
Jihadi Cyber Warfare Units
The Internet is populated with plenty of individuals and groups who may know its tools better than the average user. Some of these tools are highly sought after by criminal and terrorist organizations worldwide. ISIS and al-Qaeda have long sought and used skilled individuals to exploit those recruits who have experience and determination to use the Internet’s information systems and tools to their advantage. These groups have learned how to weaponize the Internet’s social media networks and have effectively spread terror as they employed horrific images in their propaganda, thereby earning them a reputation of being a bloodthirsty, savage death cult. But their hackers are at best a nuisance; they lack the coordination of state actor organizations like the Cyber Bears of Russia, the Pandas of China, or the Kittens of Iran. This doesn’t mean they should be taken lightly, though.
The reason for the sophistication of many jihadists has less to do with genius than intent. In examining the nearly one hundred cases in the United States and dozens of cases in Europe, we clearly saw that ISIS fanboys and operatives alike often make huge mistakes as they navigate their way to and from Syria or plan a local operation. Many of these unforced errors can and will occur in their use of the Internet or other communication devices.
To determine how to defend against their efforts, it helps to identify the groups and individuals who comprise the ISIS cyber media force. Each group’s efforts require unique examination of their objectives, resources, and threat capability. Each group may have overlapping members in various roles as ISIS picks from the total skill base of fighters and then exploits their skills wherever it sees fit.
While many of these roles can be filled by overlapping personnel, it is clear there are people who function solely to publish information on phone security and communications. There are operatives who focus mostly on setting up Twitter or Facebook pages. These intermediaries perform the function of keeping communications flowing around the caliphate.
The Horizon channel (aka the Afaaq Electronic Foundation) on Telegram frequently posts the latest information on secure communications. Launching their Telegram channel in January 2016, the group frequently posts up-to-the-minute, timely suggestions on phone hardware and suggested apps for communication and encryption.
THE ONLINE JIHADI GROUPS
There were several hacking teams under ISIS who engaged in defacements and DOS attacks. These groups sprung from existing hacker communities, including the famous hacker group Anonymous. Equipped with a desire to create chaos and fear, these groups mostly swapped home pages with ISIS banners and slogans. This “capture-the-flag”-style campaign was common until the groups turned to publishing “kill lists” drawn from already available information or lists stolen by other hackers who had real skills to do so.
Launched as a pro-Palestinian effort, AnonGhost became one of the members in the loose affiliations that comprise the ISIS hacker groups. AnonGhost detached from Anonymous after the #OpISIS campaign that followed the Charlie Hebdo attacks in Paris in January 2015. The Anonymous campaign vowed to knock down all ISIS content from the web regardless of Twitter, Facebook, or stand-alone websites.
AnonGhost was founded by a hacker named “Mauritania Attacker”1 as an offshoot of a cyber group called “Teamr00t.” Teamr00t was focused on pro-Palestinian/anti-Israel hacking campaigns, according to a Twitter channel associated with the group that was active between June 2012 and December 12, 2012.2 After years of inactivity, another channel for Teamr00t emerged in January 2016. Teamr00t was responsible for approximately 163 attacks, of which 141 were defacing attacks.

Figure 23: Flyer circulated by AnonGhost before the #OpPetrol attacks in 2013.
The hacker known as “Mauritania Attacker” claimed that virus maker Farid Essabar of Morocco, a.k.a. “Diablo,” virus writer behind the Zotob worm in 2005, was the one and only hacker he admired. His alleged identity was “Moulaye Ahmed Ould Ahmed Semane” from Nouakchot, Mauritania, according to a rival group known as the Ghost Squad Hackers.3
In April 2013, AnonGhost launched attacks as part of the campaign “OpIsrael,” which aimed to strike Israeli-affiliated sites with Distributed Denial of Service (DDoS) and defacing website attacks. Its other campaigns included “#OpUSA” and “#OpPetrol.” The OpUSA came with an official video for the campaign on YouTube and resulted in hundreds of sites being defaced. Despite the hassle, though, no serious breaches occurred. The announcement of #OpPetrol threatened attacks on 12 countries by both Anonymous and AnonGhost. Like the previous operation, an official video of the campaign was published. The 3:20 video threatened that the multinational effort would begin on June 20, 2013. Later in November of 2013, AnonGhost claims attacks against Total, the oil company. As proof of the hack, the group released emails and passwords of company employees to a pastebin.com url.4
According to posts on a Cyber Caliphate Army’s Telegram channel, AnonGhost merged with CCA in January 2016.5 This was later disputed in another post by members who objected. The resulting split in the group resulted in two groups, the Ghost Caliphate who went with CCA and the Ghost Squad Hackers.
A group of hackers who used to be aligned with AnonGhost went in another direction when members like Mauritania Attacker expressed their support for ISIS. As mentioned previously, this group, known as Ghost Squad Hackers, GSH, was a pro-Palestinian hacking group led by its founder who went by “s1ege,” which is hacker dialect for “siege.” After the split with AnonGhost, Ghost Squad members started outing AnonGhost members, including the leader, Mauritania Attacker.6 But by the end of August 2016, according to both of their twitter channels, the two groups had made peace and were once again focused on attacking Israeli cyber targets.
According to an interview with “Sec4Track,” the members are international and live in Mauritania, Morocco, Malaysia, Indonesia, Tunisia, US, and Ireland, to name a few:7
The founder and administrator was “Mauritania” Attacker.” Other members’ cyber street names are “Virusa Worm”—“SpitFir3”—“ManSyk3z”—“Deto Beiber”—“BL4ckc0d1n6”—“Dr. SaM!M_008”—“Sky Lion”—“Kais Patron”—“Ian Surgent”—“B0o3nAs”—“ Gbs Aremiey”—Mr Domoz”—“RetnOHack”—“Tak Dikenal”—“Chahid inj3ctor”—“b3ta”—“Rehber Khan”—“AnonxoxTN”—“Spec Tre”—“PsyferR”—“Raka 3r00t”—“Gh0st_3xp10!t”—“PirateX”—“Kopra1337”—“Bl4ck jorozz”—“Riad Spamer”—‘VirUs AsEr AlrOoh”—“Younes Lmaghribi”—“Zaky”—“joker inside”—“AreTheIS.”

Figure 24: CCA Mask Gazwa Reloaded Graphic. (Source: TAPSTRI)
Cyber Caliphate Army—#cybercaliphate
The name perhaps most associated with ISIS hacking groups was the Cyber Caliphate Army, which was led by hacker Junaid Hussain until his death in August 2015. After years of his work with TeaMpOisoN, Junaid Hussain took his hacking experience and joined ISIS. He had served time for hacking into Tony Blair’s emails through his advisor’s account. Once he had reached Syria, he started to recruit both hackers and fighters alike. He had built up an extensive set of hacker contacts before establishing CCA, but his extreme views and joining ISIS guaranteed that many of his former hacker friends weren’t going to join him in his new pursuits.

Figure 25: Cyber Caliphate Army members published on a page that was hijacked. (Source: TAPSTRI)
After Junaid’s death, he was reportedly replaced by a Bangladeshi web developer named Siful Haque Sujan. Sujan inherited Hussain’s role after his death but didn’t hold it for long. By December 10, 2015, Sujan was killed in Raqqa, like his predecessor.
CCA Cyber Caliphate Army—Decentralized in 2016

Figure 28: CCA Abu Hussain Graphic. (Source: TAPSTRI)
The group divided into four divisions, according to CCA postings.
CCA was known for its defacing attacks. There are members named by the group as “Eng Caliphate,” “Dr. Caliphate,” “Cyber Caliphate,” “Lion Caliphate,” “Damar Caliphate,” and “Ghost Caliphate.”

Figure 26: Ghost Caliphate Graphic. (Source: TAPSTRI)
Ghost Caliphate Section
According the members of the Ghost Security Hackers (GSH) group, Ghost Caliphate members are former AnonGhost members who chose to join ISIS. Though the GSH initially rebelled against CCA, a peace agreement was reached months later.
Sons Caliphate Army (SCA)

Figure 27: SCA Graphic. (Source: TAPSTRI)
This subgroup to the Cyber Caliphate Army was first mentioned in a post by CCA in January 2016. The group released a video called “Flames of Ansar,” which claimed credit for hackings on Facebook and Twitter accounts. They also threatened the founders of these companies, Mark Zuckerberg and Jack Dorsey, if they didn’t stop removing ISIS accounts from their systems.
Kalachnikov E-Security Team (KTN)

Figure 29: Kalachnikov E-Security Team Graphic. (Source: TAPSTRI)
This group’s efforts are focused mainly on tech security advisory posts on Telegram. However, they have conducted or assisted in defacing hacks. The group shares overlapping members with the Cyber TeamRox group. The CTR group launched a Telegram page on March 3, 2016, and renamed it Kalachnikov E-Security Team on March 16, 2016. They later affirmed the connection by denying ties to a Telegram channel and reminding users that “We only have this channel here and the kalachnikov one” in a post on their Facebook page.
Identified members: f@ng, Zeehaxor, AlW4S, Adarius, Dr Avatar.
CCA Telegram Information
In the period between the relaunch of a CCA telegram channel on July 16, 2016, and August 23, 2016, 812 members had joined a channel. This number doesn’t distinguish between CCA members, intel organizations, fanboys, or curious bystanders. It is possible there are only a handful of CCA members and 700 to 810 watchers and fanboys, many of whom are also researchers’ intelligence community onlookers.8
First, the channel was delivered almost entirely in English with occasional bits of Arabic. The channel’s profile page has “
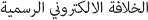 CCA” or the “Official Channel of the Electronic Caliphate Army CCA” on Description and an icon set of a hooded figure against a coded background. “Caliphate Cyber Army-Information not available-location/Unknown” is written in English again instead of in Arabic.
CCA” or the “Official Channel of the Electronic Caliphate Army CCA” on Description and an icon set of a hooded figure against a coded background. “Caliphate Cyber Army-Information not available-location/Unknown” is written in English again instead of in Arabic.
CCA frequently reposts from the United Cyber Caliphate, its self-claimed umbrella affiliation group established in April 2016. They also send out links to Telegram affiliates that often expire within just a few hours, some in a matter of minutes. If you don’t join those channels before the moderator closes the group, you’ll miss out and have to watch for another invite.
CCA’s channel frequently posts variations of imagery derived from several video-style graphic arts packages ranging from overtones of the game Halo to variations on the balaclava image à la Jihadi John, a.k.a. Mohammed Emwazi, the British executioner from the ISIS videos. They use these styles to trumpet their four core groups, “GHOST,” “CCA,” “SCA,” and “KNT.”
“Ghost” appears to be made up of AnonGhost people who went over to ISIS. SCA, the Sons of Caliphate Army, is known for its twenty-five-minute video aimed at Mark Zuckerberg and Jack Dorsey, Flames of Ansar, in which it claims to have compromised the content of 10,000 Facebook accounts and over 5,000 Twitter channels. The video was the first threat of this level against social media companies in response to their crackdown on militant profiles and postings. Twitter’s position on the matter was summed up by its spokesman: “We condemn the use of Twitter to promote terrorism.”9
One of those campaigns stamped July 16, 2016, was labeled “‘Central Military District’—russia hacked,” accompanied by a graphic of an ISIS fighter from Russia who was previously featured in an execution video from Raqqa called You will be disappointed and humiliated, oh Russians! CCA claims to have hacked a Russian Army base database in Arabic first, then English, and then Russian and under the banner of “united cyber caliphate” (all lower case) and without relinking from the UCC Telegram channel as they do in other examples. The file was released in “kmz” format. Following that post, CCA released another kmz file with information on “American civilian and military” claiming to be lifted from US military databases.
CCA posted “#Wanted to be killed Massachusetts #US” along with a young man with an ISIS flag in front of the White House with the bottom caption “The End Is Near Soon” in English. In another post, CCA said the next target listed in the campaign was “Government employees data Rhode Island #USA.”
CCA was challenged on whether their data releases were previously stolen by others or a result of combing publicly available information, even if you had to look it up with a bit of effort. They reacted in one Telegram graphic written in English, “they are lying when they tell you ‘The DATA are all #public’ and ‘No-Your systems failed to hide it and that is the true [sic]’”. Yet the data released in some cases were clearly obtained by others.10
But there is something of a clownish aspect to many of these groups when you watch them long enough. An example of this is their meme mockery of the deployment of the Charles de Gaulle aircraft carrier by putting a stuffed cow on the deck and again in English, “Charles de Gaulle-Cows carrior,” and in very small print “UCC media.”
If you forget they are serious about at least terrorizing people, they post graphics of attack metrics or graphics that show methods of killing, including icons for “Remmed [sic] them,” “stab them,” “shoot them,” “throw them” with a picture of a pile of stones, “intoxicate them,” “hit them” with a pic of a stick, and, strangely, “SCREEM [sic] THEM” with an icon of two people with lines indicating yelling from one to the other. The “Remmed them” graphic was circled in one because of the Nice, France, killing on July 14, 2016. As the other graphics passed, they used the same overall imagery but light up each icon as events transpired, almost as if they comprised a checklist of methods. The footer of the graphic stated, “Instructions to individual wolves-Kill them” and specifically tagged by the Cyber Caliphate. The post itself with the graphic stated, “Mission has been completed waiting #next and #UCC.”
The “Gazwa” campaign was launched with the “We Will Kill You All” banner and “We are watching you, our ideas are sophisticated. Our systems you cannot under estimate. Islamic state wins.” CCA seeks often to project abilities beyond its cannon of self-credited attacks. In their graphics and videos, they also seek to convey proof of their competence, which begs the question, how competent are they ultimately? If Junaid Hussain’s first claim to fame was to hack the email of Tony Blair, it’s an accomplishment that falls far below the expectations of even the finest hackers.
Despite the tremendous brutality of their campaign videos and the quality of their social media campaign, their hacking skills leave much to be desired in a Grade A terrorist organization. Consider, for instance, that they couldn’t seem to hack Google but did get “earned media” that published their names anyway because they did successfully hack a company’s site that used Google in the name, AddGoogleOnline.com.11
In August of 2016, a man identified as Othman Zebn Nayef was arrested by Kuwaiti authorities on suspicion of working with ISIS. Once arrested, he confessed to working with CCA. Authorities said they also captured other suspects related to a case in Iraq and Jordan but did not specify their relationship with Nayef.12
Most of what has been learned about CCA’s operation comes from their overall postings, graphic messages, efficacy of attacks, depth of attacks, and their demeanor while conducting these operations in a semipublic manner. The group continues posting threats and self-aggrandizing graphics, all designed to encourage its members to wreak havoc on the kufar.

Figure 30: United Cyber Caliphate Graphic. (Source: TAPSTRI)
UNITED CYBER CALIPHATE (UCC)—UNITED APRIL 2016
In March 2016, the groups associated with CCA announced that they would be uniting under the new banner, The United Cyber Caliphate. The group was comprised of “Cyber Caliphate Army,” “Ghost Caliphate Section,” “Sons of Caliphate Army,”and “Kalachnikov E-Security.”
UCC has been claiming data releases since naming itself on April 5, 2016. Each of these data dumps was usually accompanied by a demand of lone wolf attacks on the targets listed. On April 10, 2016, UCC defaced sites as part of its #KillCrusaders campaign. The countries affected by these attacks were the US, Chile, China, France, Malaysia, and Mexico. On April 18, 2016, the group launched its “#Gazwa: Reloaded,” which claims to have released information on ten thousand personal accounts in a breach. A few days later, on April 21, 2016, the group released a list of names of people in New York with “We Want Them Dead” as its banner. On April 24, 2016, the group released a list of names from US State Department staff with “Wanted to be killed” as its banner. Later, on June 7, 2016, the group released another “Kill List” with 8,318 names from 21 countries. The post indicated the list of people should be killed as “revenge for Muslims.” Then again on June 21, 2016, they repeated the effort with a list of names from the United States, Canada, Australia, UK, and others. This “kill list” contained 4,681 names.

Figure 31: United Cyber Caliphate Telegram graphic. (Source: TAPSTRI)

Figure 32: United Cyber Caliphate Gazwa Reloaded Telegram Graphic.
Islamic State Hacking Division (ISHD)
The Islamic State Hacking Division started its operations in early 2015 under the leadership of CCA leader Junaid Hussain. Like CCA, their attacks are mainly defacing or DDoS attacks. They were largely active between March 2015 and August 2015 and then went dormant after the death by airstrike of their leader, Junaid Hussain, in August 2015. The only hack attributed after that date came in May 2016 with a leak post aimed at 76 drone operators.
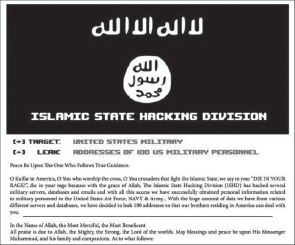
Figure 33: ISHD hacking screenshot. (Source: TAPSTRI)
March 23, 2015: ISHD releases names of 100 military personnel.
April 13, 2015: ISHD attacks and defaces two bios on Huffington Post.
April 15, 2015: ISHD hacks an Egyptian radio station Nogoum FM’s Twitter account and uses it to post ProISIS messages.
June 1, 2015: ISHD hacks Italian military servers.
August 11, 2015: ISHD releases a list of 1,500 US military and government workers. The list originated with Kosovo hacker Ardi Ferizi, a.k.a. “The3Dir3ctory,” who was later charged with stealing the data in October 2015.
September 11, 2015: ISHD releases a “Kill list” of 100 American military personnel on a JustPasteIt post. The posts included photos, names, addresses, and service branches.
May 2, 2016: ISHD releases a list with the names of 76 drone operators.13 After the leak was released, the group proclaimed under the ISHD tag:
Peace be Upon The One Who Follows True Guidance
O Crusaders, as you continue your aggression towards the Islamic State and your bombing campaign against the Muslims, know that we are in your emails and computer systems, watching and recording your every move, we have your names and addresses, we are in your emails and social media accounts, we are extracting confidential data and passing on your personal information to the soldiers of the Khalifah, who soon, with the permission of Allah, will strike at your necks in your own lands! So wait; we too are waiting.
-Islamic State Hacking Division

Figure 34: ICA members graphic. (Source: TAPSTRI)
Islamic Cyber Army—#IslamicCyberArmy
Started in September 10, 2015, ICA was part of a series of fall campaigns of cyberattacks starting with #AmericaUnderHacks. At the opening of the campaign, ICA released a video titled We Are Back In America. The group launched attacks up to late November 2015 under a series of hashtags ending with “underhacks.” The hashtags were filed under #AmericaUnderHacks, #SaudiUnderHacks, #RussiaUnderHacks, #IsraelUnderHacks, #FranceUnderHacks, and #IranUnderHacks. By November, the group moved to its final hashtag, #WorldUnderAttacks.
The names of the hackers were announced in the September video with a listing of nine members. The members included “Syria Virus,” the leader of the group; “Hcer Arkani” (identified as a member of the Kalachnikov team); “Abo 7OZYFA”; “Abu al-Qasam”; “Cyber,” sometimes listed as Ciber and may have joined CCA; “Hacker Alomar,” also known as “HaCKeR AldMaR” and who appears to have joined the Rabitat al-Ansar group; “ENG ISIS,” who later joined CCA; “DR ISIS,” who later joined CCA; and “SKWO 808.”
Rabitat al-Ansar (Union of Supporters)
Previously, Rabitat al-Ansar was known for its work with “The Media Front for Support to the Islamic State,” which included a batch of other ISIS media groups including al-Battar, al-Ghuraba, al-Wafa, al-Minhaj, and others. In this capacity, the group predominantly included reposting media releases for the Islamic State.
They claimed to have turned to hacking in 2015 after being focused on propaganda campaigns including hashtag campaigns. They were part of the #WeWillBurnUSAgain campaign starting April 8, 2015, which was announced days earlier. They were part of the #CalamityWillBefallUS campaign starting June 25, 2014. On June 25, 2014, it was the “Warning the American people” tag, and on August 22, 2014, the group chimed in with #StevensHeadinObamasHands as the world waited to hear what would happen to the American captive.
April 10, 2015: The group posts claims of data hack on 2000+ Americans, Canadians, and others on JustPasteIt. (The info had already been breached elsewhere.)14
May 11, 2015: Rabitat al-Ansar posts link to video on Twitter called Message to America: from the Earth to the Digital World. The video threatens to hit the United States with cyber war.15
July 13, 2015: Hacker Aldmar, a division of the Rabitat group, claimed to be involved in the American Visa and Master Card data breaches in July 2015.16
September 4, 2015: Hacker Aldmar issued threat to attack banks and US government on September 11, 2015. “Hacker Aldmar” was specifically named in an FBI warning to banks.
Cyber TeamRox
CTR is a group of pro-ISIS hackers who are very active at website defacings and claimed data breaches. For instance, on March 11, 2016, the group listed information on the employees of LaSalle and Purdue Universities. This group appears to have spring out of the Kalachnikov team under the CCA banner. On March 2016, the CTR group launched their Telegram feed then a few weeks later changed the page’s name to “Kalachnikov E-Security Team.”
Figure 35: Hacked by Cyber TeamRox. (Source: TAPSTRI)
The CTR hacking group was led by “Zeeshan Ali,” a.k.a. “Zeeshan Haxor,” and members have overlapped from other groups. Known mostly for defacing websites, CTR’s members are “K3L0TEX,” “Zeeshan Haxor,” “Harith101,” “D@rkCoder,” “MrGhost,” “Ctr_Def4c3r,” “Phr34ky Dump,” “CrYpt0,” “Kara dzx,” “Clinkz48,” “Aisoulu,” “ph4nt0m,” “M1S74KE,” and “Dr. Neox (Achraf).”
Examination of the ISIS Cyber Attacks
In light of the skill sets demonstrated by hackers for the Islamic State including those of its former leader, Junaid Hussain, a review of the hacks by the various pro-ISIS hacker groups yields a narrow range of methods used and shows a lack of coordination of any master strategy and likely lacks a qualified leader who is well placed in the ISIS military command structure. A list of their attacks from the early days of their operations shows an interest in defacing websites and replacing them with banners praising the Islamic State. This effort would likely only benefit the aims of the propaganda wing of the organization. As the groups moved toward the formation of the United Cyber Caliphate, the emphasis shifted to announcing data breaches around the world in order to instill fear of targeted attacks. “We Want Them Dead” or “Wanted To Be Killed” was often tagged on the releases. Similar to the defacings, this strategy is a propaganda-based strategy.
AnonGhost Hacks
This group is most commonly known for defacing websites. By examining a range of attacks from 2014 to 2016, one can see that AnonGhost predominantly engages in posting propaganda pages that replace the site owner’s home page. Targets have included Duke University, Sky News, subdomains of the U.S. Air Force, a Turkish government site, and hundreds of private enterprise sites. In November 2014, the group claimed to have hacked over 100 government sites.
After the attacks in Paris on the Charlie Hebdo offices in January 2015, AnonGhost launched attacks on hundreds of French websites. The French government confirmed that hundreds of websites had been coming under attack with defacings. The hackers dubbed the action “Operation France.”
Islamic State Hackers Division (ISHD) Hacks
March 23, 2015-September 2015: The Islamic State Hackers Division is credited with a handful of notable data dumps, starting in early 2015 with the claimed leak of the names of one hundred military personnel. Later in August of 2015, ISHD also put out a list it claimed leaked the personal information of 1,500 U.S. service members and government workers. A month later on the fourteenth anniversary of the September 11 attacks, ISHD released a list of one hundred U.S. military personnel on a JustPaste post with their names, addresses, branches of service, and photos. They then announced the post on Twitter.
The group claimed to be behind the data breach of ten Italian army personnel in June 2015.
After a period of silence of nearly a year, the group reappeared on May 2, 2016, with the previously cited post claiming to identify 76 drone operators for the US military. Additionally, the group has engaged in a few attacks that vary from the data breaches including defacing bios at Huffington Post in April 2015 to seizing the Twitter account of an Egyptian Radio station a few days later.
May 2, 2016: ISHD releases a list with the names of 76 drone operators.
Islamic Cyber Army (ICA) Hacks—active September 9–November 24, 2015
The ICA group engaged in operations that included defacings and data dumps. Working in a brief window of just over three months, the group performed many of its ops under a variation of #underhacks headers. They began by defacing British websites and threats to release private information from the breaches on September 11, 2015. The same day, they claimed to have information on FBI employees and NASA to make public. At the same time, they were committing defacing attacks under #AmericaUnderHacks and threatening to release information on military members.
The ICA group shifted its attention to Britain later in September 2015, with threats to release information on Army personnel, and engaged in more defacings. They ended the month with threats aimed at Saudi Arabia with a campaign announced to hack the royal kingdom under #SaudiUnderHacks.
In October 2015, ICA turned its sites on Russia, Israel, and France. In each case, there were more defacements and threats of releasing information, each time stepping up the call for lone wolf attacks on names released. On October 14, 2015, the group released a list purported to contain members of Israel’s Mossad.
In the final month of its appearance on the cyber stage, ICA focused its aims on Iran and defaced sites in early November 2015 along with threats of releasing information on government personnel under the hashtag #IranUnderHacks. They finished out November 2015 with a campaign under #WorldUnderAttacks, which included releasing a list of over 270,000 Twitter account details, French government personnel data, and a list claiming to be made up of United States DOD, FBI, CIA, and NSA officials.

Figure 36: CyberCaliphate JesuISIS graphic. (Source: TAPSTRI)
Cyber Caliphate Army (CCA) Hacks
Like its colleague groups, CCA has engaged in site defacings and data dumps, which are used to terrorize citizens, government personnel, and military members. Beginning in December 2014 and again in January 2015, CCA hit the scene seizing control of the website of the Albuquerque Journal newspaper and its social media page. They did the same to WBOC NewsPlex’s twitter page January 2015. But it really got attention on January 12, 2015, when the United States military’s CENTCOM Twitter and YouTube sites were replaced with the CyberCaliphate banner and icon.
The group frequently makes lofty claims about penetrating the systems of the United States government. In January 2015, CCA announced that it had breached an FBI database and stolen documents. No evidence was released to support the claim. Again in November 2015, it released 36 names it claimed were US Military. It did the same thing again days later on December 11, 2015, releasing 160 names. It claimed that there were seven hundred more to come. On December 17, 2015, the group claimed to have hacked the U.S. National Guard, Andrews Air Force Base, and NASA. In January 2016 came a list of supposed U.S. Air Force names. On June 14, 2016, came two posts with lists of DOD and U.S. Air Force names with a call for lone wolf attacks. In December 2015, the group targeted US Senator Harry Reid’s associates with calls for lone wolf attacks.
Non-US targets of the group have included data releases aimed at France, Russia, Israel, Saudi Arabia, India, and Bangladesh. Defacing of websites around the world have included targets in Saudi Arabia, Russia, Iran, India, France, UK, Spain, and Greece.
United Cyber Caliphate (UCC) Hacks
After April 4, 2016, when four groups merged to form the United Cyber Caliphate, there was a series of website defacings and data breaches claimed by the new combined group. Starting with sites defaced in the United States, China, Chile, France, Malaysia, and Mexico under the tag #KillCrusaders, UCC became a very active group that stepped up the operations by coordinating the efforts of the existing four cells.
The group largely publishes data claimed to be material for “Kill Lists” and has focused on several US government agencies including US military personnel and the US State Department. UCC has also aimed its sights at US regional law enforcement and private citizens as it did on April 21, 2016, when it released the 3,600 names of New York citizens with “We Want Them Dead” attached.
They released three large data dumps in April and June of 2016 with a total of more than twenty-two thousand names from around the world. The names were released with instructions by the group to engage in lone wolf attacks on the individuals listed as “revenge for Muslims.”
Outside of the United States, the targets have included 19 Australian websites on April 14, 2016, and the Saudi Ministry of Defense on April 22, 2016, claiming they would release information on over eighteen thousand employees. In June 2016, they defaced sites in Brazil and India. The same month they focused their sites on Canada with data dumps released as “Kill Lists.” In July 2016, they claimed they would leak the information on twenty thousand Suez Canal personnel.
In addition to citizen and government or military personnel releases, UCC has released satellite images of U.S. air force bases with emphasis that the bases are “used by the US military.” The Google earth graphics were posted to their Telegram channel in July of 2016.
There are two types of activities these groups mainly engage in—defacings and data dumps. There is little posted by the groups themselves or others on how they are acquiring their data, yet we do know they engage in passing on data already breached by others from the case of the Kosovar hacker Ardit Ferizi, member of the Kosova Hacker’s Security Group, who was arrested and sentenced to 20 years in September 2016. Ferizi gave data that had been stolen by other sources to the hacker Junaid Hussain, who in turn published the data as an original hack. Hussain posted on August 11, 2015, that he had US military and government names in a 30-page document.
One researcher on the topic examined the data dumps and concluded that many records were the result of copycat dumps. Troy Hunt runs the website “Have I been pwned?” or HIBP, which is described as a free source to investigate if you’ve been the victim of a breach. He assessed the data presented in several of the ISIS data dumps and concluded that it came from multiple locations and that it was not likely that the information came from a lone breach. He concluded that many records were culled into another database system, which resulted in inconsistent data structures and both duplicate and altered records.17
RUSSIAN HACKERS: THE TWO FALSE FLAGS
One of the most infamous attacks attributed to the Cyber Caliphate occurred on April 8, 2015, when the French television station TV5 Monde found that its website had been hacked by the dreaded Islamic State. A new graphic posted with the phrase “Je suIS IS” had replaced its Twitter page, as had been done in the CENTCOM attacks. However, this attack was going to be far worse than a simple defacing. Hackers were able to get into the station’s internal networks and began shutting down the digital broadcast system. The staff indicated that all the systems began to collapse in a very organized manner. This included the station’s admin systems and emails. They were dead in the water for three hours just after 10:00 p.m.
For days there was increasing media speculation about the ability of the Islamic State to seize a television station, which, for many news program anchors, was a reason to treat the event as terrorism itself. Yet, it turns out that event wasn’t exactly as it was being presented or even received. Further examination of the malware used to damage the system had left a trail for forensic firms to flush out the nature of the attack, and this one left bear marks. Months after the attack on the station, several firms concluded the attack had all the signs of a Russian operation.
Similarly, months before this attack, the Warsaw Stock Exchange in Poland had come under fire with a seizure of credentials for brokers in the exchange. In that case, the victims at first believed that the threat came from the Islamic State in retaliation for Polish troops in the coalition attacking the terrorist group. The dump of data on Pastbin said that CCA had hacked the economic institution.18
In both cases, the footprints on the digital trail indicated these were not jihadist tracks but those of the Russian hackers associated with the malware known as APT28. Advanced Persistent Threats or APT is a term given to malware found to have been made with the intent of being a determined, well-organized, and developed and intentional goal. In this case, the APT28 is associated with Russian intelligence and has been found in a series of attacks around the world including attacks on Russian adversaries in Ukraine, Georgia, and the United States. In the summer of 2016, the use of APTs came to highlight because of a breach of the Democratic National Committee’s data.
The evidence used to link the malware in the TV5Monde, Warsaw Stock Market, DNC, and other, related attacks is based on metadata left by the malware, including using the same command-and-control server to steal the data from targeted machines. The coding of the malware has been tracked by several leading cyber security firms including Trend Micro, FireEye (Mandiant), Symantec, and Crowdstrike.
The Russian intelligence hack on TV5 in France was part of the sophisticated global propaganda campaign. That they chose to mimic and blame the attack on the Cyber Caliphate Army shows that their usage of “false flag” operations has enhanced the image of the ISIS cyber terrorists. Many people still blame ISIS for an operation that only the Russian version of NSA could have performed.
Although al-Qaeda has issued communications indicating it was starting a cyber war on the West, the few groups working for al-Qaeda lack manpower, track record, and, based on their listed attacks, a strong skill set. Two teams are commonly identified as al-Qaeda hacker groups, the al-Qaeda Hacker Team and the official group al-Qaeda Electronic. Here are the basic overviews of the two groups:
Al-Qaeda Electronic
PROFILES:
Al Qaeda al-Jihad al-Electroniyya19
Al Qaeda Electronic Army (AQEA)
Al Qaeda Electronic Cyber Army (AQECA)
Under command of Yahya al-Nemr (Emir)20
facebook.com/mujahed.yahyanemr
Deputy: Mahmud al-Adnani21
Deputy: Qatada al-Sainawi22—Announced July 6, 2015, on al-Mareek Media
Spokesman: Abu Obeida Saidi
Head of Funding: Moaaz al-Tikriti—Announced July 6, 2015, on al-Mareek Media
The group was announced January 20, 2015, in video release from al-Mareek, the official media arm of the group.
Al-Mareek Media Arm
Twitter account
Created March 2015
Kandahar, Afghanistan
@almaarek_media
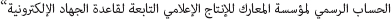 | The Official Account of al-Mareek Media
| The Official Account of al-Mareek Media
Last Tweet, July 1, 2016
Yahya al-Nemr
Yahya al-Nemr may have been born in Tirkrit, Iraq. He lived in ar-Rish and in Kandahar, Afghanistan. He conducted over three hundred defacements between October 2013 and May 2014.23
He was active on Aljyyosh.com, a defacing mirroring site.
Yahya al-Nemr’s Facebook page.
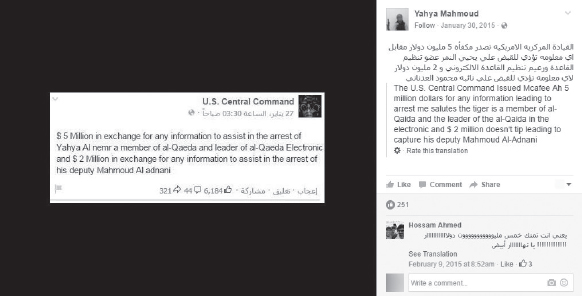
Figure 37:Yahya al-Nemr posted an announcement calling for his arrest by CENTCOM to his Facebook page. (Source: TAPSTRI)
Yahya al-Nemr’s other groups:
“Forces Iraq Electronic” (FIE)
Nemr served as commander for FIE.
Active: January 6–April 2014. They defaced over 94 sites.24
Members: “SWAT Ghost Baghdad,”Commander of special operations; “Abu al-Mashakl,” attorney general; “Lion Diyala,” Commander of Intelligence; “Prince Hacker,” spokesman.
January 4, 2014—FIE’s first post on Facebook.
March 24, 2014—Members SWAT Ghost Baghdad and “Al Qaisi” booted from FIE.25
Other FIE members included Sakar al-Karada, Ali al-Kaabi, and “!-_*YaSSeR*_-!”
AEI’s Eric Liu noted that FIE made lofty false claims of responsibility, whereas AQE’s outlet, al-Mareek, does not indicate a variation of seriousness during al-Nemr’s transition from FIE to AQE.
Members: Yahya al-Nemr operating under name “Yahya al-Saddami”, “Abu al-Mashakl,” “Alwaawi al-Malik,” “Ahtrafi.”
Figure 38: Hacked by Team al-Hackers al-Mujahidin. (Source: TAPSTRI)
AL-QAEDA ELECTRONIC ON SOCIAL MEDIA
AQE had a YouTube video that was suspended. It reportedly hosted hacking lessons including working with remote access tool, njRAT. The Twitter account set up for AQE (alqaeda_11_9) has been suspended.
Al-Qaeda Electronic Hacks
May 2015—Attacks Egyptian news outlet.
June 29, 2015—Threatens US Economy in defacement.
July 3, 2015—AQE defaces 22 British sites.
July 7, 2015—AQE targets Edicot, French software company.
July 14, 2015—ACE defaces Austrian sites and claims it hacks French sports club website.
October 7, 2015—The extremist media tracking site MEMRI reports AQ took over Russian websites in “Website Kristen Russia Hacked.” The user name was Izza Mujahid, who used the hashtags #OpSaveSyria, #OpRussia, and #Mujahidn_Cyber_Army.
March 2, 2016—ACE hackers claim to have struck the Indian Railway’s Railnet page. The hack affected the Bhusawal division of the Central Railway’s Personnel Department. The message posted was attributed to Maulana Aasim Umar, AQIS Emir.26 ““Why is there no storm in your ocean? A message for Muslims of India from Maulana Aasim Umar (May Allah protect him).” This phrase first appeared in 2013 video of Umar. An 11-page document of the speech circulates online.
April 20, 2016—ACE starts defacing sites in multiple countries including France, Russia, Greece, and the United States.
March 17, 2016—ACE defaces Iranian websites.

Figure 39: Al-Qaeda posts this graphic to hacked Websites. (Source: TAPSTRI)
The Al-Qaeda HaCKeR TeaM (AQHT)

Figure 40: Al-Qaeda Hacker Team Twitter Logo. (Source: TAPSTRI)
On March 1, 2013, the AQHT hacked the Washington State Community College website by al-Qaeda hacker Team & TKL, an unidentified member of the Palestinian Gaza Hacker Team. The home page was defaced, replaced with a picture of OBL, and signed: “Hacked by al-Qaeda Hacker Team&TKL.”27

Figure 41:We Are All Usama Page—Image posted to WSCC site by Al-Qaeda Hacker Team. (Source: TAPSTRI)
On March 3, 2013, the AQHT struck the town website for Wanatah, Indiana.28
I swear by Allah, who raised the heavens with no pillars, America and who lives in America will never enjoy security until we live it practically in Palestine and until all the infidel forces leave the Peninsula of Muhammad.
The al-Qaeda Hacker Team’s twitter channel was active starting August 31, 2013. The group attacked a Pizza Hut of India site on August 31, 2013.
Figure 42: AQ Hacker Team—Tweet 1. (Source: TAPSTRI)
They lasted on Twitter for six days. The last tweet came on September 6, 2013, one week after the page was launched. They posted mostly about a few hacks but found time to joke about the CIA and conspiracy theories.
Figure 43: AQ Hacker Team—Tweet 2. (Source: TAPSTRI)
Al-Qaeda Cyber Affiliates
In March, 2013, The Tunisian Cyber Army was a small unidentified group that claimed coordination with AQEA, al-Qaeda Electronic Army, in hacking US government sites. They also claimed assistance from Chinese hackers.29 They claimed to have attacked the Pentagon and released the statement “Thanks to Allah, the al-Qaeda digital [team], in collaboration with us [i.e., TCA], succeeded in striking America [with] a painful blow against the Pentagon.”30
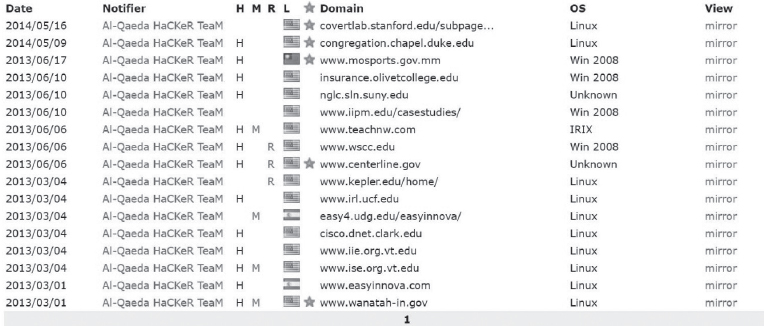
Figure 44: Zone H list of Al Hacker Team Hacks. (Source: TAPSTRI)