Security operation centers always struggle with alert floods coming from the legacy SIEM systems and false positives continue to haunt the network with data breaches. With the evolution of the computer landscape, cyber security has also changed. Let's talk about the days when employees used office desktops to access corporate applications. Things were rapidly replaced with laptops and smart devices, which has secure access to corporate applications from anywhere in the world. Traditional methods for detecting and responding to security threats are no longer effective when it comes to addressing today's security challenges. Today, organizations need a SIEM solution that can scale to support large data volumes coming from various IT resources, as well as analyzing data at a faster speed in order to detect security threats in real time. At the same time, it should fit into the organization's budget.
In this section, we will discuss the key capabilities that a next generation SIEM platform should have.
- Big-Data Storage Capabilities: Network-connected devices' methods for data amount growth is expanding. It's not all about simply collecting huge amounts of data; it also has to be maintained for threat analysis and forensic and regulatory compliance. You must have the capability to store data in a different way, and that different way comes in the form of a big data model. Big data can consume and analyze terabytes of data in real time. Query-based data can be further used for analysis and reporting.
The following diagram shows a SIEM MODEL that has the capabilities discussed previously in this section:
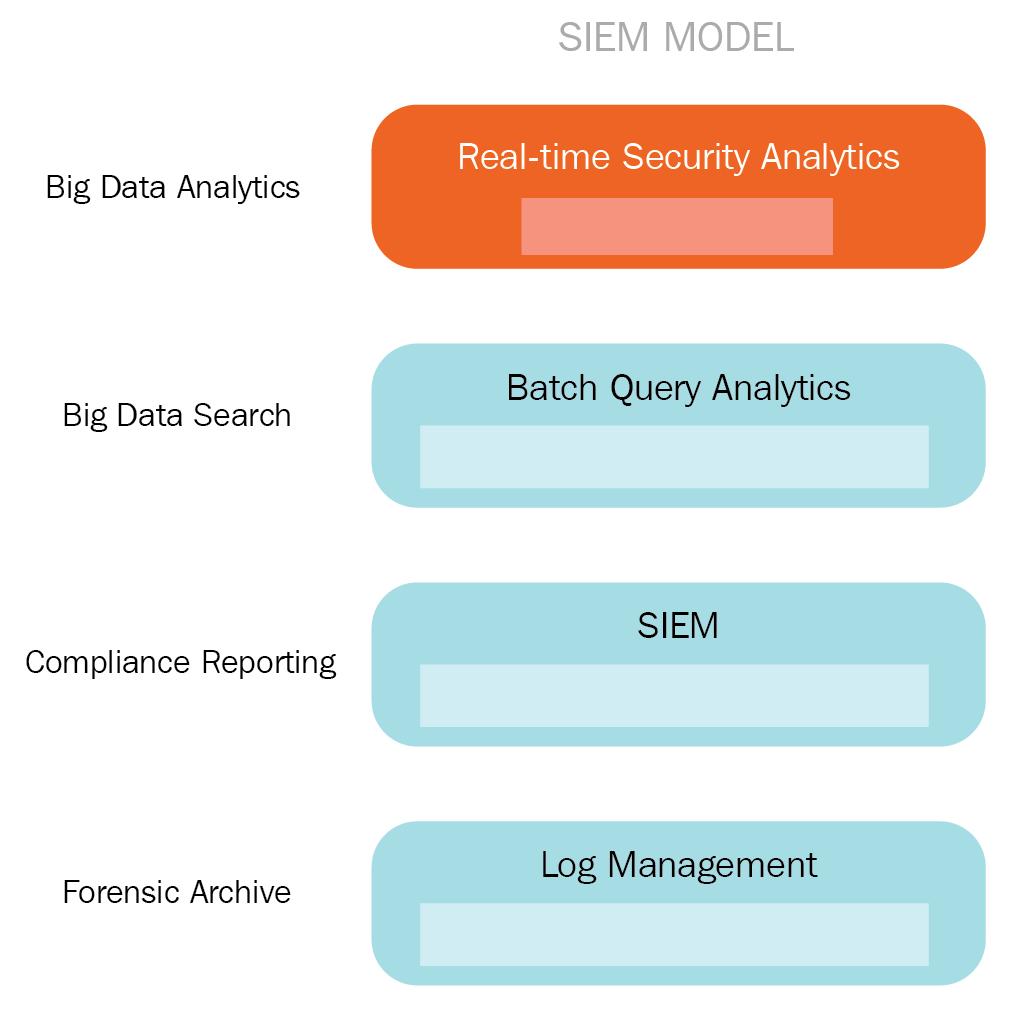
- Real-Time Analytics: Cyber threats and cyber attacks have become highly sophisticated. With an increasing number of surface attacks, attackers are now targeting organizations with ease. Legacy SIEM solutions are rule-based and dependent to know threat patterns. A next generation SIEM should be sufficiently capable of detecting threats in real time for any dynamic environment. This is done by using ML and behavior analytics in order to find highly advanced threats in today's environment.
- Accuracy: Threat intelligence can help you to stay one step ahead of cyber threats by providing you with a rich, external context. Without the proper context, a security alert may likely get lost during an alert flood or may be confused with a security operations center (SOC) analyst. As SOC professionals, how might we react to such alerts? Next generation SIEM should send alerts with a meaningful context. A meaningful context can include an IP address, location, vulnerability type, action required, and, of course, alert priority or severity.
- Automated Incident Response: Detecting cyber security threats is just one part of SIEM, but responding to threats faster is considered the most critical part of SIEM. Every alert generated by SIEM always has a recommended action associated with it. Next generation SIEM should follow best practice by having APIs interact with network and system vendor devices such as firewalls, routers, switches, and endpoint protection devices.The basic idea of this is to take an appropriate, well-defined and automated set of actions once an incident is detected.
- Easy Deployment: For any business and IT process, the deployment of SIEM systems begins with thoroughly planning and reviewing impact and policies. You should also review your security policies and the best practices available in the industry. The deployment model should correspond to the overall IT strategy of organization. The SIEM solution should offer virtual, cloud-based and hardware- based appliances to the customer.
- Low Cost: Security analytics work well with large amounts of data. With a growing number of devices, a large volume of logging data and storage might escalate the cost of the solution. A pricing model should not be based on the volume of data that is collected because this may cause unpredictability in the costing model. Next Generation SIEM costing can be based on the number of users and devices, which is a predictable number. The use of commodity hardware may reduce this cost further.