How Cyber-Savvy are Older Mobile Device Users?
C. Chia*; K.-K.R. Choo†,‡; D. Fehrenbacher§ * University of Melbourne, Melbourne, VIC, Australia
† University of Texas at San Antonio, San Antonio, TX, United States
‡ University of South Australia, Adelaide, SA, Australia
§ Monash University, Melbourne, VIC, Australia
Abstract
Singapore has one of the highest mobile device penetration rates in Asia, as well as one of the fastest aging populations in the region. Mobile users aged 45 and above grew up in an era when information and communication technologies were not as advanced and English language education was scarce. Considering these factors, this group is less likely to be conscious of mobile security. Our survey of 55 elderly participants suggested that most of them are generally unaware of security and privacy risks associated with the mobile device usage. Thus, we make recommendations for this user group with the aim of reducing cybercrime victimization using the Situational Crime Prevention Theory. Our findings underscore the need for regular ongoing cybercrime educational programs and the promotion of a culture of security among older digital immigrants.
Keywords
Cybersafety; Mobile safety; Older people and technology; Situational Crime Prevention Theory
Acknowledgments
We would like to thank Mr. Zhuang Haining, who had approached the participants about their responses on smart mobile devices on our behalf, and Mr. Seet Chong Boon for helping to recruit participants for this survey.
1 Introduction
Digital literacy can be defined as the “practices involved in reading, writing, and exchanging information in online environments” (Selfe and Hawisher, 2004, p. 2), such as smart mobile devices (e.g., smartphones and tablets). Singapore has one of the highest smart mobile device penetration rates in Asia, where the ratio of mobile devices to residents was 1.48 to 1 in the calendar year 2014 (Infocomm Development of Singapore, 2015). However, older users are likely to be less digitally literate compared to the younger groups for a variety of reasons. The older age group (defined as age 45 and above in this chapter) grew up in an era when mobile devices and later smart mobile device technology was still nonexistent or developing at a slow pace. These people are sometimes known as “digital immigrants.” It is even regarded as an “aging infrastructure” because digital immigrants refuse or are reluctant to incorporate technology in their everyday lives. By contrast, “digital natives” grew up in an era when computers and later smart mobile devices “are not technology, they are part of life” (Fieldhouse and Nicholas, 2008).
In the past, the digital divide between digital natives and digital immigrants may be more physical; that is, the ownership of digital gadgets by the former while there is little or no ownership of such gadgets by the latter. However, given the high smart mobile device ownership of digital immigrants, the current and possibly future digital divide may exist in terms of perception and awareness of digital literacy. Hence, there is a need to enhance the digital literacy of digital immigrants.
It is hoped that this study can provide some useful suggestions to digital immigrants in other societies that have a prominent aging population and are increasingly digitized.
Even though there are comparable similarities with increasingly digitized societies as mentioned earlier, it is important to know some characteristics in Singapore that may have an impact on the digital literacy of digital immigrants. English is the official language in multiethnic Singapore. However, the wide usage of English does not mean that everyone is literate in the language. Considering the relatively large proportion of ethnic Chinese population in Singapore of 74.2%, there is still a considerable number of people who are literate only in a single non-English language. In 2010, 20.6% of the population was literate in Chinese only, with the highest proportion coming from those aged between 45 and 64 years. This has served one of the main reasons for setting the age criteria of our participants; that is, 45 years and above. The literacy in Chinese only among the population in Singapore is also most concentrated among those who have never received any qualification numbering a total of 199,063. This is followed by those who received primary education numbering a total of 94,279 (Singapore Department of Statistics, 2010). (Note: the Census of Population is conducted once every 10 years.)
Given that the official working language is in English, this may indicate that those who are literate in Chinese only may have difficulty accessing official documents that are mostly available in English only. With the lack of command in English among some Singaporeans, they may not be able to understand the cybersecurity issues covered on this website.
1.1 Contributions
In this chapter, we build on the work of Imgraben et al. (2014) and seek to contribute to a better understanding of the security and privacy risks faced by elderly Singaporean Chinese smart mobile device users, particularly those who are literate in Chinese only. More specifically, we provide a snapshot of the following:
1. Prevalence and types of smart mobile device usage by these elderly users
2. Prevalence, nature, costs, and impacts of smart mobile device-related security incidents.
This survey provides a good indication of the risks associated with smart mobile device usage and also serves as the basis for an extended study of this population.
This survey focuses on examining the level of literacy as a variable to find out if users have difficulty using their smart mobile devices due to their lack of ability to read English. This is, to the best of our knowledge, the first (academic) study to examine how the lack of English literacy among the elderly will affect the ease of smart mobile device usage and their awareness of cyberthreats. Previous studies such as those of Kurniawan (2008) and Elliot et al. (2013) focus on the digital literacy and technology uptake of the elderly.
We then explain how the Situational Crime Prevention Theory can be used to mitigate risks by reducing the opportunities for criminal activities targeting mobile device users to occur, making cybercrime more difficult to commit by increasing perceived effort, increasing perceived risks, reducing rewards, removing excuses, and reducing provocations.
1.2 Chapter Outline
The rest of this chapter is organized as follows: We document the survey design in Section 2. In Section 3, we discuss our findings and outline four recommendations. Educational programs are important components when dealing with the risks of cybercrime. Therefore, in Section 4, we explain the role of criminological theories, and more specifically, the Situational Crime Prevention Theory that can help to inform and enhance cybercrime prevention strategies. Section 5 concludes the chapter and looks at future work to take forward this chapter/survey's analysis and conclusions.
2 Survey Design
The survey comprises five main sections, each representing the main threats that users of mobile devices are generally exposed to: (1) general security, (2) malware, (3) unauthorized access, (4) Wi-Fi and Bluetooth security, and (5) phishing. The questions relate to the 2012–13 financial year (i.e., Jul. 1, 2012 to Jun. 30, 2013), unless otherwise specified.
This study is based on convenient sampling because it allows us to obtain basic data and trends, particularly on how literacy in Chinese affects cybersecurity awareness, which has not been studied in the past. We will follow up with randomized sample comprising a wider group in the future.
Initial contacts with participants were made through email, Facebook, and WhatsApp. Some of the contacts were also made through friends who would relate the survey to their parents and/or seniors with whom they have contact. A typical limitation of this approach is self-selection bias, as the participants are unlikely to represent the entire target population.
Participants were selected based on their age and smart mobile device ownership. The selection process had to go through a number of factors, including willingness to participate in the survey (both online versions and hard copies of the survey form were made available), whether participants use smart mobile devices as a feature phone (for calling and text-messaging only), and the request to participate in surveys was set in Chinese, as some participants were unable to do them in English.
The initial intention to include Singaporeans of all ethnic groups had to be dropped because of the request to provide surveys conducted in non-English mediums due to the inability of the researchers to draft the survey in mediums (i.e., Tamil and Malay) other than Chinese and English. This inability to read English was also one of the motivating factors in this study to further examine how users who read little or no English respond to their use of smart mobile devices.
Analysis of data is based on 55 participants comprised of 28 males and 27 females. The age of participants are 45 years and above, with the highest number coming from the age group 51 to 55; see Fig. 1.
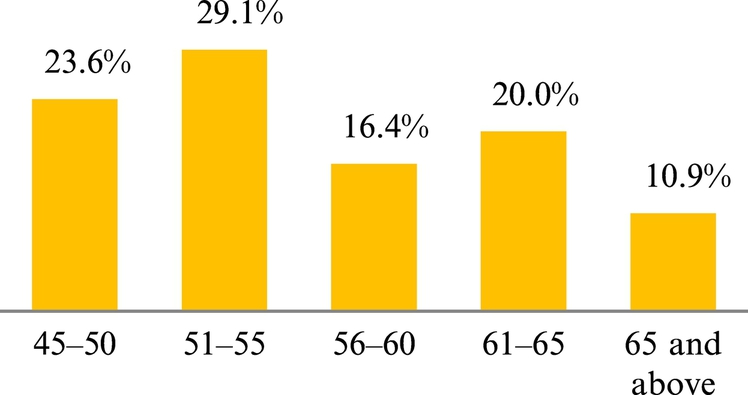
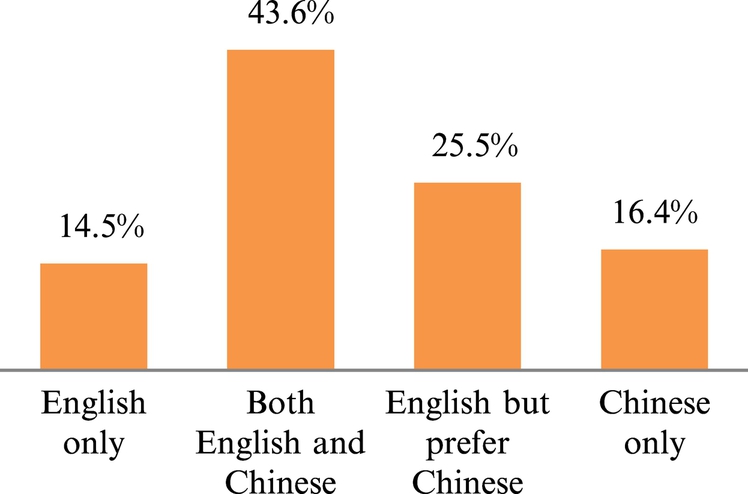
The educational level of participants ranges from primary to university level, with the exception of one who had never received any education. The literacy level of participants ranges from being literate in English only, Chinese only, both Chinese and English, and English but prefer Chinese; see Fig. 2.
In addition to the survey, the study also includes feedback through phone interviews and emails from participants during the process of collecting survey responses. There were also those who explained why they could not do the survey. This feedback can serve as an additional source of reference in understanding the attitude of users towards smart mobile devices.
This study had gathered 23 participants who either know little or no English or prefer to access their smart mobile devices in Chinese. Findings from this study indicate that the lack of literacy in English is directly related to the ease of usage and the user's awareness of cyberthreats.
To test on the ease of usage, a few factors were considered during the design of the survey. This includes asking participants whether they experience difficulty using their smart mobile devices with or without the change of language settings and their awareness of phishing.
3 Findings and Discussion
Although literacy is one of the variables focused in this study, we will also present findings on the main threats to which elderly users of smart mobile devices are generally exposed. These findings are analyzed from the 55 participants who had participated in the survey, which cover five sections as mentioned in the survey design. This will be presented in Tables 1 and 2.
Table 1
Participants' Responses on General Security (n = 55)
| Questions on General Security | Participants' Responses |
| Do you use the “Remember me” feature to save your passwords, login credentials, or credit card information? (Select all that are applicable) | Of the seven participants who reportedly saved the passwords, two also saved login credentials. |
| Do you use any encryption software to protect information on your mobile device? | Although four responded “yes,” it is doubtful if participants knew what encryption software is and more likely that they were referring to the password on their devices. |
| Have you “jail broken” or “rooted” your mobile device (s) before? | Only one responded “yes.” |
Table 2
Participants' Responses on Loss/Theft (n = 55)
| Questions on Loss/Theft | Participants' Responses |
| In the past calendar year (01/01/2013 to 31/12/2013) has/have your mobile device(s) been lost or stolen? | Only two responded “yes.” |
18 of the 55 participants (~ 32.7%) reportedly experienced difficulty in understanding the information while accessing their smart mobile devices. Of these 18 participants, 15 participants are literate in Chinese only, and five of the participants are literate in both Chinese and English but prefer to access their smart mobile devices in Chinese (e.g., changed the language settings of their devices to Chinese); see Table 3.
Table 3
Participants' Responses on Unauthorized Access (n = 55)
| Questions on Unauthorized Access | Participants' Responses |
| How likely are you to read up on information before you download an application? | See Fig. 3. |
| Have you installed any applications from nonreputable or unknown application providers? | Four responded “yes” and five responded “not sure” |
| In the past calendar year (01/01/2013 to 31/12/2013) has your mobile device(s) been accessed without your permission? | Three responded “do not know” (n = 54). |
The lack of English literacy, or that the level of comfort lies more with the Chinese language, indicates that the users may not be able to either understand all or most of the features available on smart mobile devices, such as instant messaging, emails, and information on websites or social networking sites. Such information is usually not translated into Chinese even if the user sets language settings to Chinese.
65.5% (36) of the participants are literate in both English and Chinese, but nine of them preferred to do the survey in Chinese (a total of 15 participants completed the survey in Chinese). This reflects that their level of comfort in reading lies more with Chinese. Users also responded that they have had difficulty accessing their smart mobile devices even after changing language settings.
First, we look at the 23 users who are either literate in mainly Chinese or regard Chinese as their preferred medium. Of those, 69.6% (16) have changed their language settings to Chinese. Among these 16 users, 68.8% (11) still experience difficulty in understanding information on their devices, and 9 out of these 11 users still experience difficulty understanding information after changing language settings.
Among these difficulties that the 11 users experience, the highest response came from understanding instructions while downloading mobile applications (81%). One user also reported having difficulty understanding messages prompted while playing online games and accessing social networking sites and requests to play games and join social network by friends and unknown contacts, as well as having a fear of leaking sensitive and personal identifiable information (PII) data such as bank account, credit card details, or personal photos/videos.
The two remaining users, who did not have problems understanding instructions while downloading apps, reported to have experienced difficulty in understanding advertisements and requests to play games and join social networks by friends and unknown contacts, as well as a fear of leaking sensitive data and PII.
The problem of understanding the information on their mobile devices is not unique to users who are mainly literate or feel more comfortable accessing in Chinese only.
However, the problem lies less with understanding and probably more with not being sure how to respond, as well as the possible consequences of responding. This is an indication that as features of smart mobile devices increase in function and variety in the form of new apps and device functions, digital immigrants who make use of these features may experience more difficulty in accessing their devices.
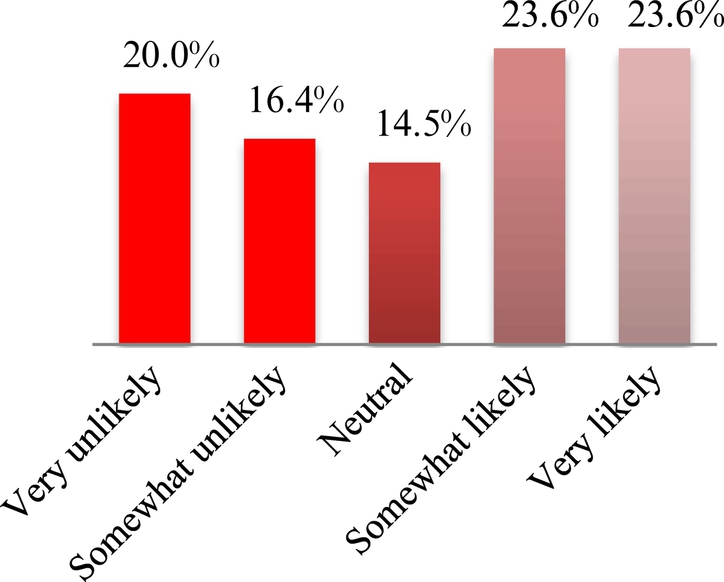
Understanding the information of the various features on their smart mobile devices may be difficult for those who are not accustomed to reading in English. It may also deter them from reading up before downloading an app. More importantly, participants may be unaware of the retrieval of sensitive data and PII upon downloading an app. 38.2% (21) of the participants responded that they are unlikely to read up on information before downloading an app. Of these 21 participants, 52.4% (11) responded “very unlikely” and nine participants responded “somewhat unlikely” (Fig. 3). Eight other participants responded “neutral” to reading up before an app is downloaded.
Other than the lack of awareness that downloading apps may retrieve sensitive data and PII from the user, four participants reportedly installed apps from nonreputable or unknown application providers (e.g., third-party app stores). There are five other participants who were “not sure” whether their apps were installed from nonreputable or unknown providers.
A study conducted by Hewlett Packard Security Research (2013), for example, revealed that 90% of the 2107 mobile apps examined were vulnerable to attacks, 97% accessed sensitive data and PII, and 86% had privacy-related risks. Lack of binary code protection was identified as a potential vulnerability affecting 86% of the apps examined. Another major vulnerability was weak or inappropriate implementation of cryptographic schemes to secure sensitive data stored by the apps on mobile devices, which was revealed in 75% of the apps examined. A study by D'Orazio and Choo (2015) revealed that due to the inappropriate implementation of cryptographic algorithm and the storage of sensitive data and PII in an unencrypted database in a widely used Australian government health care app, users' sensitive data and PII stored on the device could be compromised by an attacker. In another related work, the authors also revealed vulnerabilities in four video on-demand apps, one live TV app, and a security DRM protection module (D'Orazio and Choo, 2016).
The lack of understanding app information, coupled with a low likelihood of reading up on information before downloading and installing apps from nonreputable or unknown app providers, may put these users at risk of revealing their personal information. This is an indication that awareness needs to be increased in these areas.
Linking the above concerns about the lack of understanding of app information and the low likelihood of reading up on information before downloading an app, we also draw our attention to the type of smart mobile device the participants own.
Thirty-five out of the 55 (63.6%) participants own an Android device. The permission-based method utilized by Android to determine an app's legitimacy has been shown to be insufficient at classifying malicious apps reliably. On the other hand, the review process used by Apple is more restrictive for developers, as each app is thoroughly analyzed for security issues before being released to the public (although there have been reports of potentially malicious apps getting past Apple's reviewers).
Some participants in our study have expressed concern with encountering advertisements while using the app they have downloaded. This may indicate in-app advertising, which is commonly seen in apps. The increase of permissions is predicted to be related to in-app advertising that requires use of additional resources for data mining (Shekhar et al., 2012). A 2012 study of 100,000 Android apps revealed that some mobile advertising libraries used by apps resulted in the direct exposure of personal information, and some advertisement libraries result in unsafe fetching and loading of dynamic code from the Internet. For example, five out of the 100 identified ad libraries had the unsafe practice of downloading suspicious payloads, which allowed the host app to be remotely controlled (Grace et al., 2012).
In addition, an Android device user must choose either to accept all permissions required by the app in order to download or cancel the installation. Some of these permissions may not be necessary, and granting all permissions may pose a privacy risk to Android users. For example, in a 2014 study, seven Android social networking apps were examined (Do et al., 2014). It was discovered that the Facebook app requires the “read contacts” permission, which means retrieving users' contact data including contact numbers, contact addresses, and email addresses, regarded as unnecessary. Both Facebook and Tango require permission to “read phone state” that includes allowing the app to access the device's phone number, the international mobile equipment identifier (IMEI) of the device. As the IMEI serves as a unique identifier that is often used to locate the device, providing such information may be disadvantageous to the user.
56.4% (31) of the participants in our study reported using the Facebook app and 20 out of the 31 participants (64.5%) have used the app on their Android devices. Nine out of the 20 participants who used the Facebook app on their Android devices are mainly literate in Chinese. Given their lack of understanding the information when downloading an app, these participants may be put at risk of granting more than the necessary permissions.
If this need for permissions when downloading apps in Android devices is linked to a lack of understanding of information (in English) on apps and the low likelihood of reading up on information before downloading an app, as seen with our participants, people may be exposed to a higher risk of revealing their sensitive data and PII without being aware of doing so.
Leaving your belongings unattended in a public place or work environment that may be temporarily out of your sight may be a risky thing to do, especially when the smart mobile device contains a lot of sensitive data and PII about the user, such as photos, login details for the apps installed, corporate and personal emails, and other messages with people you know.
Even though most participants responded “very unlikely” and “somewhat unlikely,” there are still 10.9% of the participants who responded “very likely” (3) and “somewhat likely” (3). The likelihood of half of these participants leaving their smart mobile devices unattended in a public place or work environment may be related to the nature of their work, such as working in an outdoor environment that requires them to travel from place to place, and so the tendency of leaving their belongings unattended is high. Three of these participants, for example, are in the theatrical trade.
Users working in such environments have to be more wary of leaving their smart mobile devices unattended. If leaving a smart mobile device unattended is risky, not having password protection for your device or not knowing if your device has been accessed without your permission may further increase the risk. Among the six participants who are likely to leave their smart mobile devices unattended, half of them do not use a password or PIN to lock their devices. Although most of the other participants responded that their likelihood of leaving their devices unattended is low, 43.6% (24) of them do not lock their mobile devices. Three participants reported that they are “not sure” if their devices have been accessed without their permission.
Unauthorized access of smart mobile devices is a serious threat for any organization whose employees store sensitive data and/or credentials on their smart mobile devices. It should by now be common knowledge that leaving a device unattended, especially if no locking mechanism is in place, exposes any personal and corporate data stored on the device. Even if data has been deleted from the device, it could still potentially be retrieved using open-source and commercial forensic software (e.g. Micro Systemation XRY and CelleBrite UFED Kit) (Tassone et al., 2013; Quick et al., 2013).
While Internet access via smart mobile devices is easily accessible today, connecting to public Wi-Fi networks may put the user at risk of revealing sensitive data and PII. Using Wi-Fi hotspots, a hacker in the local area network may steal such information by replicating the legitimate provider's login or registration webpage. Four of our participants responded “yes” and 10 responded “depends” when asked if they would connect to unknown Wi-Fi networks (see Table 4).
Table 4
Participants' Responses on Wifi and Bluetooth Security (n = 55)
| Questions on Wifi and Bluetooth Security | Participants' Responses |
| Do you keep your mobile device(s)'s Wi-Fi switched on at all times? | 27 (49.1%) responded “yes” |
| Would you connect to unknown Wi-Fi networks? | Four responded “yes” and 10 responded “depends” |
| Do you keep your mobile device(s)'s Bluetooth switched on at all times? | Five responded “yes” |
| Would you accept a Bluetooth pairing request from unknown sources? | Three responded “depends” |
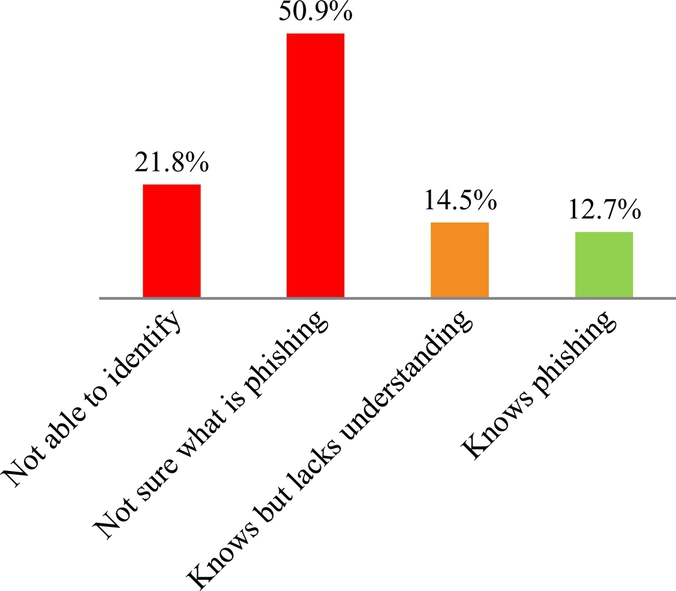
This study also aims to test participant's awareness of phishing. Our findings suggested that a high proportion of the participants are unaware of phishing; see Fig. 4.
This trend stretches across all age groups and educational levels. However, the sample may be biased in finding out if literacy mainly in Chinese may affect users' perception of phishing due to the difficulty in gathering such participants.
87.3% (48) of the participants are either unaware or do not have a sufficient understanding of phishing. Eight of the fifteen participants who said that they know what phishing is fail to identify some of the phishing examples set out in the survey, and 23 participants will perform one or more of the following actions:
• Open SMS from unknown contact (20)
• Open email (7)
• Access instant messaging request (Facebook, MSN) (2)
Table 5 illustrates the questions on phishing, and Tables 6 and 7 illustrate the 10 phishing examples set out in the survey and the participants' responses. There are five examples set in Chinese for participants who are literate mainly in Chinese, while the remaining five examples are the same with the English survey. This is to test the responses of participants who are mainly literate in Chinese on whether they will access without asking for advice, ignore it, or ask for advice from family/friends. Figures marked in bold indicate the number of participants who are aware of what phishing is.
Table 5
Participants' Responses on Phishing (n = 55)
| Questions on Phishing | Participants' Responses |
| Will you access the following from an unknown contact? | 23 participants will access one or more of the following: Open SMS from unknown contact, open email, or access instant messaging request (Facebook, MSN) |
| Will you be able to detect phishing scams received on your mobile device? | See Fig. 4. |
Table 6
Responses on Phishing for English Survey
| Phishing Examples | Responses | ||
| P | L | N | |
| Local bank phishing email (n = 39) | 18 | 5 | 16 |
| Bank update SMS phishing (n = 39) | 21 | 3 | 15 |
| Permission allowing app to messages, personal information, network (n = 38)a | 17 | 8 | 13 |
| eBay phishing email (n = 39)b | 20 | 4 | 15 |
| Facebook phishing email (n = 40) | 16 | 4 | 20 |
| Amazon phishing email (n = 40) | 19 | 1 | 20 |
| PayPal phishing email (n = 40) | 21 | 5 | 14 |
| Facebook request (n = 40) | 34 | 0 | 6 |
| Facebook phishing email (n = 40) | 16 | 4 | 19 |
| Bank phishing email (n = 40) | 21 | 5 | 14 |
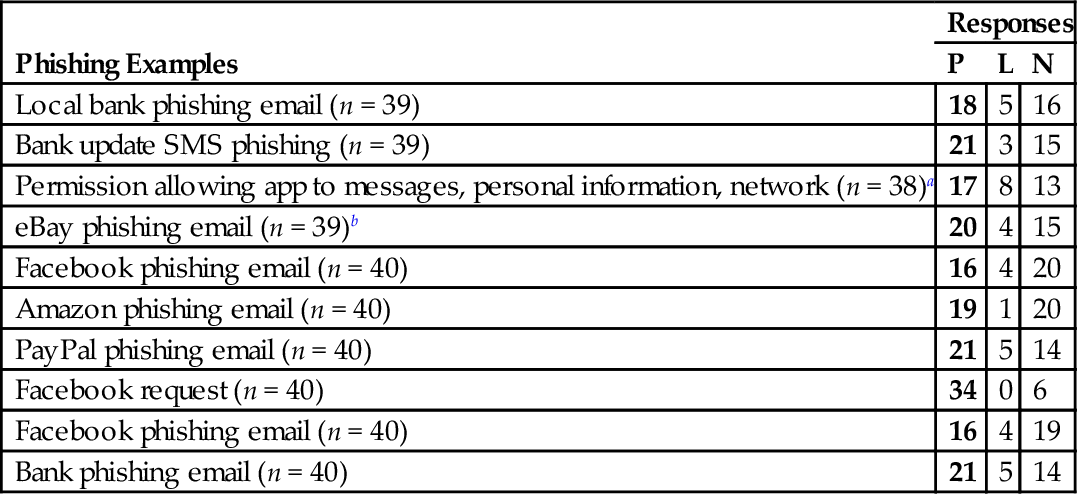
P, phishing; L, legitimate; N, not sure.
a The example here pertains to app permission. Participants will reply “yes,” “no,” or “not sure” to whether they feel this permission is necessary. The “no” option is counted under the “phishing/yes” column to imply participants' awareness that this requirement is unnecessary.
b The example question asks whether the email is legitimate, hence the “no” option will be categorized under the “phishing/yes” column to imply participants' awareness that this email is not legitimate.
Table 7
Responses on Phishing for Chinese Survey
| Phishing Examples (n = 15) | Responses | ||
| P | L | N | |
| QQ phishing email | 9 | 1 | 5 |
| Reply to WeChat SMS phishing | 14 | 0 | 1 |
| Phishing email requesting login | 14 | 1 | 0 |
| Permission allowing app to messages, personal information, network | 12 | 1 | 2 |
| Phishing alert on downloading free antivirus software | 12 | 0 | 3 |
| English phishing examples | I | W | S |
| Local bank phishing email | 8 | 0 | 7 |
| PayPal phishing email | 11 | 0 | 4 |
| eBay phishing email | 12 | 0 | 3 |
| Facebook request | 14 | 0 | 1 |
| Facebook phishing email | 11 | 1 | 3 |
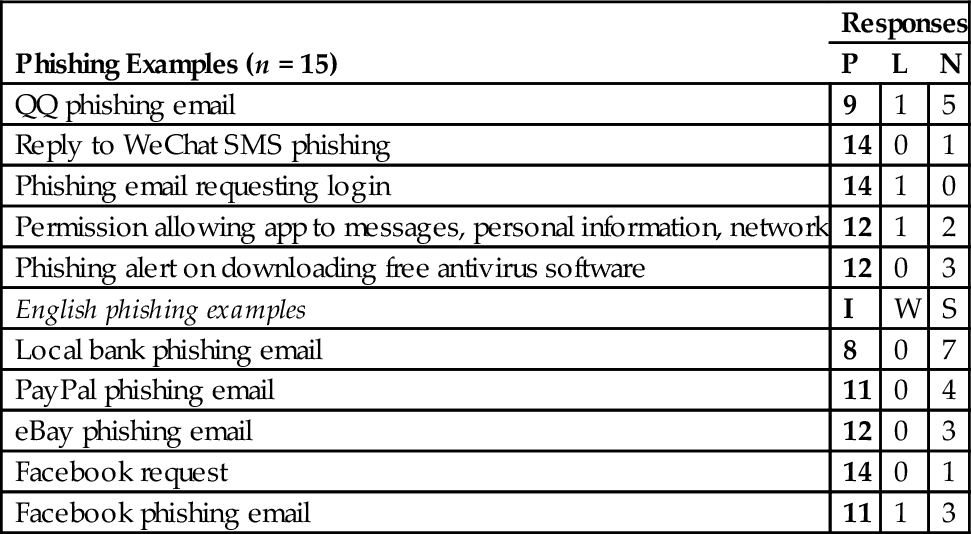
P, phishing; L, legitimate; N, not sure; I, ignore; W, will access; S, seek advice.
We tested the correlation of phishing with variables like age and educational level. Out of the seven participants who are able to recognize all the phishing examples, six have university education and one graduated with college education. The age group is also more concentrated in the 45–50 age group (4), followed by 51–55 (2) and 56–60 (1). One participant prefers to read in Chinese. However, as the number of participants who are able to identify phishing is small, more tests will need to be conducted on a larger scale for more conclusive results.
A recent research indicates that by 2017, over 1 billion users globally will use their smart mobile devices for banking purposes. Cybercrime is heading towards the “post-PC” era, which is the era of smart mobile devices. It is important to note that the term “phishing” may be unfamiliar to some but other users may have some understanding of the concept of phishing; that is, emails or websites that pretend to be from a trustworthy entity.
Other than responses from the survey, this study has also compiled some feedback from participants and other elderly smart mobile device users whom we have approached but did not participate in the survey.
One user, who did not participate in the survey, responded that he has “technology phobia” and he only knows a few features on the phone such as calling, messaging, and photos, which are mainly the functions of a feature phone. The user occasionally accesses Facebook using both his mobile device and computer.
Most of the users are unsure of how to use features, such as surfing the Internet, playing online games, and social networking. An important factor that obstructed their use of smart mobile devices is the use of the touch-screen feature, as they often face the difficulty of motor and sensory motions like the synthesis of timing to swipe or touch features of the smart mobile device.
As digital immigrants, these seniors may have a longer contact with feature phones than smartphones, so they need time to use the latter more effectively. It is worth noting that a Singapore company manufactures iNo Mobile, an elderly-friendly mobile phone with some models that support smart mobile device features (Dyeo et al., 2010). However, none of our participants own such a mobile device.
4 A Situational Crime Prevention Approach
A typical crime prevention intervention is to create conditions that are unfavorable for crime. For example, the routine activity theory is a popular theory used to explain criminal events. The theory proposes that crime occurs when a suitable target is in the presence of a motivated offender and is without a capable guardian (Cohen and Felson, 1979). Offender motivation is a crucial element in the theory, which draws on rational exploitation of “opportunity” in the context of the regularity of human conduct to design prevention strategies, especially where terrestrial interventions are possible. Criminals are assumed to be rational and appropriately resourced actors operating in the context of high-value, attractive targets protected by weak guardians (Felson, 1998; Yar, 2005), and that victimization risk is a function of how one victim patterns their behavior and lifestyle (Imgraben et al., 2014). For example, a password-protected device may be of little use to an opportunistic thief.
The interaction between smart mobile device users, cybercriminals who are financially motivated, and situational conditions e.g., opportunities and weak guardianship has great influence on the situation. For example, how easy is it to design malware and phishing websites targeting older smart mobile device users who may not be as IT literate and cyber-savvy and what is the risk of getting caught and prosecuted in a court of law?
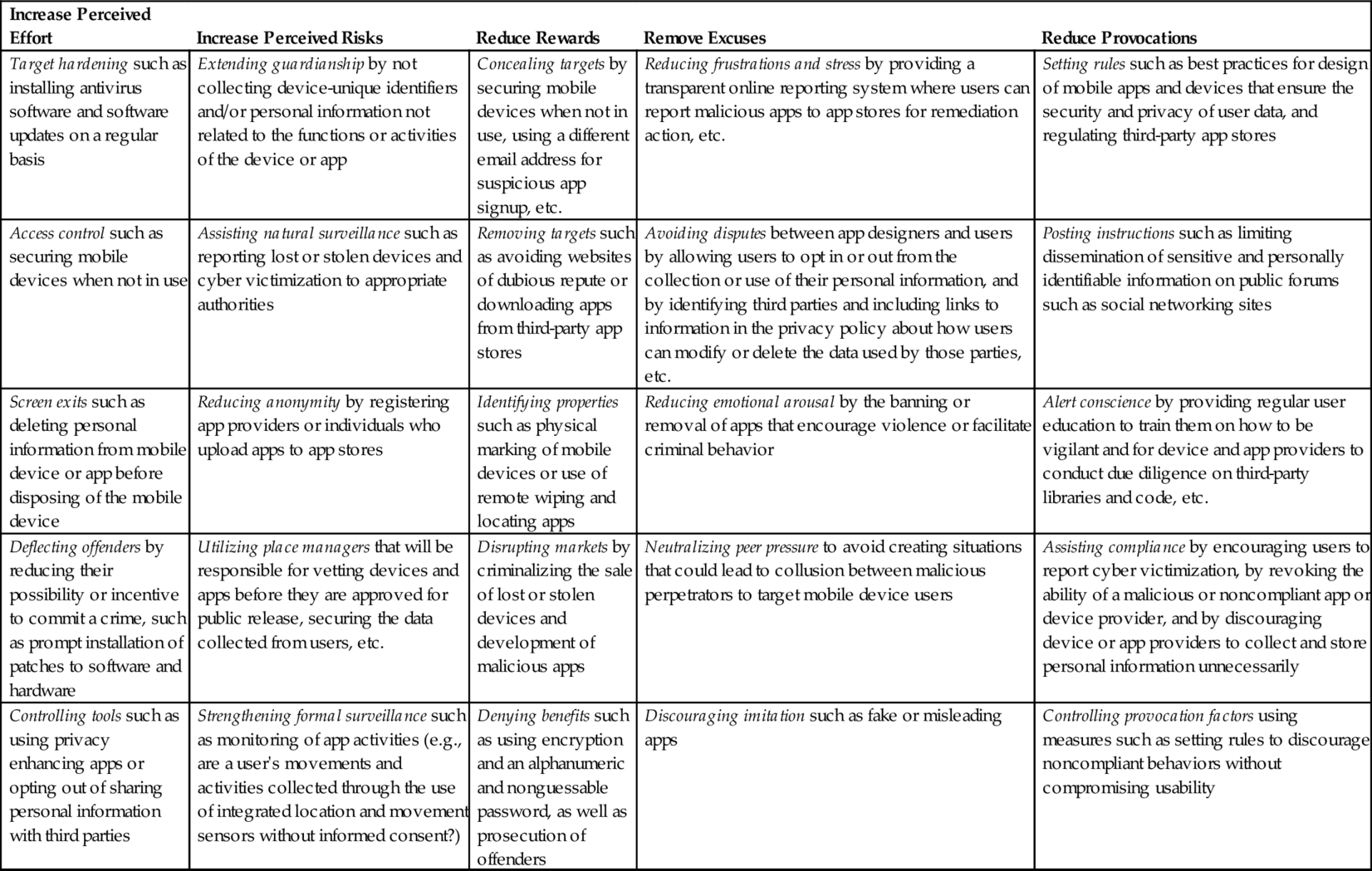
Therefore we should examine ways of creating conditions unfavorable for crime. For example, according to the Situational Crime Prevention Theory (Clarke, 1997; Cornish and Clarke, 2003), the five broad categories (comprising 25 techniques) to reduce crime targeting mobile users are:
1. Increasing perceived effort: Target hardening, controlling access to facilities, screen exits, deflecting offenders, and controlling tools/weapons
2. Increasing perceived risks: Extending guardianship, assisting natural surveillance, reducing anonymity, utilizing place managers, and strengthening formal surveillance
3. Reducing rewards: Concealing targets, removing targets, identifying properties, disrupting markets, and denying benefits
4. Removing excuses: Reducing frustrations and stress, avoiding disputes, reducing emotional arousal, neutralizing peer pressure, and discouraging imitation
5. Reducing provocations: Setting rules, posting instructions, alerting conscience, assisting compliance, and controlling drugs and alcohol (which we will replace with “provocation factors”)
Measures that users, mobile device and app designers, app store operators, and government agencies can undertake to ensure a secure mobile environment are outlined in Table 8.
Table 8
Cybersafety Practices Based on Situational Crime Prevention Theory
| Increase Perceived Effort | Increase Perceived Risks | Reduce Rewards | Remove Excuses | Reduce Provocations |
| Target hardening such as installing antivirus software and software updates on a regular basis | Extending guardianship by not collecting device-unique identifiers and/or personal information not related to the functions or activities of the device or app | Concealing targets by securing mobile devices when not in use, using a different email address for suspicious app signup, etc. | Reducing frustrations and stress by providing a transparent online reporting system where users can report malicious apps to app stores for remediation action, etc. | Setting rules such as best practices for design of mobile apps and devices that ensure the security and privacy of user data, and regulating third-party app stores |
| Access control such as securing mobile devices when not in use | Assisting natural surveillance such as reporting lost or stolen devices and cyber victimization to appropriate authorities | Removing targets such as avoiding websites of dubious repute or downloading apps from third-party app stores | Avoiding disputes between app designers and users by allowing users to opt in or out from the collection or use of their personal information, and by identifying third parties and including links to information in the privacy policy about how users can modify or delete the data used by those parties, etc. | Posting instructions such as limiting dissemination of sensitive and personally identifiable information on public forums such as social networking sites |
| Screen exits such as deleting personal information from mobile device or app before disposing of the mobile device | Reducing anonymity by registering app providers or individuals who upload apps to app stores | Identifying properties such as physical marking of mobile devices or use of remote wiping and locating apps | Reducing emotional arousal by the banning or removal of apps that encourage violence or facilitate criminal behavior | Alert conscience by providing regular user education to train them on how to be vigilant and for device and app providers to conduct due diligence on third-party libraries and code, etc. |
| Deflecting offenders by reducing their possibility or incentive to commit a crime, such as prompt installation of patches to software and hardware | Utilizing place managers that will be responsible for vetting devices and apps before they are approved for public release, securing the data collected from users, etc. | Disrupting markets by criminalizing the sale of lost or stolen devices and development of malicious apps | Neutralizing peer pressure to avoid creating situations that could lead to collusion between malicious perpetrators to target mobile device users | Assisting compliance by encouraging users to report cyber victimization, by revoking the ability of a malicious or noncompliant app or device provider, and by discouraging device or app providers to collect and store personal information unnecessarily |
| Controlling tools such as using privacy enhancing apps or opting out of sharing personal information with third parties | Strengthening formal surveillance such as monitoring of app activities (e.g., are a user's movements and activities collected through the use of integrated location and movement sensors without informed consent?) | Denying benefits such as using encryption and an alphanumeric and nonguessable password, as well as prosecution of offenders | Discouraging imitation such as fake or misleading apps | Controlling provocation factors using measures such as setting rules to discourage noncompliant behaviors without compromising usability |
The findings from this survey, as well as those in previous studies such as Imgraben et al. (2014), suggested that many elderly (and young university-educated, respectively) smart mobile device users are generally unaware of the risks that they may expose themselves to every day. More concerning, however, is that mobile device users do not appear to be sufficiently informed regarding their smart devices' usage and security. As pointed out in previous studies as well as our own study, the participants were generally unaware of the risks they subjected themselves to; for example, by leaving their Wi-Fi and Bluetooth turned on at all times, particularly those who were also likely to perform online banking (four of our participants do so) and other activities (two participants shop online) that could expose personal information to an attacker.
There is, arguably, a need for an integrated, coordinated, and concerted effort by government agencies, mobile device and app providers, and community and educational organizations (e.g., University of the Third Age; see http://www.u3aonline.org.au/) to combat the cybercriminal activities that victimize mobile device users, which can help to ensure that the most effective cybercrime prevention advice is provided to the users (Australian Government House of Representatives Standing Committee on Communications, 2010).
The success of cybercrime education programs can be mediated by a range of individual, contextual, and cultural factors. It should also be noted that education is not the only solution or the most reliable method. The broad aim of the ongoing cybercrime education should be to bring about behavioral change and increase user awareness.
Although there are various cybercrime educational initiatives in countries such as Singapore, there has been limited evaluation of these educational initiatives. The evaluation and study of such educational initiatives is important (e.g., to develop a good understanding of what works, what does not work, and why), as a badly implemented educational initiative may not result in any of the hoped-for benefits, regardless of how well-conceived the educational initiative may be.
In addition, we suggest that any educational materials developed for smart mobile device users be tailored specifically to the user group (e.g., Generation X, Generation Y, and baby boomers; as well as end users from diverse cultural and linguistic backgrounds) and end users with varying technical and literacy backgrounds.
5 Conclusion
In our study, we have discovered that some participants who know little or no English have difficulty understanding instructions of the applications installed on their smart mobile devices. Other than the language settings of the smart mobile device, which is already available in most devices, our findings have concluded that there is also a need to have flexibility in the language settings for their features. There is an urgent need to increase users' awareness about cybersafety measures.
Possible future extensions of this survey include surveying other populations of elderly users in different countries, who are literate in English or only in a single non-English language, and undertaking a targeted approach to help develop cybersafety educational materials, where small groups of older mobile device users are selected to participate in face-to-face interviews and are presented with the survey multiple times with educational materials specific to their results given after each round. The overall results can be used to show the effect that the materials have, and feedback from the participating user groups can be used to further refine the educational materials.