Based on network traffic between hosts, it is possible to predict what OS is running on a system. Every operating system has its own unique way to implement TCP/IP stack. A very simple but effective passive method is to inspect the initial time-to-live (TTL) in the IP header:

I am on a Windows 10 machine and tried the ICMP ping to host 4.2.2.2. In the Wireshark capture attached below, you can see that the Windows 10 initial TTL value is 128:

I expended the first packet from Wireshark, which confirms TTL 128:
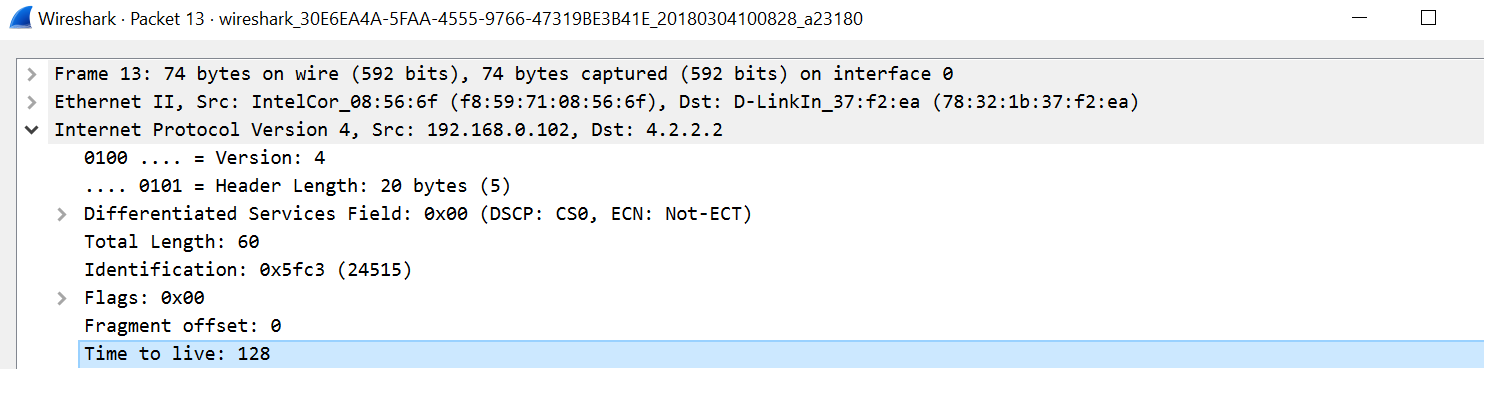
Let's try to expend the return packet, allowing us to see that the TTL value is 59:
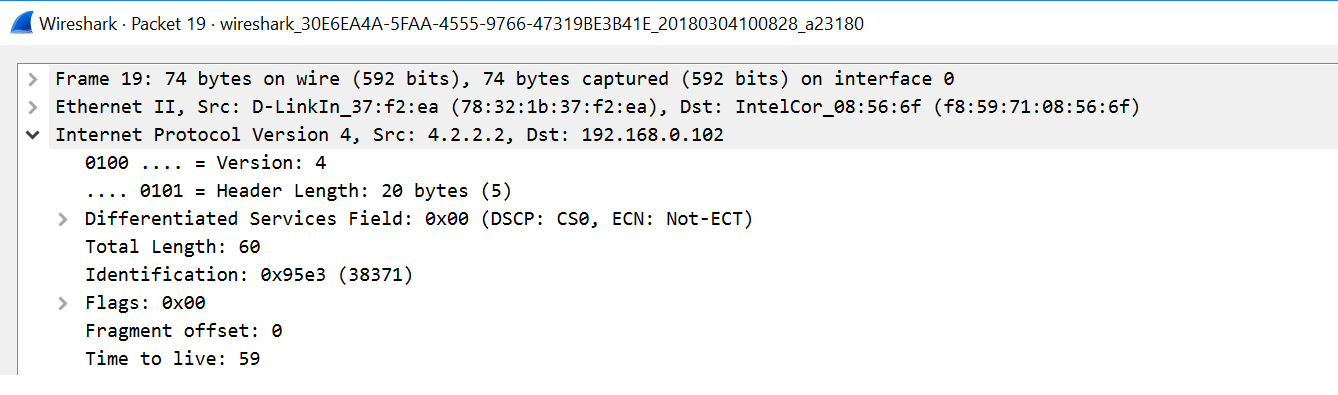
You can now take match results with Nmap remote OS detection. There is a 90% chance that this system will be running a Linux operating system. This should match our reference table. The linux TTL value 64 and value 59 means that this host is five hops away from me.