If an attacker attempts to guess the password of a local administrative account, the lockout policy will slow down their attempts by enforcing further restrictions on the number of attempts that can be made in a set time period. This, combined with the increased complexity of the password, should make it very difficult for a successful attack to take place before the account password expires.
The default values are shown in the following screenshot:
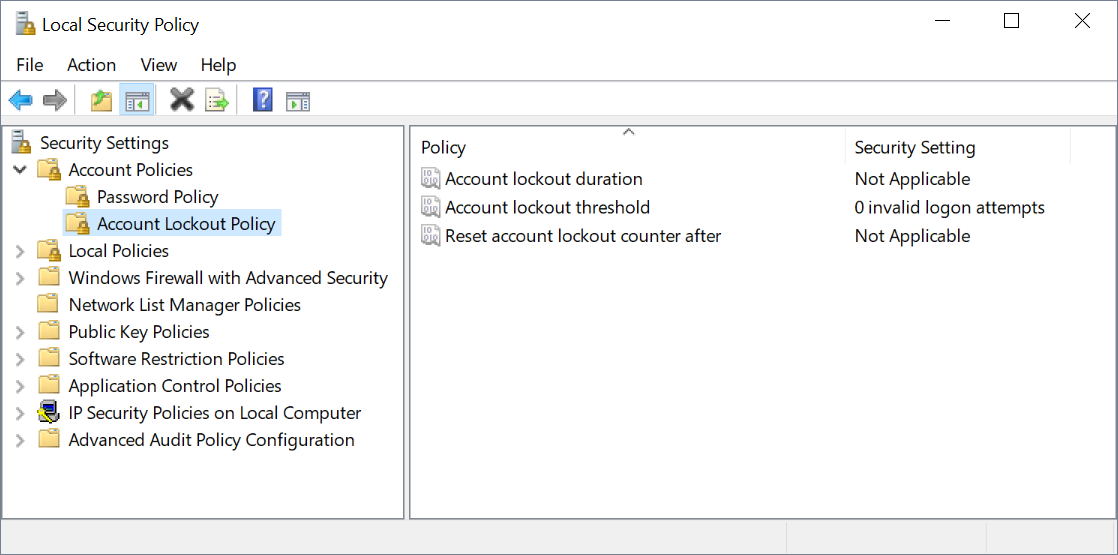
You should configure this policy to be more restrictive than the defaults that are set. This table provides some recommendations for each of the values:
|
Policy |
Recommended Settings |
Justification |
|
Account lockout duration |
60 minutes |
Once the maximum number of password attempts is reached, the account is locked for 1 hour before further attempts can be made |
|
Account lockout threshold |
15 attempts |
A genuine user may make mistakes when entering a complex password, but it should be expected to enter the correct password within 15 attempts |
|
Reset account lockout counter after |
1,440 minutes |
This specifies the time period that the account lockout threshold monitors (24 hours) |
In summary, the preceding configuration will allow an attacker to make no more than 15 bad password attempts in every 24 hours; if they do, the account is locked for one hour every time a subsequent bad attempt is made. This increases the usability for a genuine user who may make several bad attempts (but not 15) without locking them out unnecessarily, while also making it extremely difficult for a brute force attack to be achieved before the password is changed again.