Chapter 1
Understanding Digital Forensics
Abstract
Digital forensics is a discipline that must be practiced consistently to ensure the collection, preservation, and presentation of digital evidence is upheld to legal requirements. It is important that the implementation of digital forensics aligns strategically and its contextual usefulness is well understood.
Keywords
Crime; History; Overview; Resources; ScienceThis chapter provides an introductory into the history of digital crime and digital forensics as they evolved side-by-side over the last half century.
Introduction
Digital forensics has always been labeled as an “interesting” profession to work in. This comes as no surprise as public interest spikes; fueled by the works of novelists and film makers who made the world of digital crime and digital forensic both appealing and stylishly straightforward. But the reality is, there is a lot more discipline to the digital forensic profession that what is portrayed in the media.
While it is relatively known that there are legal aspects involved with digital forensics, most people are surprised to learn that the profession involves a great deal of scientific principles, methodologies, and techniques. Not only does digital forensics require a significant amount of specialized training and skills to properly apply these scientific fundamentals, digital forensics is also somewhat of an art form where analytical experience comes into play.
History of Digital Crime and Forensics
Information technology has been involved in criminal activities for more than half of a century. Dating as far back as the 1960s, computer crimes were first committed as either physical damage or sabotage to computer systems. But when technology first arrived, most people did not think that it would one day become such an integral part of our everyday lives. If history has taught us anything, it is that as information technology advances there will always be both new and evolved digital crimes.
With a growing commercialization of technology and the expansion of the Internet, computer crimes continue to take the next step in an ever evolving threat landscape. Moving forward from the 1970s and into the new millennium, computer crimes expanded out from just damage and sabotage into digital crimes such as fraud, denial of service, SPAM, advanced persistent threats (APTs), and extortion.
Prologue (1960–80)
From the 1960s to 1980s, computers were primarily owned and operated by corporations, universities, research centers, and government agencies as industrial systems largely supporting data processing functions and were, for the most part, not connected to the outside world.
Responsibility for securing these computers was left to the system administrators with routine audits done to ensure the efficiency and accuracy of the data processing functions. These activities were essentially the first systematic approach to a computer security discipline. It was during this time period that the computer first became a point of interest to the information security, legal, and law enforcement communities.
Several government agencies started creating small ad hoc groups of individuals who were provided with basic training on computer systems. These investigators would then work with administrators to gather information from the computer systems to be used as evidence in criminal matters.
Prior to the 1980s, computer crimes were dealt with using existing laws. In response to the increasing computer crimes, law enforcement agencies began creating additional laws to address them. The first computer crime law, the Florida Computer Crimes Act, was created in 1978 to address fraud, intrusion, and all unauthorized access to computer systems. The evolution of crime into computer systems during this time period instinctively coined the terms computer forensics, forensic computer analysis, or forensic computing.
Infancy (1980–95)
With the arrival of the IBM personal computer (PC), there was a sudden explosion of computer hobbyists. These PCs had very few applications and were not user friendly which enticed hobbyists to write program code to access the internals of the hardware and operating system (OS). Among the hobbyists were individuals from law enforcement, government agencies, and other organizations who collectively shared their understanding of computers and how technology could play a larger role as a source of evidence. Much of time and money spent by these individuals to learn about these new technologies was done on their accord because their respective agencies did not necessarily support their efforts.
Investigations performed by these pioneers were fairly basic in today’s perspective. The Internet was not yet widely available for consumers which limited the scope of most cases to data recovery on stand-alone systems. Cybercriminals mostly consisted of a mix between traditional criminals who used technology to support their activities (ie, phreaking1) and people who used their technical skills to illegally access other computers.
In this time period there were very few forensic tools available which left investigators to either build their own or use available data protection and recovery applications to perform their analysis. Additionally, the only means of preserving evidence at this time was to take logical backups of data onto magnetic tape, hope that the original attributes were preserved and restored it to another disk where analysis was performed using command-line utilities.
Throughout the 1990s, forensic tools began to emerge from both the hobbyists (ie, Dan J. Mares’ Maresware, Gord Hama’s RCMP Utilities) and larger software vendors (ie, Norton’s Utilities, Mace Utilities). These applications and software suites were each developed to solve specific forensic activities (ie, imaging, file recovery) and proved to be powerful tools for the computer forensics practice.
As technology became more widely available and reports of different type of computer crimes were growing in publicity, law enforcement agencies around the world started responded by enacting similar laws. Canada was the first to respond in 1983 by amending their Criminal Code. Following suite, several other nations began implementing legislation in response to computer crimes including the 1984 U.S. Federal Computer Fraud and Abuse Act, the 1989 amendment of the Australian Crimes Act to include Offenses Relating to Computers, and the 1990 British Computer Abuse Act.
In parallel to the establishment of computer laws, the forensic community was growing in popularity and interest. Agencies recognized that the majority of forensic investigations were performed by individuals who had minimal training, operated on their own terms, used their own equipment, and did not follow any formal quality control. From this, efforts began to create a common body of knowledge (CBK)2 of principles, methodologies, and techniques that could be applied to standardize and bring formal structure to computer forensics.
Childhood (1995–2005)
The years between 1995 to 2005 proved to be a major step forward in the maturity of forensics. Technology quickly became pervasive among consumers where it was embedded in elements of our daily lives which drove significant innovation such as cellular phones. Plus, the Internet had gained enough momentum where it was becoming more readily available for use in homes and businesses; introducing personal accessibility to e-mail and web browsing.
Accompanied by these technology advancements was the opportunity for criminals to commit new cybercrimes. An example of this opportunity being made available through technology occurred following the events on September 11, 2001; when investigators realized that digital evidence of the attack was recoverable on computers all across the world. This revelation reinforced the fact that criminals were using technology in the same ubiquitous ways as the everyday consumers were.
From the technology sponsored growth in digital crimes, the term computer forensics became increasingly challenging to use because both crimes and evidence could now be found throughout networks, printers, or other devices. In 2001, the first annual Digital Forensic Research Workshop (DFRWS) recognized that computer forensics was now considered a specialization and proposed the use of the term digital forensics to describe the field as a whole.
Expansion into this new digital forensic field resulted in the creation of specializations for investigating new technologies. In addition to the traditional computer forensics becoming a concentration, there was the introduction of network forensics and cellular forensics. However, with the formation of these specializations came increased technical sophistication and legal scrutiny over the requirement to follow standardized principles, methodologies, and techniques.
The formalization of digital forensics led to the first publication of digital forensic principles being issued between 1999 and 2000 from the combined work of the International Organization on Computer Evidence, G-8 High Tech Crime Subcommittee, and the Scientific Working Group on Digital Evidence. Likewise, forensic tools underwent an evolution away from the simple homegrown application, used by the hobbyist, and into sophisticated commercial suites of tools. At the same time, the digital forensic community continued to mature where professional certification programs had been created to not only recognize individuals with the appropriate knowledge and experience but also acknowledge the laboratory environments that met the requirements of forensic science principles, methodologies, and techniques.
Adolescence (2005–15)
Attributed to the academic preparation required, in addition to formal training, the maturity of digital forensics has grown exponentially to a point where it is now recognized by the Information Security profession as a core skill area. Colleges and universities have recognized the popularity and appeal of digital forensics leading to the creation of numerous academic and professional education programs around the world. Furthermore, the number of international conferences dedicated to the field of digital forensics continues to see increased attendance rates as the integration of digital forensics with other professions evolves.
During this time, the American Academy of Forensic Sciences, one of the most widely recognized professional organizations for establishing the forensic disciplines, created a new section specific to digital and multimedia sciences. This development led to a major advancement in recognizing digital forensics as a scientific discipline by providing a common foundation for specialized groups of people who can share knowledge and address current forensic challenges.
Technology has now reached a point in its evolution where almost every device has some type of storage medium and can, in some fashion, be connected to the Internet. Naturally this has driven the development of systems and applications that are increasingly adaptive and accessible from virtually anywhere and, if not secured properly, by anyone. Capitalizing on technology’s modern pervasiveness, cybercriminals once again expanding their portfolio to incorporate new and sophisticated attacks, such as varying levels of phishing campaigns (ie, spear, whaling, cloning), Advanced Persistent Threats (APTs) or even cyberespionage.
With the change in cyberattacks comes new way that digital evidence is created, gathered, and processed. Adapting to the new wave of digital evidence sources, commercial software suites began to transform from offering functionality specific to digital forensics and into other professions where digital forensics is used. Inclusive to professions like cybersecurity, electronic discovery (e-discovery), or incident response, digital forensics has become an underlying foundation driving several information security disciplines.
The Future (2015 and Beyond)
The digital forensic community has come a long way since the 1960’s. Starting out as a hobby made up mostly of homegrown tools and quite often insufficient processes, we have arrived at a convergence of various law enforcement, organizations, and intelligence agencies where everybody is following the same consistent principles, methodologies, and techniques.
Predicting what the future holds for digital forensics is a crapshoot. Rather, if history has taught us anything about how the past has shaped what digital forensics is today, the most realistic and accurate prediction that can be made is this: every person and/or group involved with digital forensics today will have some type of influence on what the future brings.
For the most part, digital forensics has become what it is today because of the tactical influences that have consistently driven its development and maturity, such as technology advancements, creation of commercial tools, or the integration with other professions. On the other hand, while the list of strategic influences might be somewhat smaller, the alignment to forensic science and subsequent creation of principles, methodologies, and techniques to abide by has brought about a standardization and formality to the structure of digital forensics. There are also influences that exist as both tactical and strategic realms that should be considered for the future of digital forensics, such as:
• The continued development of the common body of knowledge (CBK) based on research, knowledge, and experiences of the digital forensic community. At the end of the day, the digital forensic investigators of the future will be better trained and educated because the CBK that was established before them will be extensive and readily available. Organizations will need to ensure that they employ digital forensic professionals who are not only accredited to conduct digital forensic investigations but also have strong business and technical qualities.
• Historically, modern advancements that introduced new ways for technology to be used as either the fruit of crime3 or tool of crime4 will subsequently lead to an evolution of how digital forensics is used to investigate these crimes. Until recently, cybercrime was traditionally committed with a focus primarily on content (ie, data exfiltration) and done so with little context (ie, where attacks are being perpetrated). Naturally, Cybercriminals of the future will also be better trained, funded, and organized where the value of their collective efforts will be realized resulting in heightened situational awareness involving their attacks.
• To counter the evolving threat landscape, commercial digital forensic tools will need to evolve to where they can:
• easily adapt with the ever growing volumes of data that needs to be analyzed
• further automate known, verified, and validated analytic functions to alleviate manual processing time and reduce error probability
• understand and interpret both the content and context of human language and communications for better analytical results
• Given the fact that some investigations encompass an international scope, such as data residing under multiple jurisdictions, laws and regulations must evolve to enable a global standard for digital forensics.
Digital Forensics Overview
Since the 1960’s the threat landscape has evolved significantly from what is now considered simple cybercrimes (ie, sabotage) to much more sophisticated attacks (ie, APT). From the evolution of cybercrime, digital forensics was born from the ideas of pioneers that continued to develop and expand their interests into a now well-established and recognized profession.
What is currently known as Digital Forensics is a discipline that adheres to the forensic science discipline and has been well established as a result of an extensive CBK of proven methodologies, techniques, and principles. In other words, digital forensics is the application of science to law where scientific principles, methodologies, and/or techniques are used during a digital forensic investigation.
Why Is It Important?
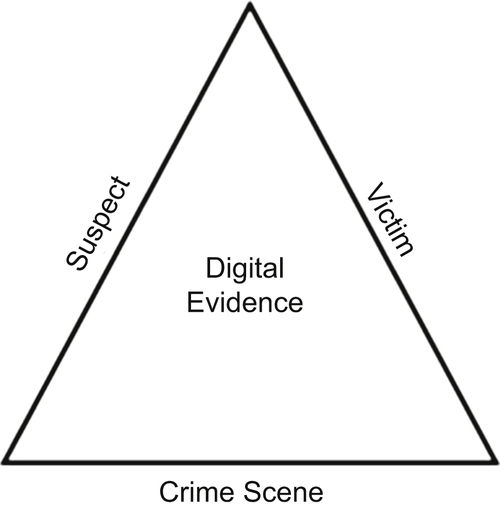
According to Locard’s exchange principle, illustrated in Figure 1.1 below, every perpetrator of a crime will bring something into the crime scene and takes something of the crime scene with them. In the digital realm, both of these occurrences can be used as digital evidence in a forensic investigation.
The capability of practicing forensically sound principles, methodologies, or techniques within any organization provides an additional “defense-in-depth” layer to ensure that potential digital evidence is (1) acquired in a manner that preserves its integrity, (2) authenticated to validate that it is identical to the original source data, and (3) analyzed using techniques and processed that maintain the evidence’s integrity.
Organizations that have a good understanding of the technical requirements for practicing digital forensics will be better equipped to gather and process digital evidence in line with the legal requirements for prosecuting intruders. But what happens when the technical and/or legal requirements for practicing digital forensics are ignored or not followed properly? The reality is, organizations that do not practice forensically sound principles, methodologies, or techniques run the risk of:
• potential digital evidence being compromised, lost, or overlooked
• digital evidence not being admissible in a court of law due to integrity and/or authenticity issues
• being noncompliant with laws and/or regulations
Legal Aspects
Even if legal prosecution is not the end-goal of the investigation, such as a corporate policy violation, there may be some form of legal action, such as employee termination. It is important that the forensic science principles, methodologies, and techniques are consistently followed because the investigation may wind up in a court of law at some point. Regardless of criminal proceedings, every digital forensic investigation must ensure that:
• an exact copy of digital data is created to ensure no information is lost or overlooked
• a chain of custody is established to maintain integrity through the evidence’s life cycle
• actions taken by people through the different investigative phases are recorded
Collecting Digital Evidence
From the traditional computer system to modern devices such as mobile phones, game consoles, or virtualized environments, the field of digital forensics encompasses a wide range of technologies that serve as potential evidence sources. While the design and functionality of these technologies is uniquely different, the application of digital forensics involves ensuring the integrity and authenticity are upheld throughout the evidence’s life cycle. Two basic types of potential digital evidence that can be gathered from these technologies include nonvolatile or volatile data.
Volatile Data
Volatile data is a type of digital information that is stored within some form of temporary medium that is lost when power is removed. This type of information is an excellent starting point for a forensic investigation because it contains residual data that may be relevant to the processing and analysis of digital evidence that is gathered from nonvolatile data sources.
The primary source of volatile data can be found inside of random access memory (RAM). Most often, the contents of RAM will contain information relating to frequently used applications, content of recently accessed files, or account information such as usernames and passwords (cleartext or hashed).
While the type of files containing potential digital evidence can be extensive, depending on the technology, examples of volatile data that are commonly included within the scope of a typical forensic investigation are as follows:
• Network configurations used by the OS are retrieved from nonvolatile data stored on the file system and loaded into RAM for quick and dynamic access, such as Internet protocol (IP) addresses and active network interfaces.
• Network connections between the local system and remote systems, in any state (ie, established, listening), listing incoming and outgoing connection properties, such as IP address and local/remote port.
• Running processes that are currently executing system commands, supporting operational services, or providing user interfaces, such as applications, scripts, or executables.
• Open files from nonvolatile data sources that are actively being accessed by either the system or a user, such as word processing documents, executables, log files.
• System date/time maintains the current date and time information, including time zone and day-light savings properties, that can be used when building a chronology of system events or when correlating the local system events to other system events. Special attention must be given to date/time values stored in a system’s Basic Input/Output System (BIOS) because it can be different than the values contained within the OS configurations.
Nonvolatile Data
Nonvolatile data is a type of digital information that is persistently stored within a file system on some form of electronic medium that is preserved in a specific state when power is removed. Contained within a file system is commonly the largest and richest source of potential digital evidence that can be analyzed during a forensic investigation. While the type of files containing potential digital evidence can be extensive, depending on the technology, examples of nonvolatile data that are commonly included within the scope of a typical forensic investigation are as follows:
• Configuration/log files are used to store various types of system or user settings as well as outputs of auditing information, such as:
• Audit records containing records of successful and failed authentication attempts within the system
• System event logs used to track the operational actions performed by OS components, such as when the system is booted
• Application events used to track the operational actions performed by application, such as when a process is executed
• Data files are used to store information for applications that can be either system-generated or user-generated, such as text files, word processing documents, spreadsheets, databases, audio files, or graphics.
• Paging/swap files are logical files located on a file system that are used by the OS, in combination within RAM, to extend the amount of temporary storage space available on a system so additional data can be dynamically available, such as usernames or password (cleartext or hashed). While the contents of these files may resemble or originate from volatile data, the page/swap file is nonvolatile and is preserved in its last operating state when power is removed.
• Dump files are used by the OS to automatically store the active contents of RAM when an error condition occurs to assist system administrator in troubleshooting. The resulting files will contain the stored RAM content that is preserved when power is removed.
• Temporary/cache files are files created by either the OS or applications during activities such as installation, upgrades, or normal operations, such as scripts, executables, or web browsing pages. Although such files can be typically deleted at the completion of these activities, this does not always occur resulting in this data being preserved in its last operating state when power is removed.
• Hibernation files are created by the OS to record the contents of RAM, running applications, and open files before the system is shut down; so the system state can be restored the next time it boots.
• Slack space is unused area in between the end of an actual file and the end of the defined storage space, also known as a cluster,7 available in a file system. When being written to a file system, depending on the volume of data, a file might not occupy the entire cluster resulting in remaining space otherwise referred to as slack space. In this space, data belonging to other files, that previous occupied the cluster but have since been overwritten by a new smaller file, are still accessible and can be recovered during a forensic investigation.
• Registry is a database, specific to the Microsoft Windows platform, which contains important information about the system including, but not limited to, hardware components, installed applications, OS configurations, and account information. While caution should be taken to not make manual changes to the registry because one wrong move can render a system inoperable, the information and potential evidence that reside in the registry make it a significant forensic resource, such as most recently used files, applications configured to automatically run at startup, network shares.
Order of Volatility
Generally, the more volatile data within a system the more challenging it is to gather in a forensically sound manner because it is only available for a specific amount of time. Considering the volatile data types listed above, this information can only be gathered from a live system that has not been rebooted or shut down since the incident originally occurred.
Therefore, it is critical that investigators are equipped with adequate knowledge of the incident to make an educated decision on whether volatile data should be preserved as part of the forensic investigation. Ideally, the criteria for making this decision should be documented in advance, as part of the organization’s standard operating procedures, so investigators can make act quickly to preserve the volatile data.
The ability to make a decision comes with the inherent risk that the longer it takes to make the decision the greater the risk that the volatile data will be lost. For instance, every action performed on the system, whether by the system or person, will most certainly alter (in some way) the current state of volatile data available to the investigator.
When deciding to preserve volatile data, it is important to keep in mind that the more volatile the data is the greater there is a need to use specialized individuals and tools to guarantee the data is preserved in a forensically sound manner. Illustrated in Table 1.1 below is the order of volatility for digital evidence, ordered from most volatile to least volatile, including its life span and relevance to the forensic investigation.
Table 1.1
| Life Span | Storage Type | Data Type |
| As short as a single clock cycle | CPU storage | Registers |
| Caches | ||
| Video | RAM | |
| Until host is shut down | System storage | RAM |
| Kernel tables | Network connections | |
| Login sessions | ||
| Running processes | ||
| Open files | ||
| Network configurations | ||
| System date/time | ||
| Until overwritten or erased | Nonvolatile data | Paging/swap files |
| Temporary/cache files | ||
| Configuration/log files | ||
| Hibernation files | ||
| Dump files | ||
| Registry | ||
| Account information | ||
| Data files | ||
| Slack space | ||
| Removable media | Floppy disks | |
| Tapes | ||
| Optical disc (read/write only) | ||
| Until physically destroyed | Optical disc (write only) | |
| Outputs | Paper printouts |

Types of Forensic Investigations
Traditionally, digital forensics is performed in response to an incident and focuses on determining the root cause for what prompted the incident. The purpose of performing a digital forensic investigation is to establish evidence and facts from digital information existing on any number of different technologies (eg, game consoles, mobile devices, computer systems), across dissimilar network architectures (eg, private, public, cloud), or in varying states (eg, volatile, static).
Since the birth of computer forensics in the 1980s, the application of forensic science has become an underlying foundation that has seen an integration of the consistent principles that support repeatable methodologies and techniques within several other information security disciplines. The application of digital forensic science in other disciplines provides organizations with an acceptable level of assurance that validated and verified processes are being followed to gather, process, and safeguard digital evidence. Examples of disciplines where digital forensic science is used include the following:
• Computer forensics which relates to the gathering and analysis of digital information as digital evidence on computer systems and electronic storage medium.
• Network forensics which relates to the monitoring and analysis of network traffic for the purposes of information gathering, gathering of digital evidence, or intrusion detection.
• Incident response which relates to reducing business impact by managing the occurrence of computer security events.
• Memory forensics which relates to the gathering and analysis of digital information as digital evidence contained within a system’s RAM.
• Electronic discovery (e-discovery) which relates to the discovery, preservation, processing, and production of electronically stored information (ESI) in support of legal or regulatory litigation matters.
• Cloud forensics which relates to the gathering and analysis of digital information as digital evidence from cloud computing systems.
As digital forensics continues to evolve alongside of technology advancements, one of the most challenging activities is to ensure that the fundamental principles, methodologies, and techniques are upheld. There is a constant struggle to maintain a balance between collecting digital evidence as efficiently as possible without modifying the integrity of the data in the process. Fortunately, the principles and methodologies of forensic science have been clearly defined and well established allowing them to be applied relatively seamlessly to any form of digital evidence.
Digital Forensic Resources
This book is written from a nontechnical, business perspective and is intended for use as an implementation guide to prepare any organization to enhance its digital forensic readiness by moving away from reacting to an incident and becoming proactive with their investigative capabilities.
While the basic principles, methodologies, and techniques of digital forensics are covered, this book focuses on outlining—in detail—the where, what, and how an organization can enhance its knowledge, processes, and technologies to implement effective and proactive digital forensic readiness.
There are countless resources available today that are designed specifically to teach different basics or specializations contained within the digital forensic discipline. The volume of reference material on digital forensic topics is beyond the intention to identify and include them as a reference in this book. While there might be some absent from the list below, the following are recent publications that can be used as a learning tool for digital forensics.
Digital Forensics with the Access Data Forensic Toolkit (FTK). McGraw-Hill Osborne Media, September 05, 2015. ISBN: 9780071845021.
Handbook of Digital Forensics of Multimedia Data and Devices. Wiley-IEEE Press, August 31, 2015. ISBN: 9781118640500.
Hacking Exposed Computer Forensics Third Edition: Secrets & Solutions. McGraw-Hill Osborne Media, July 06, 2015. ISBN: 978-0071817745.
Operating System Forensics 1st Edition. Syngress, July 01, 2015. ISBN: 9780128019498.
Cybercrime and Digital Forensics: An Introduction. Routledge, February 12, 2015. ISBN: 978-1138021303.
The Basics of Digital Forensics 2nd Edition. Syngress, December 15, 2014. ISBN: 9780128016350.
Computer Forensics and Digital Investigation with EnCase Forensic v7. McGraw-Hill Osborne Media, May 28, 2014. ISBN: 978-0071807913.
Windows Forensic Analysis Toolkit 4th Edition: Advanced Analysis Techniques for Windows 8. Syngress, April 10, 2014. ISBN: 9780124171572.
Computer Incident Response and Forensics Team Management 1st Edition. Syngress, November 22, 2013. ISBN: 9781597499965.
Digital Forensics Processing and Procedures 1st Edition. Syngress, September 17, 2013. ISBN: 9781597497428.
Computer Forensics InfoSec Pro Guide. McGraw-Hill Osborne Media, April 09, 2013. ASIN: B00BPO7AP8.
Malware Forensics Field Guide for Windows Systems 1st Edition. Syngress, June 13, 2012. ISBN: 9781597494724.
Digital Forensics with Open Source Tools. Syngress, April 14, 2011. ISBN: 9781597495868.
Handbook of Digital Forensics and Investigation. Academic Press, October 26, 2009. ISBN: 978-0123742674.
Summary
The rise and continued evolution of cybercrime has made a significant contribution to the formation of what digital forensic science is today. Growing out from the pastime of hobbyists, the establishment of forensically sound principles, methodologies, and techniques has turned it into a respected and authoritative discipline.