UAC is a fundamental security control that helps mitigate the impact of malware, yet some enterprise administrators disable User Account Control (UAC) at the request of the users, because it is seen as annoying and unnecessary prompts that get in the way of productivity. The feature has improved greatly since it was first launched (as part of Windows Vista), so we encourage you to ensure this is enabled across all managed computers in your environment.
With UAC enabled, Windows 10 prompts for consent, or prompts for credentials of a valid local administrator account, before starting a program or task that requires a full administrator access token. This prompt ensures that no malicious software can be silently installed.
If the user is logged on with local admin rights (which is not recommended), the consent prompt is presented when a user attempts to perform a task that requires a user's administrative access token. The following is an example of the UAC consent prompt you will see if you have local admin rights:
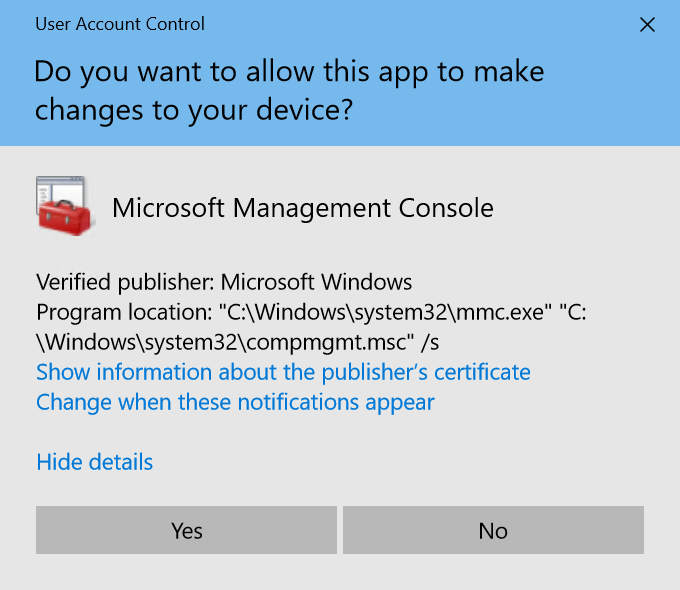
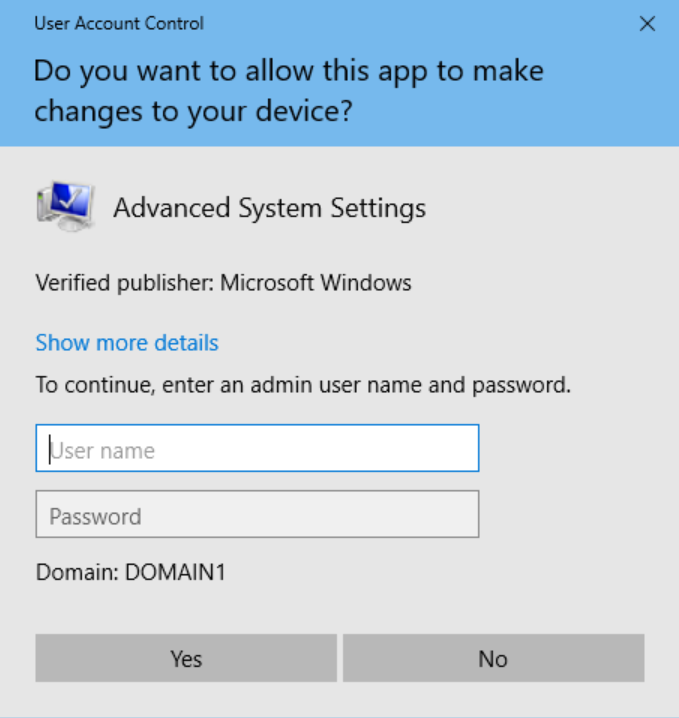
Alternatively, the credential prompt is presented when a standard user attempts to perform a task that requires administrative access, such as installing software or making a system configuration change (both potential signs of malware). Administrators can also be required to provide their credentials by setting the User Account Control: Behaviour of the elevation prompt for administrators in Admin Approval Mode policy setting value to Prompt for credentials.
The following is an example of the UAC credential prompt:
Other settings that can be controlled by UAC are listed in the following table:
|
Setting name |
Description |
|
Admin Approval Mode for the Built-in Administrator account |
Controls the behavior for the built-in administrator account only. We recommend this setting is enabled. |
|
Behavior of the elevation prompt for administrators in Admin Approval Mode |
Options include prompting for consent, prompting for credentials, or elevating without prompting. We recommend this setting be configured to prompt for consent or credentials. |
|
Behavior of the elevation prompt for standard users |
Options include prompting for credentials or automatically denying elevation requests. If the user is not provided with a separate administrator account, then set this value to automatically deny (default behavior for Enterprise). |
|
Detect application installations and prompt for elevation |
This setting determines the behavior for the entire system. Options include prompting for elevation (consent or credentials), or disabled. The default behavior for Enterprise is set to disable, because managed software does not require the user to have local admin rights to install. |
|
Only elevate executables that are signed and validated |
If enabled, this security setting enforces public key infrastructure (PKI) signature checks on any interactive application that requests elevation of privilege. |
|
Only elevate UIAccess applications that are installed in secure locations |
This option can be used to enforce the requirement that applications that request execution with a UIAccess integrity level must reside in a secure location on the filesystem. |
|
Run all administrators in Admin Approval Mode |
This security setting determines the behavior of all UAC policies for the entire system. We recommend this be set to Enabled. |
|
Switch to the secure desktop when prompting for elevation |
Secure desktop provides a clear indication to the user that elevation is being requested, or the prompt may be hidden behind other windows. Disabling this option increases your security risk, so it is recommend this is set to Enabled. |
|
Virtualize file and registry write failures to per-user locations |
Virtualization facilitates the running of pre-Vista (legacy) applications that historically failed to run as standard user. As you are deploying Windows 10 Enterprise, it is very unlikely you will have applications that still require this configuration. |
|
Allow UIAccess applications to prompt for elevation without using the secure desktop |
User Interface Accessibility (UIAccess) programs are designed to interact with Windows and application programs on behalf of a user. This setting allows UIAccess programs to bypass the secure desktop to increase usability in certain cases, but allowing elevation requests to appear on the regular interactive desktop instead of the secure desktop increases your security risk. We recommend disabling this option. |
For more information on how UAC works, see here: https://docs.microsoft.com/en-us/windows/access-protection/user-account-control/how-user-account-control-works.