1. You are analyzing the current security of your network and are concerned about the possibility that users will bypass authentication and gain greater permissions than they were given. What are the two major causes of privilege escalation? Choose all that apply.
A. Bugs in software
B. Spyware
C. Backdoors
D. BIOS
Correct Answers and Explanations: A and C. Bugs in software and backdoors are two major causes for privilege escalation. Privilege escalation occurs when a user acquires greater permissions and rights than he or she was intended to receive. This can occur as a result of bugs (which are errors in code) or backdoors in software (which can bypass normal authentication).
Incorrect Answers and Explanations: Answer B is incorrect because Spyware is used to monitor a system and send data to a third party. Answer D is incorrect because the BIOS is low-level software on a computer that’s used for recognizing and configuring hardware on a computer and starting the machine.
2. A user reports that his machine frequently crashes, and that he believes someone has accessed his e-mail account with his password. He has performed an antivirus scan on his computer and it is clean. What other likely culprit is behind the attack?
A. A worm
B. A Trojan horse
C. A Rootkit
D. A logic bomb
Correct Answer and Explanation: C. A rootkit, since they are designed to hide themselves from the OS and antivirus scans.
Incorrect Answers and Explanations: Answers A, B, and D are incorrect since they can all be detected by a virus scan.
3. You open a Microsoft Word document and notice that other files you have open suddenly close. When you reopen these files, you find that the information in them has been modified. The same behavior doesn’t occur when other programs are used. What type of virus has probably infected your system?
A. Parasitic
B. Data file
C. Boot sector
D. A logic bomb
Correct Answer and Explanation: B. A data file virus can open, manipulate, and close data files. Data file viruses are written in macro languages and automatically execute when the legitimate program is opened. A well-known type of data file virus is a macro virus, which can be embedded in such files as Microsoft Office documents and spreadsheets.
Incorrect Answers and Explanations: Answers A, C, and D are incorrect because the symptoms indicate a macro virus is at work. Answer A is incorrect because a parasitic virus infects executable files or programs in the computer. This type of virus typically leaves the contents of the host file unchanged but appends to the host in such a way that the virus code is executed first. Answer C is incorrect because bootstrap sector viruses live on the first portion of the disk, known as the boot sector (this includes both hard disks and other removable media). This virus replaces either the programs that store information about the disk’s contents or the programs that start the computer. Answer D is incorrect because multipartite viruses combine the functionality of the parasitic virus and the bootstrap sector viruses by infecting either files or boot sectors.
4. A programmer has recently been fired from the organization. On the programmer’s next birthday, your server suddenly locks up. Upon investigating, you find that there have been numerous Registry changes, and system files have been deleted by a service created by the dismissed programmer. What has affected your system?
A. Nothing. Programs often modify Registry settings.
B. Link
C. Boot sector
D. Logic bomb
Correct Answer and Explanation: D. A logic bomb is malware that is designed to execute and do damage when a condition is met. In this case, the program at fault is one that matches the birthday of a dismissed employee. The logic bomb can be a hidden function in a program that goes off on a specific date, when a command has or hasn’t been sent to it, or other conditions.
Incorrect Answers and Explanations: Answer A is incorrect because while programs may make Registry changes, there is no reason why it should have deleted system files. Answer B is incorrect because a link virus modifies the way an OS finds the program, and there is no indication that this has happened in this scenario. Answer C is incorrect because bootstrap sector viruses live on the first portion of the disk. In this scenario, it has been found that a service created by an employee has been used to modify the Registry and delete system files.
5. You have installed a new program on your computer. The software doesn’t cost anything, but it does display intermittent advertisements for products in a corner of the screen. After installing, you notice that there is a sudden increase in received data across your Internet connection, although there is no real increase in data being sent. You’re not using your Web browser, e-mail software, or other Internet applications, so you’re concerned whether the new program is sending data over the Internet. Which of the following has most likely been installed?
A. Virus
B. Antivirus
C. Adware
D. Worm
Correct Answer and Explanation: C. Adware is a type of software that uses advertising to fund development, thereby allowing users to use the program for free.
Incorrect Answers and Explanations: Answers A, B, and D are incorrect. No other problems appear to be occurring on the computer, so it is unlikely that it is a virus or worm. Antivirus software is used to protect against viruses, worms, and other malicious code, so this isn’t an issue. The application is displaying advertisements, which are likely being downloaded across the Internet, which explains the increase in received data across your Internet connection. There are no other indications that anything is amiss with the system.
6. What are good ways to protect against worms? (Select all that apply.)
A. User education programs
B. Correct firewall configuration
C. Timely software patches
D. Antivirus scans
Correct Answers and Explanations: B and C. Firewalls can prevent ports like SQL and NetBIOS from being available and usable to worms. Most worms use known vulnerabilities, so timely patches will defend against them.
Incorrect Answers and Explanations: Answer A is incorrect as worms do not require user intervention, and so user education doesn’t affect them. Answer D is incorrect as a worm is not resident, and so can only be detected in memory, where it already has infected the machine.
7. You receive an e-mail warning you about a virus, stating that if a Windows XP computer contains the file mstsc.exe, you have been infected with the virus. As such, you should delete that file and a series of others. In searching the Internet, you find information that this is a normal Windows file. What type of virus is this?
A. Link
B. Companion
C. Data file
D. Hoax
Correct Answer and Explanation: D. The file mstsc.exe is used to connect to terminal servers or remote computers. This is a normal file on Windows computers. Because the warning provides instructions on how to remove a normal Windows file, it is a hoax virus. Hoax viruses are inauthentic warnings of viruses.
Incorrect Answers and Explanations: Answer A is incorrect. Link viruses function by modifying the way the OS finds a program, tricking it into first running the virus before the desired program. Answer B is incorrect because a companion virus creates a new program with the same name as an already existing legitimate program. It then tricks the OS into running the companion program, which delivers the virus payload. Answer C is also incorrect. A data file virus is a macro virus that automatically executes when a program is opened.
8. A user has a laptop computer that normally isn’t connected to the network. She complains that her computer has slowed down considerably, and certain programs on the machine no longer open. She ran her antivirus program, but it found nothing. You establish a remote connection to the computer so that you can view what’s installed on the laptop, and see that she has antivirus software installed and running. When you map a drive letter to the laptop and run the antivirus software on your computer, you find several viruses have infected the laptop. Why are you able to find the viruses but not her?
A. The antivirus software on her laptop hasn’t been updated with the latest signature files.
B. It is a hoax virus.
C. You are getting a false positive. The virus must be on your machine and not the laptop, because you can’t scan mapped drives with antivirus software.
D. She didn’t have antivirus software installed or running on her machine.
Correct Answer and Explanation: A. The antivirus software on her laptop hasn’t been updated with the latest signature files. If the signature files haven’t been updated, it would be unable to detect any viruses that have been released since the last time it was updated.
Incorrect Answers and Explanations: Answer B is incorrect because if it were a hoax, it would not be detected by antivirus software. Answer C is incorrect because you can scan a mapped drive with antivirus software. Answer D is incorrect because the scenario stated that she has antivirus software running.
9. You are configuring a firewall to block certain file types from being attached to incoming e-mail. When the e-mail reaches the firewall, you want these files to be removed from the e-mail, so that only the message reaches the user on your network. Which of the following file extensions are associated with executables that are commonly targeted by viruses and should be removed? Choose all that apply.
A. .doc
B. .com
C. .exe
D. .reg
Correct Answers and Explanations: B and C. Files with the extension .exe and .com are executable files. Files with the .exe extension are executable binary files. These are programs that can be loaded into memory, and provide various functions and execute commands automatically or with user intervention. Files with the .com extension are command files that are binary executables, similar to files with the extension .exe.
Incorrect Answers and Explanations: Answers A and D are incorrect because they are not executables. Files with the extension .doc are Word documents. Although they may be infected with macro viruses, they are not executables. Files with the .reg extension are registry extracts, which contain settings that are applied to the Windows Registry.
10. Your company’s Web server suddenly gets tens of thousands of simultaneous requests for a Web page. After the Web server crashes, you restart the server and then take a look at the log files. You see that some of the requests came from your own network. What kind of attack has most likely happened?
A. Rootkit
B. Botnet
C. Virus
D. Worm
Correct Answer and Explanation: B. Computers have been turned into zombie machines after being infected with bots. The bot herder can then send commands to these machines to make requests from a specific Web site, preventing the server from serving legitimate requests from Web site users. When you attempt to view who caused the attack, it will only show those who have been infected with the bot.
Incorrect Answers and Explanations: Answer A is incorrect because a rootkit is used to acquire elevated permissions to a computer. Answers C and D are incorrect because computers infected with a virus or worm wouldn’t make tens of thousands of computers suddenly visit a Web site.
11. You have purchased a used computer in an auction. When you power-on the computer, you are asked for a password before the OS even loads. Since you don’t have it, how will you clear the password so that you can start the computer and begin using it?
A. Clear the password in the CMOS settings
B. Flash the BIOS
C. Press F10 or DEL on the keyboard
D. There is nothing you can do if you don’t have the power-on password
Correct Answer and Explanation: B. Flash the BIOS. By flashing the BIOS, you are erasing the existing settings by updating the BIOS software.
Incorrect Answers and Explanations: Answer A is incorrect because (although power-on passwords are set in the CMOS editor) you can’t start the CMOS editor until you’ve entered the power-on password. Answer C is incorrect because pressing keys on the computer won’t help in this situation, unless of course you’re entering the password. Answer D is incorrect because you can flash the BIOS to reset all of the settings, and clear the power-on password.
12. You have heard that upgrading the BIOS on a computer can help to fix any bugs and provide new features. You download a new BIOS version and begin the upgrade. Everything seems to go well, and you recycle the power on the computer. It doesn’t start but produces a blank screen. What is most likely the cause of the computer not starting?
A. The wrong BIOS version was installed.
B. There was a power outage during the upgrade.
C. The CMOS editor needs to be reconfigured.
D. You should never flash the BIOS as it will cause the computer to fail.
Correct Answer and Explanation: A. The wrong BIOS version was installed. Flashing the BIOS with a version that was meant for another motherboard can cause all sorts of problems, including the BIOS not being able to start the computer. When flashing the BIOS, it is important that the correct version for your computer is used.
Incorrect Answers and Explanations: Answer B is incorrect because (although a power outage would cause the BIOS upgrade to fail) the scenario says that everything seemed to go well during the upgrade. Answer C is incorrect because correctly flashing the BIOS will clear any CMOS settings, restoring them to default settings. This wouldn’t affect the computer not starting. Answer D is incorrect because you can flash the BIOS to upgrade it.
13. Your company has started issuing USB flash drives to employees. Employees now use the devices to copy data from their home computers, insert them into computers used by other businesses, and so on. Members of the sales team and others who deal with outside organizations need this removable storage, so they can obtain copies of specifications, orders, and so on. In copying files from computers outside of your network, you’re concerned about viruses. Which of the following should you do to ensure that users can benefit from the functionality of their flash drives, while protecting the network from any viruses?
A. Turn off autoplay on Windows computers used by your company
B. Disable USB ports on any computers attached to your network
C. Set write-protection on the flash drive so that viruses can’t be written to the device
D. Create a policy that prohibits users from copying data outside of the organization to flash drives
Correct Answer and Explanation: A. Turn off autoplay on Windows computers used by your company. This is the feature that will start any programs on media inserted into drives or USB ports automatically. Turning off the autoplay feature can prevent an infected program from being executed as soon as Windows reads the disk or device. In addition to this, any USB storage devices should be scanned with up-to-date antivirus software before any files are opened.
Incorrect Answers and Explanations: Answer B is incorrect because disabling the USB ports on network computers will prevent users from using the flash drives and any other USB devices. Answer C is incorrect because setting write protection will prevent files, as well as viruses from being written to the disk. If users know how to switch off write protection, the users can still use the flash drive, allowing files (including those that are infected with virus) to be copied onto the media. Answer D is incorrect because this will prohibit users from using the flash drives for work purposes.
14. You are planning to implement removable storage devices in your organization. Before doing so, your boss wants you to provide information on various types of removable media that users can use to read, write, and rewrite data to. Which of the following storage devices will you discuss?
A. Hard disks
B. CD-R
C. DVD-R
D. Flash memory card
Correct Answer and Explanation: D. Flash memory cards can be used to store and transfer varying amounts of data. Memory cards have typically ranged from 8 to 512 MB, but new cards are capable of storing more than 8 GB of data.
Incorrect Answers and Explanations: Answer A is incorrect because hard disks are not removable media. Answers B and C are incorrect because a CD-R and DVD-R are Write Once, Read Multiple and aren’t capable of having data on them rewritten.
15. You need to migrate 40 GB of data from a hard disk to removable media. You want to ensure that all of the data is stored on a single disc or media. Which of the following will you use?
A. Blu-Ray
B. DVD
C. CD
D. Disk
Correct Answer and Explanation: A. A single-layer Blu-Ray disc can store up to 25 GB of data, whereas a dual-layer Blu-Ray disc can store up to 50 GB of data.
Incorrect Answers and Explanations: Answer B is incorrect because a DVD is capable of storing 4.7 to 17 GB of data. Answer C is incorrect because a data CD is only capable of storing 700 MB of data. Answer D is incorrect because a floppy disk is only capable of storing 1.44 MB of data.
1. You have a computer and through a portscan discover that port 25 is enabled. This computer is used for file and print services only. What should you do?
A. Disable SMTP
B. Disable POP
C. Disable IIS
D. Port 25 should be enabled
Correct Answer and Explanation: The answer is A. Answer A is correct because the port for SMTP is 25.
Incorrect Answers and Explanations: Answer B is incorrect because POP is not on port 25; it’s usually 110. Answer C is incorrect because IIS will use port 80 and port 443 by default for HyperText Transfer Protocol (HTTP) and HyperText Transfer Protocol Secure (HTTPS). Answer D is incorrect because port 25 has nothing to do with file and print services.
2. You have a computer and through a portscan discover that port 25 and port 80 are enabled. This computer is used for serving Web pages only. What should you do?
A. Disable SMTP
B. Disable POP
C. Disable IIS
D. Port 25 and 80 should be enabled
Correct Answer and Explanation: The answer is A. Answer A is correct because the port for SMTP is 25.
Incorrect Answers and Explanations: Answer B is incorrect because POP is not on port 25; it’s usually 110. Answer C is incorrect because this is a Web server and port 80 should be open in order for IIS to serve Web pages. Answer D is incorrect because port 25 has nothing to do with file and print services.
3. You notice port scans on a Web server. The server processes both secure and insecure pages. What steps can you take to help secure the OS?
A. Enable port 80, disable all other ports
B. Enable port 443, disable all other ports
C. Enable port 25, disable all other ports
D. Enable port 80, 443, and 25, disable all other ports
E. Enable port 80 and 443, disable all other ports
Correct Answer and Explanation: The correct answer is E. Since Web services use port 80 and 443, they should be enabled.
Incorrect Answers and Explanations: Answer A is incorrect because this would not allow users to browse secure pages. Answer B is incorrect because this would not allow users to browse nonsecure pages. Answer C is incorrect because port 25 is SMTP, which has nothing to do with browsing Web pages. Answer D is incorrect, since port 25 is SMTP, which has nothing to do with browsing Web pages. This would work; however, it would not result in a secure system since an unused port or service would be available.
4. What port does SNMP use?
A. Port 80
B. Port 25
C. Port 161
D. Port 443
Correct Answer and Explanation: The answer is C. Answer C is correct because SNMP uses port 161.
Incorrect Answers and Explanations: Answer A is incorrect, as this is the standard port for nonsecure Web pages. Answer B is incorrect, since port 25 is SMTP. Answer D is incorrect, as this is the standard port for secure Web pages.
5. As part of the overall OS hardening process, you are disabling services on a Windows server machine. How do you decide which services to disable?
A. Disable all services, and then re-enable them one by one
B. Research the services required and their dependencies, then disable the unneeded services
C. Leave all services enabled, since they may be required at some point in the future
D. Disable all workstation services
Correct Answer and Explanation: The correct answer is B. Answer B makes the most sense, and this will result in the most secure system, while enabling only the services and dependencies needed.
Incorrect Answers and Explanations: A is incorrect. This may work; however, it will not result in the most secure system. Answer C is incorrect. This would result in a system that is not as secure as it could be. Services that are not being used could be left enabled, allowing more surface area for a hacker to attack. Answer D is incorrect. This would result in a system that is not as secure as it could be. Services that are not being used could be left enabled, allowing more surface area for a hacker to attack. Some of the workstation services may be required to perform the functions the server needs to perform.
6. You are configuring a server to be used for IIS. You have disabled all unused services. All access to the server will be through secure pages using HTTPS. What port should you enable?
A. Port 80
B. Port 25
C. Port 161
D. Port 443
Correct Answer and Explanation: The correct answer is D. Port 443 is the default port for secure Web pages.
Incorrect Answers and Explanations: Answer A is incorrect. Port 80 is generally used for nonsecure Web pages. Answer B is incorrect. Port 25 is used for SMTP, which is not required for secure Web pages. Answer C is incorrect. Port 161 is used for SNMP which is not required for secure Web pages.
7. Robby is preparing to evaluate the security on his Windows XP computer and would like to harden the OS. He is concerned as there have been reports of buffer overflows. What would you suggest he do to reduce this risk?
A. Remove sample files
B. Upgrade his OS
C. Set appropriate permissions on files
D. Install the latest patches
Correct Answer and Explanation: The correct answer is D. Generally, buffer overflows exploit flaws in the OS, which are usually fixed via security packages.
Incorrect Answers and Explanations: Answer A is incorrect. Sample files have nothing to do with buffer overflows. Answer B is incorrect. Upgrading the OS may fix the buffer overflow but introduce other problems. Answer C is incorrect. File permissions have nothing to do with buffer overflow issues. That said, however, it’s a good idea to set the appropriate file permissions on files.
8. Marissa is planning to evaluate the permissions on a Windows 2003 server. When she checks the permissions, she realizes that the production server is still in its default configuration. She is worried that the file system is not secure. What would you recommend Melissa do to alleviate this problem?
A. Remove the anonymous access account from the permission on the root directory
B. Remove the system account permissions on the root directory of the C: drive
C. Remove the “everyone” group from the permissions on the root directory
D. Shut down the production server until it can be hardened
Correct Answer and Explanation: The correct answer is C. This is a good spot to start; it will prevent unauthenticated users from accessing files at will on the root directory.
Incorrect Answers and Explanations: Answer A is incorrect. This will not produce the desired result. Answer B is incorrect. The system account needs permission to the C:\ drive directory. Answer D is incorrect. The production server needs to be on to be hardened.
9. You have been asked to review the general steps used to secure an OS. You have already obtained permission to disable all unnecessary services. What should be your next step?
A. Remove unnecessary user accounts and implement password guidelines
B. Remove unnecessary programs
C. Apply the latest patches and fixes
D. Restrict permissions on files and access to the Registry
Correct Answer and Explanation: The correct answer is A. Removing unnecessary accounts will result in less attack surface available for a hacker to penetrate. By implementing strong passwords, you will also reduce the ability of a hacker to use a “simple” password breaking program to gain access.
Incorrect Answers and Explanations: Answer B is incorrect. While installing only programs that are necessary is a good guideline, removing the unnecessary account and implementing password guidelines should be the next step. Answer C is incorrect. While patching the server is a good idea, removing the unnecessary accounts and implementing password guidelines should be the next step. Answer D is incorrect. While restricting permissions on files and access to the Registry is a good idea, removing the unnecessary accounts and implementing password guidelines should be the next step.
10. Yesterday, everything seemed to be running perfectly on the network. Today, the Windows 2003 production servers keep crashing and running erratically. The only events that have taken place are a scheduled backup, a CD/DVD upgrade on several machines, and an unscheduled patch install. What do you think has gone wrong?
A. The backup altered the archive bit on the backup systems
B. The CD/DVDs are not compatible with the systems in which they were installed
C. The patches were not tested before installation
D. The wrong patches were installed
Correct Answer and Explanation: The correct answer is C. All patches should be tested before installing.
Incorrect Answers and Explanations: Answer A is incorrect. Backups will usually not cause this problem. Answer B is incorrect. CDs/DVDs will generally not cause this problem. Answer D is incorrect. The wrong patches will usually not install (in a Windows environment).
11. Debbie is reviewing open ports on her Web server and has noticed that port 23 is open. She has asked you what the port is and if it presents a problem. What should you tell her?
A. Port 23 is no problem because it is just the Telnet client
B. Port 23 is a problem because it is used by the Subseven Trojan
C. Port 23 is open by default and is for system processes
D. Port 23 is a concern because it is a Telnet server and is active
Correct Answer and Explanation: The correct answer is D. Telnet is not required for a Web server.
Incorrect Answers and Explanations: Answer A is incorrect; port 23 is for Telnet server, which is a security risk on a Web server. Answer B is incorrect; port 23 is for Telnet server, which is a security risk on a Web server. It is not used by Subseven Trojan. Answer C is incorrect; port 23 is for Telnet server, not system processes.
12. Monday morning has brought news that your company’s e-mail has been blacklisted by many Internet service providers (ISPs). Somehow your e-mail servers were used to spread spam. What most likely went wrong?
A. An insecure e-mail account was hacked
B. Sendmail vulnerability
C. Open mail relay
D. Port 25 was left open
Correct Answer and Explanation: The correct answer is C. Open mail relay means other servers can use your server to relay messages (including spam).
Incorrect Answers and Explanations: Answer A is incorrect. This problem usually is from the server configuration allowing open mail relay. Answer B is incorrect. This problem usually is from the server configuration allowing open mail relay. Answer D is incorrect. This problem usually is from the server configuration allowing open mail relay. Port 25 being open means SMTP is installed and working (which you would expect on a mail server).
13. Management was rather upset to find out that someone has been hosting a music file transfer site on one of your servers. Internal employees have been ruled out as it appears it was an outsider. What most likely went wrong?
A. Anonymous access
B. No Web access control
C. No SSL
D. No bandwidth controls
Correct Answer and Explanation: The correct answer is A. Anonymous access means anyone can log in to an FTP server.
Incorrect Answers and Explanations: Answer B is incorrect. No Web access control has nothing to do with FTP servers. Answer C is incorrect. SSL is used to secure HTTPS traffic. Answer D is incorrect. Bandwidth controls are used to throttle bandwidth.
14. You have been given the scan below and asked to review it. Interesting ports on (18.2.1.88):
(The 1263 ports scanned but not shown below are in state: filtered)
Port |
State |
Service |
22/tcp |
open |
ssh |
53/udp |
open |
dns |
80/tcp |
open |
http |
110/tcp |
open |
pop3 |
111/tcp |
open |
sun rpc |
Your coworker believes it is a Linux computer. What open port led to that assumption?
A. Port 53
B. Port 80
C. Port 110
D. Port 111
Correct Answer and Explanation: The correct answer is D. Port 111 would generally be found on a Linux computer, but not a Windows computer.
Incorrect Answers and Explanations: Answer A is incorrect. Port 53 is used for DNS, which is used regardless of OS. Answer B is incorrect. Port 80 is used for HTTP Web traffic which is used regardless of OS. Answer C is incorrect. Port 110 is used for pop mail traffic, which is used regardless of OS.
15. During a routine check of a file server, you discover a hidden share someone created that contains 100 GB of music content. You discover the share was created on a drive that everyone has full control over. What steps should you take to ensure this doesn’t happen again?
A. Define an acceptable use policy
B. Remove full control from the “everyone” group
C. Remove full control from the offending user
D. Remove the files and the directory
Correct Answers and Explanations: The correct answers are A, B, and D. A, B, and D are correct because it’s important for employees to know that this behavior won’t be tolerated. Additionally, granting full control to shares to everyone is a bad idea, as people will do this sort of thing if not kept in check. Answer D is important, as music sharing is illegal and it’s important to protect your company from legal action.
Incorrect Answers and Explanations: Answer C is incorrect. This would not be enough to prevent another user for doing this in the future.
1. A user contacts you with concerns over cookies found on their hard disk. The user visited a banking site several months ago, and when filling out a form on the site, provided some personal information that was saved to a cookie. Even though this was months ago, when the user returned to the site, it displayed his name and other information on the Web page. This led the user to check his computer, and find that the cookie created months ago is still on the hard disk of his computer. What type of cookie is this?
A. Temporary
B. Session
C. Persistent
D. Tracking
Correct Answer and Explanation: Answer C is correct. Persistent cookies are created to store for a long-term basis, so the person doesn’t have to log in each time they visit, or to save other settings like the language you want content to be displayed in, your first and last name, or other information.
Incorrect Answers and Explanations: Answers A and B are incorrect, because temporary and session cookies are created on a temporary basis, and removed from the computer when the Web browser is shut down. Answer D is incorrect, because the user filled out a form on a banking site, and it is retrieving this information months later to display on a Web page when the user returns to the site. This is the behavior of a persistent cookie. Tracking cookies are different, because they are used to retain information on sites visited by a user.
2. Your company has recently installed IM software on computers throughout the network, to encourage better communication between departments. A user on a network has installed a packet sniffer, and is using it to attempt viewing IMs transmitted between users of the network. When the packet sniffer captures one of the packets from an IM session, which of the following will occur?
A. The information from the IM session can’t be viewed because it is encrypted.
B. The information from the IM session can be viewed because it is sent as cleartext.
C. The message will be unreadable because IM only allows small messages to be sent, meaning that the entire message will be split between numerous packets.
D. The message will be unreadable because the Short Message Service Center automatically encrypts every message sent over Short Message Service (SMS).
Correct Answer and Explanation: Answer B is correct. The information from the IM session can be viewed because it is sent as cleartext. By using a packet sniffer to monitor IM on a network, you can view what people are chatting about and other sensitive information, because the information is sent as cleartext messages without any encryption.
Incorrect Answers and Explanations: Answer A is incorrect, because IM messages are not encrypted. Answers C and D are incorrect, because the SMS is used on cell phones and other devices to send small electronic messages through a Short Message Service Center. SMS is different from the IM software installed on computers.
3. Which layer of the OSI model is the target of most Internet-based attacks?
A. The network layer, directly above the data link layer
B. The session layer directly above the transport layer
C. The application layer directly above the session layer
D. The application layer directly above the presentation layer
Correct Answer and Explanation: Answer D is correct. The application layer is the target of most Internet-based attacks. The application layer is the last layer of the OSI model and exists directly above the presentation layer.
Incorrect Answers and Explanations: Answers A and B are incorrect because they reference layers that are not the most attacked. Answer C is incorrect because the application layer does not reside above the session layer.
4. What does the term drive-by-download refer to?
A. Downloading of Trojans from P2P networks
B. Downloading Trojans from instant messaging applications
C. Downloading mail attachments via an open mail relay
D. Navigating to a Web site and having malicious code auto execute without your knowledge
Correct Answer: Answer D is correct.
Incorrect Answers and Explanations: Answers A, B, and C refer to third-party applications/software other than the Web browser which is the prime method for drive-by-download attacks..
5. True or False, Cookie security is truly only at the mercy of the Web site administrator?
Answer: False, although the Web site administrator is ultimately responsible for the information that is stored within cookies and if the cookie is sent to visitors’ Web browsers over encrypted channels it is not the only form of cookie security. Users can configure their Web browser to reject cookies from entrusted sites and filter on the type of cookies that will be downloaded and loaded.
6. Proper Input validation should be inclusive of which of the following checks? (Select all that apply)
A. Data type
B. Data length
C. IP address of data transmission
D. Name of the user submitting the data
E. Range of values
Correct Answers and Explanations: Answers A, B, and E are correct and all pertain to ensure that the entered data is in a form that the application is expecting.
Incorrect Answers and Explanations: Answers C and D are related to authentication as opposed to data validation.
7. If P2P networks are to be used on corporate networks, which of the following steps does the best job of securing it?
A. Configure P2P client to share files within a single directory and install and antivirus client on the all computers running P2P software
B. Disable any open mail relays that are accessible from P2P clients
C. Disable ActiveX, Java, and scripting within users’ Web browsers
D. Disable any IM clients installed on the P2P clients
Correct Answer and Explanation: Answer A is correct and provides the best protection against major P2P threats. Sharing a single file will help ensure sensitive user information is not leaked to P2P networks and installing antivirus clients on computers running P2P software will help ensure Trojans and worms originating from the P2P network are identified and blocked before they impact the user’s computer.
Incorrect Answers and Explanations: Answers B and D may help encase a computer running P2P software should it be compromised but does not help prevent the actual system compromise. Answer C involves technologies primarily used within Web browsers and not P2P clients.
8. Monday morning has brought news that your company’s e-mail has been blacklisted by many ISPs. Somehow your e-mail servers were used to spread spam. What most likely went wrong?
A. An insecure e-mail account was hacked
B. Sendmail vulnerability
C. Open mail relay
D. Port 25 was left open
Correct Answer and Explanation: Answer C is the most likely answer for a company being blacklisted. Traditionally spammers troll the Internet looking for open mail relays to distribute unsolicited mail messages.
Incorrect Answers and Explanations: Answers A, B, and D are related to missing patches and firewall rules that may be used by an attacker to gain unauthorized access to a mail server\relay and send spam; however, this is a much more difficult task when compared to Answer C.
9. Your developer contacts you for guidance on how to secure ActiveX controls he plans on using within his Web application. What advice would you provide him?
A. Remind the developer to follow secure coding practice and sign the control before publishing
B. Only transfer the control over SSL sessions to and from the Web browser
C. Write the ActiveX control within Java
D. Perform a Threat Model on the ActiveX control
Correct Answers and Explanations: Answer A is correct. Following securing coding practices will help prevent the existence of vulnerabilities within the code. Signing the control will allow the developer to ensure the control has not been tampered with after development and publication.
Incorrect Answers and Explanations: Answer B is incorrect. Securing ActiveX is all about secure coding practice. Only transfering the control over SSL sessions does no good if the ActiveX control itself is not secure from scratch and signed appropriately before publishing. Answer C is incorrect as the language used to create an ActiveX control is not the largest security concern. Answer D is incorrect as performing a threat model will help identify vulnerabilities within the ActiveX control and countermeasures to be applied; however, a separate action of applying the threat model results is required to effectively secure the control.
10. Multiple user laptops have been compromised due to exploitation of vulnerabilities in Java applets downloaded from third parties. What should you do to secure Java and help prevent further reoccurring security incidents? (Select the best answer)
A. Install the latest patches for all employee computers
B. Install the latest patches for all employee computers and ensure employees only visit sites with proper input validation
C. Install the latest patches for all employee computers and use Internet Explore security zones to restrict the permissions of downloaded Java applets
D. Install the latest patches for all employee computers and use Internet Explore security zones to restrict the permissions of downloaded JavaScript
Correct Answers and Explanations: Answer C is correct and is the best answer because it addresses vulnerabilities within existing Java applets by installing the latest patches and configuring security zones to restrict their permissions assigned to Java will help with newly released zero day vulnerabilities.
Incorrect Answers and Explanations: Answer A will ensure that presently downloaded Java applets have the latest patches as well as associated Java interpreters. However, this is not the best answer as it does not provide protection against zero day vulnerabilities that may affect third-party Java applets. Answer B is incorrect as Web sites not performing data input validation will have no impact on vulnerabilities within third-party Java applets. Answer D is incorrect because applying restrictions to downloaded JavaScript does not correctly address the security of downloaded Java applets.
11. You are tasked with creating a threat model for a new application your company is developing. Who should you include in the threat modeling process?
A. A member of the corporate security team
B. Members of the security team and upper management
C. Members of the security team and middle management
D. Members of the security team and members from all teams responsible for the design and operation of the application
Correct Answer and Explanation: Answer D is correct. To create an accurate threat model you will need participation from all teams responsible for the design and operation of the targeted application. This representation will help ensure vulnerabilities from all operational aspects are identified.
Incorrect Answers and Explanations: Answers A, B, and C are incorrect because they do not cover participation from all application design and operational teams.
12. You perform a security assessment of your company’s Web server and identify a cross-site scripting vulnerability. What recommendation can you provide to your company to correct the vulnerability? (Choose the best answer)
A. Advise Web site users to ensure cookies are only transferred over secure connections
B. Implement a policy mandating that Web site users disable ActiveX support within their Web browsers
C. Implement a policy mandating that Web site users disable Java applet support within their Web browsers
D. Advise the Web administrator to ensure all Web application data inputs are validated prior to processing
Correct Answer and Explanation: Answer D is correct as the best way to address cross-site scripting vulnerabilities is to validate data input. This would fix occurrences of XSS on ActiveX controls and Java applets downloaded to the client as well as any vulnerability located on server-side code within the application.
Incorrect Answers and Explanations: Answer A is incorrect; disabling cookies is not a countermeasure against XSS. Answers B and C are also incorrect as although XSS vulnerabilities may exist within downloaded Java applets or ActiveX controls, these controls are executed on the client and would not address the server side XSS vulnerability.
13. You push out a security hardening policy to corporate users and later receive complaints from users stating that they can no longer view business Web sites. What element of your security hardening policy is most likely the cause of the issue?
A. Removal of open mail relays
B. Disabling of ActiveX controls and Java applets
C. Implementation of P2P client restrictions
D. Implementation of IM client filtering
Correct Answer and Explanation: Answer B is correct as ActiveX controls and Java applets directly affect client side application presentation.
Incorrect Answers and Explanations: Answer A is incorrect as mail relays would not affect the user’s ability to view Web pages. Answers C and D are incorrect as they have no relation to users not being able to view Web pages.
14. Which of the following is not a phase within the threat modeling process?
A. Security objective definition
B. Application review
C. Application decomposition
D. Threat identification
E. Vulnerability identification
F. Application vulnerability scan
Correct Answer and Explanation: Answer F is not a phase within the threat modeling process; alternatively it is a subcomponent that may fall within the vulnerability identification phase of the threat modeling process.
15. Bob is preparing to evaluate the security on his Windows XP computer and would like to harden the OS. He is concerned as there have been reports of buffer overflows What would you suggest he do to reduce this risk?
A. Remove sample files
B. Upgrade his OS
C. Set appropriate permissions on files
D. Install the latest patches
Correct Answer and Explanation: Answer D is correct. The best defense against buffer overflows is to apply the appropriate patches or fixes to eliminate the buffer overflow condition.
Incorrect Answers and Explanations: Answers A, B, and C are incorrect because removing sample files would not reduce the risk of buffer overflows. Upgrading the OS may fix the immediate buffer overflow, but is not a sustainable long-term strategy. Patches and hotfixes were designed to address this issue. Setting appropriate file permissions will not prevent a buffer overflow.
1. You have been asked to install a SQL database on the intranet and recommend ways to secure the data that will reside on this server. While traffic will be encrypted when it leaves the server, your company is concerned about potential attacks. With this in mind, which type of IDS should you recommend?
A. A network-based IDS with the sensor placed in the De-Militarized Zone (DMZ)
B. A host-based IDS that is deployed on the SQL server
C. A network-based IDS with the sensor placed in the intranet
D. A host-based IDS that is deployed on a server in the DMZ
Correct Answer and Explanation: B. Answer B is correct, because by selecting a host-based IDS system, which loads on the SQL server directly, you will be able to more readily monitor the SQL server and identify attacks targeting this particular machine.
Incorrect Answers and Explanations: A, C, and D. Answer A is incorrect, because a network-based IDS in the DMZ would have difficulty identifying attacks targeting this SQL server specifically. Also, since this option places the sensor in the DMZ, visibility to a server in the LAN would be further restricted. Answer C is incorrect, because a network-based IDS has large amounts of traffic to scan through and the SQL server will not get the attention that it may require. In this case, the sensor would be placed on the intranet, putting it closer to the server that it will manage, but still not the ideal scenario for a single server monitoring. Answer D is incorrect, host-based IDS is loaded on a particular host for monitoring, and if loaded into the DMZ as suggested in this case would not be able to monitor the SQL server at all.
2. Which security control can best be described by the following? Because normal user behavior can change easily and readily, this security control system is prone to false positives where attacks may be reported based on changes to the norm that are “normal,” rather than representing real attacks.
A. Anomaly based IDS
B. Signature-based IDS
C. Honeypot
D. Honeynet
Correct Answer and Explanation: A. Answer A is correct, because anomaly based IDS utilizes rules and network patterns of behavior to determine if an attack has occurred. When the traffic patterns change, the IDS may be confused and determine that the change in network behavior indicates an attack.
Incorrect Answers and Explanations: B, C, and D. Answer B is incorrect, because signature-based IDS systems compare network traffic against signature files looking for matches in the traffic patterns. Changes in the normal network behavior would not cause these IDS types to generate false positives since they are simply checking traffic against a signature file, which would not be impacted by traffic pattern changes. Answer C is incorrect, because a honeypot does not trigger alerts based on legitimate user activity. An attack must target a honeypot directly for it to generate an alert. Answer D is incorrect, because a honeynet does not trigger alerts based on legitimate user activity. An attack must target a honeynet specifically for it to generate an alert.
3. Your network is configured to use an IDS to monitor for attacks. The IDS is network-based and has several sensors located in the internal network and the DMZ. No alarm has sounded. You have been called in on a Friday night because someone is claiming their computer has been hacked. What can you surmise?
A. The misconfigured IDS recorded a positive event
B. The misconfigured IDS recorded a negative event
C. The misconfigured IDS recorded a false positive event
D. The misconfigured IDS recorded a false negative event
Correct Answer and Explanation: D. Answer D is correct, because if a computer has been hacked and an IDS has not detected it, then a false negative has occurred. A false negative is when identification of an attack has failed, thus no event has been triggered or alarm has been sounded, but an event has actually occurred and was not caught.
Incorrect Answers and Explanations: A, B, and C. Answer A is incorrect, because if a positive event had been detected, alarms would have been generated. Answer B is incorrect, because a negative event is a true negative event, when no hack attempt has occurred. This is not a negative event because a hack took place that the IDS failed to detect, which makes it a false negative, not a negative. Answer C is incorrect, because during a false positive event no security breach is taking place; however, alarms are sounded and the IDS believes that an unauthorized access attempt is taking place.
4. You have installed an IDS that is being used to actively match incoming packets against known attacks. Which of the following technologies is being used?
A. Stateful inspection
B. Protocol analysis
C. Anomaly detection
D. Pattern matching
Correct Answer: D. Answer D is correct.
Incorrect Answers and Explanations: A, B, and C. Answer A is incorrect, because stateful inspection is when a firewall is able to keep track of the network connection between two devices and apply block or allow for the connection, and not just for individual packets being transmitted. Answer B is incorrect, because protocol analysis is when data is captured from the network and then reviewed. Answer C is incorrect, because anomaly detection is when traffic is evaluated and determined to be normal based on a configured rule set. Patterns are not used during anomaly detection.
5. You have been reading about the ways in which a network-based IDS can be attacked. Which of these methods would you describe as an attack where an attacker attempts to deliver the payload over multiple packets over long periods of time?
A. Evasion
B. IP Fragmentation
C. Session splicing
C. Session splicing
D. Session hijacking
Correct Answer and Explanation: C. Answer C is correct, because typically IDS systems notice patterns of attack. By dividing data into multiple packets and delivering these over time the IDS will have greater difficulty recognizing the attack. This technique is called session splicing.
Incorrect Answers and Explanations: A, B, and D. Answer A is incorrect, because evasion is a general term used to refer to the behavior of attempting to bypass or evade an IDS. Answer B is incorrect, because IP fragmentation is the process of taking large IP packets and breaking them into smaller packets for transmission. There is multiple attack methods that exist utilizing fragmented IP packets, most of them are DoS attempts. Answer D is incorrect, because session hijacking is when an attacker manipulates a valid session to gain unauthorized access. These attacks have many forms, but one example is a man-in-the-middle attack, where the attack is positioned as a middle point between two valid sources and is intercepting and possibly manipulating data between the two entities.
6. You have been asked to explore what would be the best type of IDS to deploy at your company site. Your company is deploying a new program that will be used internally for data mining. The IDS will need to access the data mining application’s log files and needs to be able to identify many types of attacks or suspicious activity. Which of the following would be the best option?
A. Network-based IDS that is located in the internal network
B. Host-based IDS
C. Application-based IDS
D. Network-based IDS that has sensors in the DMZ
Correct Answer and Explanation: C. Answer C is correct, because by deploying application-based IDS you can focus specifically on the log files of data mining application. Other types of IDS are typically broader in their scope and would be complex to figure and deploy. Since the need is to monitor activity pertinent to a particular application, application-based IDS is the best choice.
Incorrect Answers and Explanations: A, B, and D. Answer A is incorrect, because a network-based IDS solution would cover well beyond just a single application, and would require complex configuration and tuning in order to reduce false positives. Since a single application is all that requires monitoring, this solution is too broad based on the needs and would make it difficult to pinpoint specific activity targeting the application. Answer B is incorrect, because host-based IDS will cover all activity on a particular host and not just on a particular application. Host-based IDS is narrower than network-based IDS, but still would contain much more content than required. Answer D is incorrect, because a network-based IDS solution in the DMZ would cover well beyond just a single application, and would require complex configuration and tuning in order to reduce false positives. Since a single application is all that requires monitoring, this solution is too broad based on the needs and would make it difficult to pinpoint specific activity targeting the application. Also, the application is mentioned to be internal; thus, an IDS located in the DMZ would most likely not catch any suspicious traffic targeting this application.
7. You are a Microsoft engineer working on a new project. You need to configure a secure environment for systems and their users to perform networking functions. You want to achieve this through Windows Firewall. Which of the following correctly describes the MS recommended settings for this firewall service?
A. The Windows Firewall service should be enabled for protecting all profiles on all incoming interfaces.
B. The Windows Firewall service should be enabled for protecting all administrator profiles on all interfaces.
C. The Windows Firewall service should be enabled for protecting all profiles on all public interfaces.
D. The Windows Firewall service should be enabled for protecting all profiles on all interfaces.
E. The Windows Firewall service should be enabled for protecting all standard user profiles on all private interfaces.
Correct Answer and Explanation: D. Answer D is correct, because by protecting all profiles on all interfaces you have allowed the firewall to create a secure network scenario. Regardless of the user that is logged on, or the interface that is used, the firewall will be in place protecting the local machine.
Incorrect Answers and Explanations: A, B, C, and E. Answer A is incorrect, because by only enabling the firewall on incoming interfaces, there may be interfaces left unprotected, thus allowing for the potential for a security breach. Answer B is incorrect, because by enabling the firewall alone on administrator profiles, when other users log onto the machine that are not administrators they will not be protected, thus allowing for the potential for a security breach. Answer C is incorrect, because by only enabling the firewall on public interfaces, there may be interface left unprotected, thus allowing for the potential for a security breach. Answer E is incorrect, because by only enabling the firewall on standard user profiles on private interfaces, when other users log onto the machine that are administrators they will not be protected, thus allowing for the potential for a security breach. Also, if standard users utilize interfaces that are not classified as private, then they will also be unprotected.
8. Dan is a user on your network. Computer policies prevent him from utilizing file sharing while he is connected to the company network but he needs to be able to share files while he is working from home. What would you do to accomplish this request?
A. Use the MMC with the Windows Firewall with Advanced Security snap-in and change the private profile to allow incoming connections.
B. Use the MMC with the Windows Firewall with Advanced Security snap-in and change the public profile to allow incoming connections.
C. Use the Windows Firewall from within the control panel to allow file sharing.
D. Use the MMC with the Windows Firewall with Advanced Security snap-in and change the domain profile to allow incoming connections.
Correct Answer and Explanation: A. Answer A is correct, because working from a home network is considered a private network, so by changing the private profile to allow incoming connections, Dan will be able to share files while working from home.
Incorrect Answers and Explanations: B, C, and D. Answer B is incorrect, because since Dan is working from home he will not be using the public profile. The public profile is used in public settings, like a wi-fi hot spot or other public location. Answer C is incorrect, because if inbound traffic is blocked allowing file sharing will not be effective. The specific profile in use must allow the inbound connections for file sharing to be successful. Answer D is incorrect, because if the user is not on the corporate network the domain profile will not be in use. So changes to the domain profile will not be in effect while the user is working from a home network.
9. Sam is a network administrator for a small company that has 15 Vista Business computers all joined to a domain. When checking the logs on the domain controller, he notices that there are errors communicating with one particular computer. When he checks the computer, it is able to access the Internet, file servers, and is able to communicate with the Domain Controller that was reporting the errors. What is the most likely cause of the errors?
A. The Vista PC’s firewall profile is set to Public.
B. The Vista PC’s firewall profile is set to Private.
C. The Vista PC’s firewall profile is set to Domain.
D. The Vista PC’s firewall profile is set to Block All Incoming Connections.
Correct Answer and Explanation: A. Answer A is correct, because when the Vista firewall is set to Public outbound connections are not restricted, which explains why all attempts outbound from the machine are successful, but inbound traffic is restricted but not blocked, which explains why the domain controller is showing errors in attempting to connect to the PC, but connections to other locations in the network are error free. In order to remedy this issue, change the Vista firewall configuration to change the profile setting to the Domain profile.
Incorrect Answers and Explanations: B, C, and D. Answer B is incorrect, because setting the profile to Public will not allow the required traffic to a domain controller. The profile should be set to Domain to allow the proper connectivity. Answer C is incorrect, because if the firewall would have been set to Domain, then connectivity errors would not be occurring on the domain controller when trying to connect to this client. Answer D is incorrect, because blocking all incoming connections would not allow even exception traffic to enter the machine. All traffic inbound is blocked.
10. Your manager has asked you to install and configure a server to run the Cisco Security Agent Management Console. The server you choose has the following specs: Windows Server 2003 SP1, 1.2 Ghz processor, 2 GB memory, a 20 GB hard drive with two partitions, one with 4 GB of free space on an NTFS partition and one with 4 GB of free space on a FAT32 partition. What must you do to install the Management Console?
A. Nothing, this configuration will support the CSA MC.
B. You must add an additional 2 GB of memory.
C. You must install Service Pack 2 for Windows Server 2003.
D. You must add an additional hard drive with 9 GB of free space on an NTFS partition.
Correct Answer and Explanation: D. Answer D is correct, because the Cisco Security Agent Management Console requires a minimum of 9 GB of free disk space. In this case, each disk drive only has 4 GB of free disk space, thus requiring an additional hard drive with a minimum of 9 GB of free disk space available to install the Cisco Security Agent Management Console.
Incorrect Answers and Explanations: A, B, and C. Answer A is incorrect, because an additional hard drive is required on the machine for the Cisco Security Agent Management Console to be installed. Answer B is incorrect, because the minimum random access memory (RAM) requirement has already been met, so additional RAM is not necessary. Answer C is incorrect, because Windows Server 2003 SP1 is within the minimum requirements. SP2 is not required to run the Cisco Security Agent Management Console.
11. You are configuring some of the advanced features of the Windows XP firewall. You want to block the client machine from responding to pings. Which of the advanced setting types would you need to change to accomplish this?
A. Network connection settings
B. Security logging
C. ICMP
D. None of the above
Correct Answer and Explanation: C. Answer C is correct, because ICMP is the protocol that is used when a PING command is issued, received, and responded to. By blocking ICMP, the machine will not respond to pings because it will not receive the initial request for the ping.
Incorrect Answers and Explanations: A, B, and D. Answer A is incorrect, because network connection settings allow you to manage the properties of your network cards, and not the ports coming into the host. Answer B is incorrect, because security logging will not change the ports that a particular host is listening to, and it only documents what is taking place on the host based on your auditing configuration settings. Answer D is incorrect, because there is a correct answer in the list. C is the correct answer.
12. You have decided to use a third-party pop-up blocker solution as opposed to the built-in Microsoft Internet Explorer pop-up blocker. You are looking at the Anti-Spy feature of the Yahoo! Toolbar. Which of the following is NOT one of the three available options for scanning?
A. Scan at Launch
B. Scan for Tracking Cookies
C. Scheduled Scan
D. Check for Updates on Startup
Correct Answer and Explanation: C. Answer C is correct, because scheduled scan is not an option available from within the Yahoo! Toolbar.
Incorrect Answers and Explanations: A, B, and D. Answer A is incorrect, because Scan at Launch is available with the Yahoo! Toolbar. Answer B is incorrect, because Scan for Tracking Cookies is available with the Yahoo! Toolbar. Answer D is incorrect, because Check for Updates on Startup is available with the Yahoo! Toolbar.
13. You are deciding between a behavior-based IDS and signature-based IDS. Which of the following are positive characteristics of signature-based IDS?
A. Examines ongoing traffic
B. Uses a database of current attack signatures
C. Examines ongoing activity on the system
D. All of the above
Correct Answer and Explanation: D. Answer D is correct, because signature-based IDS uses a database of current attack signatures for comparison while it is reviewing traffic, as well as examining ongoing traffic and ongoing activity on the system.
Incorrect Answers and Explanations: A, B, and C. Answer A is incorrect, because this is not the only positive characteristic of signature-based IDS. Answer B is incorrect, because this is not the only positive characteristic of signature-based IDS. Answer C is incorrect, because this is not the only positive characteristic of signature-based IDS.
14. A user contacts the helpdesk to gain assistance in unblocking port 39873, which is the customized port she has assigned to an application she runs. The client application must make an outbound connection on port 80, and then the server side responds on port 39873, which is currently being blocked inbound. In what type of product would the action of unblocking a port take place?
A. Pop-up blocker
B. Port configuration tool
C. Software firewall
D. Adware tool
Correct Answer and Explanation: C. Answer C is correct, because a software firewall protects the local host from unauthorized traffic by monitoring local ports and protocols. By unblocking or white-listing the port will allow the server to respond on the correct port.
Incorrect Answers and Explanations: A, B, and D. Answer A is incorrect, because a pop-up blocker prevents unauthorized windows from launching as a user browses the Internet. It does not examine ports, it just blocks pop-ups. Answer B is incorrect, because a port configuration tool is a fictional tool. Answer D is incorrect, because port blocking is typically not performed in adware tools. Adware tools may use ports to identify malicious adware, but they are not used to authorize particular ports on the client. Adware tools function to block adware on a host.
15. You have a user that has been calling to complain that as she is browsing the Internet she frequently receives a pop-up message asking her to install antivirus software. She states that she has gone through the install four times and she doesn’t understand why she is still receiving this message from time to time. She wants you to perform the installation to be sure it is being performed correctly and so that it will not have to be continually repeated. What could be happening on this user’s machine to create these circumstances?
A. Her antivirus software is out-of-date, and she must renew it before the pop-ups for reinstall will stop.
B. She had to be a local administrator on the machine for the install to complete successfully, and therefore she isn’t able to complete the install herself.
C. The pop-up message was generated by the corporate antivirus server and was sent out mistakenly. You must correct the issue on the antivirus server.
D. This user has adware on her machine and the pop-up to install antivirus is not an actual antivirus installation window. The user’s machine should be scanned and cleaned.
Correct Answer and Explanation: D. Answer D is correct, because pop-up messages oftentimes will claim that your machine requires antivirus software or software that improves your network connection and that the user must click to install. These types of pop-ups are considered adware and can be malicious in nature, because they may carry Trojans or spyware to be installed once the user clicks the pop-up. Any type of repeating pop-ups that have not been generated by the administrator should prompt a scan and clean up on that machine immediately.
Incorrect Answers and Explanations: A, B, and C. Answer A is incorrect, because whether or not her local software is out-of-date, it does not impact a pop-up of this type. The pop-ups pop up to be clicked upon and it is unimportant as to the status of the local antivirus software. Answer B is incorrect, because the pop-up is an unwanted threat, and whether the logged on user is or is not a local administrator on the local host is immaterial to the pop-up. Answer C is incorrect, because the pop-up seems to be triggered by browsing the Internet. Also, corporate antivirus installations will typically take place in a silent mode so as not to disturb the user. The fact that a pop-up is taking place on a reoccurring basis should tell you that this isn’t a routine administrative installation.
1. You are the security administrator for Versa Corp. You have been assigned the task of creating a “honey pot” server on the company’s Internet DMZ. You have decided to use virtualization and a VM for this purpose. One of the best reasons for using a VM is
A. VMs run Windows only and cannot have security template applied to them
B. VMs can be rapidly restored when breached
C. VMs cannot join the production Active Directory
D. VMs are not vulnerable to viruses
Correct Answer and Explanation: Correct answer is B. VMs can be rapidly restored if they are breached. By using the snapshot features or using a template, a new VM can quickly be restored to a known state without the breach that was detected.
Incorrect Answers and Explanations: Answer A is incorrect because VMs are just like physical machines and can have security templates applied to them the same as any physical server. Answer C is incorrect because a VM can join an Active Directory and can even be a domain controller. Answer D is incorrect because just like a physical server, virus attacks are capable of compromising the server.
2. Which is a benefit of virtualization?
A. Lower operating system costs
B. Reduced bandwidth requirements
C. Reduced hardware costs
D. Reduced need for backups
Correct Answer and Explanation: Correct answer is C. Converting physical servers to virtual servers allows consolidating on to a smaller number of physical servers. It is easily possible to between 7 and 35 VMs running on a single physical server. This is a significant cost reduction for hardware costs.
Incorrect Answers and Explanations: Answer A is incorrect because you still must license your operating systems running on the VMs. You may be able to realize some cost savings by leveraging advanced licensing from software vendors, but there are specific rules and limitations for these programs. Answer B is incorrect because the bandwidth requirements of the virtual servers will be similar to the physical server they replaced. Answer D is incorrect because VMs are easier to restore, but this does not remove the requirement that they be backed up using either traditional methods or a combination of snapshots and backups or replication.
3. You are the security administrator for Versa Corp. You need to have three VMs running on HP DL380 servers. There are IBM x3350 servers also running the same hypervisor and processor family with available resources. You have moved your VMs to the IBM servers. What should you do to configure your VMs to run on the IBM servers?
A. Replace the network and RAID controller drivers on all the VMs immediately after powering them up
B. Replace only the RAID controller drivers
C. Replace only the network drivers
D. Nothing
Correct Answer and Explanation: Correct answer is D. VMs have the same hardware drivers when running on the same hypervisor. The hypervisor isolates the VMs from differences in the physical hardware.
Incorrect Answers and Explanations: Answers A, B, and C are incorrect because the VM never sees the physical network or RAID controllers. The hypervisor and the virtual drivers ensure that all the VMs see the same device drivers regardless of the physical resources.
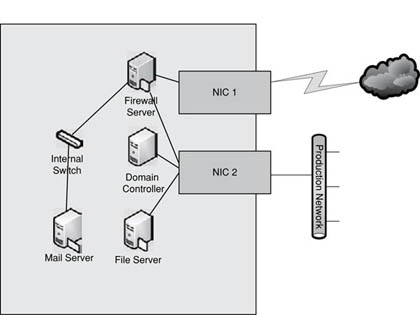
4. You are the security administrator for Versa Corp. You have been tasked with designing a single server solution for the remote branch offices. You must have in your solution:
A. A Linux-based firewall
B. A mail server in a DMZ
C. A domain controller
D. A file server
Correct Answer and Explanation: The system administrator has created a virtual host to run the necessary VMs and has asked you how you want the NICs connected to the virtual servers. You have provided him with the diagram shown in Figure 5.14.
FIGURE 5.14
Connecting N ICs to a Virtual Server
This solution
A. Fails to meet the requirements specified
B. Exposes the virtual servers to the open Internet
C. Prevents users from receiving their e-mail
D. Meets all requirements
The correct answer is D. By using both internal network connections and managing the external physical NICs, all requirements have been met and a secure environment can be deployed to the remote office.
Incorrect Answers and Explanations: Answer A is incorrect because all requirements have been met. Answer B is incorrect because only the firewall is connected to NIC 1, which is connected to the Internet. There is no direct path to the Internet from any other server. Answer C is incorrect because the mail server is connected to the internal switch with the firewall. The firewall has its De-Militarized Zone (DMZ) ports connected to this internal switch. Users should be able to access their e-mail through NIC 2 to the firewall then be routed to the internal switch connected to the e-mail server.
5. A VM is hosted on a server you are going to retire. The host server is not connected to a SAN but is connected to a network. You have access to the administrator account. You need to move it to another host. The fastest way to accomplish this task is to
A. Locate the VM configuration file and the virtual hard disk file; use Service Control Point (SCP) to copy these files to the new server
B. Locate the virtual disk file for the VM and use the backup solution to back up this file to tape; restore this file to the new server
C. Locate the configuration file for the VM and use the backup solution to backup this file to tape; restore the configuration file to the new server
D. Use SFTP to create a snapshot of the VM and copy it to the new server
Correct Answer and Explanation: The correct answer is A. Because most hypervisors are based on Linux, the root user account is typically prevented from using FTP for file transfers. Being based on Linux does not mean there is a full Linux OS. It is typically a specially tuned version that can support most of the TCP/IP protocols. SCP, secure copy, is part of the Secure Shell (SSH) implementation and is normally allowed because it has the limited functionality of only being able to securely transfer files. You must copy the configuration file and the virtual hard disk files to move the VM.
Incorrect Answers and Explanations: Answer B is incorrect because it will take longer to backup the virtual hard disk file to tape than to use the network to copy the file to the new server. The virtual hard disk is also only part of the solution. If this is all you have, it is possible to create a new VM and attach the copied virtual hard disk file to recover the VM. Answer C is incorrect because the configuration file alone is not enough to move the VM to the new server. The tape solution is also a longer process than using the network to transfer the files. Answer D is incorrect because SFTP will not create a snapshot. This is Secure File Transfer Protocol for sending encrypted files via FTP.
6. You are the security administrator of Versa Corp. You have several “honey pot” virtual servers running on a physical host along with production virtual servers. You notice that one of them has been breached. You must move quickly to isolate this server. You need to maintain the server intact so it can be analyzed but must maintain the security of the organization. Which action will accomplish the required goals?
A. Immediately log on to the affected server and shut it down; once shutdown, make a copy of the virtual hard disk file and export it to your laptop for analysis
B. Immediately log on to the hypervisor console and disconnect the virtual network card; mount the ISO file for the analysis tools to the virtual DVD drive and install the analysis tools
C. Immediately shutdown the physical host; disconnect all NICs from the physical host and load your security analysis tool to this server
D. Immediately log on to the affected server and shut it down; disconnect the virtual hard disk from the virtual server and mount it to another virtual server running the analysis tools
Correct Answer and Explanation: The correct answer is B. Disconnecting the virtual NIC will isolate the VM from the network without changing anything on the virtual server. Mounting the ISO file to the virtual DVD will allow you to load analysis tools onto this server. You can always access a VM from the hypervisor console of the physical host. This method is the best way to preserve the compromised server for analysis without compromising the security of the rest of the network.
Incorrect Answers and Explanations: Answer A is incorrect because shutting down the server may mask the compromise or payload of the attack. Making a copy and attaching it to your laptop could import the threat into the production network or otherwise infect your laptop. Answer C is incorrect because disconnecting the NICs from the physical host will disconnect the production VMs along with the infected VM. When this physical host is powered back up, the compromised virtual server is still there and connected to the network. Answer D is incorrect because connecting the virtual hard drive to another VM may also infect or compromise that VM. It may also alter the virtual hard drive and prevent a thorough analysis.
7. You are the security administrator of Versa Corp. You have recently noticed a lot of VMs on your physical hosts that are powered off or have not been accessed in over 2 weeks. You have decided to remove the powered down VMs. What is the best method of removing these VMs?
A. Use the console for your hypervisor and delete the VM and its associated virtual hard disk
B. Use the SAN console to remove the logical unit number (LUN) associated with each VM
C. Notify the owners of the VM that you are going to remove them from the physical server; remove the virtual hard drive but leave the virtual server configuration file in case they need the server again later
D. Use the hypervisor console to convert the VMs to templates in case they are needed again at a later date
Correct Answer and Explanation: The correct answer is A. Using the hypervisor console to remove the VM and its associated virtual hard drive will completely remove it from the physical host. If it is needed again, it will need to be recreated. It is a good practice to remove unused VMs to prevent potential security problems and to free resources on the physical hosts and the storage.
Incorrect Answers and Explanations: Answer B is incorrect because removing storage logical unit numbers (LUNs) will remove all the VMs loaded into that location. There may be running VMs in that storage location that you did not want to remove. Answer C is incorrect because while notifying the owners of the VMs is a good thing to do, removing the virtual hard drive will destroy the data on the VM. The configuration file will not allow you to recreate the VM. Answer D is incorrect because converting a VM to a template will not remove it from the server.
8. You are the security administrator for Versa Corp. You have been asked to virtualize 10 security servers without altering their configurations. Your manager wants to retain the physical servers just in case there is a problem later. What is your best course of action to accomplish the assigned tasks?
A. Build new VMs on the physical host to match the security servers, and once loaded, you copy the data files from each of the original server to the virtual servers; you leave the original servers online until the new servers are verified as working
B. You copy the disk drives of the original servers to the SAN; once completed you create new VMs and attach the data on the SAN to the VM; you shut down the original servers
C. You use a physical to virtual migration tool to copy the disk drives of the physical servers to the new VMs; once completed, you shut down the original server and power on the new virtual server
D. You create a new VM and use a bulk copy utility to copy all the data from the source servers to the new VMs; when complete, you leave the original servers online until the new servers are verified
Correct Answer and Explanation: The correct answer is C. Using a physical to virtual migration tool copies all the configuration and settings to the virtual hard disk without altering the configuration of the source. Once complete, the original can be powered down and the new virtual server powered on.
Incorrect Answers and Explanations: Answer A in incorrect because just copying the data files will not get all the configuration information from the original server. Even if this did work, you would have two servers with the same name and IP address online at the same time. This would cause a conflict. Answer B is incorrect because merely copying the files to the SAN will not make them useable on the VMs. The data must be copied to the virtual hard disk, not just a folder on the SAN. Answer D is incorrect because just copying the file to the virtual hard disk may not allow them to be used by the new VM. You also left the original servers online so both a name and IP conflict would exist if the copy did work.
9. You are the security administrator for Versa Corp. You have recently moved the virtual hard disk file for the virtual firewall to the D drive on your physical host. When you try to start the VM you receive the message, “The virtual hard disk cannot be found.” What action should you take to correct the problem?
A. Rename the virtual hard drive and try to restart the VM
B. Edit the boot.ini file of the VM to point to the D drive
C. Mount the virtual hard disk file to another VM and edit the /etc/hosts, allow file
D. Edit the VM configuration file to point the path of the virtual hard disk to the D drive
Correct Answer and Explanation: The correct answer is D. The VM configuration file contains the location of the virtual hard disk file. If you recently moved this file, you can edit this file to specify the new location.
Incorrect Answers and Explanations: Answer A is incorrect because renaming the virtual hard disk file will still not tell the configuration file where to find it. You would still need to edit the configuration file with the new path and file name to start the VM. Answer B is incorrect because you cannot edit the boot.ini file on the virtual hard disk. Even if you could, it still would not tell the configuration file where to find the virtual hard disk file. Answer C is incorrect because this would also not tell the VM configuration file where the virtual hard disk file was located.
10. You are the security administrator for Versa Corp. Your manager has given you a new server to develop and test a new security design. You want to be able to test the performance and capabilities of both Windows and Linux-based servers. You want to minimize the amount of time you spend building and rebuilding servers for testing. What is your best course of action to accomplish your goals?
A. Build a physical virtualization host server and create the necessary number of Windows and Linux VMs; configure each VM for your test; after the test, delete the VMs and recreate them for the next round of tests
B. Build a physical virtualization host server and create the necessary number of Windows and Linux VMs; take snapshots of each server; configure each VM for your test; after the test, restore the VMs using the snapshots before the next round of tests
C. Build a physical virtualization host server and create the necessary number of Windows and Linux VMs; configure each VM for your test; convert each configured VM to a template; after the test, use the templates to recreate the VMs for the next round of tests
D. Build a physical virtualization host server and create the necessary number of Windows and Linux VMs; configure each VM for your test; after the test clone the VMs for the next round of tests
Correct Answer and Explanation: The correct answer is B. Once the VMs are all created, taking a snapshot of them will allow you to quickly revert back to a known good state without having to remove anything or reconfigure to get back to a clean state. You would simply apply the new configuration for the next round of tests.
Incorrect Answers and Explanations: Answer A is incorrect because this has a lot of additional work to create, configure, test, delete, recreate for each round of test configurations. You would spend most of your time reloading operating systems instead of testing security configurations. Answer C is incorrect because once a VM is converted to a template it cannot be started. If you create templates from the basic VMs, you could use those templates to recreate the VMs. Answer D is incorrect because you are using a previous configuration to restart your tests. A clone maintains the settings of the VM being cloned. Your test would be skewed because previous configuration would still be present.
11. What is a benefit of application virtualization?
A. Applications are executed on the local clients instead of the application server
B. Applications are all Web based
C. Only Windows clients can access the published applications
D. Any device that can run the client can access the applications
Correct Answer and Explanation: Answer D is correct. Any device that can run the client software can access and run the published application. This is especially true of XenApp. There are clients for a wide variety of operating systems and processors.
Incorrect Answers and Explanations: Answer A is incorrect because the application is executed on the server, not the client device. Answer B is incorrect because applications do not need to be Web based to function on a terminal server. Answer C is incorrect because Windows is only one of several operating systems that can have a Terminal Services or XenApp client loaded.
12. You are the security administrator for Versa Corp. You have several executives that travel with laptops. Your internal applications servers publish applications for all users and are maintained in a secure fashion. Your executives complain that they cannot run a necessary financial application while disconnected from the corporate network. These executives are rarely disconnected longer than 10 days at a time. What action can you perform to satisfy the executive request and still maintain security?
A. Enable the Terminal Services Gateway and allow the executives to connect remotely using RDP over HTTPS
B. Enable application streaming for the financial application and set a timeout on checked out applications for 2 weeks
C. Load the financial application on the executive laptops and set a group policy to enable encryption on the data files
D. Load the latest XenApp client and configure it to use the highest level of encryption when connecting to the application server
Correct Answer and Explanation: The correct answer is B. Enabling application streaming and allowing the executives to check out the application will allow them to run when they are disconnected from the network. The timeout of 2 weeks will give the executives 14 days to connect back to the network before the application will stop working. This is well within the normal 10 days they travel.
Incorrect Answers and Explanations: Answer A is incorrect because while it is a secure method of delivering the application, it does not work when the executives are not connected to the network. Answer C is incorrect because loading the application on the laptops defeats the security policy by running sensitive application on individual desktops. Answer D is incorrect because the executives would still need to be connected to the network to access the applications and data.
13. You are the security administrator for Versa Corp. The company has decided to terminate the leased line T-1 between branch offices and the home office. All users use virtualized applications running on a terminal server to perform their daily work. All user files are located near the application servers. Each branch office is connected to the Internet using either a DSL line or a cable connection. Which action will allow users to continue working with the least amount of effort and still maintain the company’s security policy?
A. Set up a Terminal Server Gateway with a SSL certificate; direct all users to connect using the URL of the gateway to access the application servers
B. Have users create an Internet Protocol Security (IPSEC) tunnel to the application servers to continue working
C. Have the users generate personal certificates and use them to access the firewall to gain access to the application servers
D. Have the users load and configure the VPN client software for your firewall; then create a VPN connection to access the application servers to continue working
Correct Answer and Explanation: The correct answer is A. The easiest method is to set up a Terminal Services Gateway and load a SSL certificate on it. Users can use their Web browser to connect to the application servers securely and continue working.
Incorrect Answers and Explanations: Answer B is incorrect because the application server may not support IPSEC and they would still need to get past your firewall first. Answer C is incorrect because a personal certificate will not give them access through the firewall. They will only identify the user. Answer D is incorrect because while it might work it is considerably more work for both you and the users to gain access to the application servers.
14. You are the security administrator for Versa Corp. You have been asked to create 10 new VMs for a new development project. Each new VM needs have identical resources and configurations. You have a physical host running a hypervisor and connected to a SAN. What is the best method for accomplishing this task?
A. Create a new VM and load and configure the operating system; take careful notes and configure each identically until you have all 10 VMs
B. Create a new VM and load and configure the operating system; clone this VM nine more times and apply system customizations to each new VM
C. Create a new VM and load and configure the operating system; copy the virtual hard drive to create the other nine servers
D. Create a new VM and load and configure the operating system; use the SAN features to replicate the LUN to create the remaining servers
Correct Answer and Explanation: The correct answer is B. Cloning the first server and applying server customizations will generate 10 VMs with identical resources. You need to apply the server customizations to create unique System Identifiers (SID) for each VM.
Incorrect Answers and Explanations: Answer A is incorrect because creating each VM individually will take significantly more effort than cloning. Because we are configuring each individually, it is possible that a mistake will be made with this many servers being needed. Answer C is incorrect because just copying the virtual hard drive will not create the VMs. You would still need to run server customizations to generate a unique name and SID. Answer D is incorrect because replicating the SAN LUN will not create the VMs.
15. You are the security administrator for Versa Corp. You currently have a physical host running a hypervisor. You have a VM running a firewall application. You have received a new version of the software and need to set it up and configure it with a minimum of disruption to the users. The best method to accomplish the task would be to
A. Create a new VM and load the operating system and the new firewall software; connect it to the Test network; configure the software to match the production firewall; when testing is complete disconnect the virtual NIC on the production firewall from the Internet network and connect the new firewall to the Internet network
B. Create a new VM and load the operating system and the new firewall software; connect it to the Internet network; disconnect the virtual NIC on the production firewall from the Internet network and shut down the old firewall; configure the new firewall software
C. Load the new firewall software on the production firewall; configure the software
D. Create a snapshot of the production firewall; load the new firewall software on the production firewall; configure the software; if testing fails, you can reload the snapshot to restore the old configuration.
Correct Answer and Explanation: Answer A is correct. Creating the new VM and doing a fresh build of the operating systems and the new software will eliminate any current problems with the current server and allow for a completely fresh build. Connecting the new server to the Test network allows for testing without disruption of the users. Once complete, the virtual network can be connected to the Internet network and the old production firewall powered down. If a problem is discovered, the old server can be restarted.
Incorrect Answers and Explanations: Answer B is incorrect because users will be disrupted while the new firewall is being configured and tested. Answer C is incorrect because we are loading new software on a production firewall. This will cause a disruption with the users and there is no way to recover if there is a problem with the new software. Answer D is incorrect because it will cause a disruption with the users if there is a problem. We can always restore from the snapshot, but we would lose all the work that was done on the new software.
1. Your company is considering implementing a VLAN. As you have studied for your Security+ exam, you have learned that VLANs offer certain security benefits as they can segment network traffic. The organization would like to set up three separate VLANs in which there is one for management, one for manufacturing, and one for engineering. How would traffic move for the engineering to the management VLAN?
A. The traffic is passed directly as both VLANs are part of the same collision domain.
B. The traffic is passed directly as both VLANs are part of the same broadcast domain.
C. Traffic cannot move from the management to the engineering VLAN.
D. Traffic must be passed to the router and then back to the appropriate
Correct Answer and Explanation: D. Answer D is correct, because VLANs are logical segmentations in the network that are configured at Layer 3, routers must be involved in routing traffic between separate VLANs.
Incorrect Answers and Explanations: A, B, and C. Answer A is incorrect, because a collision domain exists at Layer 1 and VLANs exist at Layer 3. Collision domains occur when a data packet enters a network containing Level 1 devices, such as hubs and repeaters. When data is sent out on the media, these devices forward the data to all nodes on a particular segment flooding the network and thus creating a collision domain. Answer B is incorrect, because a broadcast domain exists at Layer 1 and a VLAN exists at Layer 3. A broadcast domain is another name for a collision domain. Collision domains occur when a data packet enters a network containing Level 1 devices, such as hubs and repeaters. When data is sent out on the media, these devices forward the data to all nodes on a particular segment flooding the network and thus creating a collision domain. Answer C is incorrect, because the rationale behind creating VLANs is typically to control traffic flow, but not to necessarily isolate it. VLANS are oftentimes created to segment the network in such a way that groups of machines that require frequent contact end up on the same VLANs. This functions to isolate broadcast traffic and in turn improves network effectiveness.
2. You have been asked to protect two Web servers from attack. You have also been tasked with making sure that the internal network is also secure. What type of design could be used to meet these goals while also protecting all of the organization?
A. Implement IPSec on the Web servers to provide encryption.
B. Create a DMZ and place the Web server in it while placing the intranet behind the internal firewall.
C. Place a honeypot on the internal network.
D. Remove the Cat 5 cabling and replace it with fiber-optic cabling.
Correct Answer and Explanation: B. Answer B is correct, because a DMZ will provide layered architecture that allows for firewall protection from direct Internet access, as well as firewall protection which prevents direct access to any machine that is deployed on the intranet.
Incorrect Answers and Explanations: A, C, and D. Answer A is incorrect, because IPSec encrypts the data to/from the client and the server, but it does not assist in ensuring that a particular part of the network, such as the internal network is secure. Answer C is incorrect, because a honeypot is used as a deterrent against attacks and is used to lure attacks to a designated target. If the internal network is accessible, there wouldn’t be anything in place to stop the same attacks from turning their attention on the internal network and creating a security breach. Answer D is incorrect, because changing the cable type will result in faster transmission speeds, but offers no protection to the internal network.
3. You have been asked to put your Security+ certification skills to use by examining some network traffic. The traffic was from an internal host whose IP address falls into an RFC 1918 range and you must identify the correct address. Which of the following should you choose?
A. 127.0.0.1
B. 10.27.3.56
C. 129.12.14.2
D. 224.0.12.10
Correct Answer and Explanation: B. Answer B is correct, because the three ranges of IP addresses RFC 1918 reserved are 10.0.0.0 to 10.255.255.255 (10/8 prefix), 172.16.0.0 to 172.31.255.255 (172.16/12 prefix), and 192.168.0.0 to 192.168.255.255 (192.168/16 prefix) and 10.27.3.56 falls within these ranges.
Incorrect Answers and Explanations: A, C, and D. Answer A is incorrect, because 127.0.0.1 is reserved as the loopback address and does not fall within the RFC outlined ranges. Answer C is incorrect, because 129.12.14.2 does not fall within the RFC outlined ranges. Answer D is incorrect, because 129.12.14.2 does not fall within the RFC outlined ranges.
4. You have been running security scans against the DMZ Web server and have obtained the following results. The Web server is also the externally facing DNS server. How should these results be interpreted?
C:\>nmap -sT 192.168.1.2
Starting nmap V. 3.91
Interesting ports on (192.168.1.2):
(The 1,598 ports scanned but not shown below are in state: filtered)
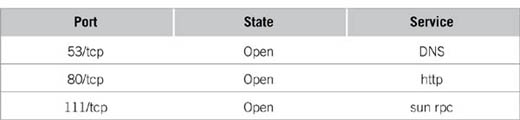
Nmap run completed −1 IP address (1 host up) scanned in 409 s.
A. Port 80 and 53 are expected but TCP port 111 should not be open
B. Port 80 and 111 should not be open but TCP port 53 should be open
C. UDP port 80 should be open to the DMZ
D. TCP port 25 should be open to the DMZ
Correct Answer and Explanation: A. Answer A is correct, because the roles described as running on the server are Web services and DNS. Port 80 is typically used for Web services and port 53 is used for DNS. These ports are expected to be open because they are in use for specific services.
Incorrect Answers and Explanations: B, C, and D. Answer B is incorrect, because port 80 must be open for Web services to function correctly. Answer C is incorrect, because UDP port 80 is not utilized for Web services or for DNS, which are the two services implemented on the server. Answer D is incorrect, because TCP port 25 is used for SMTP services. This server is not running SMTP services where it would require TCP port 25 to be open.
5. You have been asked to use an existing router and utilize it as a firewall. Management would like you to use it to perform address translation and block some known bad IP addresses that previous attacks have originated from. With this in mind, which of the following statements are accurate?
A. You have been asked to perform NAT services
B. You have been asked to set up a proxy
C. You have been asked to set up stateful inspection
D. You have been asked to set up a packet filter
Correct Answer and Explanation: D. Answer D is correct, because a packet filter will evaluate each packet and either block or allow the traffic from reaching its destination based on the rules defined. In this case the packet filter would examine the packets for the bad IP addresses and the action taken on the packets would be to drop or block them.
Incorrect Answers and Explanations: A, B, and C. Answer A is incorrect, because NAT is the process of mapping external to internal IP addresses, which is not being described here. Answer B is incorrect, because a proxy server functions as a middle device which passes information from a requesting client to a destination server, and then once a response is received from the server back to the proxy, the proxy passes the information back to the requesting client. Proxy servers can be used to speed up responses by caching content such as Web pages, and they can also be used for security purposes to keep the internal clients hidden from the external world. Answer C is incorrect, because stateful inspection is when a device, typically a firewall, keeps track of state of network connections. This allows the firewall to detect when packets have been modified or if they are not appropriate to be transmitted, but by only analyzing header information the firewall remains efficient.
6. Which security control can best be described by the following? Because normal user behavior can change easily and readily, this security control system is prone to false positives where attacks may be reported based on changes to the norm that are “normal,” rather than representing real attacks.
B. Signature-based IDS
C. Honeypot
D. Honeynet
Correct Answer and Explanation: A. Answer A is correct, because anomaly-based IDS specifically looks for changes in behavior as a sign of intrusion behavior. The problem with this is that if user habits or behavior changes as a part of the normal trends in an organization, the IDS will detect the change and raise an alarm, thus generating false positives.
Incorrect Answers and Explanations: B, C, and D. Answer B is incorrect, because signature-based IDS systems reply on signature files to detect attacks in the network. The user behavior is not considered or evaluated and thus would not have an impact on a signature-based IDS system’s attack perception. Answer C is incorrect, because a honeypot is used as a lure to distract attackers from valid network targets. Honeypots do not consider or evaluate user traffic and thus would not be impacted by changes in user behavior. They simply alert when attacked. Answer D is incorrect, because a honeynet is used as a lure to distract attackers from valid targets. Honeynets do not consider or evaluate user traffic and thus would not be impacted by changed in user behavior. They simply alert when attacked.
7. You have been asked to install a SQL database on the intranet and recommend ways to secure the data that will reside on this server. While traffic will be encrypted when it leaves the server, your company is concerned about potential attacks. With this in mind, which type of IDS should you recommend?
A. A network-based IDS with the sensor placed in the DMZ
B. A host-based IDS that is deployed on the SQL server
C. A network-based IDS with the sensor placed in the intranet
D. A host-based IDS that is deployed on a server in the DMZ
Correct Answer and Explanation: B. Answer B is correct, because a host-based IDS system installed on the SQL server will give you the capability to configure the IDS to focus specifically on the application you desire to protect.
Incorrect Answers and Explanations: A, C, and D. Answer A is incorrect, because a network-based IDS is a poor choice. Because a network-based IDS listens on the wire, there will be a lot more than just data from this specific application transversing the wire. This will make it more difficult for the administrator to focus in on the SQL server. Also, because traffic leaving the server will be encrypted, this presents a challenge for the network-based IDS system. Finally, this answer depicts the sensor being placed in the DMZ, and there is no indicator that the SQL database will transverse the DMZ, rendering the senor useless in protecting this specific application from internal attacks. Answer C is incorrect because a network-based IDS is a poor choice. Because a network-based IDS listens on the wire, there will be a lot more than just data from this specific application transversing the wire. This will make it more difficult for the administrator to focus in on the SQL server. Also, because traffic leaving the server will be encrypted, this presents a challenge for the network-based IDS. Answer D is incorrect because even though a host-based IDS is the correct choice, if the sensor for the IDS is placed on a server in the DMZ, this will not protect the SQL server in the intranet.
8. Your network is configured to use an IDS to monitor for attacks. The IDS is network-based and has several sensors located in the internal network and the DMZ. No alarm has sounded. You have been called in on a Friday night because someone is claiming their computer has been hacked. What can you surmise?
A. The misconfigured IDS recorded a positive event
B. The misconfigured IDS recorded a negative event
C. The misconfigured IDS recorded a false positive event
D. The misconfigured IDS recorded a false negative event
Correct Answer and Explanation: D. Answer D is correct, because a false negative describes an event where an attack has occurred and no alarm has been raised. Essentially the IDS systems falsely responded in a negative manner by not sounding an alarm.
Incorrect Answers and Explanations: A, B, and C. Answer A is incorrect, because a positive event occurs when an attack is taking place and rightly an alarm is generated. In this case an attack was occurring, however, no alarm was generated which means that a positive event was not recorded. Answer B is incorrect, because a negative event occurs when no attack is in progress and no alarm is sounded. This is not the situation described. Answer C is incorrect, because a false positive occurs when an alarm is sounded in error. This happens when an IDS system mistakenly identifies legitimate traffic as a threat and in response generates alerts. This is not the situation described in this question.
9. You have installed an IDS that is being used to actively match incoming packets against known attacks. Which of the following technologies is being used?
A. Stateful inspection
B. Protocol analysis
C. Anomaly detection
D. Pattern matching
Correct Answer and Explanation: D. Answer D is correct, because pattern matching or signature-based IDS systems monitor traffic and then compare it against known attacks to determine if an attack is occurring.
Incorrect Answers and Explanations: A, B, and C. Answer A is incorrect, because stateful inspection describes the method used by many firewalls to analyze the traffic stream to identify bad packets by analyzing header information. Answer B is incorrect, because protocol analysis describes the process of collecting packets from a network to analyze or inspect the packets at a later time. Answer C is incorrect, because anomaly detection is when an IDS system evaluates traffic patterns on a network, determines what is “normal” for that network, and then alerts when the traffic patterns change dramatically or suddenly.
10. You have been reading about the ways in which a network-based IDS can be attacked. Which of these methods would you describe as an attack where an attacker attempts to deliver the payload over multiple packets over long periods of time?
A. Evasion
B. IP fragmentation
C. Session splicing
D. Session hijacking
Correct Answer and Explanation: C. Answer C is correct, because session splicing is when attackers break up payloads and send them over a longer period of time in an attempt to bypass any IDS systems that may be deployed.
Incorrect Answers and Explanations: A, B, and D. Answer A is incorrect, because evasion is the term used to refer to the modifications made by attackers to attack methods in an attempt to bypass IDS systems, and not a specific attack. Answer B is incorrect, because IP Fragmentation is the process of breaking IP packets into smaller datagrams. There are multiple attack methods which attempt to exploit IP Fragmentation, such as IP Fragment Overwrite, IP Fragment Overrun, and IP Fragment Buffer Full. Answer D is incorrect, because session hijacking is a man-in-the-middle attack that involves an attacker positioning themselves between the client and the server to intercept data and hijack the session. Session hijacking can also occur when a cookie or token is stolen and used by an attacker to participate in a session.
11. You have been asked to explore what would be the best type of IDS to deploy at your company site. Your company is deploying a new program that will be used internally for data mining. The IDS will need to access the data mining application’s log files and needs to be able to identify many types of attacks or suspicious activity. Which of the following would be the best option?
A. Network-based IDS that is located in the internal network
B. Host-based IDS
C. Application-based IDS
D. Network-based IDS that has sensors in the DMZ
Correct Answer and Explanation: C. Answer C is correct, because by selecting an application-based IDS system, which would be tailored for the specific application you will be able to more readily monitor the application and its components and identify application targeted attacks.
Incorrect Answers and Explanations: A, B, and D. Answer A is incorrect, because a network-based IDS would encompass much more than a single application and it would be difficult to configure a network-based IDS to focus on a particular application when they are intended to monitor the broader scope of network traffic. Answer B is incorrect, because a host-based IDS system only focuses on a particular host and therefore may exclude components of a distributed application. Answer D is incorrect, because a network-based IDS would encompass much more than a single application and it would be difficult to configure a network-based IDS to focus on a particular application when they are intended to monitor the broader scope of network traffic. Also, placing sensors in the DMZ would only be beneficial if the application had components deployed in the DMZ, but the network traffic to be analyzed in the DMZ would reach well beyond just the scope of a single application.
12. You are about to install WinDump on your Windows computer. Which of the following should be the first item you install?
A. LibPcap
B. WinPcap
C. IDSCenter
D. A honeynet
Correct Answer and Explanation: B. Answer B is correct, because WinPcap is a prerequisite to the installation of WinDump.
Incorrect Answers and Explanations: A, C, and D. Answer A is incorrect, because LibPcap is not a prerequisite for installing WinDump. Answer C is incorrect, because IDSCenter is not a prerequisite for installing Win-Dump. Answer D is incorrect, because a honeynet is not a prerequisite for installing WinDump.
13. You must choose what type of IDS to recommend to your company. You need an IDS that can be used to look into packets to determine their composition. What type of signature type do you require?
A. File-based
B. Context-based
C. Content-based
D. Active
Correct Answer and Explanation: C. Answer C is correct, because content-based IDS systems can be configured to examine the contents of packets to determine their composition and will then take action based on the action configured in a matching rule set.
Incorrect Answers and Explanations: A, B, and D. Answer A is incorrect, because a file-based IDS does not examine packet composition. Answer B is incorrect, because a context-based IDS system does not examine packet composition. Answer D is incorrect, because an Active IDS does not examine packet composition. The idea with an Active IDS is that when an attack is detected the system will then move to stop the attack.
14. You have decided to implement split horizon DNS. You install two instances of DNS, and place one in the DMZ and one in the LAN. Which of these two DNS servers will become authoritative for your domain namespace?
A. Both the DMZ- and the LAN-based servers will be authoritative for your domain namespace
B. Only the LAN-based DNS
C. Only the DMZ-based DNS
D. Neither, the ISP is the only one who can be authoritative for a domain namespace
Correct Answer and Explanation: A. Answer A is correct, because the concept of split horizons DNS is that multiple servers are authoritative for your domain namespace. The benefit in this is that the externally facing DNS can have a limited number of records, thus keeping internal records safe from harm, while still maintaining a matching namespace internally and externally in the organization.
Incorrect Answers and Explanations: B, C, and D. Answer B is incorrect, because if only a single of the two servers was configured authoritative then the deployed model would not be split horizon DNS. With only the LAN-based DNS being authoritative, if the same namespace was in use internally and externally, the DMZ-based replica would potentially expose the internal records to the outside world. Answer C is incorrect, because if the DMZ-based DNS was the authoritative server for your domain namespace all records would be required to be registered in the DMZ and then replicated to the LAN-based instance. This would require firewall ports to be opened and configured as well as potentially expose the internal records to the outside world. Answer D is incorrect, because this statement is incorrect. Many companies house their DNS onsite.
15. One of your servers has a host-based IDS installation in place. The system has been generating many false positives and you would like to examine the network traffic that is going to and from the server. Which of the following tools is going to be able to successfully capture this data off the wire for you to analyze?
A. A protocol analyzer
B. An IDS snuffler
C. An NIDS system
D. A protocol stealer
Correct Answer and Explanation: A. Answer A is correct, because a protocol analyzer is a tool utilized to capture data off the network. It can be used to capture data and store it to analyze it at a later time, or it can be used to monitor real time data to and from a specific machine.
Incorrect Answers and Explanations: B, C, and D. Answer B is incorrect, because an IDS snuffler does not exist, it is a fictional component. Answer C is incorrect, because an NIDS system is a network intrusion system. These systems are configured to detect network intrusions on the network and alert the administrator through configured alarms. Typically an NIDS system does not monitor a single host, but instead an entire network segment. Answer D is incorrect, because a protocol stealer is a fictional component.
1. WEP uses which of the following encryption standards?
A. AES
B. ECC
C. RC4
D. DES
Correct Answer and Explanation: The correct answer is C. The RC4 encryption algorithm is a symmetric stream cipher. This is the encryption that WEP is based on.
Incorrect Answers and Explanations: Answer A is incorrect, because AES is the advanced encryption standard and is used by 802.11i. Answer B is incorrect, because ECC is elliptic curve cryptosystem and is an asymmetric standard that is not used by WEP. Answer D is incorrect, because DES is data encryption standard and is not used by WEP.
2. The medium for communications in a wireless system is
A. Cabling
B. Access point
C. Antenna
D. EM field
Correct Answer and Explanation: The correct answer is D. The medium for communications in a wireless system is EM field, the region of space that is influenced by electromagnetic radiation. (Unlike audio waves, radio waves do not require a medium such as air or water to propagate.)
Incorrect Answers and Explanations: Answer A is incorrect, because cabling is used for a wired network. Answer B is incorrect, because an AP is the termination point of the signal. Answer C is incorrect, because an antenna is used by an AP as the device to emanate the EM field.
3. The area over which the radio waves propagate from an electromagnetic source is known as the
A. Control zone
B. Fresnel zone
C. Footprint
D. Wavelength
Correct Answer and Explanation: The correct answer is B. The area over which the radio waves propagate from an electromagnetic source is known as the fresnel zone.
Incorrect Answers and Explanations: Answer A is incorrect. Answer C is incorrect, because the footprint is the surface space occupied by a structure or device. Answer D is incorrect, because the wavelength is the distance (measured in the direction of propagation) between two points in the same phase in consecutive cycles of a wave.
4. Wireless devices that are communicating directly to each other without an AP are said to be operating in what mode?
A. Peer to client mode
B. Ad-hoc mode
C. Independent mode
D. Infrastructure
Correct Answers and Explanations: The correct answer is B. The ad-hoc mode is geared for a network of stations within communication range of each other. Ad-hoc networks are created spontaneously between the network participants.
Incorrect Answers and Explanations: Answers A and C are distracters. Answer D describes an infrastructure, which consists of one or more APs as well as a distribution system (that is, a wired network) behind the APs that tie the wireless network to the wired network.
5. Which of the following is not a valid class for Bluetooth?
A. Class 0
B. Class 1
C. Class 2
D. Class 3
Correct Answer and Explanation: The correct answer is A. The class rating of Bluetooth refers to the power class of the radio transmitter in the device.
Incorrect Answers and Explanations: Answer B is incorrect because Class 1 is one of three classes for Bluetooth. Class 1 devices have a range of 100 M. Answer C is incorrect, because Class 2 is another class for Bluetooth. Class 2 devices have a range of 10 M. Answer D is incorrect, because Class 3 is another class for Bluetooth. Class 3 devices have a range of less than 10 M.
6. Why is a site survey performed?
A. Distribute wireless WEP/WPA/WPA2 keys
B. Find and remove unwanted access locations
C. Plan the design and topology of a wired network
D. Record current wireless signal strength and suggest improvements
Correct Answer and Explanation: The correct answer is D. The primary purpose of a site survey is to record current wireless signal strength and suggest improvements. Site surveys are used to map out the extent to which wireless networks are visible outside the physical boundaries of the buildings in which their components are installed.
Incorrect Answers: Answers A, B, and C are incorrect.
7. Tools like NetStumbler are primarily used for
A. Wireless intrusion detection
B. Site surveys
C. Sniffing and decoding emanations from a CRT
D. Attacking wireless systems
Correct Answer and Explanation: The correct answer is B. The primary use of tools like NetStumbler is that when used with wireless sniffers, they can be used in a site survey. Windows-based users would use NetStumbler and the UNIX/Linux-based user would use Kismet or Wireshark.
Incorrect Answers and Explanations: Answers A, C, and D are incorrect as NetStumbler is not used for wireless intrusion detection, decoding CRT-based data or attacking wireless systems. An example of NetStumbler is shown in Figure 7.7.
FIGURE 7.7 Clients Detected by NetStumbler
A. A method used to attack wired networks
B. A means to attack wireless networks
C. A passive sniffing tool
D. A tool used to set up a rogue AP
Correct Answer and Explanation: The correct answer is C. TEMPEST was designed to look at hardening devices to prevent emanations form items such as keyboards and CRTs. It is not used to attack wired networks, wireless networks, or to set up a rogue AP.
9. Sending unsolicited messages over Bluetooth is defined as
A. Bluecrashing
B. Bluejacking
C. Karma
D. Bluesnarfing
Correct Answer and Explanation: The correct answer is B. Sending unsolicited messages over Bluetooth is defined as Bluejacking.
Incorrect Answers and Explanations: Answer A is incorrect as blue-crashing is a distracter. Answer C, Karma is a wireless AP attack. Answer D is incorrect, as Bluesnarfing is the unauthorized access of information from a wireless device through a Bluetooth device.
10. Which type of attack is best defined by the unauthorized access of information from a wireless device through a Bluetooth device?
A. Bluecrashing
B. Bluejacking
C. Karma
D. Bluesnarfing
Correct Answer and Explanation: The correct answer is D. Bluesnarfing is the unauthorized access of information from a wireless device through a Bluetooth device.
Incorrect Answers and Explanations: Answer A is incorrect as blue-crashing is a distracter. Answer B is incorrect as the sending of unsolicited messages over Bluetooth is defined as Bluejacking. Answer C, Karma is a wireless AP attack.
11. Which of the following is the most effective approach against detecting rogue APs?
A. Enforce the use of static addressing
B. Perform yearly site surveys
C. Develop a policy that prohibits the installation of unauthorized APs
D. Install wireless intrusion detection systems
Correct Answer and Explanation: The correct answer is D. To prevent the installation of rogue APs, organizations should install wireless intrusion detection systems that can detect and alert administrators to the presence of unauthorized APs. Static addressing would not prevent someone for installing an unauthorized AP. Yearly site surveys would allow an unauthorized AP to operate for a long period of time before detection. Policies are only deterrents and would do nothing to prevent the installation of the rogue AP.
12. Van Eck phreaking is best defined as
A. Attacks against phone systems
B. A random signal with a flat power spectral density
C. To eavesdrop on the contents of the monitor using its electronic emissions
D. A special enclosure that acts as an EM capacitor
Correct Answer and Explanation: The correct answer is C. Van Eck phreaking is to eavesdrop on the contents of the monitor using its electronic emissions.
Incorrect Answers and Explanations: Answer A describes phone phreaking. Answer B describes white noise. Answer D describes a Faraday cage.
13. Sometimes a DoS attack can be unintentional. If your home wireless network is having intermittent problems in the afternoon and the evenings, the most likely issue is which of the following?
A. The AP is malfunctioning and should be replaced
B. Someone is attacking your network with a VOID 11 DoS attack
C. The wireless network is not configured correctly
D. Your cordless phone is using the same frequency as the wireless network and whenever someone calls or receives a call the phone jams the wireless network
Correct Answer and Explanation: The correct answer is D. The problem is most likely that a cordless phone or other wireless devices is jamming the wireless signal because it uses the same frequency. This is becoming more and more common as cordless phone manufacturers use the same frequency as APs.
14. James is worried about the security of the wireless network and as such has disabled SSID broadcasts. James has now made the statement that his wireless network cannot be hacked. How should you respond?
A. Sniffing the SSID is not possible once the SSID broadcast has been disabled
B. Once broadcast has been disabled, sniffing the SSID is only possible with specialized expensive equipment
C. James is correct only if 128-bit WEP has been enabled
D. Even with SSID turned off someone can still sniff the network
Correct Answer and Explanation: The correct answer is D. Answer D is correct. It is possible to turn off SSID on some APs. Disabling SSID broadcasts creates a “closed network.” If possible, SSID broadcasts should be disabled, although this will interfere with the capability of Windows XP to automatically discover wireless networks and associate with them. However, even if SSID broadcasts are turned off, it is still possible to sniff the network traffic and see the SSID in the frames.
Incorrect Answers: Answers A, B, and C are incorrect.
15. Which of the following about 802.11a is correct?
A. 802.11a and 802.11b work on the same frequencies
B. 802.11g uses DSSS
C. 802.11 a and 802.11b are incompatible
D. 802.11a has a max speed of 11 Mbps
Correct Answer: The correct answer is C.
Incorrect Answers and Explanations: Answers A, B, and D are incorrect, because the 802.11a and 802.11g standards define the operation of wireless networks with higher transmission rates. The 802.11a devices are not compatible with 802.11b, because they use frequencies in the 5-GHz band. Furthermore, unlike 802.11b networks, they do not use DSSS. 802.11g uses the same ISM frequencies as 802.11b and is backward-compatible with 802.11b devices.
1. When using DAC systems with ACLs, what permission or privilege gives users the ability to read and write to an access control object?
A. Write
B. Create
C. Execute
D. Modify
Correct Answer and Explanation: Answer D is correct. The “modify” permission allows users to both read and write to an access control object.
Incorrect Answers and Explanations: Answer A is incorrect because the ability to write to an object does not imply the ability to read from the object. Answer B is incorrect because the ability to create new objects does not imply the ability to read or write to the new objects. Answer C is incorrect because the ability to execute an object does not imply the ability to read or write to the object.
2. When using MAC, how is permission to access control objects controlled after a user has been authenticated?
A. By ACLs
B. By sensitivity levels
C. By identification
D. By user role
Correct Answer and Explanation: Answer B is correct. Sensitivity levels such as “secret” or “top-secret” are used to control access to objects.
Incorrect Answers and Explanations: Answer A is incorrect because ACLs are used by DAC, not MAC. Answer C is not correct because identification is a part of the authentication process and does not control access to objects. Answer D is incorrect because user roles are used in role-based access control, not MAC.
3. How does role-based access control differ from DAC?
A. Role-based access control requires that permissions be configured on every object and DAC does not
B. Role-based access control uses the ID of the user to help determine permissions to objects and DAC does not
C. Role-based access control uses the position of the user in the organization structure to determine permissions for objects and DAC does not
D. Role-based access control requires that every object have a sensitivity label and DAC requires that every object have an ACL
Correct Answer and Explanation: Answer C is correct. Role-based access control uses the position of the user in the organization structure or their role to determine the user’s permissions.
Incorrect Answers and Explanations: Answer A is incorrect because both role-based access control and DAC require that every object have permissions defined. Answer B is incorrect because DAC does use the ID of the user to determine their permissions. Answer D is not correct because role-based access control does not use sensitivity labels.
4. The Bell–La Padula formal model for access control is most similar to which access control model?
A. DAC
B. MAC
C. Role-Based Access Control
D. Clark–Wilson Access Control
Correct Answer and Explanation: Answer B is correct. The Bell–La Padula access control model specifies the use of sensitivity labels on every access control subject and object. MAC uses sensitivity labels in the same way.
Incorrect Answers and Explanations: Answer A is incorrect because DAC does not use sensitivity labels as outlined in the Bell–La Padula formal access control model. Answer C is incorrect as role-based access control uses roles or positions for access control rather than sensitivity labels. Answer D is incorrect because Clark–Wilson is another formal access control model, but it is a guideline for access control relating to integrity.
5. The Clark–Wilson formal access control model specifies a very important guideline related to account administration. What is this guideline and what does it mean?
A. Principle of least privilege Grant all the rights and permissions necessary to an account, but no more than what is needed.
B. Account administration Work hand-in-hand with the human resources or personnel office of the company to ensure that accounts can be authorized and created when employees are hired and immediately destroyed when they are dismissed.
C. Segregation of duties No single person should perform a task from beginning to end, but the task should be divided among two or more people to prevent fraud by one person acting alone.
D. Access control Provide access control subjects the ability to work with access control objects in a controlled manner.
Correct Answer and Explanation: Answer C is correct. The Clark–Wilson formal model provides guidelines related to segregation or separation of duties.
Incorrect Answers and Explanations: Answer A is incorrect because the principle of least privilege is not part of the Clark–Wilson formal model. Answer B is incorrect because this definition is only part of the definition for account administration. Answer D is not correct because the Clark–Wilson formal model does not define access control itself, just manners in which access controls can be used.
6. When performing account administration, the principle of least privilege is an important guideline to apply. Why is this principle so important?
A. Applying the principle of least privilege ensures that permissions are broken up based on job functions which can prevent fraud
B. Applying the principle of least privilege ensures that an access control policy is in place which can increase security by requiring frequent password changes
C. Applying the principle of least privilege ensures that users are guaranteed a minimum level of access to the access control objects that they need to work with which provides assurance in the form of availability
D. Applying the principle of least privilege ensures that users do not have more permission to an access control object than is necessary which can prevent users from accessing more than they should
Correct Answer and Explanation: Answer D is correct. By applying the principle of least privilege, you ensure that users are only able to access what they specifically need and no more. This prevents users from being able to access data that they should not be able to access.
Incorrect Answers and Explanations: Answer A is incorrect because this option describes role-based access control, not the principle of least privilege. Answer B is incorrect because the principle of least privilege has nothing to do with administrating an access control policy. Answer C is incorrect because the principle of least privilege does not provide for assurance.
7. When administering access control objects in a MAC system, what is an important part of an administrator’s duty?
A. Declassifying data when necessary
B. Removing ACLs when necessary
C. Deleting inactive accounts regularly
D. Replacing expired access control tokens when necessary
Correct Answer and Explanation: Answer A is correct. Declassifying access control objects is an important part of an administrator’s duty. This involves changing the sensitivity label for the objects as needed.
Incorrect Answers and Explanations: Answer B is incorrect because MAC systems do not use ACLs. Answer C is not correct because deleting inactive accounts is a function of account administration, not access control object administration. Answer D is incorrect because replacing expired tokens is also not a part of access control object administration.
8. You have been brought in as a security consultant for a programming team working on a new operating system designed strictly for use in secure government environments. Part of your role is to help define the security requirements for the operating system and to instruct the programmers in the best security methods to use for specific functions of the operating system. What method of access control is most appropriate for implementation as it relates to the security of the operating system itself?
A. MAC
B. DAC
C. RBAC
D. All of the above
Correct Answer and Explanation: Answer A is correct. MAC works at the operating system level and best fits this security requirement.
Incorrect Answers and Explanations: Answer B is incorrect because DAC does not meet government guidelines for a secure operating system. Answer C is not correct because role-based access control does not apply at the operating system level. Answer D is incorrect because answers B and C are incorrect.
9. You are designing the access control methodology for a company implementing an entirely new IT infrastructure. This company has several hundred employees, each with a specific job function. The company wants their access control methodology to be as secure as possible due to recent compromises within their previous infrastructure. Which access control methodology would you use and why?
A. RBAC because it is job-based and more flexible than MAC
B. RBAC because it is user-based and easier to administer
C. Groups because they are job-based and very precise
D. Groups because they are highly configurable and more flexible than MAC
Correct Answer and Explanation: Answer A is correct. Role-based access control is more flexible than MAC and fits the job-based need specified in the scenario.
Incorrect Answers and Explanations: Answer B is incorrect because RBAC is not user-based. Answer C is not correct because groups are not job-based. Answer D is incorrect because while groups are highly configurable and more flexible than MAC, they do not fit the need of working with each user’s role.
10. You have been brought in to analyze the overall security strength of a banking organization. As part of your analysis, you work with the existing security administrator to see what issues she has to deal with on a daily basis. She receives a help desk ticket stating that a teller issued a credit to his own account then authorized the credit so that he was able to prevent bouncing a check. According to the human resources department who called in the ticket, he said that he planned on removing the credit later after he got paid. The security administrator made a change to the security policies around one of the following areas. If she analyzed the issue correctly, which area did she change the policy for?
A. System logging to capture events similar to this in the future
B. Separation of duties to prevent a teller from issuing and authorizing a credit
C. System scanning to test other areas of the software for vulnerabilities similar to this
D. Log analysis to ensure that future events like this are flagged for follow-up.
Correct Answer and Explanation: Answer B is correct. The concept of separation of duties is intended to prevent events like this from occurring.
Incorrect Answers and Explanations: Answer A is incorrect because while additional logging helps, it does not solve the root cause of the problem and prevent it from happening again. Answer C is not correct because system scanning will not correct this problem. Answer D is incorrect because log analysis, while important, will not prevent this from happening.
11. Both identification and authentication play a role in access control. When analyzing a security infrastructure, you are tasked with documenting which elements of their security fall into identification versus authentication. Which option below correctly identifies these elements?
A. Identification: ID Badge, PIN, User ID
B. Identification: Fingerprint, User ID, Password
C. Authentication: Password, PIN, Visual ID Verification
D. Authentication: PIN, Fingerprint, Password
Correct Answer and Explanation: Answer C is correct. A password, PIN, and verified visual ID are all proof that the person is who they say that they are.
Incorrect Answers and Explanations: Answer A is incorrect because a PIN is proof of identity, not an identifier. Answer B is not correct because a password is also proof of identity, not an identifier. Answer D is incorrect because a fingerprint, until validated, is used as an identifier.
12. You are consulting for a small organization which does retail services. As part of your role, you must outline a security infrastructure and justify its cost to executives. Your biggest concern is around the lack of security in their point of sale system. Because credit cards are used for transactions in the point of sale system and it can be easily compromised, how would you justify the cost of an upgrade to executives?
A. Note the merits of the new system including how much faster it can process transactions, how much easier it is to integrate with other systems, and its support for faster hardware
B. Show what can happen with a real-time demonstration of how easily their current system can be compromised
C. Present the merits of enterprise security and design a full enterprise architecture with appropriate intrusion, detection, and access controls to work around the limitations of the existing point of sale system
D. Present an analysis of the pros and cons of upgrading including the potential cost of lost credibility in the event that the existing system is compromised
Correct Answer and Explanation: Answer D is correct. The most compelling argument for mitigating the security vulnerability here is the potential lost customers and credibility in the event of a compromise of the system.
Incorrect Answers and Explanations: Answer A is incorrect because while the system may be faster and have more features, that it not why you are suggesting that it be upgraded. Answer B is not correct because while a demonstration may show your penetration testing abilities, it does not explain the impact of the vulnerabilities and what that means to the business. Answer C is incorrect because a full enterprise security architecture, while nice, is not necessary for a small organization using a simple point of sale system.
13. You are working on an existing Windows Active Directory implementation. A problem has been identified where users are able to keep their passwords for 90 days instead of the company mandated 30-day policy. You’ve looked at the GPO defined at the domain level and the password expiration is set for 30 days. What could be the problem?
A. A policy at the OU level is setting the expiration for 90 days
B. A policy at the site level is setting the expiration for 90 days
C. A policy at the local level is setting the expiration for 90 days
D. A policy at the domain level is set for “Enforce”
Correct Answer and Explanation: Answer A is correct. Because the values in the GPO at the OU level are applied after those at the domain level, this policy can be overridden if “Enforce” is not set.
Incorrect Answers and Explanations: Answer B is incorrect because the GPO at the domain level would override the setting at the site level by default. Answer C is not correct because the GPO at the domain level would override the setting at the local level by default. Answer D is incorrect because if this was set for “Enforce,” the domain policy would be taking effect.
14. When implementing a security infrastructure in an organization, you are tasked with designing their ACLs. Specifically, you must define how some firewall rules are set up. What principle or method would you want to make sure to include in your design?
A. Separation of duties
B. Principle of least privilege
C. Implicit deny
D. Block inheritance
Correct Answer and Explanation: Answer C is correct. Any time that you are working with ACLs, you should define an implicit deny to ensure that access requests which fall outside the existing rules are denied by default.
Incorrect Answers and Explanations: Answer A is incorrect because separation of duties does not apply to firewall ACLs in most cases. Answer B is not correct because while this should be applied to firewall configuration, it is not as critical as the implicit deny. Answer D is incorrect because block inheritance does not apply to firewall ACLs.
15. You are working with an access control mechanism which uses logical tokens to validate user access requests. When a user presents his ID and token to the secured resource, he is granted access, but it is read-only rather than the read-write access he was expecting. Where should you look first for the cause?
A. Have the user confirm that he is using the right password
B. Ensure that the third-party authentication service is working properly
C. Check the security permissions on the access control object
D. Check to see if the token has been revoked
Correct Answer and Explanation: Answer C is correct. The authentication and token verification appears to be working. The issue is with the level of permission granted which implies that there is a problem with the permissions set on the access control object.
Incorrect Answers and Explanations: Answer A is incorrect because the user must have had the correct password to be issued a token. Answer B is not correct because the third-party authentication service appears to have already done its job if the user has a token and it can be validated by the access control system. Answer D is incorrect because a revoked token would deny all access, not change the access level.
1. You are acting as a security consultant for a company wanting to decrease their security risks. As part of your role, they have asked that you develop a security policy that they can publish to their employees. This security policy is intended to explain the new security rules and define what is and is not acceptable from a security standpoint as well as defining the method by which users can gain access to IT resources. What element of AAA is this policy a part of?
A. Authentication
B. Authorization
C. Access control
D. Auditing
Correct Answer and Explanation: C. Access control is defined as a policy, software component, or hardware component that is used to grant or deny access to a resource. Because this policy is defining how to access resources, it is considered part of access control.
Incorrect Answers and Explanations: Answer A is incorrect because this type of written policy is not a part of the authentication process although they may explain the authentication as part of the policy. Answer B is incorrect because this type of written policy is not a part of the authorization process. In addition, authorization is not included in the acronym AAA per CompTIA’s definition. Answer D is incorrect because this type of written policy is not part of the auditing process.
2. One of the goals of AAA is to provide CIA. A valid user has entered their ID and password and has been authenticated to access network resources. When they attempt to access a resource on the network, the attempt returns a message stating, “The server you are attempting to access has reached its maximum number of connections.” Which part of CIA is being violated in this situation?
A. Confidentiality
B. Integrity
C. Availability
D. Authentication
Correct Answer and Explanation: C. Availability under CIA has not been assured because the resource is not available to the user after they have authenticated.
Incorrect Answers and Explanations: Answer A is incorrect because confidentiality has not been breached in this scenario. Answer B is incorrect because integrity has not been breached in this scenario. Although the resource may not be available, that does not mean that the integrity of the data has been violated. Answer D is incorrect because authentication is not a component of CIA and the scenario describes that authentication has completed successfully.
3. You are performing a security audit for a company to determine their risk from various attack methods. As part of your audit, you work with one of the company’s employees to see what activities he or she performs during the day that could be at risk. As you work with the employee, you see him or her perform the following activities: Log in to the corporate network using Kerberos Access files on a remote system through a Web browser using SSL Log into a remote UNIX system using SSH Connect to a POP3 server and retrieve e-mail Which of these activities is most vulnerable to a sniffing attack?
A. Logging in to the corporate network using Kerberos
B. Accessing files on a remote system through a Web browser using SSL
C. Logging into a remote UNIX system using SSH
D. Connecting to a POP3 server and retrieving e-mail
Correct Answer and Explanation: D. Connecting to a POP3 server sends the ID and password over the network in a nonencrypted format because of the use of cleartext authentication. This data (in addition to the e-mail content itself) is consequently vulnerable to being collected when sniffing the network.
Incorrect Answers and Explanations: A, B, C. Answer A is incorrect because logging into a network using Kerberos is secure from sniffing attacks due to encryption and timestamps. Answer B is incorrect because using SSL encrypts the connection so that it cannot be viewed by sniffing. Answer C is incorrect because using SSH encrypts the connection to the remote UNIX system.
4. You are reading a security article regarding penetration testing of various authentication methods. One of the methods being described uses a time-stamped ticket as part of its methodology. Which authentication method would match this description?
A. Certificates
B. CHAP
C. Kerberos
D. Tokens
Correct Answer and Explanation: C. Kerberos is the only access control method listed which uses time-stamped tickets.
Incorrect Answers and Explanations: Answer A is incorrect because certificates do not use tickets although they are time-stamped. Answer B is incorrect because CHAP does not use time-stamped tickets as part of its methodology. Answer D is incorrect because tokens do not use tickets, although their numerical algorithms may be based on time stamps.
5. You are a security consultant for a large company that wants to make its intranet available to its employees via the Internet. They want to ensure that the site is as secure as possible. To do this, they want to use multifactor authentication. The site uses an ID and password already but they want to add security features that ensure that the site is indeed their site, not a spoofed site, and that the user is an authorized user. Which authentication technology supports this?
A. Certificates
B. CHAP
C. Kerberos
D. Tokens
Correct Answer and Explanation: A. Certificates can be used not only to ensure that the site is the company’s Web site, but also that the user is an authorized user. The Web server can be configured to require client-side certificates.
Incorrect Answers and Explanations: B, C, D. Answer B is incorrect because CHAP does not support two-way authentication in this manner. Answer C is incorrect because Kerberos can authenticate the user in a method similar to this, but could not serve to authenticate the server. Answer D is incorrect because tokens are used for one-way authentication.
6. You are developing a password policy for a company. As part of the password policy, you define the required strength of the password. Because of the security requirements for the company, you have required a minimum length of 14 characters, the use of uppercase and lowercase alphabetic characters, the use of numbers, and the use of special characters. What else should you require?
A. No dictionary words allowed in the password
B. No portion of the username allowed in the password
C. No personal identifiers allowed in the password
D. All of the above
Correct Answer and Explanation: D. All of the options listed are good requirements for a strong password. Because the security requirements are stringent enough to require the use of a 14-character password, you should ensure that the policy is as restrictive as possible in the other elements of password strength.
Incorrect Answers and Explanations: Answer A is incorrect because, while this will help increase the strength of the password, it is not the strongest answer. Answer B is incorrect because, while this will help increase the strength of the password, it is not the strongest answer. Answer C is incorrect because, while this will increase the strength of the password, it is not the strongest answer. It should also be noted that all of the options except for this one can be enforced systematically whereas option C can only be enforced by policy.
7. You have been asked to help a company implement multifactor authentication. They want to make sure that the environment is as secure as possible through the use of biometrics. Based on your knowledge of authentication, you understand that biometrics falls under the “something you are” category. Which other category should be used with the biometric device to provide the highest level of security?
A. Something you know
B. Something you have
C. Something you do
D. All of the above
Correct Answer and Explanation: D. All of these options have their own benefits and detriments. A combination of all of them in a multifactor authentication system would provide the highest level of security although it would be quite an inconvenience to the user.
Incorrect Answers and Explanations: Answer A is incorrect because, while this is a valid solution for the multifactor authentication requirement, it is not the most secure solution. Answer B is incorrect because this too is not the most secure solution. Answer C is incorrect as well because any two-factor authentication method is not as secure as a four-factor authentication method.
8. You are attempting to query an object in an LDAP directory using the distinguished name of the object. The object has the following attributes:
cn: 4321
givenName: John
sn: Doe
telephoneNumber: 905 555 1212
employeelD: 4321
mail: jdoe@nonexist.com
objectClass: organizationalPerson
Based on this information, which of the following would be the distinguished name of the object?
A. dc = nonexist, dc = com
B. cn = 4321
C. dn: cn = 4321, dc = nonexist, dc = com
D. jdoe@nonexist.com
Correct Answer and Explanation: C. dn: cn = 4321, dc = nonexist, dc = com. The distinguished name is a unique identifier for the object, and is made up of several attributes of the object. It consists of the relative distinguished name, which is constructed from some attribute(s) of the object, followed by the distinguished name of the parent object.
Incorrect Answers and Explanations: Answer A is incorrect, because this identifies the root of the tree. Answer B is incorrect, because this identifies the common name of the object. Answer D is incorrect, because this is the user account’s e-mail address.
9. You are creating a new LDAP directory, in which you will need to develop a hierarchy of OUs and objects. To perform these tasks, on which of the following servers will you create the directory structure?
A. DIT
B. Tree server
C. Root server
D. Branch server
Correct Answer and Explanation: C. The root server is used to create the structure of the directory, with OUs and objects branching out from the root. Because LDAP directories are organized as tree structures, the top of the hierarchy is called the root.
Incorrect Answers and Explanations: Answer A is incorrect, because the DIT is the name given to the tree structure. Answers B and D are incorrect, because there is no such thing as a Branch server or Tree server in LDAP.
10. When using LDAP for authentication in an internetworking environment, what is the best way to ensure that the authentication data is secure from packet sniffing?
A. Use LDAP to keep all passwords encrypted when transmitted to the server.
B. Use LDAP over SSL/TLS to encrypt the authentication data.
C. Require that the clients use strong passwords so that they cannot easily be guessed.
D. Use LDAP over HTTP/S to encrypt the authentication data.
Correct Answer and Explanation: B. Use LDAP over SSL/TLS to encrypt the authentication data. This will ensure that no LDAP authentication is performed unencrypted, so that anyone capturing the packets on the network will be able to read it easily.
Incorrect Answers and Explanations: Answer A is incorrect, because LDAP doesn’t encrypt data transmitted between the client and server. Answer C is incorrect, because even though it is important to use strong passwords, it does not protect the authentication data from being captured by a packet sniffer. Answer D is incorrect, because HTTP/S is a protocol for transferring Web pages securely.
11. Which password attack will take the longest to crack a password?
A. Password guessing
B. Brute force attack
C. Dictionary attack
D. All attacks are equally fast
Correct Answer and Explanation: B. Brute force tries most if not all combinations, so it takes the longest time.
Incorrect Answer and Explanations: Answer A is incorrect because password guessing can be the fastest if correct guesses are used. Answer C is incorrect because a dictionary attack, if successful, only uses a very finite amount of tries. Answer D is incorrect because certainly different methods have different speeds.
12. The company you are working for has decided to do something to make their workstations more secure. They have decided to give all users a Smart Card for use with system logins. Which factor of authentication is utilized with this new requirement?
A. Something you know
B. Something you have
C. Something you are
D. Something you do
Correct Answer and Explanation: B. A Smart Card is something you have, so this is the appropriate authentication factor.
Incorrect Answers and Explanations: A, C, D. Answer A is incorrect because a Smart Card does not necessarily require a password so the “something you know” factor does not apply. Answer C is incorrect because this factor relates to biometrics and therefore does not apply to Smart Cards. Answer D is incorrect because Smart Cards are a physical object, not an action, and therefore do not necessarily provide this factor.
13. Choose the correct set of terms: When a wireless user, also known as the ____________wants to access a wireless network, 802.1x forces them to authenticate to a centralized authority called the_____________.
A. Authenticator; supplicant
B. Supplicant; authenticator
C. Supplicant; negotiator
D. Contact; authenticator
Correct Answer and Explanation: B. Supplicant is the client that wants to access a wireless network and authenticator performs the authentication.
Incorrect Answers and Explanations: A, C, D. Answer A is incorrect in order; Answer C is incorrect as there is no negotiator in the process. Answer D is incorrect as contact is not the right term used while defining authentication process.
14. One of the biggest differences between TACACS and TACACS+ is that TACACS uses__________as its transport protocol and TACACS+ uses __________as its transport protocol.
A. TCP;UDP
B. UDP;TCP
C. IP; TCP
D. IP; UDP
Correct Answer and Explanation: B. TACACS is based on UDP and TACACS+ is based on TCP.
Incorrect Answers: A, C, D.
15. EAP is available in various forms including:
A. EAPoIP, EAP-TLS, EAP-TTLS, RADIUS, Cisco LEAPEAP-FAST
B. EAPoIP, EAP-TLS, EAP-MPLS, RADIUS, EAP-FAST
C. EAPoIP, EAP-TLS, EAP-TTLS, RADIUS, Cisco PEAP
D. EAPoIP, EAP-TLS, EAP-TTLS, Kerberos, EAP-FAST
Correct Answer and Explanation: A. EAP comes in several forms: EAP over IP (EAPoIP), Message Digest Algorithm/Challenge-Handshake Authentication Protocol (EAP-MD5-CHAP), EAP-TLS, EAP-TTLS, RADIUS, and Cisco LEAP.
Incorrect Answers and Explanations: B, C, D. EAP-MPLS, Cisco PEAP, and Kerberos are not the EAP forms.