Before we get into the details of how to model threats, we must become familiar with some common terms used throughout the process of threat modeling. Some common terms are as follows:
- Asset: An asset can be any resource that is valuable. The asset can be tangible or intangible. For example, a mainframe computer in a data center may be a tangible asset while the reputation of an organization may be an intangible asset.
- Attack: An attack is something that happens when an actor or a threat agent takes action utilizing one or more vulnerabilities in the system. For example, an application session hijacking attack might happen when someone exploits a cross-site scripting vulnerability to steal user cookies and session IDs.
- Attack vector: An attack vector is a path taken by the attacker in order to successfully compromise the system. For example, an email with a malicious attachment sent to the victim could be one possible attack vector.
- Attack surface: An attack surface essentially marks out the in-scope components that need to be taken into consideration while enumerating threats. The attack surface may be logical or physical.
- Countermeasures: In simple terms, countermeasures help address or mitigate vulnerabilities to decrease the likelihood of attacks and consequently the impact of a threat. For example, installing antivirus software would be one countermeasure for addressing virus threats.
- Use case: A use case is a normal functional situation that is intended and expected in line with the business requirements. For example, a drop-down menu allowing the end user to select a color of choice may be one of the use cases of an application.
- Abuse case: When a user (actor) deliberately abuses functional use cases in order to achieve unexpected results, it is known as an abuse case. For example, an attacker might send 1,000 characters to an input field with a maximum length of 20.
- Actor or threat agent: An actor or a threat agent may be a legitimate or an adverse user of use or abuse cases. For example, a normal end user logging into an application with his valid credentials is an actor while an attacker logging into an application using SQL injection is also an actor (threat agent).
- Impact: An impact, in simple terms, is the value of the damage after a successful attack. It may be tangible or intangible. If a system holding financial data is breached, it may have a revenue impact, while if a company website is defaced, it may have a reputational impact.
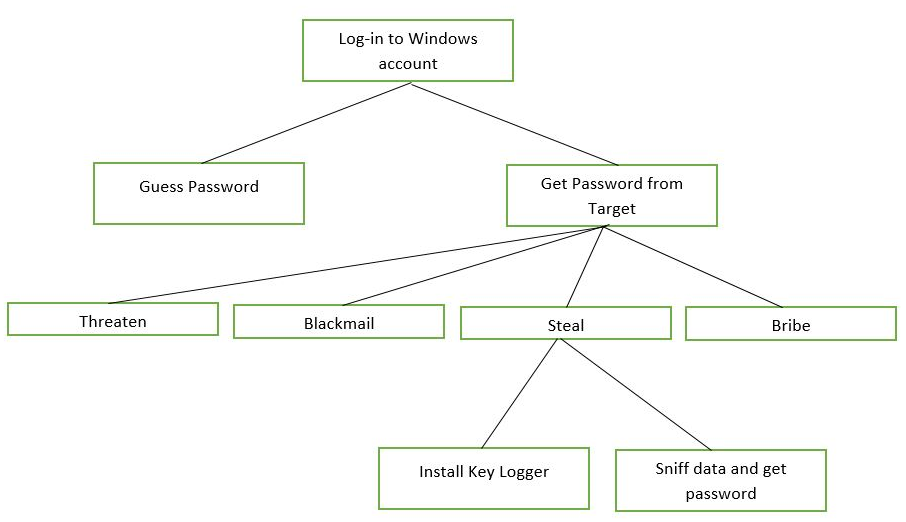
- Attack trees: Attack trees visually depict the various paths available in order to successfully attack or compromise the target. The following diagram shows a sample attack tree for gaining access to a Windows system:
- Data flow diagrams: Various types of diagram are used to visualize interactions between the various components of the system. Although there are different types of threat modeling diagram, the most commonly used type is the data flow diagram (DFD). DFD is used to display major components of an application and the flow of information between those components. DFD also indicates trust boundaries showing the separation of information that is trustworthy and information that requires additional caution while being used in the application.