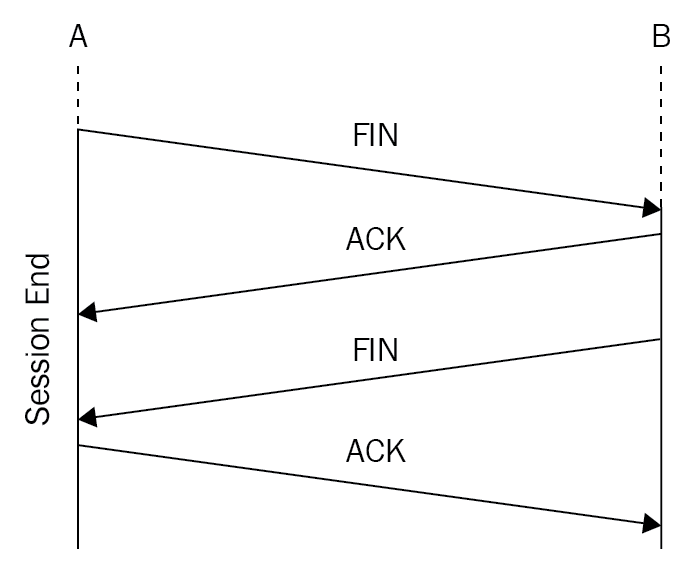
A FIN packet is used to close the TCP connection between client and server. Closing the connection is more complex than creating a connection because both sides have to release its resources. In the following diagram, you can see that a FIN packet works with the last ACK:
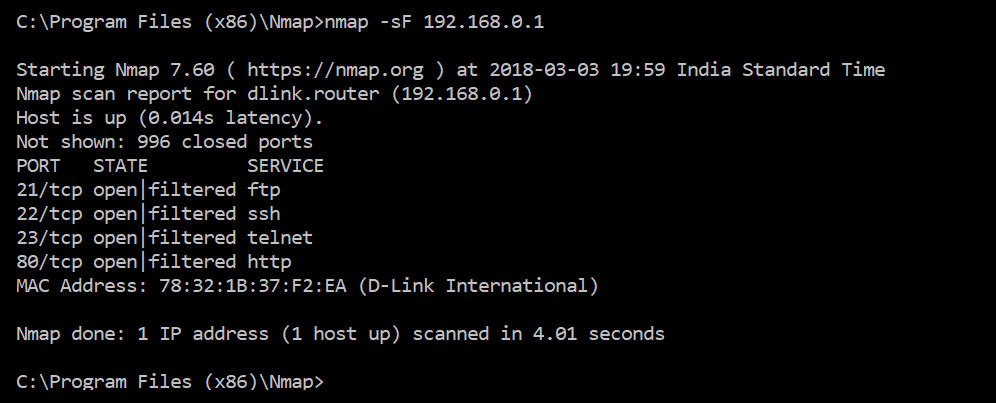
Tools like Nmap can generate a FIN packet without having the ACK set to 1. An operating system might respond to this with RST, which gives you a clue about the remote operating system.
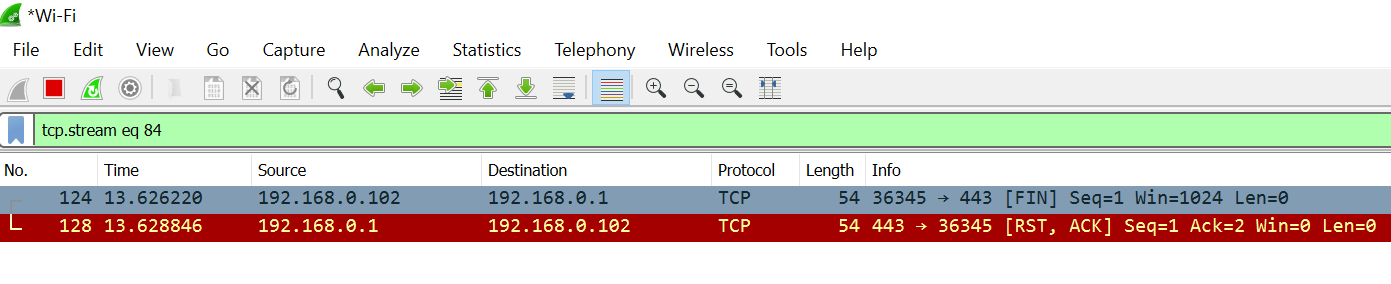
Let's test a live environment with the packet capture. I tested FIN on my wireless router, and here are the results when I followed the TCP stream on Wireshark:
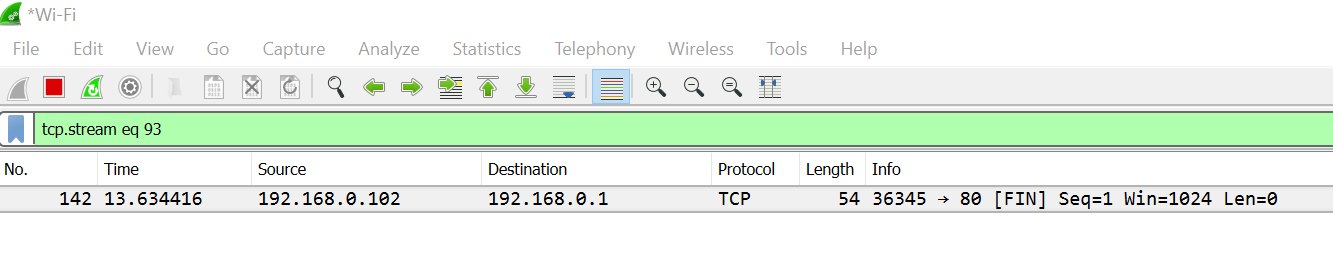
Let's test the result on Wireshark for port 80, which I know is open on this box. You can see that only FIN was sent and no response was received from the router:
The FIN sent on port 443 gets a RST back because this port is not open on this router: