Intrusion detection systems can be further divided into two broad categories based on their placement: host-based IDSes and network-based IDSs.
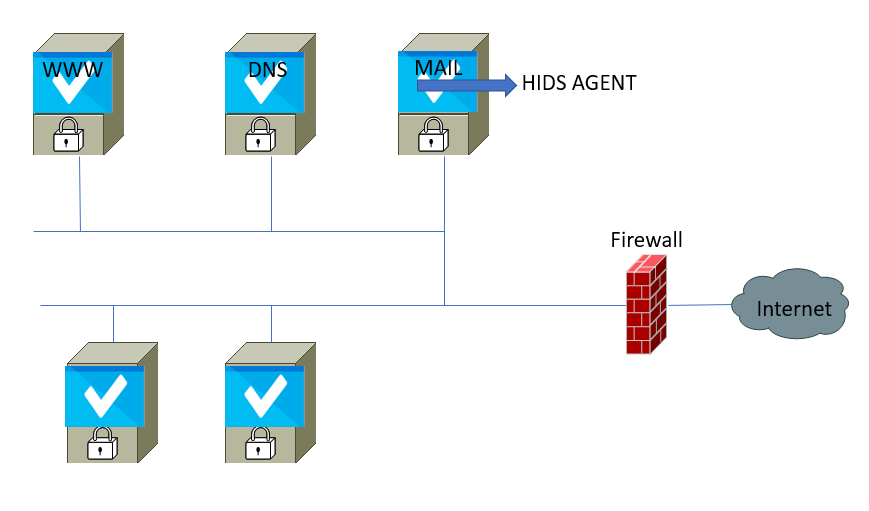
- Host-based intrusion detection system (HIDS): This is a small, agent or sensor-based piece of software installed on single or multiple hosts on a network. It protects the individual host by monitoring and reporting the system configuration and by keeping track of application activity. A host IDS is passive in nature, provides functionality to gather information by identifying, logging, alerting, and reporting. You can always install a HIDS on different DMZ servers such as web servers, mail servers, database servers, or any server that you want to monitor or protect on the network. Any masking techniques such as insertion, padding, fragmentation, or out-of-sequence delivery bypass a network-based IDS but can be easily caught by a host-based IDS. The primary goal of any HIDS is to monitor and analyze data traffic passing through the network interface card (NIC) of a host, but can also be expanded to monitor application behavior and activities.
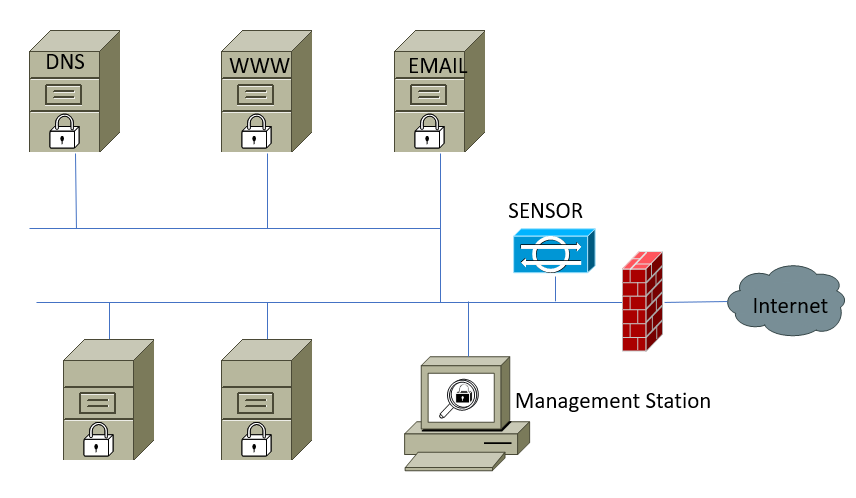
- Network-based intrusion detection system (NIDS): This offers a different approach and monitors activity on the overall network traffic, rather than on each separate individual host. NIDS operations are based on the concept of wiretapping and the system comes with known attack signatures, which can also be customized. Signature updates are released by vendors from time to time. The major issue with NIDS is performance. For small organizations, this might be a suitable solution that deals with gigabytes of traffic. However, for larger organizations with high speed networks, it simply cannot handle it:
NIDS does not decrypt encrypted traffic.