According to Microsoft's newest security report, the password length recommendation has been raised to a minimum of 12 characters. But strong passwords can be difficult to remember, and forcing users to frequently change their passwords will often lead to yellow sticky note problems. Also, users often reuse passwords. Passwords are sometimes shared among individuals. Server breaches can expose passwords, especially if they are stored in plain-text or hashed without a salt. Also, users can unintentionally expose their passwords due to phishing attacks.
So passwords are no longer sufficient because they are frequently weak, the same password is used in too many locations, and due to increased cloud calculation power they can easily be cracked by brute force attack or rainbow tables if too short. They can easily be stolen, breached, or phished. Additionally, PtH attacks are now a very real threat. PtH was discovered in 1997 when the Server Message Block (SMB) client accepted NTLM password hashes. It was weaponized in 2008 by Hernan Ochoa from Amplia Security.
The hash changes only when the password is changed. Additionally, there is a relationship between the password and hash. If the password is too short, it can easily be brute-forced or calculated. Even worse is the use of the smart card-only feature because the hash will only change when you toggle this feature or when you change your smart card. Also, a stolen password can be used on multiple computers, and in most cases, you will not even notice that someone else is using your credentials.
We need to move to a more secure, password-free experience. And Windows Hello is capable of providing one. Microsoft is a board member of Fast IDentity Online (for more information visit https://www.fidonet.com/index.php) and uses standardized hardware and software described in FIDO 2.0. When using Windows Hello, your credentials (consumer mode) or your asymmetric private key (business mode) are stored inside your TPM. Your PIN or biometric factor is used to unlock your TPM.

To be able to use biometric sensors, you need to first define a PIN. Don't be baffled by the word PIN. It is not a numerical-only password; it can be also alphanumeric with special characters. The complexity of the PIN can be managed by Group Policy Object (GPO) or Mobile device management (MDM). And where with a normal password you are only capable of setting the complexity, here you can define each of lowercase, uppercase, digits, and special characters with not allowed, allowed, and required, giving you a more granular control over the PINs.

The PIN is defined per device and does not roam. So even a six character long PIN could be more safe than a 12 character long traditional password, as the PIN can only be used on the device owning it, whereas a password, once compromised, can be used in most cases on every device in the domain.
Windows Hello currently supports three types of biometric sensors: fingerprint, face, and iris. More login types such as biometric rings and blood vessel scan are currently being evaluated and will be added with future releases of Windows 10.
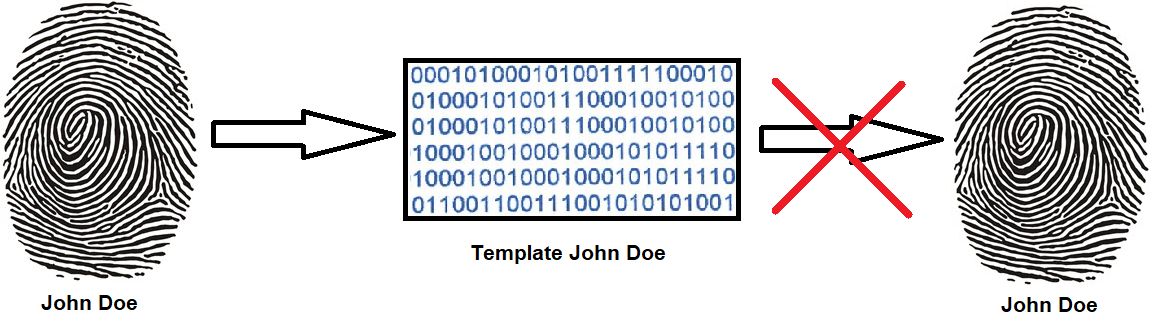
Don't worry; the scan of your fingerprint generates a template, which cannot be transformed back to a fingerprint. These templates are only stored locally. So even if an attacker compromises your system, he or she will not be able to get your fingerprint scan. Windows 10 is not the world's largest fingerprint collector!
The biometric data used to support Windows Hello is stored on the local device only. It doesn’t roam and is never sent to external devices or servers. The use of TPM is strongly recommended. While using TPM is more secure and robust, Windows also contains an alternate software-based mechanism that will be used when no TPM is available. The use of Windows Hello on machines without TPM can be prevented by GPO (set Use a hardware security device to Enabled).
Fingerprint-capable devices need to meet the biometric requirements (biometric requirements: https://docs.microsoft.com/en-us/windows-hardware/design/device-experiences/windows-hello-biometric-requirements) for false and true acceptance rate, implement anti-spoofing techniques, and provide a Windows Biometric Framework (WBF) driver for being allowed as Windows Hello fingerprint devices. But even if there are detailed requirements, the quality of anti-spoofing and liveness detection can vary among different models. You should look at fingerprint devices with capacitive, thermal, or ultrasound liveness detection if you want to ensure more security. But these sensors are more expensive. Also, large-area sensor models are usually safer than swipe models. There is no GPO possibility to limit to certain fingerprint models, so you should disable unwanted models directly inside the BIOS/UEFI firmware of your devices.
For face and iris scans, all devices must also meet the strict Microsoft sensor specifications (infrared sensors, IR illuminators, resolution, and so on). But why does Windows Hello use infrared instead of normal color images? Because IR can handle low-light and side-light situations more robustly, it is generally more immune to makeup and facial hair. Additionally, it helps with spoofing because it doesn't allow photos or LCD displays.
If your biometric device does not meet the biometric requirements and therefore has no WBF-certified driver, it will not be offered as a biometric sensor in the Windows Hello system control. But you will still be able to use a PIN with Windows Hello. If you enforce the use of biometrics by GPO, it will only apply to certified sensors.
If your biometric data is not recognized any longer by your device (such as due to a finger injury, using wet fingers with capacitive sensor models, or by wearing new glasses) you will still be able to use your PIN as a backup. If you are wearing glasses, you should register multiple times with the face recognition system with and without glasses to get the best user experience.