Appendix D: Service Catalog
Introduction
Information security controls can be either administrative, technical, and physical in implementation. For every security control that exists within the organization, it must deliver value in support of business functions throughout the organization. Unfortunately, with the inner workings of information security typically not made common knowledge, the business value being delivered and the role it plays in achieving successful business outcomes is not usually recognized. This leaves the overall information security program vulnerable to not be seen as strategically relevant to the organization’s business functions. To be successful in demonstrating value, information security needs to be strategically aligned to business functions and positioned as an empowering contributor to the organizations success.
As part of the overall service management life cycle, a service portfolio is the entire set of services1 managed and offered by the provider. The service catalog, also referred to as an information technology (IT) service catalog, is a subset of the service portfolio that acts as a centralized register and entry point for details about the organization’s available services. Through the creation of a service catalog, the value of information security can be demonstrated more effectively by aligning the delivered outcomes to business functions in a format that is easily understood.
Business Benefits
At a minimum, a service catalog provides organizations with a centralized way to see, find, invoke, and execute services regardless of where the service exists within the organizational. Organizations utilize a service catalog to eliminate the need for developing or supporting localized implementations that may be otherwise redundant.
Implementing a service catalog demonstrates a positive return on investment (ROI)2 back to the organization in the form of direct financial savings or through maximizing effectiveness and efficiencies. From the strategic alignment of information security to business functions, organization can realize the ROI through the following positive effects of a service catalog:
• Provides a platform to better understanding and communicate business requirements
• Positions the overall information security program to be run like a business
• Reduces operational costs by identifying essential services and either eliminating or consolidating both redundant or unnecessary services
• Enhances operational efficiencies through the strategic structuring of resources and funding
• Helps market the awareness and visibility of the information security program to build stronger business relationships
Inevitably, if a service catalog does not already exist, somebody within the organization will understand the benefits of having it in place and what it provides in terms of visibility to the information security program. Once identified, creating a service catalog should not be viewed as a straight forward task. By taking a laid back approach to creating a service catalog, the organization may not realize the true ROI and will most likely be wasting resources, time, effort, and money. Guidance and oversight should be in place right from the start of creating the service catalog to make sure the organization properly utilizes its assets throughout the entire process.
Design Considerations
The creation of services that deliver business value will differ from one organization to the next. Before starting the work of defining services, every organization should consider including the four consistent elements to support the service in delivering value:
• People—Human resources and organizations structure(s)
• Processes—Service management documentation
• Products—Technology and infrastructure
• Partners—Dependencies on external entities
Service catalogs include descriptive elements so that users within the organization can easily find and request the desired service. There are no predefined requirements indicating what specific elements must be included in a service catalog; leaving the decision to include or exclude elements entirely up to the subjectivity of the organization. The most common descriptive elements that organizations should use in any service catalog implementation include the following.
Service Name
The service name should clearly illustrate, in both business and IT terminology, how the service is commonly referred to throughout the organization. Structuring the name in such a way eliminates any confusion that may exist about the service.
Service Description
The description should be written at a very high level, with no more than two to three lines, in a nontechnical, business language that is simple and easy to understand.
Service Family/Group/Category
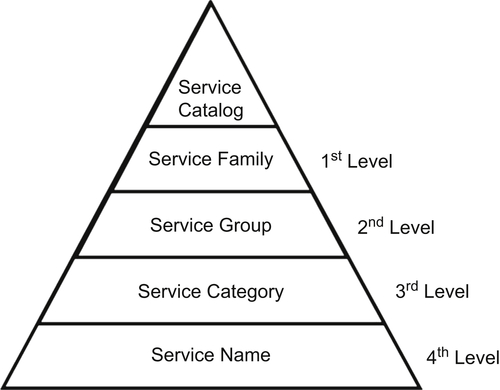
Illustrated in Figure D.1, the hierarchical use of families, groups, and categories allows for individual services to be classified and aligned into the organization’s common areas of functionality. The purpose of classifying individual services into the larger areas is to simplify resource management and cost analysis.
Service Family
In the first level of the service catalog hierarchy, the purpose of a service family is to translate services into core business driven functions; such as IT services or business services.
Service Group
In the second level of the service catalog hierarchy, the purpose of a service group is to expand the individual business functions contained within the service family, such as security services or compliance.
Service Category
In the third level of the service catalog hierarchy, the purpose of a service category is to specify the individual service functions, such as security operations or investigations.
Service Owner
The owner is the person within the organization who provides funding for the service; commonly assigned to the executive management person where the service is offered.
Key Contact(s)
The key contact(s) of the service are those within the organization who functions as the focal point for all communications between IT departments and the business communities. These individuals are responsible for understanding and supporting the level of service being delivered in line with established service level objectives.3
Service Costs
Documenting all services as quantifiable provides organizations with a better understand where funding is allocated across the total cost for operating the service. Having identified all of the contributors to the total service cost, organizations can then implement a chargeback model for performing cost allocations based on the services activities costs.
Cost Elements
The fixed (eg, software licensing, capital) and variable (eg, remuneration, outside data processing) costs associated with operating the service.
Cost Driver
The specific fixed (eg, software licenses) or variable (eg, billable work hours) unit(s) of service activity that results in a change in cost to the requestor.
Cost Per Unit
The measurement used to identify the cost of delivering one unit of service activity.
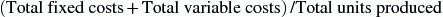
Cost Allocation
The distribution of service costs through the organization to areas that consume the service activities.
A service catalog template has been provided as a reference in the Templates section of this book.
Summary
Every administrative, technical, and physical security control contributes to an organization’s overall service offering. With Information Security service offerings mostly being considered as overhead to an organization, it is important that associated resources and technologies are identified so that cost elements can be allocated appropriately.