Since a long time ago, you could enable extra security on your OS using the free Enhanced Mitigation Experience Toolkit (EMET). Development of EMET was stopped last year, and support for it will end in July 2018. Also, the latest version of EMET 5.5.2 is no longer supported on Windows 10 1709 and will be uninstalled with an in-place upgrade, and installation of EMET will be actively blocked.
But no worries; all the functionality of EMET and even more features are now built in to Windows 10 1709. This new security feature is named Windows Defender Exploit Guard and is located inside the Windows Defender Security Center under App & browser control | Exploit protection:

By accessing the Exploit protection settings, you can control system-wide settings and program-specific overrides. Be carefully with system-wide settings. Per-program settings are made by a scheme enforcing the feature in the name of the app. As App-V schemes and EMET/Exploit Guard schemes cannot be nested, Exploit Guard settings will not be enforced on App-V apps.
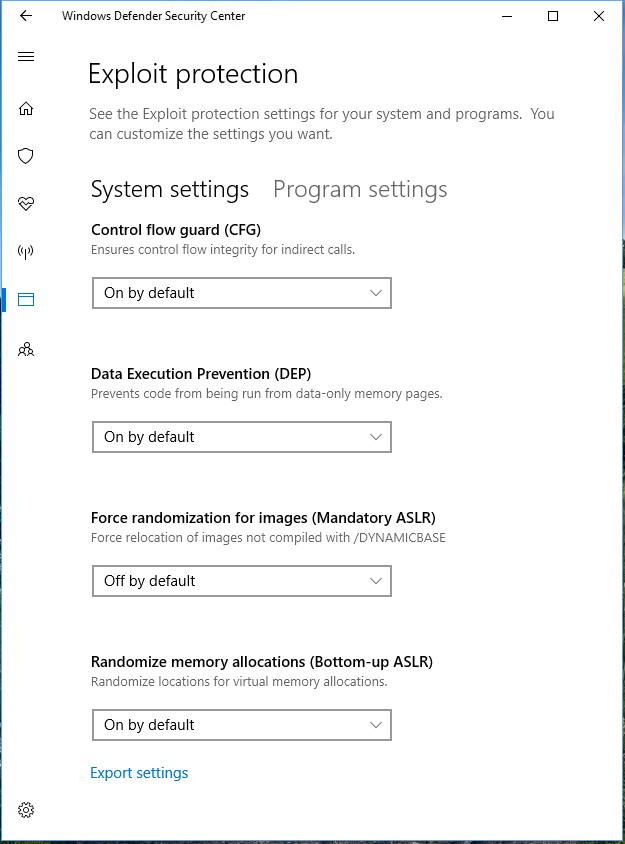
System-wide settings contain the (already known from EMET) Data Execution Prevention (DEP) setting, which prevents code execution from data-only memory pages; Address Space Layout Randomization (ASLR), now called (Mandatory ASLR), which forces relocation of images (DLLs); and Structured Exception Handling Overwrite Protection (SEHOP), which ensures the integrity of the exception handler before executing it, validating heap integrity for heap spray and heap corruption. Additionally, you can now enforce CFG which ensures integrity of all indirect calls, and Bottom-up ASLR, which will randomize all locations for virtual memory allocations.
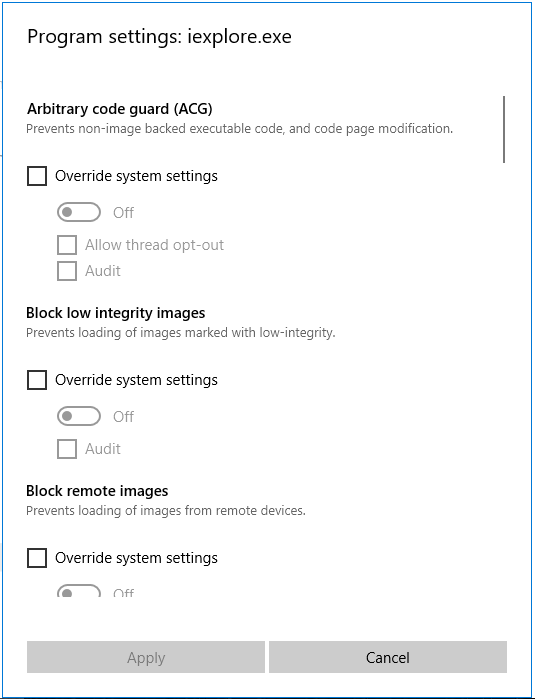
Program settings can be defined by the program name or exact file path. Per program, you can override every system-wide setting and define more settings. And as a huge improvement over EMET, you can activate an audit on every setting. Where EMET was more like a trial-and-error way of configuration (activate all settings and then deactivate settings one by one until the app works), the new audit helps in effectively finding incompatible settings very quickly.

Per program settings of Exploit Guard include Arbitrary Code Guard (ACG), which prevents code page modification; Block low integrity images, which prevents loading of images marked with low integrity; Block remote images, which prevents loading of images from remote devices; Block untrusted fonts, which prevents loading any GDI-based fonts not installed in the system fonts directory; Code integrity guard, which only allows the loading of images signed by Microsoft; Disable extension points to disable various extensible mechanisms that allow DLL injection into all processes such as window hooks; Disable Win32k system call to stop programs from using any Win32k system call; Do not allow child processes to prevent programs from creating child processes; Export address filtering (EAF) to detect dangerous exported functions being resolved by malicious code; Import address filtering (IAF), which does the same as EAF but for imported functions; Simulate execution (SimExec) to ensure that calls to sensitive functions return to legitimate callers; Validate API invocation (CallerCheck), which ensures that sensitive APIs are invoked by legitimate callers; Validate handle usage, which raises an exception on any invalid handle references; Validate image dependency integrity, which enforces code signing for Windows image dependency loading; and Validate stack integrity (StackPivot), which ensures that the stack has not been redirected for sensitive functions.
Each of these functions adds security to your applications at the cost of CPU overhead. As this overhead depends on the code of the app, there are no general numbers on the performance hit for most of the security features. You need to check the performance of each of your apps individually.
Settings can only be changed/removed as an admin user. All settings can be edited in the GUI and exported as XML for configuring by GPO.