With Redstone 3/Windows 10 1709, a new security feature with the cumbersome name WDAG for Microsoft Edge was introduced. Even though it has an unwieldy name, its functionality can be explained easily. The concept of VBS is extended to software containers. So it will execute exposed software such as your browser in an extra virtual OS and connect only by Remote Desktop Protocol (RDP). The first program capable of this was Microsoft Edge, but other products will follow with the next versions of Windows 10. If a Microsoft Edge instance running in such a secure container gets hacked, it does not have access to the host OS. When Microsoft Edge is displaying a intranet or trustworthy site, it will be executed in the host OS. When surfing on other sites, a new instance in the Windows OS will be executed and connected by RDP.

To get this security feature activated, you need Hyper-V and VBS running, so you will need the 64 bit OS and CPU virtualization extensions. For Hyper-V guests, you need to activate the Hyper-V nesting feature. As it will add a third OS to your memory, the absolute minimum RAM should be 4 GB. 8 GB or more is recommended. This security feature also needs an Enterprise SKU. When VBS is up and running, you can add the Windows Defender Application Guard feature, which can be found in Insider Preview builds since 16251 and in retail Windows 10 version 1709. It is also possible to control this feature with the GPO Turn On/Off Windows Defender Application Guard (WDAG). The feature needs a restart to activate.
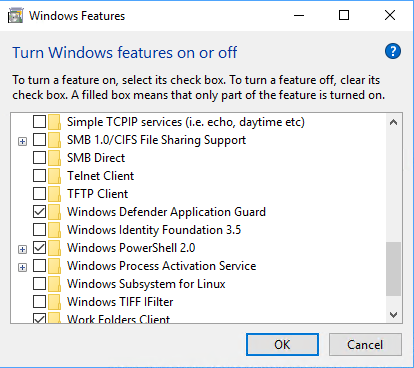
In standalone mode (when no network isolation GPO is applied) the user can open a protected Edge instance with the context menu.
Organizations can control various aspects of WDAG. To define trusted sites for WDAG, they need the Enterprise resource domains hosted in the cloud GPO. This GPO can be found under Computer Configuration | Administrative Templates | Network | Network Isolation. To add, for example, all PacktPub and Microsoft sites to your trusted sites list, you need to enable this GPO and add the following line to Enterprise's cloud resources: .packtpub.com|.microsoft.com.
All entries need to start with . and multiple entries need to be separated with the pipe character (|). Placeholder characters like * or ? are not allowed. If a resource needs a proxy address to access, you need to pair the domain using a trailing comma followed by the proxy address.
WDAG-specific GPOs can be found under Computer Configuration | Administrative Templates | Windows Components | Windows Defender Application Guard after importing the 1709 GPO templates (in fact, they've already partially existed since 1703 but weren't functional in the release version).
The Configure Windows Defender Application Guard clipboard settings GPO controls clipboard operations. By default, clipboard operations from and to WDAG Edge are blocked completely. You can enable copying from WDAG to host and/or vice versa. Clipboard content can be limited to text only, images only, or text and images. Enabling the clipboard lowers security.
The Configure Windows Defender Application Guard Print Settings GPO controls printing capabilities. By default, all print functionality is turned off in Application Guard. You can enable printing and limit it to XPS, PDF, local only, network only, and a lot of combinations of these four options or enable all printing. Enabling print functionalities lowers security.
The Allow data persistence for Windows Defender Application Guard GPO controls whether user data such as cookies and favorites as well as downloaded files will persist inside the Application Guard silo. By default, WDAG deletes all user data within the Application Guard container after the instance is stopped. When the GPO is enabled, you can still delete the content using the Reset-ApplicationGuard PowerShell command.
If you just need the Edge log files of an Application Guard container, there is the Allow auditing events in Windows Defender Application Guard GPO. By default, audit event logs aren't collected for WDAG. When you enable this setting, auditing events will be logged in host events.
On the first start of WDAG after start/reboot, you will see a short splash telling you when WDAG gets started. At the time of writing this book, depending on RAM, HDD, and CPU, this can take from 10-20 seconds up to 1-2 minutes on very old or limited systems.

Additionally, the user gets a (disengageable) information box informing him or her about the WDAG mode with a link to more information.

The Edge icon shows a shield symbol  when running in WDAG mode.
when running in WDAG mode.
With the disengaged information box, the user will only see an orange Application Guard notice in the upper left corner. Here is a comparison between the normal trusted site mode and Application Guard mode:

Task Manager will not show protected Edge instances but the WDAG RDP client instead:
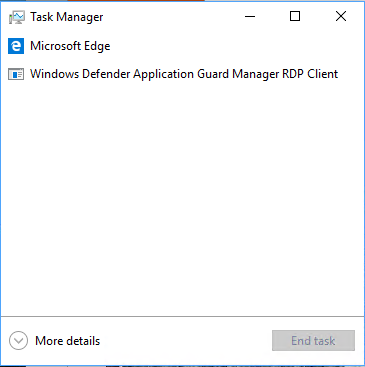
With the current implementation of WDAG, there is no easy way to check the memory consumption of the applications running inside the Application Guard container. Currently, Microsoft Edge is the first product supporting the new WDAG mode. More Microsoft products will follow. The third-party Virtualization-based security solution Bromium can run side by side with WDAG.