CHAPTER 1
Introduction to Networking Technologies
This chapter covers the following official Network+ objective:
 Compare and contrast the characteristics of network topologies, types and technologies.
Compare and contrast the characteristics of network topologies, types and technologies.
This chapter covers CompTIA Network+ objective 1.5. For more information on the official Network+ exam topics, see the “About the Network+ Exam” section in the Introduction.
A variety of physical and logical network layouts are in use today. As a network administrator, you might find yourself working on these different network layouts or topologies. Therefore, you must understand how they are designed to function.
This chapter reviews general network considerations, such as the various topologies used on today’s networks, local-area networks (LANs), wide-area networks (WANs), and some of the Institute of Electrical and Electronics Engineers (IEEE) standards.
Wired and Wireless Network Topologies
 Compare and contrast the characteristics of common network topologies, types, and
technologies.
Compare and contrast the characteristics of common network topologies, types, and
technologies.
CramSaver
If you can correctly answer these questions before going through this section, save time by skimming the Exam Alerts in this section and then completing the Cram Quiz at the end of the section.
1. Which topology (star, bus, or ring) would utilize a switch?
2. With which topology does every node have a direct connection to every other node?
Answers
1. Of the choices given, only a star topology would utilize a switch.
2. With a mesh topology, every node has a direct connection to every other node.
A topology refers to a network’s physical and logical layout. A network’s physical topology refers to the actual layout of the computer cables and other network devices. A network’s logical topology refers to the way in which the network appears to the devices that use it.
Several topologies are in use on networks today. Some of the more common topologies are the bus, ring, star, mesh, and wireless. The following sections provide an overview of each.
Bus Topology
A bus topology uses a trunk or backbone to connect all the computers on the network, as shown in Figure 1.1. Systems connect to this backbone using T connectors or taps (known as a vampire tap, if you must pierce the wire). To avoid signal reflection, a physical bus topology requires that each end of the physical bus be terminated, with one end also being grounded. Note that a hub or switch is not needed in this installation.
ExamAlert
Loose or missing terminators from a bus network disrupt data transmissions.
The most common implementation of a linear bus is the IEEE 802.3 Ethernet standard. Table 1.1 summarizes the advantages and disadvantages of the bus topology.
TABLE 1.1 Advantages and Disadvantages of the Bus Topology
|
Advantages |
Disadvantages |
|
Compared to other topologies, a bus is cheap and easy to implement. |
Network disruption might occur when computers are added or removed. |
|
Requires less cable than other topologies. |
Because all systems on the network connect to a single backbone, a break in the cable prevents all systems from accessing the network. |
|
Does not use any specialized network equipment. |
Difficult to troubleshoot. |
Ring Topology
The ring topology is a logical ring, meaning that the data travels in a circular fashion from one computer to another on the network. It is not a physical ring topology. Figure 1.2 shows the logical layout of a ring topology. Note that a hub or switch is not needed in this installation either.
In a true ring topology, if a single computer or section of cable fails, the signal is interrupted. The entire network becomes inaccessible. Network disruption can also occur when computers are added to or removed from the network, making it an impractical network design in environments where the network changes often.
As just mentioned, if a single system on the ring fails, the whole network fails. This is why ring networks can be set up in a fault-tolerant design, meaning that they have a primary and secondary ring. If one ring fails, data can use the second ring to reach its destination. Naturally, the addition of the second ring adds to the cost of the network as well as the complexity.
Ring networks are most commonly wired in a star configuration. In a token ring network, a multistation access unit (MSAU) is equivalent to a hub or switch on an Ethernet network. The MSAU performs the token circulation internally. To create the complete ring, the ring-in (RI) port on each MSAU is connected to the ring-out (RO) port on another MSAU. The last MSAU in the ring is then connected to the first to complete the ring. Table 1.2 summarizes the advantages and disadvantages of the ring topology.
TABLE 1.2 Advantages and Disadvantages of the Ring Topology
|
Advantages |
Disadvantages |
|
Cable faults are easily located, making troubleshooting easier. |
Expansion to the network can cause network disruption. |
|
Ring networks are moderately easy to install. |
A single break in the cable can disrupt the entire network. |
Star Topology
In the star topology, all computers and other network devices connect to a central device called a hub or switch. Each connected device requires a single cable to be connected to the hub or switch, creating a point-to-point connection between the device and the hub or switch.
Using a separate cable to connect to the hub or switch allows the network to be expanded without disruption. A break in any single cable does not cause the entire network to fail. Figure 1.3 shows a star topology.
ExamAlert
Among the network topologies discussed in this chapter, the star topology is the easiest to expand in terms of the number of devices connected to the network.

FIGURE 1.3 Star topology
The star topology is the most widely implemented network design in use today, but it is not without shortcomings. Because all devices connect to a centralized hub or switch, this creates a single point of failure for the network. If the hub or switch fails, any device connected to it cannot access the network. Because of the number of cables required and the need for network devices, the cost of a star network is often higher than other topologies. Table 1.3 summarizes the advantages and disadvantages of the star topology.
TABLE 1.3 Advantages and Disadvantages of the Star Topology
|
Advantages |
Disadvantages |
|
Star networks are easily expanded without disruption to the network. |
Requires more cable than most of the other topologies. |
|
Cable failure affects only a single user. |
A central connecting device allows for a single point of failure. |
|
Easy to troubleshoot and implement. |
Requires additional networking equipment to create the network layout. |
Wired Mesh Topology
The wired mesh topology incorporates a unique network design in which each computer on the network connects to every other, creating a point-to-point connection between every device on the network. The purpose of the mesh design is to provide a high level of redundancy. If one network cable fails, the data always has an alternative path to get to its destination; each node can act as a relay.
The wiring for a mesh network can be complicated, as illustrated by Figure 1.4. Furthermore, the cabling costs associated with the mesh topology can be high, and troubleshooting a failed cable can be tricky. Because of this, the mesh topology is not the first choice for many wired networks but is more popular with servers/routers.

FIGURE 1.4 Mesh topology
A variation on a true mesh topology is the hybrid mesh. It creates a redundant point-to-point network connection between only specific network devices (such as the servers). The hybrid mesh is most often seen in WAN implementations but can be used in any network.
Another way of describing the degree of mesh implementation is by labeling it as either partial or full. If it is a true mesh network with connections between each device, it can be labeled full mesh, and if it is less than that—a hybrid of any sort—it is called a partial mesh network.
Table 1.4 summarizes the advantages and disadvantages of the mesh topology.
ExamAlert
Because of the redundant connections, the mesh topology offers better fault tolerance than other topologies.
TABLE 1.4 Advantages and Disadvantages of the Mesh Topology
|
Advantages |
Disadvantages |
|
Provides redundant paths between LAN topologies. |
Requires more cable than the other topologies. |
|
The network can be expanded without disruption to current users. |
Complicated implementation. |
Wireless Topologies
Wireless networks typically are implemented using one of three wireless topologies:
 The infrastructure, or managed, wireless topology
The infrastructure, or managed, wireless topology
 The ad hoc, or unmanaged, wireless topology
The ad hoc, or unmanaged, wireless topology
 The mesh wireless topology
The mesh wireless topology
The following sections describe these three wireless topologies in greater detail.
Infrastructure Wireless Topology
The infrastructure wireless topology is commonly used to extend a wired LAN to include wireless devices. Wireless devices communicate with the wired LAN through a base station known as an access point (AP) or wireless access point. The AP forms a bridge between a wireless and wired LAN, and all transmissions between wireless stations, or between a system and a wired network client, go through the AP. APs are not mobile and have to stay connected to the wired network; therefore, they become part of the wired network infrastructure (thus the name). In infrastructure wireless networks, there might be several access points providing wireless coverage for a large area or only a single access point for a small area, such as a single home or small building.
Note
WAP or AP? Notice that although we call it a wireless access point, it is commonly referred to as an AP. As you study for the exam, know that it can be called either an AP or a WAP, and—just to make matters confusing—WAP is also the acronym for the Wireless Application Protocol.
The Network+ objectives require you to be familiar with wireless topologies such as mesh, ad hoc, and infrastructure.
Ad Hoc Wireless Topology
In a wireless ad hoc topology, devices communicate directly among themselves without using an access point. This peer-to-peer network design is commonly used to connect a small number of computers or wireless devices. For example, an ad hoc wireless network may be set up temporarily between laptops in a boardroom or to connect systems in a home instead of using a wired solution. The ad hoc wireless design provides a quick method to share files and resources among a small number of systems. Connecting mobile devices together or to a printer using Bluetooth is an example of an ad hoc network.
Figure 1.5 shows an ad hoc wireless network, and Figure 1.6 shows the infrastructure network using the AP.

FIGURE 1.5 Ad hoc wireless topology
Tip
Ad Hoc Wireless Topology The ad hoc, or unmanaged, network design does not use an AP. All wireless devices connect directly to each other.

FIGURE 1.6 Infrastructure wireless topology
Wireless Mesh Topology
As discussed earlier, wired mesh networks are costly because of the cabling required to interconnect all computer systems. Wireless mesh networks obviously do not need cables running between systems, making wireless mesh networks fairly common in the networking world. In the wireless mesh network, as with the wired mesh, each network node is interconnected to other nodes on the network. With a wired mesh, the wireless signal starts at a wireless base station (access point) attached to a wired network. A wireless mesh network extends the transmission distance by relaying the signal from one computer to another. Unlike the wired mesh, in which a complex and expensive collection of physical cables is required to create the mesh, the wireless mesh is inexpensive to implement. Figure 1.7 shows a wireless mesh topology.
Note
Wireless Mesh A wireless mesh network is created through the connection of wireless access points installed at each network user’s locale. Data signals in a wireless mesh rely on all nodes to propagate signals. Wireless mesh networks can be identified by the interconnecting signals between each node.
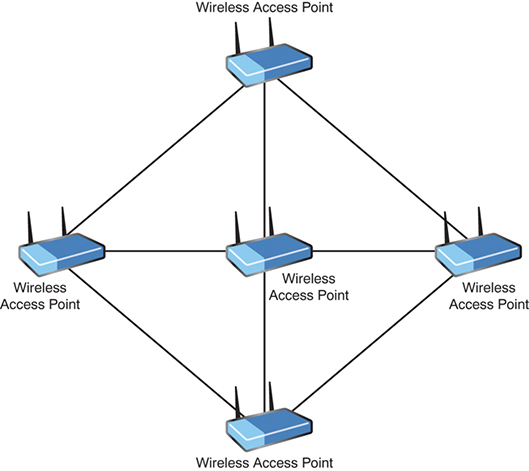
FIGURE 1.7 A wireless mesh topology
The wireless mesh network has several key advantages. Because a wireless mesh network is interconnected with one or more nodes on the network, the data can travel multiple paths to reach its destination. When a new node is added, it provides new paths for other nodes, which in turn improves network performance and decreases congestion. Advantages of the wireless mesh include the following:
 Self-healing: Wireless mesh networks are known as self-healing, which refers to the network’s ability
to adapt to network failure and even function should a node be moved from one location
to another. Self-healing in a wireless mesh environment is possible because of the
interconnected connections and because of the wireless media.
Self-healing: Wireless mesh networks are known as self-healing, which refers to the network’s ability
to adapt to network failure and even function should a node be moved from one location
to another. Self-healing in a wireless mesh environment is possible because of the
interconnected connections and because of the wireless media.
 Scalable: Wireless mesh networks are highly scalable. Using wireless, it is possible to add
new systems to the network without the need for expensive cables.
Scalable: Wireless mesh networks are highly scalable. Using wireless, it is possible to add
new systems to the network without the need for expensive cables.
 Reliability: Of all network topologies, the mesh network provides the greatest reliability. The
redundant number of paths for the data to travel ensures that data can reach its destination.
Reliability: Of all network topologies, the mesh network provides the greatest reliability. The
redundant number of paths for the data to travel ensures that data can reach its destination.
 Cost: One disadvantage of the wired mesh is the cost associated with running the cabling
and the support costs of such a complex network. Wireless mesh networks are essentially
self-configuring and do not have cabling requirements. Therefore, systems can be added,
removed, and relocated with little cost or disruption to the network.
Cost: One disadvantage of the wired mesh is the cost associated with running the cabling
and the support costs of such a complex network. Wireless mesh networks are essentially
self-configuring and do not have cabling requirements. Therefore, systems can be added,
removed, and relocated with little cost or disruption to the network.
Hybrid Topologies
As you might expect, topology designs are not black and white. Many of the topologies found in large networking environments are a hybrid of physical topologies. An example of a hybrid topology is the star bus—a combination of the star topology and the bus topology. Figure 1.8 shows how this might look in a network implementation.

FIGURE 1.8 A star bus topology
ExamAlert
Another meaning: The term hybrid topology also can refer to the combination of wireless and wired networks. For the Network+ exam, however, the term hybrid most likely refers to the combination of physical networks.
1. You have been asked to install a network that will give the network users the greatest amount of fault tolerance. Which of the following network topologies would you choose?
 A. Star
A. Star
 B. Ring
B. Ring
 C. Mesh
C. Mesh
 D. Bus
D. Bus
2. Which of the following topologies allows for network expansion with the least amount of disruption for the current network users?
 A. Bus
A. Bus
 B. Ring
B. Ring
 C. LAN
C. LAN
 D. Star
D. Star
3. What topology is represented in the following figure?

 A. Star topology
A. Star topology
 B. Star bus
B. Star bus
 C. Ad hoc
C. Ad hoc
 D. Infrastructure
D. Infrastructure
4. Which network topology offers the greatest level of redundancy but has the highest implementation cost?
 A. Wireless mesh
A. Wireless mesh
 B. Wired mesh
B. Wired mesh
 C. Hybrid star
C. Hybrid star
 D. Bus network
D. Bus network
5. Which of the following statements are associated with a bus LAN network? (Choose all correct answers.)
 A. A single cable break can cause complete network disruption.
A. A single cable break can cause complete network disruption.
 B. All devices connect to a central device.
B. All devices connect to a central device.
 C. It uses a single backbone to connect all network devices.
C. It uses a single backbone to connect all network devices.
 D. It uses a dual-ring configuration.
D. It uses a dual-ring configuration.
6. As a network administrator, you are called in to troubleshoot a problem on a token ring network. The network uses two MSAUs connected using the ring-in ports on both devices. All network cards are set at the same speed. What is the likely cause of the problem?
 A. Bad network card
A. Bad network card
 B. Faulty cabling
B. Faulty cabling
 C. MSAU configuration
C. MSAU configuration
 D. Network card configuration
D. Network card configuration
Cram Quiz Answers
1. C. A mesh network uses a point-to-point connection to every device on the network. This creates multiple points for the data to be transmitted around the network and therefore creates a high degree of redundancy. The star, ring, and bus topologies do not offer the greatest amount of fault tolerance.
2. D. On a star network, each network device uses a separate cable to make a point-to-point connection to a centralized device, such as a hub or a switch. With such a configuration, a new device can be added to the network by attaching the new device to the hub or switch with its own cable. This process does not disrupt the users who are currently on the network. Answers A and B are incorrect because the addition of new network devices on a ring or bus network can cause a disruption in the network and cause network services to be unavailable during the installation of a new device.
3. D. The infrastructure wireless topology is commonly used to extend a wired LAN to include wireless devices. Wireless devices communicate with the wired LAN through a base station known as an access point (AP) or wireless access point. The AP forms a bridge between a wireless and wired LAN, and all transmissions between wireless stations or between a system and a wired network client go through the AP.
4. B. The wired mesh topology requires each computer on the network to be individually connected to every other device. This configuration provides maximum reliability and redundancy for the network. However, it is very costly to implement because of the multiple wiring requirements.
5. A, C. In a bus network, a single break in the network cable can disrupt all the devices on that segment of the network, a significant shortcoming. A bus network also uses a single cable as a backbone to which all networking devices attach. A star network requires networked devices to connect to a centralized device such as a hub, switch, or MSAU. Therefore, answer B is incorrect. Answer D is also incorrect because it uses a dual-ring configuration.
6. C. To create the complete ring, the ring-in (RI) port on each MSAU is connected to the ring-out (RO) port on another MSAU. The last MSAU in the ring is then connected to the first to complete the ring.
Network Types
 Compare and contrast the characteristics of network topologies, types and technologies.
Compare and contrast the characteristics of network topologies, types and technologies.
CramSaver
If you can correctly answer these questions before going through this section, save time by skimming the Exam Alerts in this section and then completing the Cram Quiz at the end of the section.
1. True or false: The biggest difference between a LAN and a WAN is usually the size of the network.
2. What network type is essentially a LAN created to share data among devices associated with you?
3. In what networking type is consolidated, block-level data storage made available to networked devices?
Answers
1. True. A WAN is a network that spans more than one geographic location, often connecting separated LANs.
2. A personal-area network (PAN) is essentially a LAN created to share data among devices associated with you.
3. A storage-area network (SAN) makes block-level data storage available to devices on the network.
Networks are classified according to their geographic coverage and size. The two most common network classifications are local-area networks (LANs) and wide-area networks (WANs). Choosing between the two is often a matter of understanding the requirements.
ExamAlert
For the exam, you should be able to differentiate between the various types of networks discussed here.
LANs
A local-area network (LAN) is a data network that is restricted to a single geographic location and typically encompasses a relatively small area, such as an office building or school. The function of the LAN is to interconnect workstation computers for the purpose of sharing files and resources. Because of its localized nature, the LAN typically is high speed and cheaper to set up than a WAN. Figure 1.9 shows an example of a LAN.

FIGURE 1.9 A local-area network
WLANs
Instead of being wholly dependent on wiring for your local network, the wireless LAN (WLAN) provides a flexible and secure data communications system that augments an Ethernet LAN or, in some cases, replaces it altogether. Wireless transmissions send and receive data using radio frequency (RF) signals, freeing you from wired solutions, and are dependent on a hotspot. That hotspot can be in a coffee shop, a train station, a restaurant, or almost any public place. Security should be a prime concern of public hotspot users, and encryption should be used everywhere possible.
In a common wireless implementation, a wireless transceiver (transmitter/receiver), known as an access point, connects to the wired network from a fixed location using standard cabling. The wireless access point receives and then transmits data between the wireless LAN and the wired network infrastructure.
Client systems communicate with a wireless access point using wireless LAN adapters. Such adapters are built in to or can be added to laptops and other mobile devices or desktop computers. Wireless LAN adapters provide the communication point between the client system and the airwaves via an antenna.
WANs
A wide-area network (WAN) is a network that spans more than one geographic location, often connecting separated LANs. WANs are slower than LANs and often require additional and costly hardware, such as routers, dedicated leased lines, and complicated implementation procedures. Figure 1.10 shows an example of a WAN.

FIGURE 1.10 A wide-area network
MANs
Occasionally, a WAN will be called a metropolitan-area network (MAN) when it is confined to a certain geographic area, such as a university campus or city. No formal guidelines dictate the differences between a MAN and a WAN; technically, a MAN is a WAN. Perhaps for this reason, the term MAN is used less often than WAN. If any distinction exists, it is that a MAN is smaller than a WAN. A MAN is almost always bigger than a LAN and usually is smaller than or equal to a WAN. MANs utilize an Internet service provider (ISP) or telecommunications (telco) provider.
CANs
When it comes to terminology and definitions, a computer network in a defined area that links buildings and consists of multiple LANs within that limited geographical area is usually called a Campus-Area Network (CAN). The CAN may encompass the whole college campus, or a portion of it. It may also have nothing to do with a college but consists of office buildings in an enterprise “campus,” industrial complex, military base, or anywhere else. In reality, a CAN is a WAN, but what makes it distinct is the confined geographic area it includes.
SANs
A storage-area network (SAN) consists of just what the name implies: networked/shared storage devices. With clustered storage, you can use multiple devices to increase performance. SANs are subsets of LANs and offer block-level data storage that appears within the operating systems of the connected devices as locally attached devices.
File systems built on top of SANs can provide file-level access, but the SAN itself does not provide file abstraction, only block-level operations.
PANs
A personal-area network (PAN) is essentially a LAN created to share data among devices associated with you. Wireless technologies have taken PAN further and introduced a new term—wireless personal-area network (WPAN). WPAN refers to the technologies involved in connecting devices in very close proximity to exchange data or resources, usually through the use of Bluetooth, infrared, or near-field communication (NFC). An example is connecting a laptop with a smartphone to synchronize an address book. Because of their small size and the nature of the data exchange, WPAN devices lend themselves well to ad hoc wireless networking. Ad hoc wireless networks are those that have devices connect to each other directly, not through a wireless access point.
Cram Quiz
1. When a WAN is confined to a certain geographic area, such as a city, it is known as a:
 A. LAN
A. LAN
 B. MAN
B. MAN
 C. VAN
C. VAN
 D. VPN
D. VPN
2. Which of the following is a computer network in a defined area that links buildings and consists of multiple LANs within that limited geographical area?
 A. SAN
A. SAN
 B. PAN
B. PAN
 C. DAN
C. DAN
 D. CAN
D. CAN
3. Which of the following provides a flexible and secure data communications system that augments an Ethernet LAN or, in some cases, replaces it altogether?
 A. PHLAN
A. PHLAN
 B. MAN
B. MAN
 C. WLAN
C. WLAN
 D. CRAN
D. CRAN
1. B. A WAN can be referred to as a metropolitan-area network (MAN) when it is confined to a certain geographic area, such as a city.
2. D. A campus-area network (CAN) is a computer network in a defined area that links buildings and consists of multiple LANs within that limited geographical area.
3. C. A wireless LAN (WLAN) augments an Ethernet LAN or, in some cases, replaces it altogether.
 Compare and contrast the characteristics of network topologies, types and technologies.
Compare and contrast the characteristics of network topologies, types and technologies.
CramSaver
If you can correctly answer these questions before going through this section, save time by skimming the Exam Alerts in this section and then completing the Cram Quiz at the end of the section.
1. What is the access method employed by the 802.11 wireless standards?
2. What technologies are considered the biggest developments for 802.11n/802.11ac and the keys to the newer speeds?
Answers
1. All the 802.11 wireless standards employ the CSMA/CA access method.
2. Multiple input, multiple output (MIMO) and multiuser MIMO (MU-MIMO) antenna technologies are the biggest developments for 802.11n/802.11ac and the key to the new speeds.
In the IT world of today, one of the fastest growing areas is that of embedded devices such as thermostats, water softeners, and other appliances. This interconnection via the Internet of computing devices embedded in everyday objects is known as the Internet of Things (IoT). The goal is to enable them to send and receive data. To do this, technologies are needed that facilitate such interaction. Those are discussed in the sections that follow.
ExamAlert
The seven items listed here constitute those associated with IoT beneath the Network+ objective 1.5. You should make certain that you know them as you study for the exam.
Z-Wave
When it comes to HVAC, automated window coverings, home cinema, and some security system/home access controls, Z-Wave is a popular communications protocol. Focused on the office/residential/automation market, it requires a Z-Wave gateway (central control device), which acts as both the hub controller and the portal (typically to the Internet). Up to 232 devices can be on a Z-Wave network, and each new device has to be paired (or “included”) for it to be recognized by the controller.
An estimated 50 million devices that are Z-Wave compliant have been shipped since the standard was developed by the Danish company Zen-Sys. The standard is now governed by the members of the Z-Wave Alliance. The frequency it uses varies by country, but in the United States, the two frequencies are 908.4 and 916.
Each Z-Wave network is identified by a 32-bit Network ID (known as the Home ID), and each device is identified by an 8-bit Node ID that must be unique within the network.
Ant+
Although not open per se, the Z-Wave protocol is associated with many companies. ANT+, on the other hand, is governed by Garmin through its ANT+ Alliance. Similar to Z-Wave, it is a wireless protocol but is often used to control lighting systems, television sets, and other indoor entities, such as a line of fitness monitoring equipment licensed by Garmin.
ANT+ operates in the 2.4 GHz range, and a typical ANT-enabled device includes an application host MCU interfaced with an ANT module, chipset, or chip. Communication utilizes bidirectional, serial messages across a channel. Each channel has a master and at last one slave participant.
Bluetooth
When it comes to wireless standards for short distances, Bluetooth is the industry leader. Using the 2.4 to 2.485 GHz band, the technology is popular for personal-area networks (PANs) and is based on the IEEE 802.15.1 standard. The IEEE no longer maintains the standard, and it is now managed by the Bluetooth Special Interest Group (SIG).
There are 79 Bluetooth channels available, and each channel has a bandwidth of 1 MHz. Bluetooth is a packet-based protocol with a master-slave structure; one master can communicate with up to seven slaves. A number of Bluetooth “versions” or standards have been released since 1.0 first appeared. Some of the main versions of Bluetooth evolution include v1.2, v2.0, v2.1, v3.0, v4.0, and v4.1. As of this writing, the most recently announced was 5, and it is focused on the Internet of Things (IoT). It provides double the speed (2 Mbps), fourfold the range, and eightfold the data broadcasting capacity of transmissions compared to Bluetooth 4.x.
ExamAlert
Up until the most recent version, the numbers have always included a point and a decimal: 1.0, 1.2, and so on. With the latest, there is no point or decimal. After much discussion, it was decided it was less confusing to go with a whole number: Bluetooth 5.
NFC
Near field communication (NFC) is a technology that requires a user to bring the client close to a wireless access point (AP) in order to verify—often through Radio Frequency Identification (RFID) or Wi-Fi—that the device is present. The popularity of this has grown with phones being used as a part of payment systems, and it can also be used between two phones to “bump” and send data from one to another. Although there is no hardcoded standard defining “near,” the industry tends to use 4cm (1.6 inches) as the distance.
IR
Infrared (IR) has been around for a long time; perhaps your first experience with it was the TV remote. The commands entered into the remote-control travel over an infrared light wave to the receiver on the TV. Infrared technology has progressed, and today infrared development in networking is managed by the Infrared Data Association (IrDA). However, its use in mobile devices and peripherals has been displaced by more modern Wi-Fi and Bluetooth wireless technologies that do not require a direct line-of-sight and offer less-restrictive distance limitations.
Infrared wireless networking uses infrared beams to send data transmissions between devices. Infrared wireless networking offers higher transmission rates, reaching 10 Mbps to 16 Mbps.
As expected, infrared light beams cannot penetrate objects; therefore, the signal is disrupted when something blocks the light. Infrared can be either a directed (line-of-sight) or diffuse technology. A directed infrared system provides a limited range of approximately 3 feet and typically is used for personal-area networks. Diffused infrared can travel farther and is more difficult to block with a signal object. Diffused infrared wireless LAN systems do not require line-of-sight, but usable distance is limited to room distances.
Infrared provides a secure, low-cost, convenient cable-replacement technology. It is well suited for many specific applications and environments. Some key infrared points follow:
 It provides adequate speeds—up to 16 Mbps.
It provides adequate speeds—up to 16 Mbps.
 Infrared devices use less power and therefore do not drain batteries as much.
Infrared devices use less power and therefore do not drain batteries as much.
 Infrared is a secure medium. Infrared signals typically are a direct-line implementation
in a short range and therefore do not travel far outside the immediate connection.
This eliminates the problem of eavesdropping or signal tampering.
Infrared is a secure medium. Infrared signals typically are a direct-line implementation
in a short range and therefore do not travel far outside the immediate connection.
This eliminates the problem of eavesdropping or signal tampering.
 Infrared is a proven technology. Infrared devices have been available for some time
and as such are a proven, nonproprietary technology with an established user and support
base.
Infrared is a proven technology. Infrared devices have been available for some time
and as such are a proven, nonproprietary technology with an established user and support
base.
 It has no RFI issues or signal conflicts.
It has no RFI issues or signal conflicts.
 It replaces cables for many devices, such as keyboards, mice, and other peripherals.
It replaces cables for many devices, such as keyboards, mice, and other peripherals.
 It uses a dispersed mode or a direct line-of-sight transmission.
It uses a dispersed mode or a direct line-of-sight transmission.
 Transmissions travel over short distances.
Transmissions travel over short distances.
RFID
Although NFC is a newer standard, it is built on the older standards created for RFID, which allows compatible hardware both to supply power to and communicate with an otherwise unpowered and passive electronic tag using radio waves. RFID is widely used for identification, authentication, and tracking applications.
“Proximity reader” is a catchall term for any ID or card reader capable of reading proximity cards. Proximity cards go by a number of different titles, but they are just RFID cards that can be read when close to a reader and truly never need to touch anything. The readers work with 13.56 MHz smart cards and 125 kHz proximity cards, and they can open turnstiles, gates, and any other physical security safeguards after the signal is read.
802.11
802.11 represents the IEEE designation for wireless networking. Several wireless networking specifications exist under the 802.11 banner. The Network+ objectives focus on 802.11a, 802.11b, 802.11g, 802.11n, and 802.11ac. All these standards use the Ethernet protocol and the Carrier Sense Multiple Access/Collision Detection (CSMA/CA) access method.
ExamAlert
The exam includes questions on the characteristics of the wireless standards. Remember, 802.11 wireless standards use the CSMA/CA access method.
The 802.11 wireless standards can differ in terms of speed, transmission ranges, and frequency used, but in terms of actual implementation, they are similar. All standards can use either an infrastructure or ad hoc network design, and each can use the same security protocols:
 IEEE 802.11: There were two variations on the initial 802.11 wireless standard. Both offered 1
or 2 Mbps transmission speeds and the same RF of 2.4 GHz. The difference between the
two was in how data traveled through the RF media. One used Frequency Hopping Spread
Spectrum (FHSS), and the other used Direct Sequence Spread Spectrum (DSSS). The original
802.11 standards are far too slow for modern networking needs and are now no longer
deployed.
IEEE 802.11: There were two variations on the initial 802.11 wireless standard. Both offered 1
or 2 Mbps transmission speeds and the same RF of 2.4 GHz. The difference between the
two was in how data traveled through the RF media. One used Frequency Hopping Spread
Spectrum (FHSS), and the other used Direct Sequence Spread Spectrum (DSSS). The original
802.11 standards are far too slow for modern networking needs and are now no longer
deployed.
ExamAlert
With this iteration of the exam, CompTIA wants you to know the acronyms FHSS and DSSS, but no longer tests on the intricacies of either technology. In the interest of completeness, these technologies are discussed in more detail at the end of this chapter to round out your knowledge.
 IEEE 802.11a: In terms of speed, the 802.11a standard was far ahead of the original 802.11 standards.
802.11a specified speeds of up to 54 Mbps in the 5 GHz band, but most commonly, communication
takes place at 6 Mbps, 12 Mbps, or 24 Mbps. 802.11a is incompatible with the 802.11b
and 802.11g wireless standards.
IEEE 802.11a: In terms of speed, the 802.11a standard was far ahead of the original 802.11 standards.
802.11a specified speeds of up to 54 Mbps in the 5 GHz band, but most commonly, communication
takes place at 6 Mbps, 12 Mbps, or 24 Mbps. 802.11a is incompatible with the 802.11b
and 802.11g wireless standards.
 IEEE 802.11b: The 802.11b standard provides for a maximum transmission speed of 11 Mbps. However,
devices are designed to be backward compatible with previous 802.11 standards that
provided for speeds of 1, 2, and 5.5 Mbps. 802.11b uses a 2.4 GHz RF range and is
compatible with 802.11g.
IEEE 802.11b: The 802.11b standard provides for a maximum transmission speed of 11 Mbps. However,
devices are designed to be backward compatible with previous 802.11 standards that
provided for speeds of 1, 2, and 5.5 Mbps. 802.11b uses a 2.4 GHz RF range and is
compatible with 802.11g.
 IEEE 802.11g: 802.11g offers wireless transmission over distances of 150 feet and speeds up to
54 Mbps compared with the 11 Mbps of the 802.11b standard. Like 802.11b, 802.11g operates
in the 2.4 GHz range and therefore is compatible with it.
IEEE 802.11g: 802.11g offers wireless transmission over distances of 150 feet and speeds up to
54 Mbps compared with the 11 Mbps of the 802.11b standard. Like 802.11b, 802.11g operates
in the 2.4 GHz range and therefore is compatible with it.
 IEEE 802.11n: One of the more common wireless standards today is 802.11n. The goal of the 802.11n
standard was to significantly increase throughput in both the 2.4 GHz and the 5 GHz
frequency ranges. The baseline goal of the standard was to reach speeds of 100 Mbps,
but given the right conditions, it is stated that the 802.11n speeds can reach a theoretical
600 Mbps. In practical operation, 802.11n speeds are much slower. Multiple Input,
Multiple Output (MIMO) was introduced with 802.11n.
IEEE 802.11n: One of the more common wireless standards today is 802.11n. The goal of the 802.11n
standard was to significantly increase throughput in both the 2.4 GHz and the 5 GHz
frequency ranges. The baseline goal of the standard was to reach speeds of 100 Mbps,
but given the right conditions, it is stated that the 802.11n speeds can reach a theoretical
600 Mbps. In practical operation, 802.11n speeds are much slower. Multiple Input,
Multiple Output (MIMO) was introduced with 802.11n.
 IEEE 802.11ac: The newest of the wireless standards listed in the Network+ objectives is 802.11ac,
which became an approved standard in January of 2014 and can be thought of as an extension
of 802.11n. Any device using this standard must support all the mandatory modes of
both 802.11n and 802.11a. The goal of the standard is 500 Mbps with one link and 1.3
Gbps with multiple links. It has support for up to eight MIMO streams and increased
channel bonding, as well as support for up to four multiuser MIMO (MU-MIMO) clients. 802.11ac is a 5 GHz-only technology and is available with most wireless
routers sold today.
IEEE 802.11ac: The newest of the wireless standards listed in the Network+ objectives is 802.11ac,
which became an approved standard in January of 2014 and can be thought of as an extension
of 802.11n. Any device using this standard must support all the mandatory modes of
both 802.11n and 802.11a. The goal of the standard is 500 Mbps with one link and 1.3
Gbps with multiple links. It has support for up to eight MIMO streams and increased
channel bonding, as well as support for up to four multiuser MIMO (MU-MIMO) clients. 802.11ac is a 5 GHz-only technology and is available with most wireless
routers sold today.
ExamAlert
Be prepared to answer questions on the specific characteristics of wireless standards. Performance-based questions might ask you to select or place the appropriate standard or wireless configuration setting for a particular scenario.
The Magic Behind 802.11n and 802.11ac
802.11n took the best from the 802.11 standards and mixed in some new features to take wireless to the next level. First among these new technologies was multiple input, multiple output (MIMO) antenna technology.
MIMO was unquestionably the biggest development for 802.11n and the key to the new speeds. Essentially, MIMO uses multiplexing to increase the range and speed of wireless networking. Multiplexing is a technique that combines multiple signals for transmission over a single line or medium. MIMO enables the transmission of multiple data streams traveling on different antennas in the same channel at the same time. A receiver reconstructs the streams, which have multiple antennas as well. By using multiple paths, MIMO provides a significant capacity gain over conventional single-antenna systems, along with more reliable communication.
While 802.11n can transmit more than one spatial stream at the same time, the streams are directed to a single address (MIMO). 802.11ac allows for MU-MIMO to let an AP send multiple frames to multiple clients at the exact same time (thus allowing the AP to act like a switch instead of just a hub).
In addition to MIMO, 802.11n enabled channel bonding that essentially doubled the data rate. What is channel bonding? The 802.11b and 802.11g wireless standards use a single channel to send and receive information. With channel bonding, you can use two channels at the same time. As you might guess, the capability to use two channels at once increases performance. Bonding can help increase wireless transmission rates from the 54 Mbps offered with the 802.11g standards to a theoretical maximum of 600 Mbps with 802.11n. 802.11n uses the Orthogonal Frequency Division Multiplexing (OFDM) transmission strategy—a scheme used as a digital multicarrier modulation method in which a large number of closely spaced orthogonal subcarrier signals are used to carry data on several parallel data streams or channels. It is discussed in more detail shortly.
802.11ac extends this by increasing the maximum from 40 MHz to 80 MHz (with hypothetical of 160 MHz). By doubling the channel bandwidth, twice as much data can be carried in the same time.
Note
In wireless networking, a single channel is 20 MHz in width. When two channels are bonded, they are a total of 40 MHz. 802.11n systems can use either the 20 MHz channels or the 40 MHz channel. 802.11ac supports the 20 MHz, 40 MHz, 80 MHz, and 160 MHz channels.
Aggregation is the other big difference, allowing data to be packaged together to increase speeds. 802.11n brought the technology to the mainstream, and 802.11ac simply builds on it.
A Summary of 802.11 Wireless Standards
Table 1.5 highlights the characteristics of the various 802.11 wireless standards.
TABLE 1.5 802.11 Wireless Standards
|
IEEE Standard |
Frequency/Medium |
Speed |
Topology |
Transmission Range |
Access Method |
|
802.11 |
2.4 GHz |
1 to 2 Mbps |
Ad hoc/ infrastructure |
20 feet indoors |
CSMA/CA |
|
802.11a |
5 GHz |
Up to 54 Mbps |
Ad hoc/ infrastructure |
25 to 75 feet indoors; range can be affected by building materials |
CSMA/CA |
|
802.11b |
2.4 GHz |
Up to 11 Mbps |
Ad hoc/ infrastructure |
Up to 150 feet indoors; range can be affected by building materials |
CSMA/CA |
|
802.11g |
2.4 GHz |
Up to 54 Mbps |
Ad hoc/ infrastructure |
Up to 150 feet indoors; range can be affected by building materials |
CSMA/CA |
|
802.11n |
2.4 GHz/ 5 GHz |
Up to 600 Mbps |
Ad hoc/ infrastructure |
175+ feet indoors; range can be affected by building materials |
CSMA/CA |
|
802.11ac |
5 GHz |
Up to 1.3 Gbps |
Ad hoc/ infrastructure |
115+ feet indoors; range can be affected by building materials |
CSMA/CA |
ExamAlert
For the exam, you should know the values in Table 1.5.
Spread spectrum refers to the manner in which data signals travel through a radio frequency. With spread spectrum, data does not travel straight through a single RF band; this type of transmission is known as narrowband transmission. Spread spectrum, however, requires that data signals either alternate between carrier frequencies or constantly change their data pattern. Although the shortest distance between two points is a straight line (narrowband), spread spectrum is designed to trade bandwidth efficiency for reliability, integrity, and security. Spread-spectrum signal strategies use more bandwidth than in the case of narrowband transmission, but the trade-off is a data signal that is clearer and easier to detect. The two types of spread-spectrum radio are frequency hopping and direct sequence.
Table 1.6 compares wireless standards and the spread spectrum used.
TABLE 1.6 Comparison of IEEE 802.11 Standards
|
IEEE Standard |
RF Used |
Spread Spectrum |
Data Rate (in Mbps) |
|
802.11 |
2.4 GHz |
DSSS |
1 or 2 |
|
802.11 |
2.4 GHz |
FHSS |
1 or 2 |
|
802.11a |
5 GHz |
OFDM |
54 |
|
802.11b |
2.4 GHz |
DSSS |
11 |
|
802.11g |
2.4 GHz |
DSSS |
54 |
|
802.11n |
2.4/5 GHz |
OFDM |
600 (theoretical) |
|
802.11ac |
5 GHz |
OFDM |
1300 (theoretical) |
Frequency-Hopping Spread-Spectrum Technology
Frequency-hopping spread-spectrum (FHSS) requires the use of narrowband signals that change frequencies in a predictable pattern. The term frequency hopping refers to data signals hopping between narrow channels. For example, consider the 2.4 GHz frequency band used by 802.11b/g. This range is divided into 70 narrow channels of 1 MHz each. Somewhere between 20 and several hundred milliseconds, the signal hops to a new channel following a predetermined cyclical pattern.
Because data signals using FHSS switch between RF bands, they have a strong resistance to interference and environmental factors. The FHSS signal strategy makes it well suited for installations designed to cover a large geographic area and where using directional antennas to minimize the influence of environmental factors is not possible.
FHSS is not the preferred spread-spectrum technology for today’s wireless standards. However, FHSS is used for some lesser-used standards and for cellular deployments for fixed broadband wireless access (BWA), where the use of DSSS (discussed next) is virtually impossible because of its limitations.
Direct-Sequence Spread-Spectrum (DSSS) Technology
With DSSS transmissions, the signal is spread over a full transmission frequency spectrum. For every bit of data sent, a redundant bit pattern is also sent. This 32-bit pattern is called a chip. These redundant bits of data provide both security and delivery assurance. The reason transmissions are so safe and reliable is because the system sends so many redundant copies of the data, and only a single copy is required to have complete transmission of the data or information. DSSS can minimize the effects of interference and background noise.
As for a comparison between the two, DSSS has the advantage of providing better security and signal delivery than FHSS, but it is a sensitive technology, affected by many environmental factors.
Orthogonal Frequency-Division Multiplexing
Orthogonal frequency-division multiplexing (OFDM) is a transmission technique that transfers large amounts of data over 52 separate, evenly spaced frequencies. OFDM splits the radio signal into these separate frequencies and simultaneously transmits them to the receiver. Splitting the signal and transferring over different frequencies reduces the amount of crosstalk interference. OFDM is associated with IEEE 802.11a, 802.11g, 802.11n, and 802.11ac wireless standards as well as 4G mobile phone standards.
A multiuser version of OFDM is orthogonal frequency-division multiple access (OFDMA). It assigns subsets of subcarriers to individual users to allow for simultaneous data transmission from multiples users, and it is considered scalable.
Cram Quiz
1. You are installing a wireless network solution, and you require a standard that can operate using either 2.4 GHz or 5 GHz frequencies. Which of the following standards would you choose?
 A. 802.11a
A. 802.11a
 B. 802.11b
B. 802.11b
 C. 802.11g
C. 802.11g
 D. 802.11n
D. 802.11n
 E. 802.11ac
E. 802.11ac
2. You are installing a wireless network solution that uses a feature known as MU-MIMO. Which wireless networking standard are you using?
 A. 802.11a
A. 802.11a
 B. 802.11b
B. 802.11b
 C. 802.11n
C. 802.11n
 D. 802.11ac
D. 802.11ac
1. D. The IEEE standard 802.11n can use either the 2.4 GHz or 5 GHz radio frequencies. 802.11a uses 5 GHz, and 802.11b and 802.11g use 2.4 GHz. 802.11ac operates at 5 GHz.
2. D. MU-MIMO is used by the 802.11ac standard and makes multiuser MIMO possible (increasing the range and speed of wireless networking). MIMO itself enables the transmission of multiple data streams traveling on different antennas in the same channel at the same time.
What’s Next?
This chapter created a foundation upon which Chapter 2, “Models, Ports, Protocols, and Networking Services,” builds. It examines the Open Systems Interconnect (OSI) reference model—a conceptual model describing how network architecture allows data to be passed between computer systems. It also examines how common network devices relate to the model.

