What risks invite attackers into the network?
What attack vectors are likely to be used?
Two important tools designed to answer these questions are the cyber risk assessment and the Cyber Attack Life Cycle developed by Mandiant. The risk assessment lays out the risks present in the environment in which cyber events are likely to occur. The Cyber Attack Life Cycle outlines the process attackers follow when seeking to breach entities and steal, modify or destroy assets.
The cyber risk assessment and analysis entails several key items. Properly analyzing risks to the entity’s digital assets requires assessing threats and vulnerabilities these threats are likely to exploit and analyzing each in terms of the likelihood of a successful attack and the impact to the entity.
Viewing these risks in terms of the Attack Life Cycle, formerly known as the Kill Chain, generates context in terms of an attack vector’s threats. Think of it like laying the Attack Life Cycle on top of the risk assessment. A threat actor exploits a vulnerability to gain an initial foothold inside the entity. Then it searches for ways to exploit other systems, increasing its privileges, until the target is reached. Prioritizing the incident response plan and associated playbooks around these scenarios enhances planning and preparation for potential incidents.
Documenting Cyber Risks
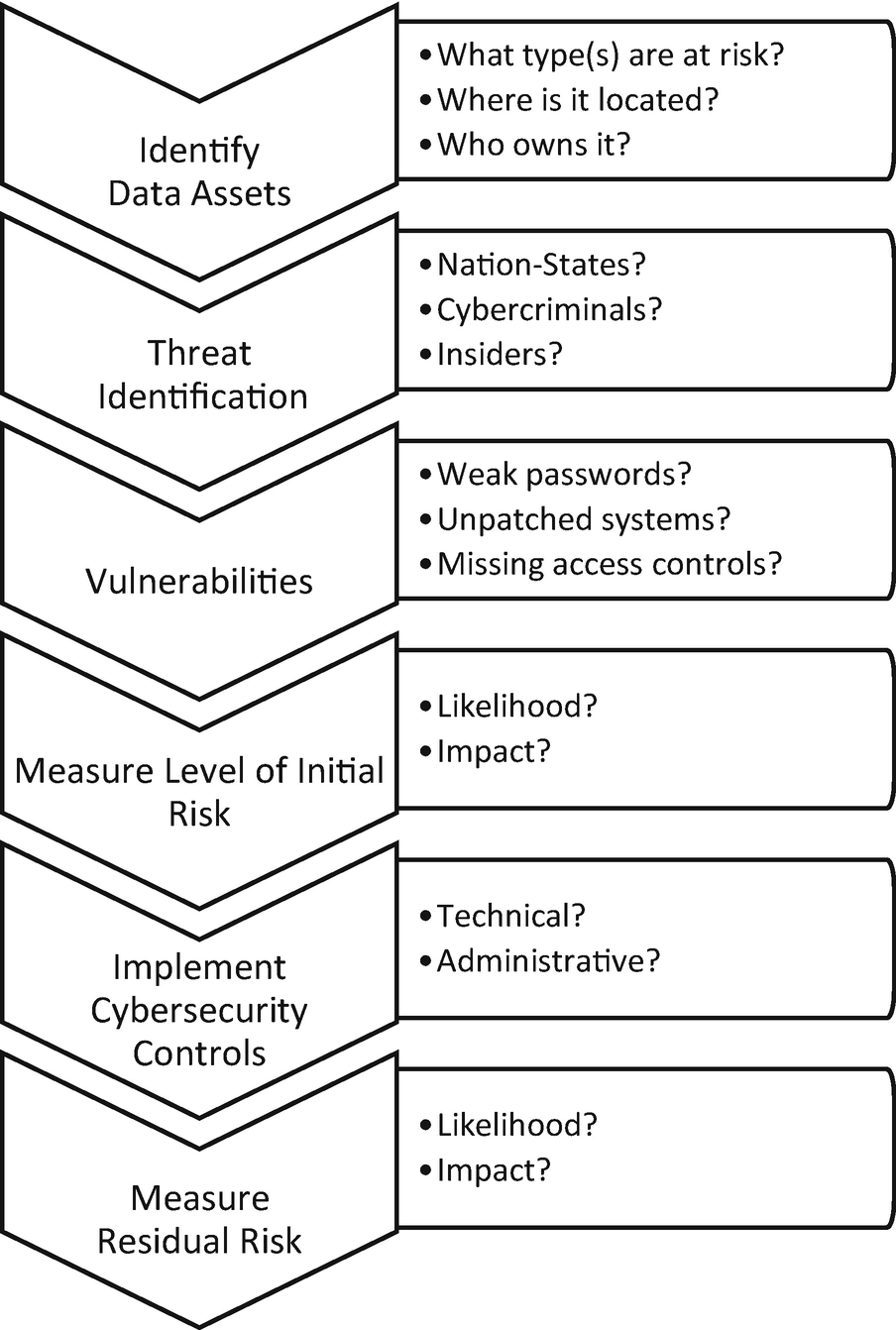
The six activities necessary to measure cybersecurity risk
Threat Analysis
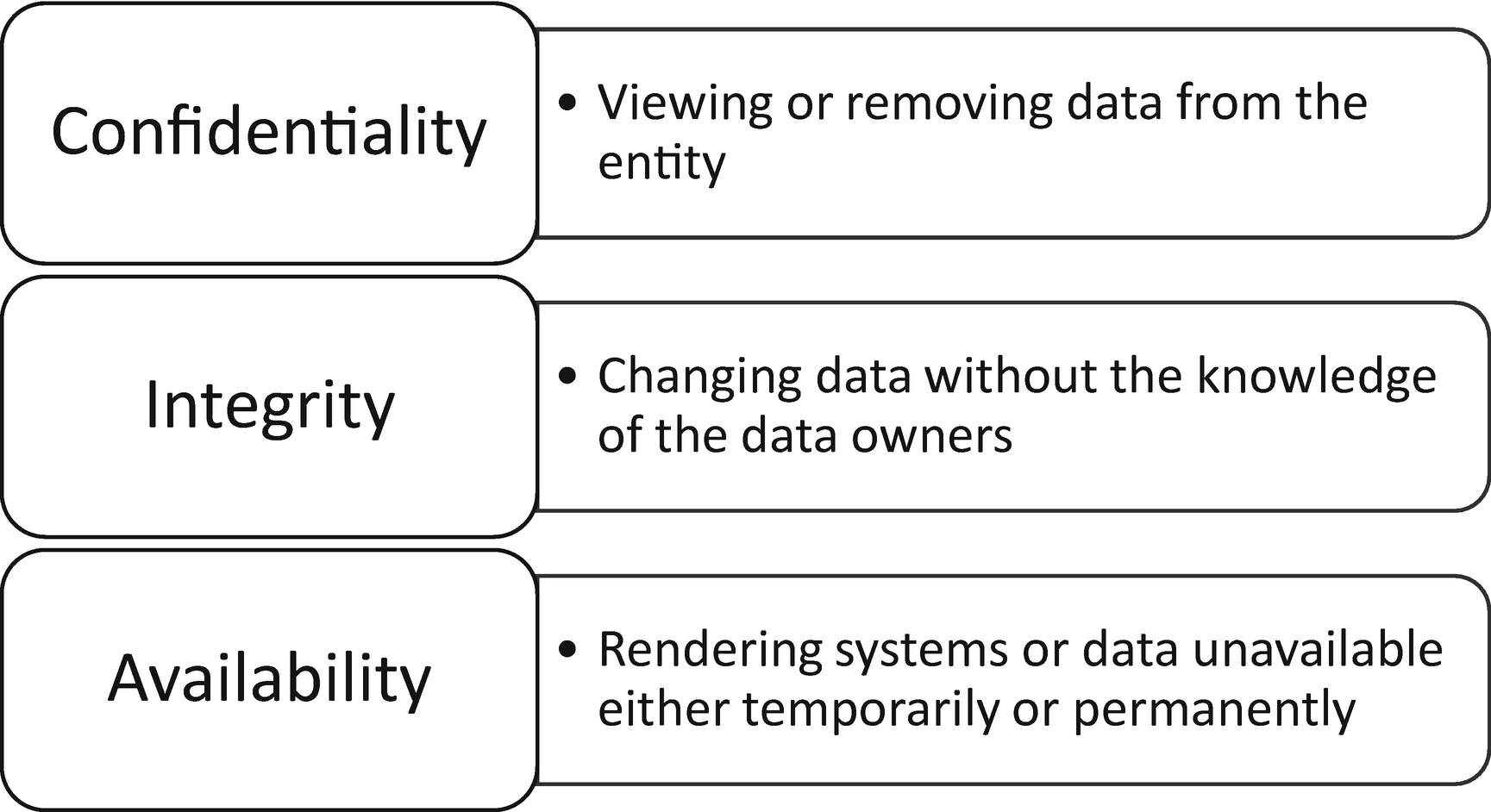
The cybersecurity triad of confidentiality, integrity, and availability
Cybersecurity attacks are targeted against one or more of the pillars shown in Figure 6-2. Attacks such as the Equifax breach target confidentiality of data. Data is viewed by unauthorized individuals, whether it remains at the entity or is removed. Attacks against data integrity result when a threat actor changes data without the data owners detecting these changes. Even when a breach is detected, these attacks are still problematic, because knowing what data changed is not always an easy task. Business operations are anchored in accurate data, so when integrity is compromised, business performance is impacted. Availability attacks include denial-of-service attacks designed to crash servers and other network devices. When networks are rendered unavailable, revenue and contractual obligations might be at risk. Ransomware is another type of availability attack. These are common and are reported in the news several times a year. These attempts succeed when attackers successfully exploit end users who inadvertently launch malware designed to encrypt databases and other important repositories. Attackers expect victim entities to pay ransom to get the data unlocked. If the ransom is not paid, attackers threaten to destroy the data. It is important to know that backups with integrity exist and are ready for restoration purposes; otherwise, target organizations have limited options.
The last example of availability threats is included in business continuity and disaster recovery plans. Events such as floods, earthquakes, and terrorist attacks cause disruptions in business operations and force recovery of IT operations to backup sites.
Threat actors and scenarios cause incidents ranging in classification from nuisance to detrimental. In severe cases, threats cause the loss of significant revenue over a period of years.
How Vulnerabilities Become Risks
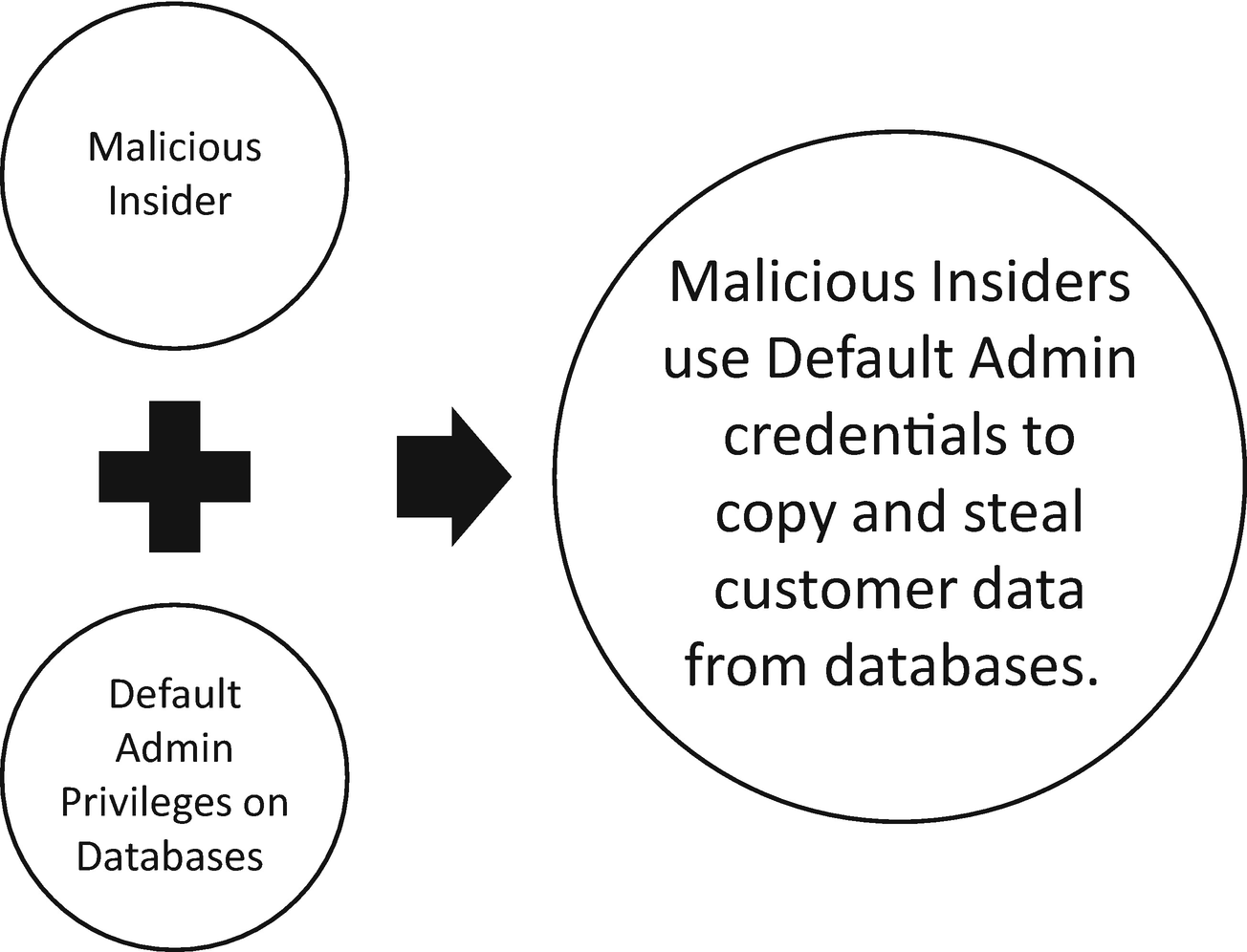
A threat actor, in this case a malicious insider, exploits a vulnerability —default admin credentials—creating a risk to the confidentiality, integrity, or availability of customer data
Once these relationships are identified and established, the seriousness of each risk is measured.
Measuring Risk Severity
Risk is measured using two parameters: likelihood the risk will be exploited and impact to the entity if exploited. Each has its own considerations for measurement.
Likelihood
How well known is the vulnerability publicly?
What are the odds that the threat actors know about and can find the vulnerability in the organizations environment?
What special skills or resources are required to successfully administer the exploit?
Is the vulnerability worth the effort?
These questions are used to understand and measure vulnerabilities in terms of likelihood. Without significant statistical data and actuarial tools, likelihood can be subjective. These types of risk assessment are known as qualitative. Analysis used to develop risk measurement does not use statistical measurements. Using such tools allows the risk assessment to be quantitative. Where possible, a blend of the two types yields results in which the benefits outweigh the costs. Both qualitative and quantitative risk assessments use a scale of one to five, five indicating that the vulnerability has a high likelihood of being exploited.
Impact
The data the system processes
The privileges exposed via the exploit
Ability to detect the exploit or attacker’s movements afterward
Proximity to mission-critical data
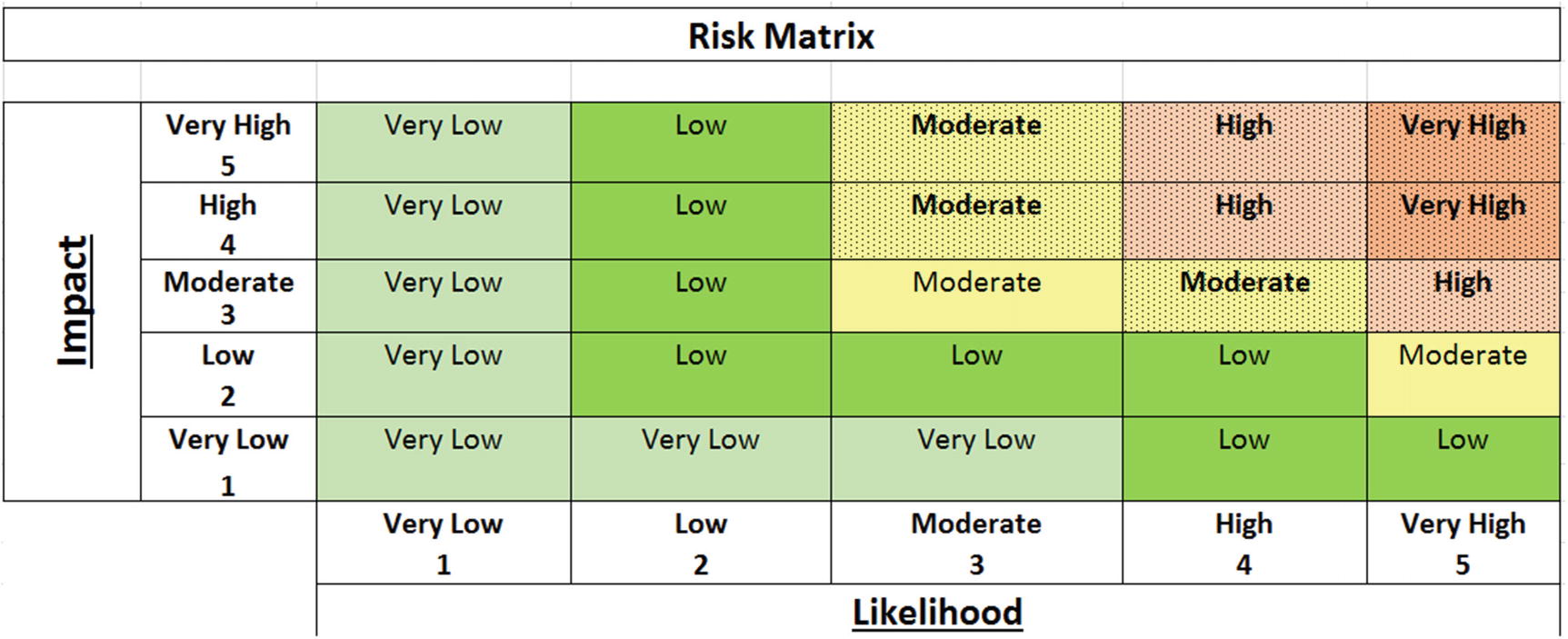
Heat maps are used to measure risks by assigning values to the likelihood and impacts or risks identified
Using the heat map, a risk with very high impact and very high likelihood is considered very high. Risks with very low ratings in both categories are considered very low. Every other combination of likelihood and impacts falls somewhere in between.
Review the Risk Assessment
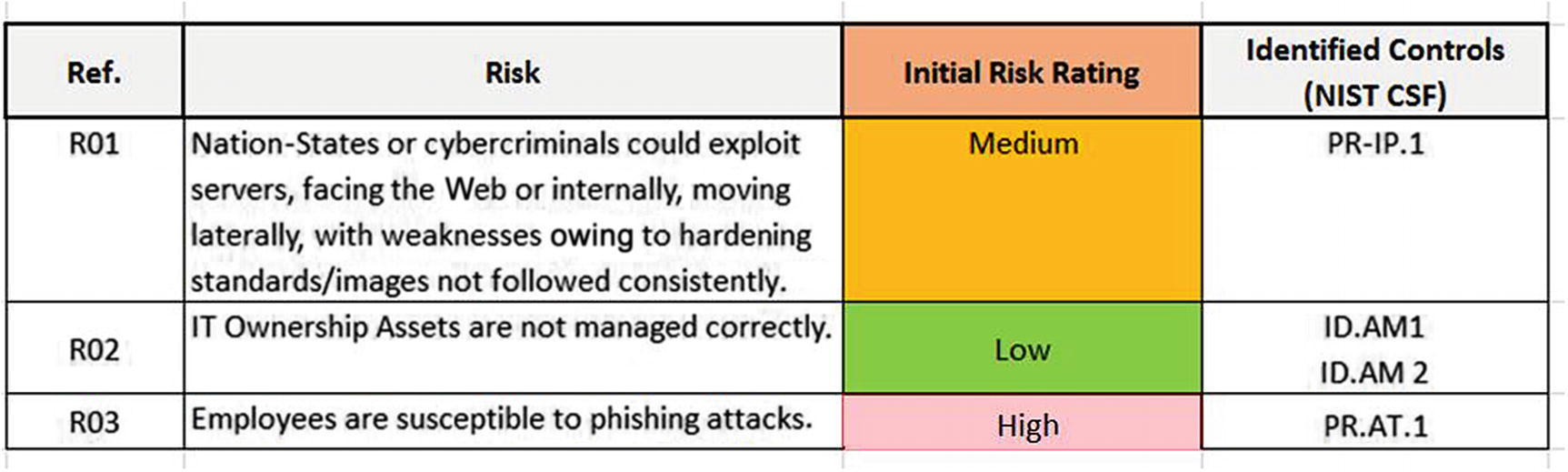
A risk register showing high, medium, and low risk
The high risk documented during the assessment states that employees are susceptible to phishing attacks. One way to reduce the risk level is to identify a cybersecurity control. To combat vulnerable end users being targeted by phishing attacks, a training and awareness control identified in the NIST CSF would be aligned to this risk. The amount of risk reduction, if any, depends on the maturity of the control process. Immature controls tend to operate ineffectively, and, therefore, fail to reduce the amount of risk. During incident response planning, the team would focus on preparing for attacks launched via e-mails directed at employees. Playbooks outlining necessary actions to combat phishing campaigns, malware, and ransomware attacks are key focus areas for practice sessions.
The medium risk illustrates vulnerabilities nation-states and cybercriminals can exploit in web applications. This one allows access to an entity’s environment. The incident response team should plan for successful attacks against web servers and understand the relevant playbooks to contain an attack of this type.
The low risk shows that the entity does an effective job maintaining an inventory of hardware and software assets. The incident response team does not have to spend as much time planning for responses due to lost assets.
These three examples illustrate how the incident response team can think through scenarios in which events, incidents, and breaches initiate: critical and high risks first, then moderate as necessary, and, finally, low risks. It is probable that low risks are not part of the scenario planning and that only certain moderate/medium risks, depending on overlap with critical and high risks, are, for example, the medium risk owing to misconfigured web applications being exploited. If a high risk existed because out-of-date code libraries were in use, the configuration risk might be redundant and not necessary for incident planning purposes. The items on the risk register must be evaluated individually but should be considered where common attack vectors are present.
The Mandiant Cyber Attack Life Cycle
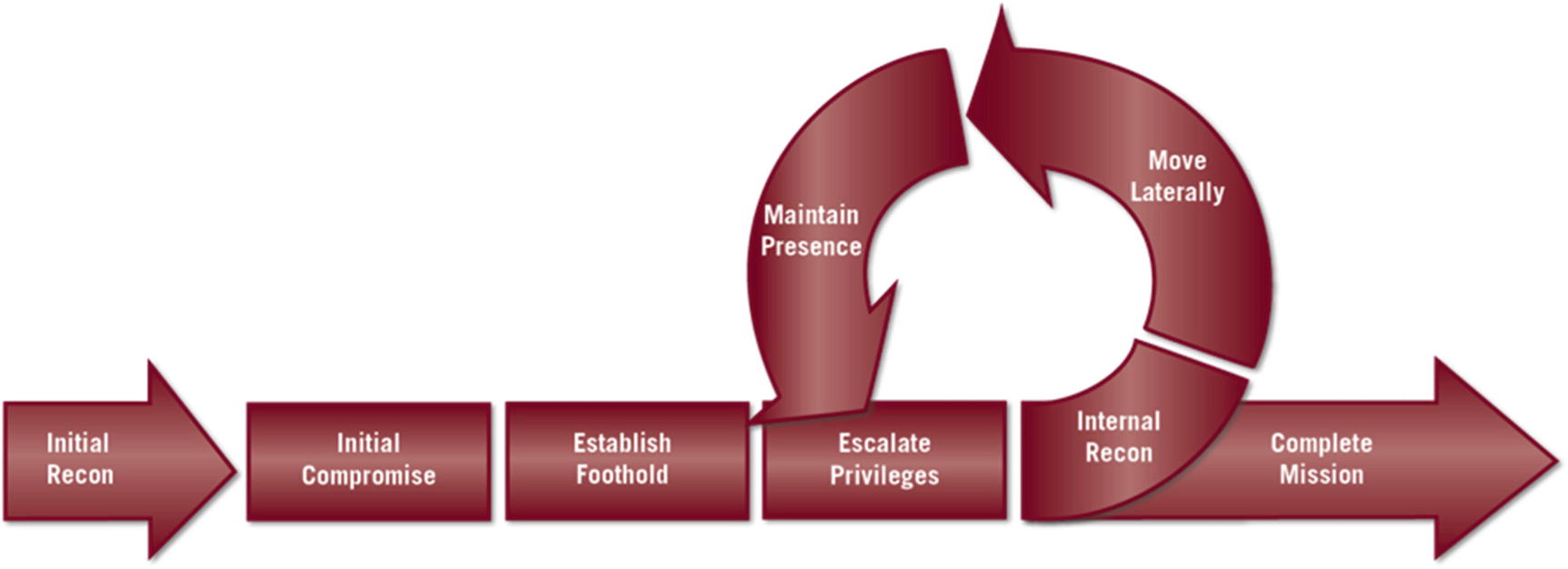
The Mandiant Cyber Attack Life Cycle (formerly Kill Chain) shows the life cycle of attacks, which includes seven steps, from initial compromise to completing the mission. (Image courtesy of FireEye Inc.)
Breaking Down the Life Cycle
The attack life cycle can be thought of as having three phases. The first begins with initial recon and ends once a foothold is established inside the targeted network. The second is an iterative process of escalating privileges, conducting internal reconnaissance, moving laterally, and maintaining persistence. The last phase is finishing the job.
Phase One
The attacks entities experience in today’s environment are not quick hits, in many cases. This initial set of activities are designed to gather as much information about the target as possible. Attackers often know more about the network they plan to prey on than individuals working daily at the site of the targeted network.
Reconnaissance
Common Methods Attackers Use to Gather Information Against Targets
Reconnaissance Method | Value Derived |
|---|---|
DNS | The objective is to gain knowledge about the entity’s domains and subdomains. |
Shodan | Adversaries see what devices are connected to the Internet and focus on capturing IP addresses. |
Social Media | Attackers can understand the entity, personnel, technology used, and personnel issues. |
E-mail Harvesting | A list of targets at the entity can result in mass phishing campaigns that attempt to exploit an end user and gain entry. |
Two common ways in which entities are compromised are through phishing attacks and exploiting misconfigured devices (more on this in the following section). Successful attacks are a result of extensive intelligence gathered before any active attack methods are launched.
Initial Compromise
If an attacker can trick end users into letting them into the environment, all the security controls at the perimeter and internally can be bypassed. Taking advantage of flawed configurations in devices exposed to the Internet is another way attackers attempt to infiltrate networks. Today’s threat actors have the advantage of vast resources to take advantage of the intelligence gathered during the recon stage. If a phishing attack is the chosen method, attackers will know everything possible about the target, both personal and professional, to increase the chances of success.
Establishing a Foothold
Once inside, malicious software is used to establish a foothold in the environment. Successful phishing attacks lead to control over an end user device or stolen credentials. Exploiting web applications, for example, gives the adversary a level of privileged access that is useful. The objective requires placing a back door into the system, so the attackers can come and go.
Phase Two
This phase is iterative. First, privilege escalation requirements are met. These privileges are used to conduct recon of the internal environment and move laterally toward the objective, while maintaining persistence. When opportunities to further escalate privileges occur, or privileges to other environments present themselves, these credentials are used to execute internal reconnaissance again, keep moving through the network, and maintain persistence. This cycle continues until the mission is achieved.
Escalating Privileges
Once inside, the attackers want to escalate privileges, first by investigating the machine compromised, to see if any means of escalation exist. Cyber hygiene plays a role in limiting attackers’ ability to escalate privileges. If default administrative or service accounts are pervasive in the environment, it is not hard for malicious groups to compromise one of these accounts to gain elevated privileges.
Internal Recon
Internal recon consists of investigating connections to the machine initially compromised and/or the machine currently in control of the attackers. Using Nmap to uncover connections is possible. It depends on whether the attacker thinks detection capabilities exist to alert the entity of the scanning.
Move Laterally
Once an attacker gets inside and maps a lay of the land, it is time to move around. The intent is to find credentials with the ability to get into systems housing the data targeted by the attacker. This includes gaining entry into machines that are literally lateral moves, meaning no elevation of credentials occurs, and finding machines in which elevated credentials exist.
Maintain Presence
Attacks are carried out over several months. Some statistics report a seven-month lag or more before detection of intrusions. This means threat actors come and go. They do this by implementing a back door, allowing access when time to continue the attack exists. One simple way is through the use of Telnet. Attackers also use rootkits. Rootkits modify system files, leaving back doors in systems as another means of maintaining persistence. If monitoring capabilities are immature, enabling this service makes reconnection easy.
Phase Three —Complete the Mission
This is a single-step phase. Once the attacker has found what he or she is looking for, removing changing, or destroying the data comes next. If the attacker wants to steal data, it is moved via irregular means and in small enough increments not to cause alarm.
How This Helps
The attackers targeting the entity
The methods used to conduct the attack and complete the mission
Weaknesses it exploits
Similar weaknesses within the entity
Actions available to reduce likelihood of success
Tie the Risk Assessment and Kill Chain
Two common ways in which attacks were launched in the last several years were via exploiting end users through phishing attacks and exploiting configuration weaknesses in web applications. These attack vectors represent ways attackers initially gain entry and establish a foothold in entities. These risks, if high or medium, require consistent monitoring and assessment. Measuring the level of risk for end-user vulnerability and securing web applications for changes keep the entity on its toes and focused on common ways events, incidents, and breaches begin.
Targeting End Users
Phishing attacks are used either to gain entry and establish a foothold for the attacker or to unleash ransomware. Beginning with the attack on Anthem, 2015 became a year of large breaches, owing to phishing attacks. These attacks targeted healthcare entities and captured many headlines. Anthem’s attack began with a well-crafted spear phishing attack aimed at an individual with elevated credentials. The e-mail setting off the chain of events led the target to a malicious domain.
Targeting Web Applications
The Equifax breach reminded everyone how important basic configuration management and security of web applications is to entities. Equifax faced intense criticism because its breach began when a vulnerability did not get patched.
OWASP Top Ten
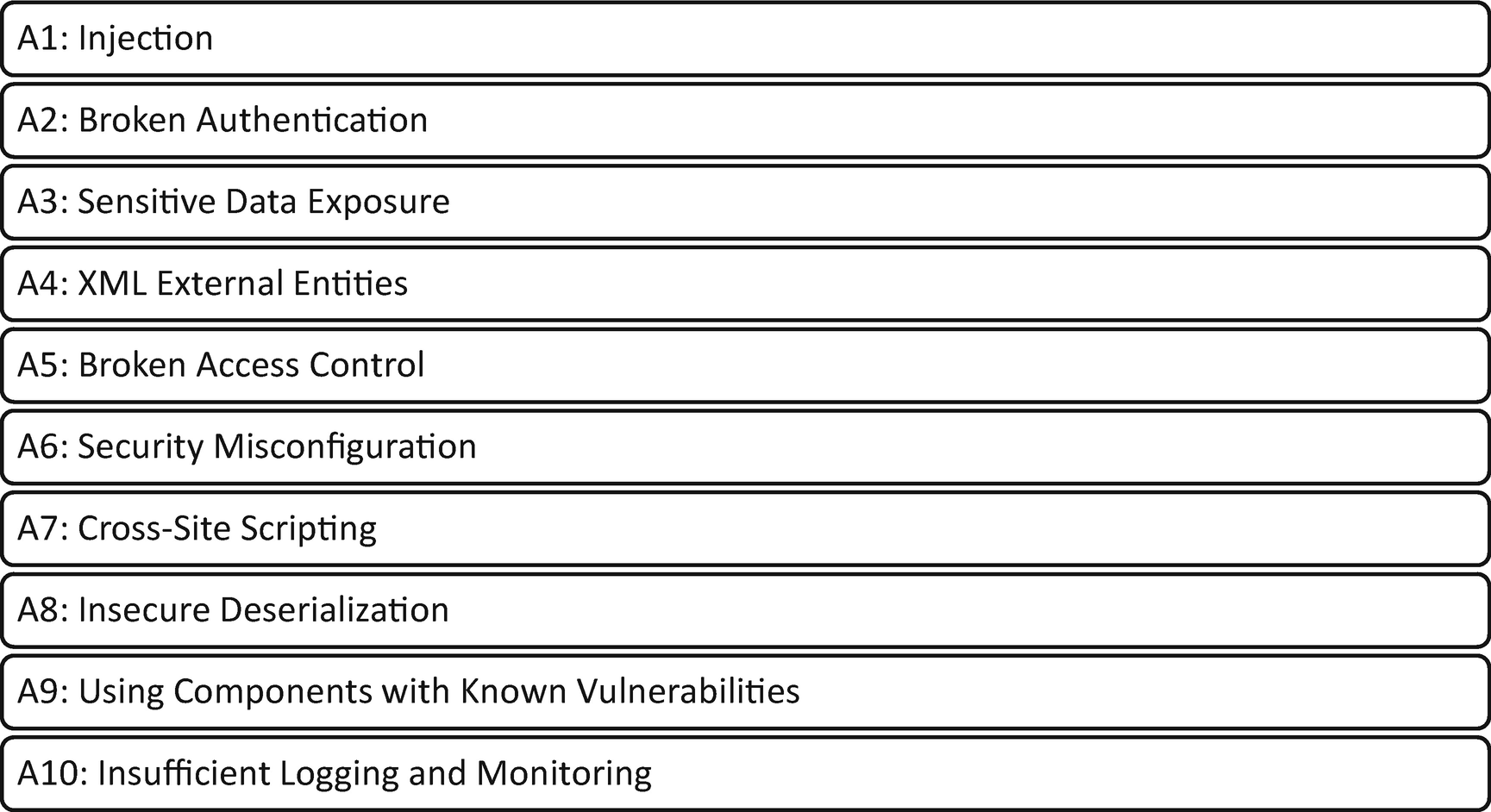
OWASP top-ten security risks published in 2017
A1: Injection: Common in SQL, NoSQL, and other platforms, this flaw allows for the execution of commands by these platforms causing data exposure to the attacker.
A2: Broken Authentication: Insecure configurations of authentication mechanisms and session management lead to attackers capturing session tokens or passwords. Attackers can impersonate individuals using these credentials.
A3: Sensitive Data Exposure: Web applications and APIs expose sensitive data when moving from web servers to the browser, if traveling in the clear.
A4: XML External Entities: These attacks target XML-based web services by uploading or include hostile code in an XML document.
A5: Broken Access Control: This issue occurs when entities do not configure authorizations for users correctly. Authenticated users who are not configured correctly allow users to interact with data not intended by the data owners.
A6: Security Misconfiguration: There are many ways application misconfiguration can occur, making this a very common risk. The misconfigurations result from unchanged default settings to configuration changes not fully vetted for security issues.
A7: Cross-Site Scripting (XSS): Missing validation checks allow user input to update or end up in web pages.
A8: Insecure Deserialization: Often difficult to execute, because available exploits require customization, these attacks occur when attackers substitute malicious data and rebuild it into a malicious object.
A9: Using Components with Known Vulnerabilities: Libraries, frameworks, and modules with vulnerabilities are easily exploited. Entities not consistently testing for and remediating these vulnerabilities leave themselves exposed to exploits available in the wild.
A10: Insufficient Logging and Monitoring: If web applications are not monitored for exploitation of vulnerabilities, attackers can use these to establish a foothold and pivot to other parts of the network.
These risk items are not unusually sophisticated. Threat actors know how to find these issues and exploit them without too much effort. If not already completed, it is important for the entity to test web applications for the presence of these issues. If any exist, the incident response team must plan for and anticipate cybersecurity events related to these events. How is this accomplished? By focusing detective capabilities and resources on these risks, if remediation is not possible or the team believes recurrence is possible. Regarding response playbooks, these would focus on compromised credentials, data theft, malware/ransomware outbreaks, or denial of service, depending on the exploit.
Summary
Planning responses to cybersecurity events is very similar to game planning in sports or military battle planning. Considering how adversaries attack based on their preferred methods and what weaknesses exist in the information systems focuses the team on specific actions to increase the effectiveness of the incident response program. Understanding what risks to assets exist is a must. Discussing these risks in terms of how sophisticated attackers approach targets helps the team build a comprehensive program aimed at preparing to handle events with the potential to occur.