In traditional enterprise and hosting networks architecture, IT resources such as compute, firewall, storage, load balancer and WAN are fairly static and well-defined under boundaries with a greater degree of control. Network security teams implemented Security Information & Event Management (SIEM), proper security zones, passive TAPs, net flow based solution and IDS/IPS tools to provide deeper insights into security threats occurring in their network environment:
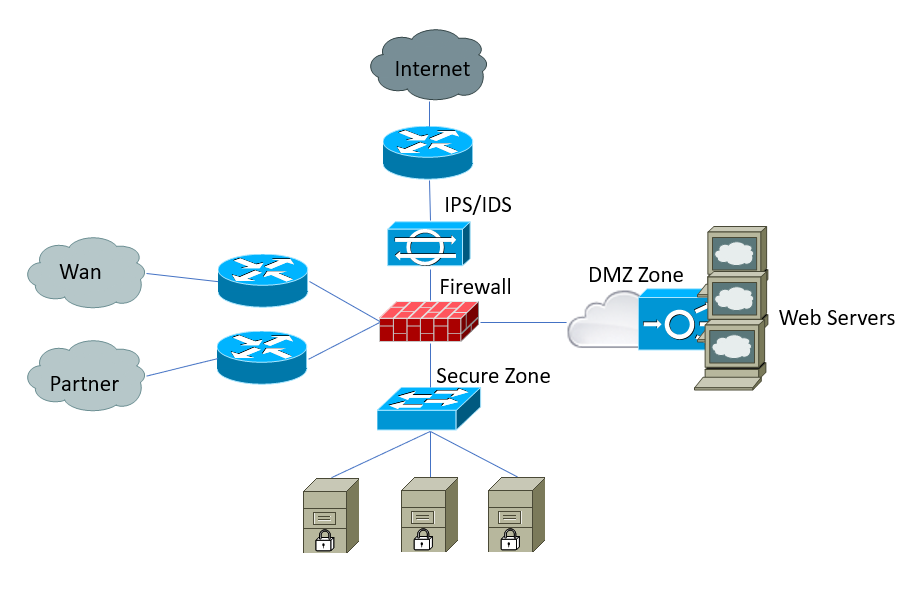
This diagram displays the web servers, network devices, WAN/partner connectivity, and security architecture of a legacy network. Under this model, all systems, network, servers and security were within the organization's control. Achieving full visibility into the network was not a significant challenge.
This is not a perfect model; it has got it own limitations, including:
- Fixed architecture and topology
- Proprietary protocols
- Inefficient use of infrastructure resources
- Hardware-centric
- Manual configuration processes
- Lack of automation and programmability