11
Locks
There is no padlock that you cannot open. However, this all depends on how skilled you are; therefore, you should always get hands-on practice.
Opening tools are designed to help you open the doors of the enemy house with ease. Therefore, of all the arts, this is the one conducted when you are closest to the enemy.
—Bansenshūkai, Ninki III 1
In ancient Japan, locks were simpler than the locking devices of today, as the manufacturing capabilities of the time could not produce the intricate pins, tumblers, and other components that contemporary locks use. However, these older locks were elegantly designed, making exemplary use of “prongs, latches, and the natural forces of gravity and tension” to keep people’s valuables safe from intruders and thieves.2
Shinobi regularly encountered complex locks during their missions—and devised ways to open all of them. The scrolls indicate that no lock, barrier, or other mechanism was safe from a shinobi with well-constructed tools, sufficient training and ingenuity, and an optimistic mindset. Significant portions of all three scrolls are dedicated to documenting how to make and use various picks, shims, and other probing tools used to open locks, doors, and gates (Figure 11-1).3
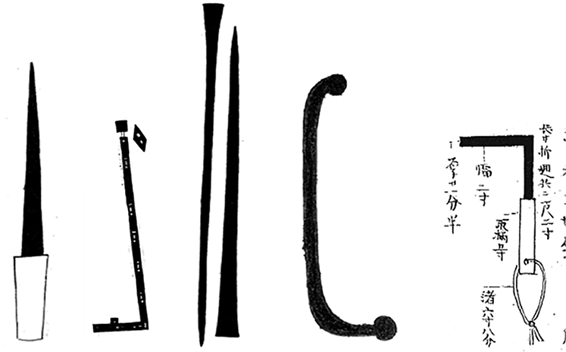
Figure 11-1: A variety of tools used to open locks, doors, and gates. From left to right, a probing iron, an extendable key, lockpicking shims, a pick for guided padlocks, and a door-opening tool (Bansenshūkai and the Ninpiden).
From ring latches to rope, locking bars to hooks and pegs, sophisticated key latches to rudimentary, homemade technology . . . whatever the lock’s design, shinobi had methods and tools to bypass it. In fact, shinobi were able to breach any security system or deterrent used at the time.4 Knowing that locks could not be fully trusted, shinobi themselves developed techniques to take security into their own hands. Some were bluntly simple: when sleeping in lodgings secured by locks they did not trust, shinobi sometimes tied a string from the door or window to the topknot in their hair, ensuring they would wake up if the door latch or lock were opened as they slept.5
Today, as in the time of shinobi, people use locks to safeguard their property—and threat actors still use picks to defeat them. The lock, as it always has, serves multiple purposes: it works as a deterrent. It is a visible assurance to an owner that their property is safe. It creates a system of accountability to the key holder(s) if the lock is breached through use of a key. It also serves as a barrier and an alarm, since thieves will take time and make noise as they attempt to bypass it. In this chapter, we will discuss how hackers, much like shinobi, are still picking locks and bypassing security. Furthermore, we’ll talk about why physical locks are so important to digital systems and detail the necessary companion precautions. We will also explore some technological advances in locks and picks, discovering what else the shinobi can teach us about security.
Physical Security
Just as lockpicking is often a gateway hobby into hacking, defeating a lock is a common entry point into cybersecurity. The act of finding flaws in or physically accessing a thing that is supposed to be secure—the visual, tactile, and audible feedback of a lock’s opening in your hand after you’ve beaten its defenses—can be a powerful sensation. It can pique interest in the security field and build confidence in fledgling abilities.
The cybersecurity industry uses locking devices to restrict physical access to buildings, data centers, switching closets, and individual offices.6 On a more granular level, rack locks limit access to servers, chassis-case locks limit access to a system’s physical components, device port locks prevent unauthorized use of USBs or console jacks, tethering locks prevent systems from leaving their location, and power locks keep devices from turning on at all. Locking down physical access to systems is a crucial piece of an organization’s cybersecurity strategy. If systems are vulnerable to being tampered with physically, many digital security controls are at risk of being rendered ineffective once the adversary gains physical access. It should be assumed that, if adversaries gain physical access to a machine, they also gain admin-level privileges on the system and acquire its data.
Despite the proliferation of illicit lockpicking tools and techniques, organizations tend to use the same locks year after year, leaving themselves extremely vulnerable to attack. Most information system and building access locks use weak pin tumblers, such as the Yale cylindrical lock—patented in the 1860s and now the world’s most common lock due to its low cost and ease of mass production—and tubular locks (or “circle locks”), the most common type of bicycle lock. Criminals construct, sell, and use picking tools that can easily beat these off-the-shelf locks. For example, soda can shims can pry open locks, pen caps can simulate tubular keys, and 3D-printed plastic keys can be easily forged from pictures of the original. For the unskilled criminal, autoelectronic lockpickers can, with the pull of a trigger, do all the work of picking every tumbler lock’s pin within seconds.
Large-scale lockpicking countermeasures are few and far between, and some are more concerned with liability than security. For example, certain insurance policies won’t cover break-ins and thefts if inferior locks—such as the most common ones sold in the United States—were picked or bypassed during the crime. Some governments issue compliance standards for lock manufacturers, along with restrictions that bar selling substandard locks to citizens. In the cybersecurity realm, select governments safeguard their classified systems and data with a combination of cipher locks or other high-assurance locks and supplemental security controls that mitigate the lock’s security flaws.
However, too many doors and systems still use weak lock-and-key defenses—defenses that even a mildly sophisticated threat actor can defeat with ease. Locks and barriers for information systems must be improved to mitigate against common attacks such as shimming, picking, stealing, copying, and forcing.
Improving Locks
Preventing all lockpicking is likely impossible. However, there are many proactive steps you can take to improve the resiliency of your locks. Improving locks will also improve your cybersecurity posture by mitigating unauthorized physical access attacks to your systems.
- Upgrade your locks. Evaluate the more advanced locking systems, such as European dimple locks, to determine which ones are compatible with your business requirements and budget. Seek approval from your stakeholders and physical security team and then upgrade all of your locks to models that are more resilient to attack.
- Think outside the lock. Consider nontraditional locking solutions for your organization, such as multiple-stage locks. When a first-stage unlock mechanism controls access to a second-stage lock, intruders cannot quickly and easily open both locks at once or in quick succession.
For instance, to close off an entryway, use two independent locking systems that complement each other. The first stage could be a digital 4-digit PIN lock that would temporarily unfreeze the pins in the second-stage lock, a cylinder lock. While the pins are frozen in the second-stage lock, they are impossible to pick, but a key could be inserted in preparation for activation by the first-stage lock. Once the pins are temporarily unfrozen, the physical key can be turned, and the entryway can be unlocked. However, this window of opportunity opens for only three seconds. After that, the digital lock resets and refreezes the pins. To be successful, the intruder would need to first learn the PIN and then be able to pick the door lock in under three seconds, a feat that may not be humanly possible.
- Add reinforcements. Consider reinforcing the thing the lock is securing. You might protect the hinges from tampering or install strike plates, door/frame reinforcements, door handle shields, or floor guards.
- Petition the lock industry. Urge the lock industry to innovate and incorporate new designs into products used to protect information systems. Until there is sufficient consumer pressure to upgrade their outdated products, manufacturers will continue to sell the same familiar, vulnerable equipment.
Recommended Security Controls and Mitigations
Where relevant, the recommendations are presented with applicable security controls from the NIST 800-53 standard. Each should be evaluated with the concept of locks in mind.
- Secure paper files, magnetic tape, hard drives, flash drives, disks, and other physical media in locked, controlled containers. [MP-4: Media Storage; MP-5: Media Transport]
- Use secure keys or other locking devices to enforce physical access controls and authorization to systems and environments. [PE-3: Physical Access Control | (1) Information System Access | (2) Facility/Information System Boundaries | (4) Lockable Casings | (5) Tamper Protection; PE-4: Access Control for Transmission Medium; PE-5: Access Control for Output Devices]
Debrief
In this chapter, we talked about locks and their purposes. We noted that adversaries, no matter the era, will develop tools and techniques to bypass locks. We touched on the common lock technologies used to protect access to systems and why it’s important to upgrade them. It’s especially important to remember that, if an adversary gains physical access to your system, you should assume they can compromise it—hence the importance of physically preventing access to those systems with locks.
In the next chapter, we will discuss an advanced tactic shinobi used when the target was very securely locked down—one that effectively tricked their adversary into giving away the key. In a way, an organization’s defenses aren’t that different. Even if you have the best lock, if you give the key to an intruder, it won’t help you.