Chapter 4
TCP / IP
Transmission Control Protocol / Internet Protocol (TCP / IP) is a collection of standard protocols, which was to communicate over large networks, which consist of various interconnected via routers network segments developed.
TCP / IP is z. As usual, etc. connect the Internet, the collection of thousands, globally distributed networks, research centers, universities, libraries, businesses, private individuals.
In contrast, the intranet is a very general term. An intranet is not limited in its size: there are Intranet, which a few, but even those that include hundreds of networks. With the term Internet, however, the global or public Internet is called as the public internet.
This raises the question of how two different hosts that are connected to different networks with a large distance from each other to communicate.
The second part of the answer is a software aspect: to be active on every host needs a universal communication service. Although there are numerous software protocols for intranet, a family stands out among them particularly. This is known as the TCP / IP suite.
The TCP / IP family can be located perfectly in the OSI model. However, presenting the TCP / IP family, usually, a simplified, four-layer model is used: The DoD1- the model also ARPANET reference model or mostly just TCP / IP model named.
In this model are the Internet layer and the transport layer in the center, and advertising deals with the detail in this chapter. The application layer gathers and describes all protocols that use the
TCP / IP protocol. This includes the HTTP protocol used on the Internet for surfing. The TCP / IP protocol is doing a universal communication service available that allows the surf order is possible over the Internet. The network layer then ensures the communication between host and router or between two routers on the LAN.
The Internet Protocol (IP)
The main features and functions of the IP protocol are:
-
The protocol is responsible for routing through the Internet. A 32-bit IP address identifies each host.
-
The IP protocol is connectionless. Every single IP packet can take a different path on the destination way to the destination host, and it does not establish a fixed physical connection.
-
It is built up a universal data packet consists of a header and a DA Tenfold. The header contains, among other things, the sender and the Empfänge- address. The data packet is hardware-independent and is encapsulated in a local network before the transport again.
-
The IP protocol does not check whether data has been sent correctly, and also has no confirmation or correction mechanisms: Send and hope.
-
The IP header has a length of 20 bytes. When using the options field of the header up to 60 bytes can be great. The protocol generates a header checksum.
The Internet Protocol (IP) is (the OSI model layer 3) applies reasonable at the network layer. This layer is responsible for providing and transporting information across different networks. For this purpose, a uniform Addressing of need: the IP address.
As long as the information transfer takes place within the same
network, the DIE function can be disregarded. The connection between different networks is made together by routers. If different networks into a larger whole connectedness to, then you have also any network at a unique address identifiable. Therefore, each network is assigned a unique network address. Based on this network address to each subscriber of the network will be assigned a unique address within half this network address space. The uniform addressing is based on this principle. The address is defined on the IP layer and IP address called.
The IP Address
Generally, An IP address consists of 32 bits or 4 bytes, which are represented by 4 separated by a point decimal number.
Each network has a name (Net ID), and each network device is assigned a unique number (host ID) within this network.
Classification of IP Addresses
IP addresses are divided into different classes. The Figure below shows an overview.
The table below shows the characteristics of the classes A, B, and C. Class D was added to send multicast messages easily. Class E is still unused at present.
The number of bytes distinguishes the classes A, B, and C, respectively used for the Net ID one hand, and the host id other. The most significant bits of the IP address which class an IP address belongs to.
|
class A
|
Net ID
Host ID
range example
|
Byte 1, the first bit is 0, (0 xxxxxxx) 126 possible network addresses
Byte 2 Byte 3 + + byte 4
16777214 possible hosts per network
1 . n. n. n→ 126th n. n. n 90.15.167.2 (network name 90.0.0.0)
|
|
class B
|
Net ID
Host ID
range example
|
Byte 1, the first bits are 0, 1 (1 0 xxxxxx) + Byte 2
16,383 possible network addresses
Byte 3 Byte 4 +
65,534 possible hosts per network
128th 0th n. n→ 191st 255th n. n
128.19.205.132 (network name 128.19.0.0)
|
|
class C
|
Net ID
Host ID
range example
|
Byte 1, the first bits are 1 1 0 (1 0 0 xxxxx) + Byte 2 Byte 3 +
2097152 possible network addresses
byte 4
254 possible hosts per network
192nd 0th 0th n→ 223rd 255th 255th n
192.147.25.112 (network name 192.147.25.0)
|
The allocation of IP addresses from the IANA (Internet Assigned Numbers Authority).
IP Addresses for Private Networks
When assigning addresses, public and private (company) networks distinction to be. The Internet (the sum of all public networks) must each IP address to be unique. Routers connect corporate networks to the Internet. To prevent conflicts between private and public networks, several IP addresses defined within each class, which are not used on the Internet. These are described in RFC 1597 under (Reserved Address Space). A corporate network preferably has given a value from this range allocated as the network address.
Special IP Addresses
The table below shows an overview of the specific IP addresses.
|
Net ID
|
Host ID
|
description
|
|
all zeros
|
all zeros
|
The IP address of each computer is used at startup
|
|
Net ID
|
all zeros
|
Network address identifies a complete-ended network
|
|
Net ID
|
all ones
|
Broadcast address on the network
|
|
127
|
any
|
The IP address for testing networked system applications
|
Router and the Subnet Mask
Each ISP (Internet Service Provider) connects its network with at least one other network. Since each network has unique identification features, the information from one station can be sent to another. Here, routers ensure that the information is properly routed through the Internet. These routers perform so-called routing tables that can be found in those who are where certain IP addresses. The router receives an IP packet, and it compares the destination address with its routing tables. If a match is found, the router knows to which port that packet must be sent.
To simplify the routing and even better use of the existing classes has been created 1985, RFC 950 a possibility to create groups of addresses within the classes A, B, and C. To create multiple subnets within a class, the prefix (Net-ID) is extended by some bits, there
arises an Extended Network Prefix. By using subnets, changes to the IP address per se nothing. However, the information is important for the router, which bits form the Net ID. To this end, the router uses a subnet mask. With this mask, the router filters network share from the IP address.
How is the Subnet Mask Composed?
The network share representing bits maintains the value of 1. The host share representing bits get set to 0.
Thereafter, it is converted into the decimal system.
For example, a Class C address is extended by four network bits. Then the sub is network mask:
11,111,111th 11,111,111th 11,111,111th 11110000
255th 255th 255th 240
Classless Inter-Domain Routing
Due to the success of the Internet is a lack of IP addresses is imminent. The increasing number of networks provides a strong increase in the number of routes, causing a problem for the routing tables globally.
There are two steps to solve this problem:
CIDR (Classless Inter-Domain Routing) is a new form of addressing the Internet, which uses the IP addresses compared to classes A, B, and C efficiently. It is an evolution of Subnetting.
The Net ID is not restricted here more to 8, 16, or 24 bits. A CIDR address includes the 32-bit IP address and additional information about the number of bits that make up the Net ID. Thus, respectively. In the address 206.13.01.48/25 "/ 25" means that the first 25 bits define the network name, while the remaining bits
identify the suffix B. the individual subscriber in the network.
|
CIDR
code
|
subnet mask
|
binary
|
number
hosts
|
|
/ 28
|
255255255240
|
11111111 11111111 11111111 11110000
|
16
|
|
/ 27
|
255255255224
|
11111111 11111111 11111111 11100000
|
32
|
|
/ 26
|
255255255192
|
11111111 11111111 11111111 11000000
|
64
|
|
/ 25
|
255255255128
|
11111111 11111111 11111111 10000000
|
128
|
|
/ 24
|
255.255.255.0
|
11111111 11111111 11111111 00000000
|
256
|
|
/ 23
|
255.255.254.0
|
11111111 11111111 11111110 00000000
|
512
|
|
/ 22
|
255.255.252.0
|
11111111 11111111 11111100 00000000
|
1024
|
|
/ 21
|
255.255.248.0
|
11111111 11111111 11111000 00000000
|
2048
|
|
/ 20
|
255.255.240.0
|
11111111 11111111 11110000 00000000
|
4096
|
|
/ 19
|
255.255.224.0
|
11111111 11111111 11100000 00000000
|
8192
|
|
/ 18
|
255.255.192.0
|
11111111 11111111 11000000 00000000
|
16384
|
|
/ 17
|
255.255.128.0
|
11111111 11111111 10000000 00000000
|
32768
|
|
/ 16
|
255.255.0.0
|
11111111 11111111 00000000 00000000
|
65536
|
|
/ 15
|
255.254.0.0
|
11111111 11111110 00000000 00000000
|
131072
|
|
/ 14
|
255.252.0.0
|
11111111 11111100 00000000 00000000
|
262144
|
|
/ 13
|
255.248.0.0
|
11111111 11111000 00000000 00000000
|
524288
|
The addressing of CIDR also allows the Summary of the Route (Route Aggregation "). This can represent table routing one parent Route numerous minor routes in a global. In this way, a complete hierarchical structural created structure associated with the allocation of compared telephone numbers in local networks advertising the can.
Examples
Show that the server with the IP addresses or 203.125.72.28/28 203.125.72.34/28 does not belong to the same network.
-
Show that this host belongs to the network with the address 192.168.100.96/27.
-
Show that the broadcast address of this network is 192.168.100.127.
-
Show that the IP address of all participants of this network lies between 192168100126 and 192.168.100.97.
-
The participants of the below IP addresses belong to particular sub-networks: 172.23.140.197, 172.23.139.78, and 172.23.136.45.
-
The participants with the IP address 172.23.126.120 172.23.127.92 and include hinge gen on the same subnet.
-
Show that the CIDR is within the corporate network / 23rd
The IP Packet
The information that needs to be transmitted is moved to the Internet layer from the transport layer. The information is packed by the internet layer packs in the field of data and then includes the IP header. This IP packet is then passed layer for further processing of the mediation. Sending data to the protocol is done based on the IP packets.
If a router gets a packet of IPv4 that is too large for the network into which the packet is to be forwarded, the router separates the packet into several smaller packets that fit into the data frames of the subnet concerned. When these packets reach their final destination, the IPv4 protocol of the target host reassembles these packets in the original order. When splitting a package:
-
Each package gets its own IP header.
-
All part messages belonging to the same original message, save the original identification field. The flag more fragments flag indicates that there are more fragments. The last fragment of this flag is not set.
-
The fragment offset field in there, at which point the fragment in question has the original message.
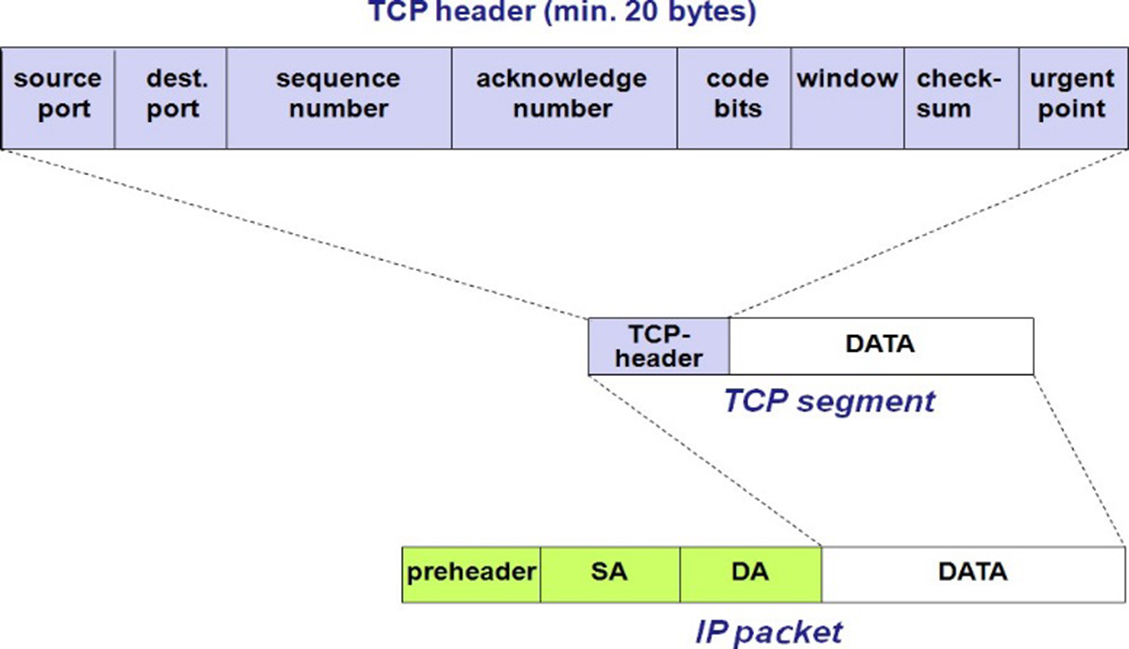
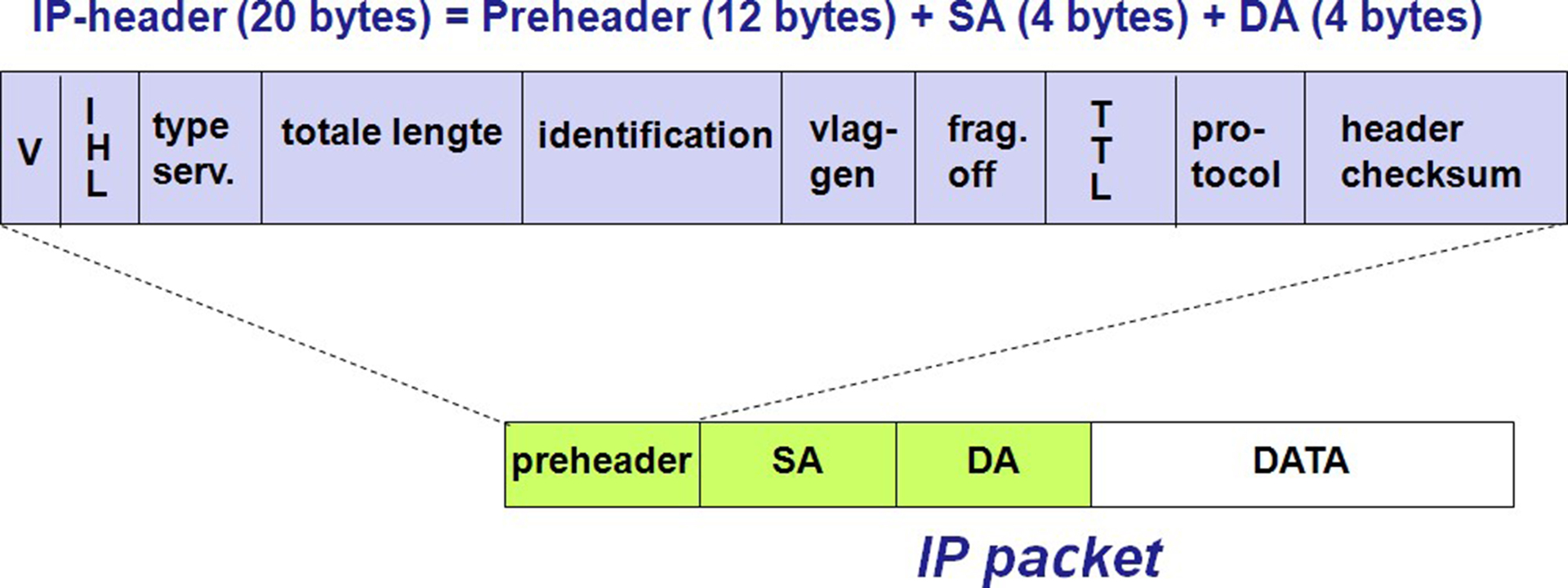
To give a clear idea of the functions of the IP protocol, the IP header is explained in more detail below. The figure below shows the various fields in the IP header. The header consists of a minimum of 20 bytes.
-
Version (V): 4 bits field containing the IP version reflects.
-
IHL: 4-bit wide field indicating the length of the header in bytes.
-
Grade of Service: reserved / priority of the desired service
-
Total length: Total length of the complete IP packet in bytes.
-
ID: If an IP packet needs to be split, each sub-packet is assigned a unique ID, so that the recipient all packets correctly can be joined together again.
-
Flags: The flags are used to monitor the fragmentation of the packets.
-
Fragment Offset: When a data packet is divided, so the position of the fragment is recorded within the original packet here in an 8-bit unit.
-
Time to Live (TTL): Each time an IP packet passes through a router, the value is reduced by the first If the value reaches zero, the router discards the packet concerned shall. In this way prevents a message remains indefinitely loading.
-
Protocol: Reference is made to the next higher protocol.
01hICMP
06h
TCP
11hUDP
-
Header Checksum: Each router recomputes this checksum for the IP header.
-
Source IP Address: IP address of the sending station.
-
Destination IP Address: IP address of the receiving party.
-
Options: additional network information in the IP header can be accommodated. If the option data does not end with a 32-bit word, the rest is filled with zeros.
IPv6
Generally, the most recent previously discussed in this chapter IP protocol has version number 4 (IPv4). However, a new version is necessary due to the huge success of the IP protocol. There is a clear lack of IP addresses. Also, new features need to integrate multiple switches. Also, a new version of the IP protocol can also provide higher performance.
The introduction of IPv6 also brings a practical problem: How can the Internet accessible to the public, which so far is working on the basis of IPv4, switch to IPv6? The easiest way is the so-called dual-stack approach. Here is implemented in knots, both IPv6 and IPv4. These nodes can process; therefore, both IPv4 and IPv6 datagrams.
In the field of industrial automation is not working at the time on the integration of IPv6.
The following are some features of IPv6 are described briefly. There are, however, as far as possible, the characteristics that have made IPv4 so successful considered.
IP Address
IPv6 provides IP addresses before with a length of 128 bits. This creates extensive addressing. The 128 bits long addresses are recorded in 8 separate from each other by colons groups of 4
hexadecimal digits:
2000: 0000: 0000: 0FED: CBA9: 8765: 4321
2000 :: FED: CBA9: 8765: 4321
IPv4 addresses: 192.32.20.46
IPv6 header has been changed extensively. It is now used as a simpler basic header, which provides the ability to integrate optional headers and processing time header ensures to offer a substantial reduction of the router. Some IPv4 fields there are not more or available only as an option. The fields in the IPv6 header:
-
To identify a 20-bit identification number to a packet in a data stream: flow label.
-
Hop Limit: The maximum number of routers that can pass through a particular package.
-
Next Header: Defines the type of the first optional header.
-
Version field: This 4-bit field specifies the IP version number. For IPv6, this value is the sixth
-
Payload Length: This 16-bit number is an unsigned integer value, specifying the number of bytes in the IPv6 datagram, which follows after the 40-byte standard header.
-
Since the protocols of the transport layer (TCP and UDP) and link layer (z. B. ethernet) calculate the Internet checksum were the IPv6 developers, believe that in the Internet layer no checksum is needed
Transmission Control Protocol (TCP)
IP is a connectionless packet delivery protocol. TCP has, therefore, been a difficult task: About the unreliable IP packet services has various application programs a reliable data transmission service is provided applications for many check the reliability of a
transmission system is an essential feature: The system must ensure that no data is lost, duplicated, or arrive in the wrong order.
End-to-End Transport Service
The TCP protocol is responsible for transferring information correctly through one or more power plants. The exchange of data with TCP is called a connection-oriented: It establishes a logical connection, used, and then stopped again. TCP is, therefore, an end-to-end protocol. The Figure below illustrates this relationship. TCP sees IP as a mechanism by which the TCP can exchange on a particular host data with a TCP on a second, remote host.
From the perspective of the TCP, the entire Internet is a communications system that can send messages and receive, without altering their content or to interpret.
Reliability is Guaranteed
TCP is a library of routines that can be used by applications when they want to add a reliable communication with another participant or host.
To ensure complete reliability, TCP uses a variety of techniques.
Resending datagrams:
If TCP receives data, it sends an acknowledgment (Acknowledgement) back to the sender. Every time the TCP sends data, a timer is started. If the timer expires before the acknowledgment is received, the data is sent again (see also the next Figure).
Window mechanism for data stream control:
When a connection is established, each of the two communication partner reserved connection of a buffer for incoming and outgoing data, and notifies the respective another end of the size of this buffer with. The available buffer size at any given time is called Window, shares the so-called Window Size Window Advertisement. The receiver sends along with each receipt a window advertisement. If the receiving application can read the data as fast as they are received, it
transmits a positive Window Advertisement along with any confirmation. If the data but faster when the receiving end they can read, the receiver buffer is full at some point. The receiver then reports a window size of zero (SZERO window ").
Three-way handshake:
To ensure that connections are established reliably and terminated, the TCP uses a three-way handshake is exchanged in which three messages. TCP uses the term synchronization segment (SYN segment) for messages in a three-way handshake used for stable connections. Called FIN segment messages are named for terminating a call in a three-way handshake.
The TCP Segment
The information to be transmitted is passed layer from the application layer to the transport. The transport layer packs the information in the data field and then adds the TCP header. This packet is then passed on for further processing to the Internet layer. The sending of data with the TCP protocol is done on the basis of TCP segments.
To give a clear idea of the functions of the TCP protocol, the TCP header is explained in more detail below. The Figure above shows the various fields in the TCP header. The header consists of 20 bytes.
-
Source Port and Destination Port: TCP is accessible via
different port numbers for the applications in upper layers. Ports are unique 16-bit addresses. The combination of a port having an Internet address according to the originally called socket as per ARPA definition 1971. The use of port numbers is important for establishing communication between different applications. It will be discussed further later in this chapter, even closer to it. The table below provides an overview of commonly used in automation ports.
-
Sequence Number: The TCP each byte is assigned a number. The sequence number (SSE sequence Number ") is the number of first data byte in the TCP segment after the TCP header.
-
Acknowledgment Number: This field contains the next number of sequences from the partner as the expected sequence number.
➢
The RST bit with which the communication can be re-initialized;
➢
The SYN bit, with which the communication can be restarted;
➢
The FIN bit is indicating that communication can be terminated.
-
Window: The Window field specifies the maximum amount of data bytes again, that can be sent prior to sending and receiving a confirmation.
-
Checksum: a checksum of the TCP packet;
-
Urgent Pointer: This value indicates where the urgency information starts loading in the data field. To urgent information to send a TCP packet must be the URG code bit set.
UDP
The protocol suite of the Internet, namely, also includes a connectionless transport protocol, UDP (User Data Protocol). With the UDP applications can send IP packets without having to establish a connection. Many client-server applications that include a request and a response using UDP instead of having to connect and later quit again. UDP is described in RFC 768 pixels.
UDP is almost a null protocol: The only services that it provides are a checksum for the data and multiplexing applications using port numbers. The UDP header is, therefore, much easier than that of the TCP.
A UDP segment consists of a header having a size of eight bytes followed by the data.
The header consists of:
-
Source port (2 bytes): port number of the sender, if no port is used, the value is zero.
-
Destination port (2 bytes): Port of the application for which the message is intended.
-
Length (2 bytes): The length of the UDP header and the encapsulated data in bytes.
-
Checksum (2 bytes)
A typical example of UDP is real-time audio. If this lost data packets, which is unfortunate, but does not affect the continued functioning of the application.
TCP and UDP Ports in the Automation
In this list, we give an overview of some commonly used in automation port numbers.
|
application
|
Port number / Protocol
|
|
FTP Data (File Transfer Protocol)
|
20 / TCP
|
|
FTP Control (File Transfer Protocol)
|
21 / TCP
|
|
SSH (Secure Shell)
|
22 / TCP, UDP
|
|
Telnet protocol
|
23 / TCP
|
|
BootP server
|
67 / UDP
|
|
DHCP server
|
67 / UDP
|
|
BootP client
|
68 / UDP
|
|
DHCP client
|
68 / UDP
|
|
TFTP (Trivial File Transfer Protocol)
|
69 / UDP
|
|
HTTP (Hypertext Transfer Protocol)
|
80 / TCP
|
|
NTP (Network Time Protocol)
|
123 / UDP
|
|
SNMP (Simple Network Management Protocol)
|
161 / TCP, UDP
|
|
SNMP TRAP (Simple Network Management Protocol Trap)
|
162 / TCP, UDP
|
|
HTTPS (Hypertext Transfer Protocol Secure)
|
443 / TCP
|
|
ISAKMP (Internet Security Association And Key Management Protocol)
|
500 / UDP
|
|
MODBUS
|
502 / TCP; UDP
|
|
IPsec NAT traversal
|
4500 / UDP
|
|
EtherNet / IP
|
2222 / TCP; UDP
|
|
PROFINET, such as connection establishment
|
0x8892 (34962) / UDP
0x8893 (34963) / UDP
0x8894 (34964) / UDP
|
|
IANA, free ports reserved for dynamic and / or Private Ports (Profinet Service)
|
0xC000 - 0xFFFF
|
|
DDI Device Driver Interface (especially for Diagnostic function Utilized protocol)
|
1962 / TCP
|
|
SOCOMM interface (engineering channel Control communication)
|
20547 / TCP
|
Communication Via TCP (UDP) / IP
Client-Server Model
A network (TCP / IP) provides a general communication infrastructure without specifying it, what services can be used. TCP /
IP provides a Basic communications Service available, but the protocol software is not up able to contact a remote party or answer. Therefore, in every communication, two application programs must be used simultaneously: one starts communication, the other accepts it.
One significant problem is that the protocol software has no way an application program to communicate is that attempted to shoot a communication. Therefore base communication between two users on a model in which a purchase application is active (Request of interaction), while the other is passive (listening and possibly accept). Such a model is currently generally employed in communication between two hosts via TCP / IP and is called a client-server model. A server application waits passively for contact, and the client application starts the communication active.
Features of the Client Software
-
It is started directly by the user and performed only for a single session.
-
It runs locally on the PC of a user.
-
She actively contacts the server.
-
Can get to multiple servers if necessary access, but will point at any given time only to a server contact.
-
Requires no special hardware or a complex control system.
Features of the Server Software
-
Server software, however, can deal with several clients, a special application program that accurately represents a particular service available simultaneously.
-
It is started automatically during system startup and remains active for many sessions.
-
You are passively waiting for contact from any client.
-
They often require powerful hardware and a sophisticated control system (depending on the application).
Endpoint and Internet Socket
The previous Figure shows a client-server communication via the TCP / IP stack. On a computer system, several clients and servers can be active simultaneously. Each application must be uniquely identifiable, and a computer to run applications on multiple presences, has only one physical connection to the Internet.
To this end, transport protocols give each communication service a unique name. TCP protocol used port numbers. Each server is assigned a specific protocol port number. About this port number, the server waits for communication requirements on the computer. When sending a request, the client reports the port number of the requested service. The TCP software on the server computer uses the destination port number in an incoming message to edit certain to which server the request must.
Endpoint
The term endpoint sometimes leads to confusion with the term socket. According to ARPANET originally defined in the socket, the combination of an IP address with the port number. This combination is now called the endpoint. Describes an endpoint, over which logical way an application is accessible in a network.
Internet Socket
The term socket is now a pure software concept. A socket provides for the MAP ping, linking an application with an endpoint. Thus, the term intervention arises net socket, also known as a network socket.
An Internet socket or short socket is a bidirectional communication endpoint for a process-to-process connection and is determined by:
-
UDP: Datagram Sockets or connectionless sockets
-
TCP: Stream sockets or connection-oriented sockets
-
Basic IP packet (for example, ICMP.): Raw sockets
The Dynamic Server
Can work on a computer system with multiple applications at the same time, they say, it supports multitasking. A program with more than one thread of control (or short thread), process, or task is called a competing program.