Mobile is living up to the hype as the next great technology revolution, rivaling the Internet in its game-changing impact. Of course, with great change comes potential risk—is there a magic bullet to secure the inevitable adoption of mobile everywhere? This book presents the latest mobile security trends and observations from the field by some of the leading practitioners in mobile security worldwide.
In many ways, this book is a wake-up call for anyone who uses a mobile device. The world-in-the-palm-of-your-hands power that these devices convey has a dark side in the event of loss or theft. This book will show you the many ways you can find yourself on that dark side, and how to get out.
We particularly focus our mobile security advice in this book on the following audiences:
• Mobile app developers
• Corporate IT staff
• IT consultants
• Technology managers and leaders
• End-users
These are the people we work with daily to identify and fix the many issues we’ll recount in these pages, so naturally our writing is directed at those who can make the most difference in directly and indirectly changing the evolving mobile technology environment to make it safer for everyone.
We’ve also focused our discussion on the two leading mobile platforms today: Apple’s iOS and Google’s Android mobile operating systems. The market share held by these platforms is so dominant at this point that it’s hard to imagine a radically different future, so we’ve striven to provide the most relevant technical analysis possible for the most-used platforms.
Way back in 1999, the first edition of Hacking Exposed™ introduced many people to the ease with which computer networks and systems are broken into. Although there are still many today who are not enlightened to this reality, large numbers are beginning to understand the necessity for firewalls, secure operating system configuration, vendor patch maintenance, and many other previously arcane fundamentals of information system security.
This book shows you how to meet the mobile security challenge with the two-pronged approach adapted from the original Hacking Exposed™.
First, we catalog the greatest threats your mobile deployment will face and explain how they work in excruciating detail. How do we know these are the greatest threats? Because we are hired by the world’s largest companies to break into their mobile applications, and we use attacks based on these threats daily to do our jobs. And we’ve been doing it for many years, researching the most recently publicized hacks, developing our own tools and techniques, and combining them into what we think is the most effective methodology for penetrating mobile application (in)security in existence.
Once we have your attention by showing you the damage that can be done, we tell you how to prevent each and every attack. Deploying a mobile application without understanding the information in this book is roughly equivalent to driving a car without seat belts—down a slippery road, over a monstrous chasm, with no brakes, and the throttle jammed on full.
The ancient debate: start with page one or jump to the good parts? We say: both!
Clearly, this book could be read from start to finish for a soup-to-nuts portrayal of mobile application security testing and remediation. However, true to the original Hacking Exposed™ model, we have attempted to make each chapter stand on its own, so the book can be digested in modular chunks, suitable to the frantic schedules of our target audience.
Moreover, we have strictly adhered to the clear, readable, and concise writing style that readers overwhelmingly responded to in Hacking Exposed™. We know you’re busy, and you need the straight scoop without a lot of doubletalk and needless jargon. As a reader of Hacking Exposed™ once commented, “Reads like fiction, scares like hell!”
We think you will be just as satisfied reading from beginning to end as you would piece by piece, but it’s built to withstand either treatment.
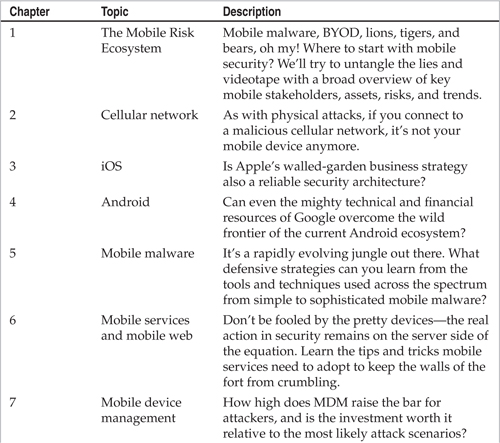
As we recount in more detail in Chapter 1, this book is designed to explore the most important components of the mobile risk ecosystem, from the various perspectives noted earlier (mobile app developers, corporate IT staff, IT consultants, technology managers and leaders, and end-users). Based on this list of players, and on our own experiences with mobile security through hands-on research over the last several years, we’ll cover topics including the following:

A lot of combined experience from some of the top mobile security consultants in the world is packed into these pages—how will you use it?
Here are some more features of this book that we hope will help.
As with Hacking Exposed™, the basic building blocks of this book are the attacks and countermeasures discussed in each chapter.
The attacks are highlighted here as they are throughout the Hacking Exposed™ series:
 This Is an Attack Icon
This Is an Attack IconHighlighting attacks like this makes it easy to identify specific penetration-testing tools and methodologies and points you right to the information you need to convince management to fund your new security initiative.
We have also followed the Hacking Exposed™ line when it comes to countermeasures, which follow each attack or series of related attacks. The countermeasure icon remains the same:
 This Is a Countermeasure Icon
This Is a Countermeasure IconThis should be a flag to draw your attention to critical-fix information.
We’ve also made prolific use of visually enhanced

icons to highlight those nagging little details that often get overlooked.
Mobile security is a rapidly changing discipline, and we recognize that the printed word is often not the most adequate medium to keep current with all of the new happenings in this vibrant area of research.
Thus, we have created a website that tracks new information relevant to topics discussed in this book, along with errata and a compilation of the public-domain tools, scripts, and techniques we have covered throughout the book. That site address is
It also provides a forum to talk directly with the authors. We hope you return to the site frequently as you read through these chapters to view any updated materials, gain easy access to the tools that we mentioned, and otherwise keep up with the ever-changing face of mobile security. Otherwise, you never know what new developments may jeopardize your mobile devices before you can defend yourself against them.
We’ve poured our hearts, minds, and combined experience into this book, and we sincerely hope that all of our effort translates to tremendous time savings for those of you responsible for securing mobile infrastructure and applications. We think you’ve made a courageous and forward-thinking decision to stake your claim on the new mobile frontier—but, as you will discover in these pages, your work only begins the moment the app goes live. Don’t panic—start turning the pages and take great solace that when the next big mobile security calamity hits the front page, you won’t even bat an eye.