terms of investment in their cyber and mobile security, due to inherent financial constraints. The evidence of cyber and mobile security for individual smartphone end users is dire; as indicated by the example of the horse race winner in Perth, there is little awareness or knowledge of issues regarding smartphone mobile security and privacy. However, with the proliferation of individual and personalized portable devices, these problems will only grow and multiply. Furthermore, there is evidence to suggest that individuals are reluctant to invest money in equipping their different devices with security software, or that they are unaware of their vulnerability to uninvited third parties accessing their devices. As a result, there is clear evidence that smartphone end users are the weakest link in the mobile security chain.
Finally, the ease of access to and the affordability of developing mobile devices will inevitably fuel an explosion of new products, including the Internet of Things (IoT). In the not-too-distant future, the installed bases of these systems will reach critical mass and will offer enough penetration levels that they will attract attackers. To ensure that security and privacy are not playing catch-up to technological innovation, the cybercrime theorist, practitioner, technology vendors and manufacturers, and vertical solution providers should work to educate end users and establish best practices for using smart devices, such as ISO 27001 Information Technology Management. Alternatively, security controls should be built into the mobile device architecture by default, where appropriate, thereby reducing smart device breaches and crime, thus reducing the costs borne by society as a whole and those sustained by individual end users.