Similar checks can be performed using the Metasploit modules. Open Kali Linux, which we installed in the VM, and type the following command in Terminal:
msfconsole
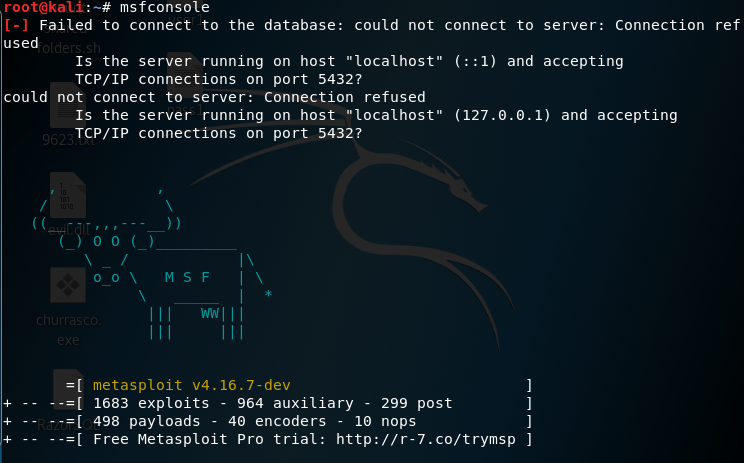
This is used to open the Metasploit console. There is also a GUI version of Metasploit available with the name Armitage. To find out the various Metasploit modules that are available for SCADA, enter the following command:
searchscada

As shown in the preceding screenshot, various modules for SCADA that are supported by Metasploit are loaded. Let's try a specific search for Modbus to see what modules are supported:
searchmodbus
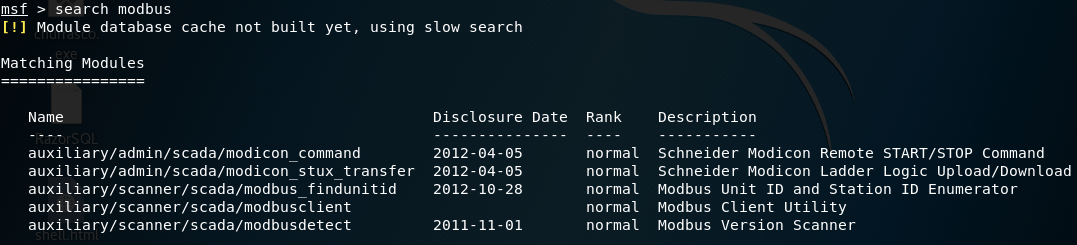
From the preceding screenshot, you can use modbusdetect to identify whether Modbus is running on port 502 using the following syntax:
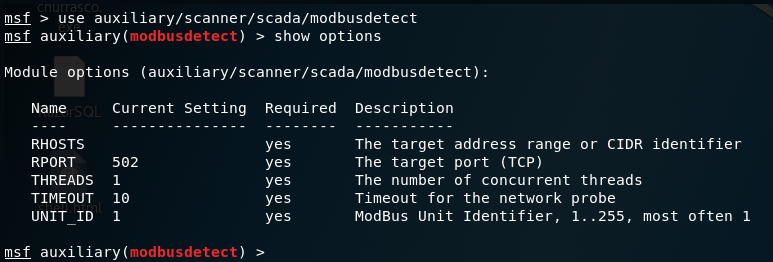
use auxiliary/scanner/scada/modbusdetect
Fill in the required details by using show options to identify the same:
Set RHOSTS to 192.168.75.133 using the following command and run the exploit:
set RHOSTS 192.168.75.133
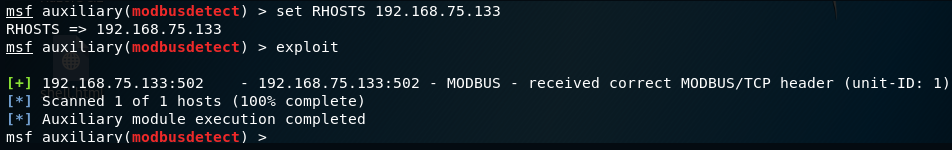
The preceding screenshot shows that the module has detected the presence of Modbus on port 502.