The following debugging tools are used:
- ICMP ping scan: When checking any device on a network, the first thing that comes to mind is to test ICMP-based scanning. The way it works is that you send an ICMP request packet and expect ICMP echo to reply. The basic idea behind this is to get the live host on the network and then launch a port scanner against those live hosts. Angry IP Scanner is a very popular tool used for network scanning. The problem with ICMP is a network administrator can block ICMP on the network or host layers. You can also easily create a script for an IP scanner which can scan IPs for their defined range.
- TCP ping scan: We have learned that ICMP can be blocked and is therefore not very reliable nowadays. However, instead of using ICMP, a ping probe can be sent by a remote host to a specific port by sending TCP syn. You will then get a reply as a TCP syn-ack. If you want to keep your application alive, this cannot be be blocked by the network administrator.
- Arp ping: You can use utilities like NMAP for ping sweep, and if you use it on a local subnet, it uses an ARP Ping instead of ICMP. NMAP does this by default.
- NAMP: NAMP can do multiple things for you, starting with scanning a host. It can even detect the operating system of a remote host using the light capability of vulnerability scanning.
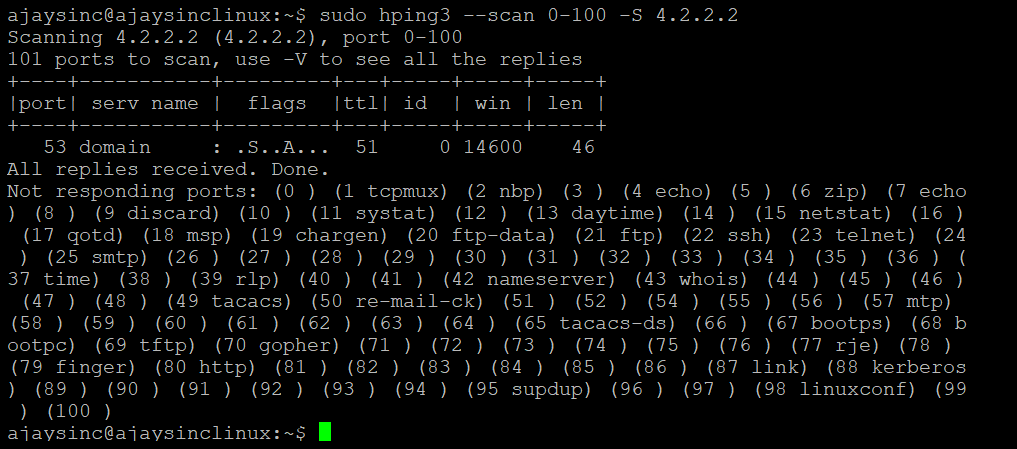
- Hping: Hping was mainly used as a security tool and can be used for firewall testing, port scanning, network testing, MTU discovery, advance traceroute,and OS fingerprinting. This tool gives you the ability to craft a packet. I am using the Ubuntu server, and you need to install the hping package:

Let's look at how to run this tool in port scan mode. Syntax has an argument of 0-100 (port range to be scanned), -S (Send Syn Packet) and 4.2.2.2 (IP address for host) to be scanned. Results show that one port is opened for DNS and this is true, 4.2.2.2 is a DNS server and hence the result is as expected:
- TCP connect scan: TCP connect can be used as port scanning, a simpler form of probing a remote host. This involves a full TCP/IP connection, which is established with all TCP ports and one of the target hosts in an incremental manner. A TCP/IP is reliable as a protocol and such port scanning is a very reliable way to determine which TCP services are accessible on a given target host.
In this example, the nmap tool will try to connect to the remote host in two ways. The first way is through a syntax argument (-sS) , which means that a 3-way handshake will be completed. With the other method, an (-sT) tool will use an application like a browser in the backend to connect to a remote host:
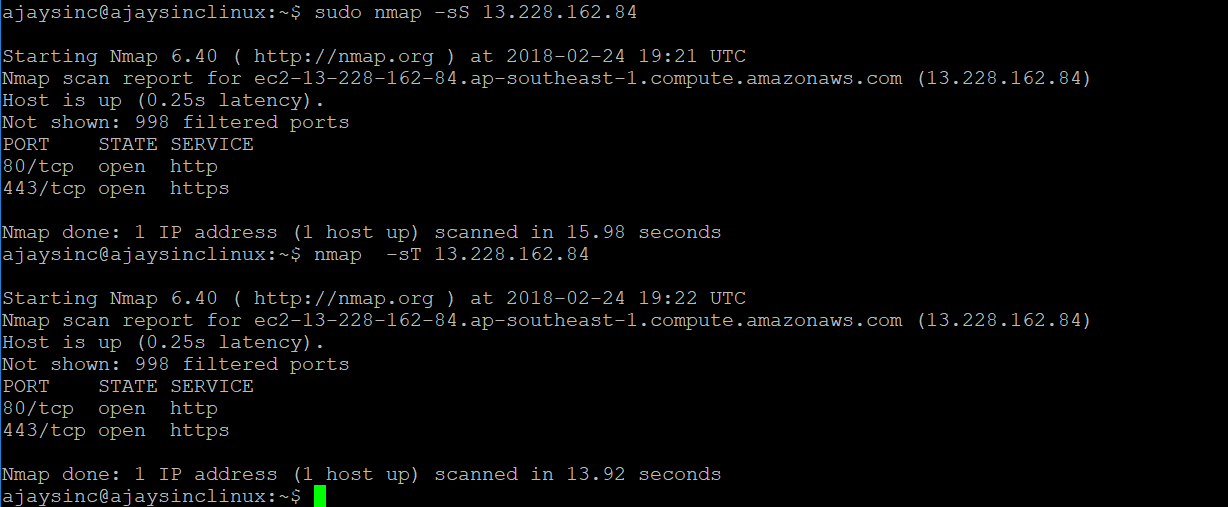
In case the target port is closed, the source receives an RST/ACK packet directly.